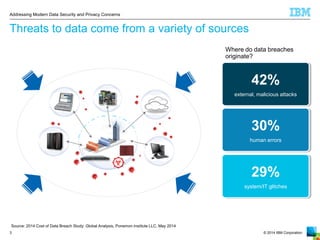
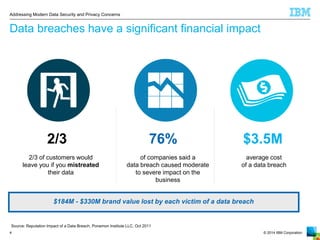
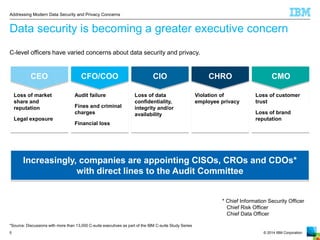
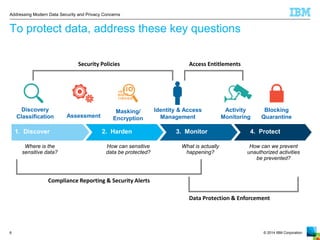
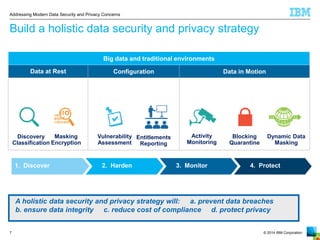
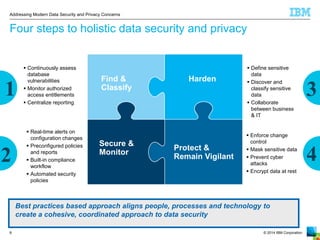
The document outlines the increasing challenges and concerns of data security and privacy in the context of big data, highlighting the prevalence of data breaches and their significant financial impacts on companies. It emphasizes the necessity of appointing dedicated roles such as CISOs and implementing a holistic strategy that includes discovering, securing, monitoring, and protecting data. The four key steps to enhance data security involve identifying sensitive data, monitoring access, and enforcing robust protection measures to mitigate risks.