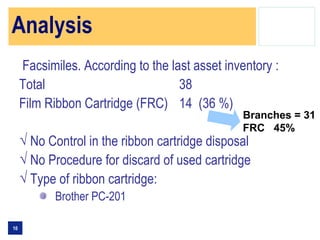
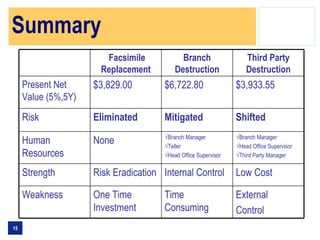
The document summarizes the findings of an information security risk assessment conducted for a bank. It identified risks related to the disposal of used fax machine film cartridges containing confidential information. To address this issue, the committee analyzed options for replacing existing fax machines, destroying cartridges on-site at branches, or using a third party destruction service. Replacing fax machines with newer models that eliminate film cartridges would eliminate the risk but require an initial investment, while in-house or third party cartridge destruction would mitigate the risk but involve ongoing costs and require internal controls or reliance on an external vendor.