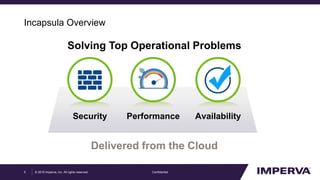
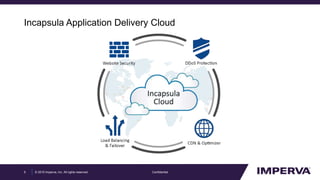
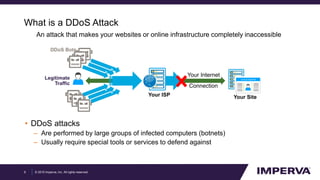
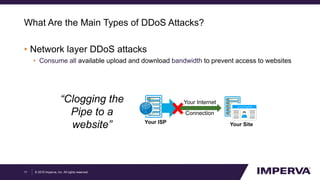
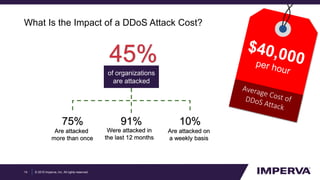
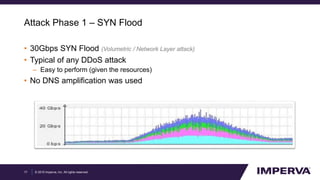
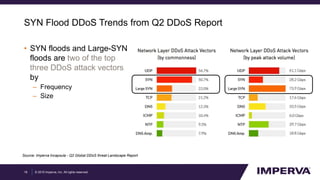
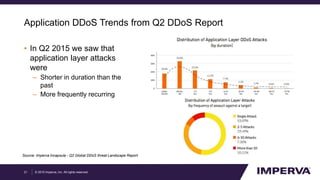
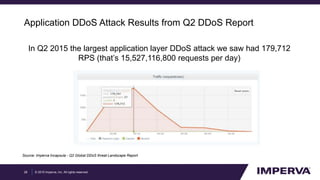
The document provides an in-depth examination of sophisticated Distributed Denial of Service (DDoS) attacks, highlighting their increasing prevalence and complexity. It discusses various types of DDoS attacks, their impacts, and phases of an attack, as well as mitigation strategies. Additionally, it emphasizes the importance of preparedness and user-friendly defense mechanisms to minimize disruption during such attacks.