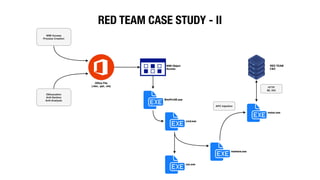
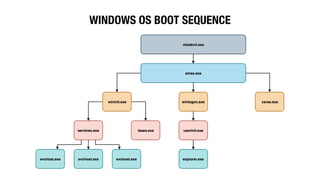
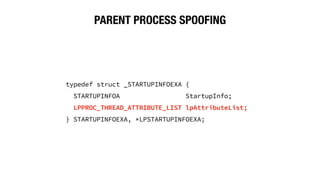
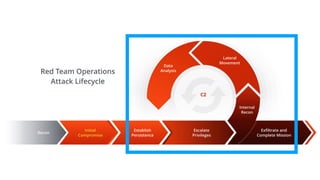
This document discusses endpoint detection and response (EDR) solutions and how red teams can evade them. It provides an introduction to EDR, explaining that EDR solutions monitor endpoints for threats by collecting behavioral data using installed agents. It then discusses why EDR is used, including failures of endpoint protection platforms and enabling real-time visibility and anomaly detection. The document goes on to provide examples of how red teams can evade detection, such as hiding Windows processes, spoofing process arguments and parent processes, and using memory evasion techniques like obfuscation and behaving like a beacon.









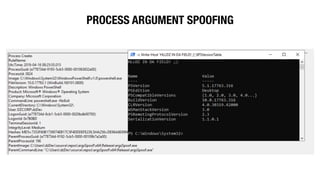
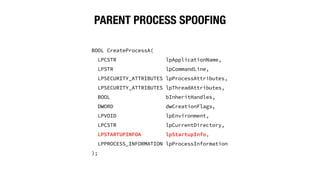
![PROCESS ARGUMENT SPOOFING
typedef struct _RTL_USER_PROCESS_PARAMETERS {
BYTE Reserved1[16];
PVOID Reserved2[10];
UNICODE_STRING ImagePathName;
UNICODE_STRING CommandLine;
} RTL_USER_PROCESS_PARAMETERS, *PRTL_USER_PROCESS_PARAMETERS;](https://image.slidesharecdn.com/hd-190505181422/85/Next-Generation-War-EDR-vs-RED-TEAM-14-320.jpg)