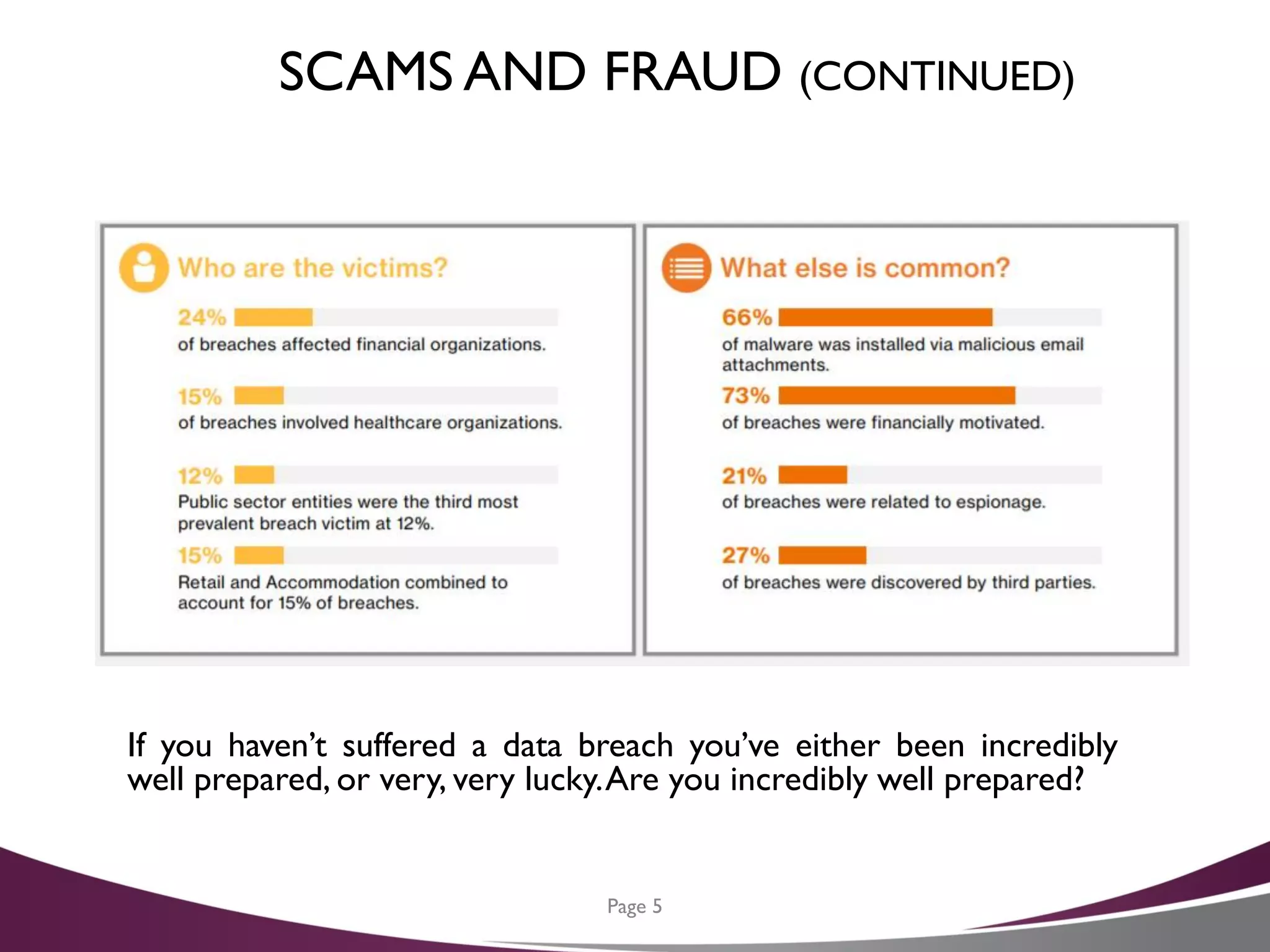
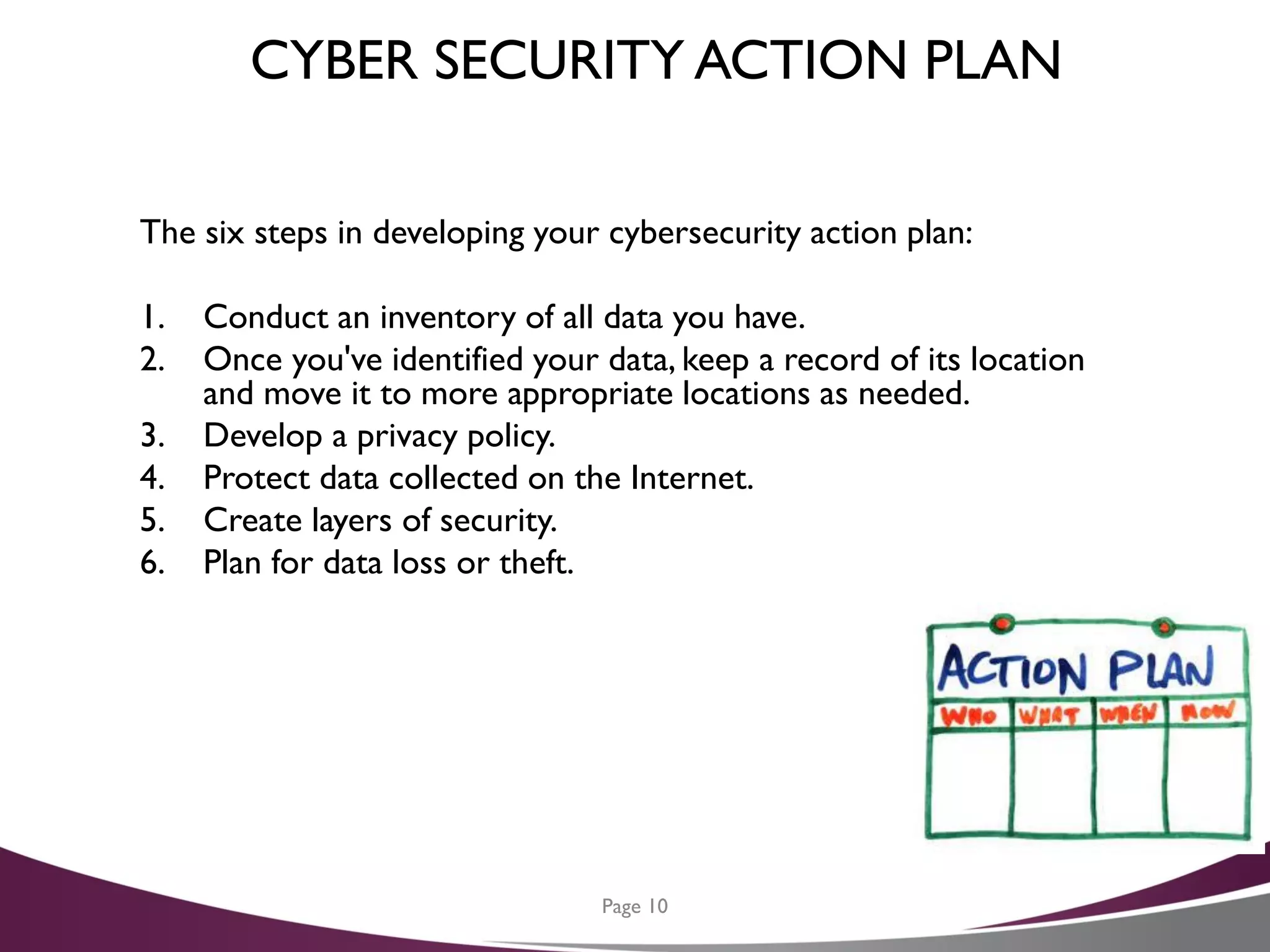
The document is a cybersecurity planning guide for CFOs, emphasizing the importance of data security in light of increasing fraud and data breach incidents. It outlines a six-step action plan for developing an effective cybersecurity strategy, including data inventory, developing a privacy policy, and creating layers of security. Additionally, it offers tips for protecting against cyber threats and resources for further assistance.