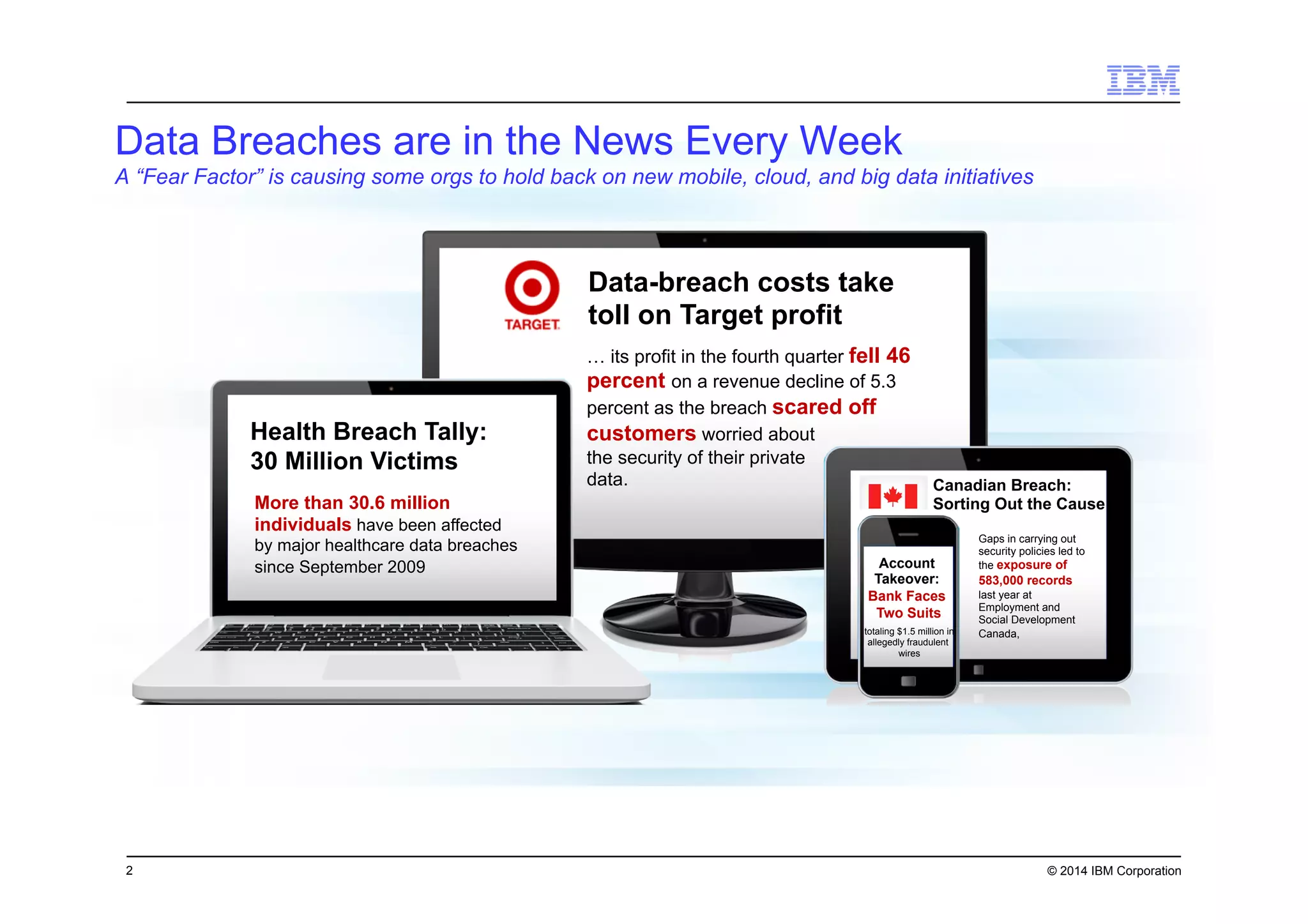
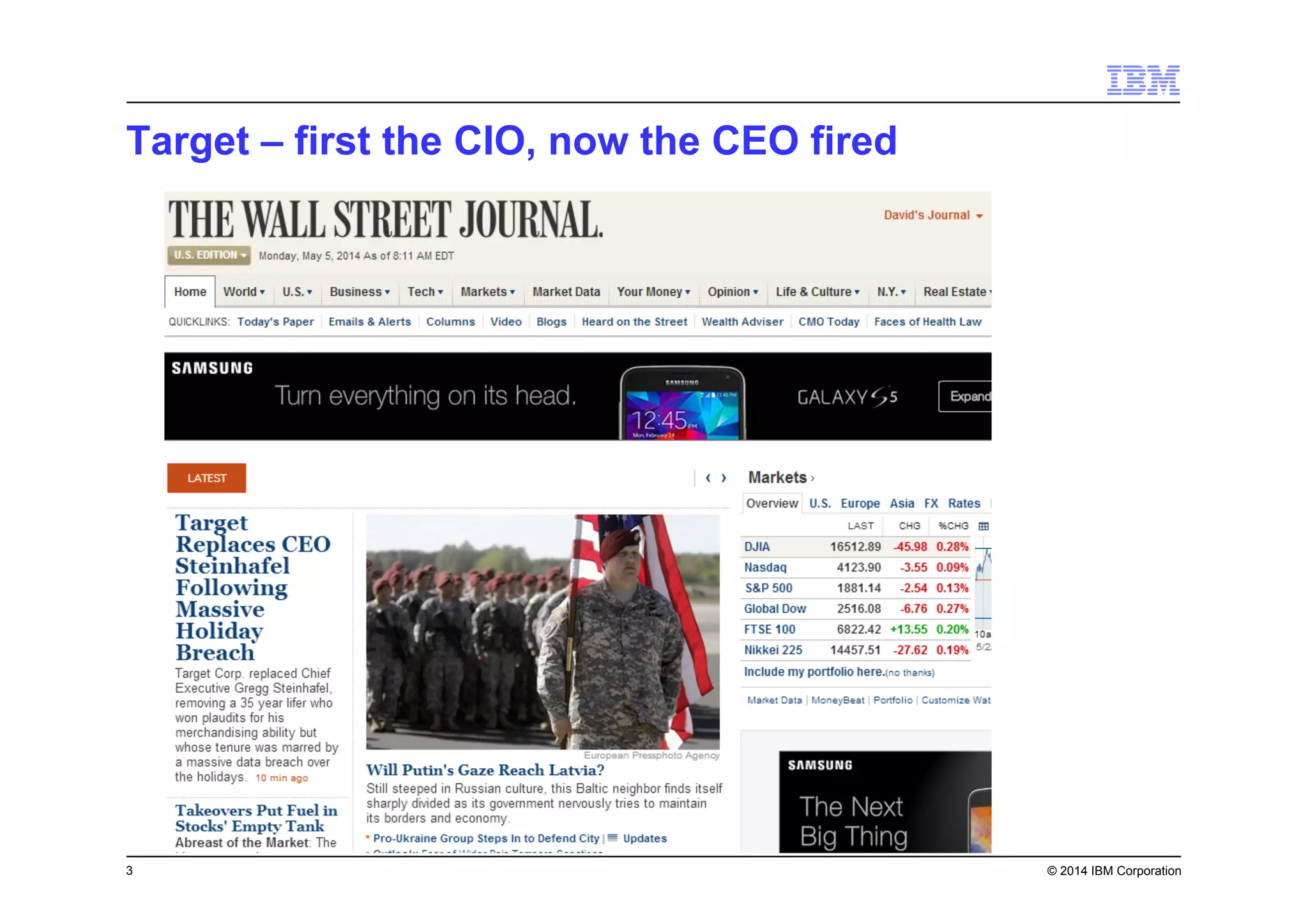
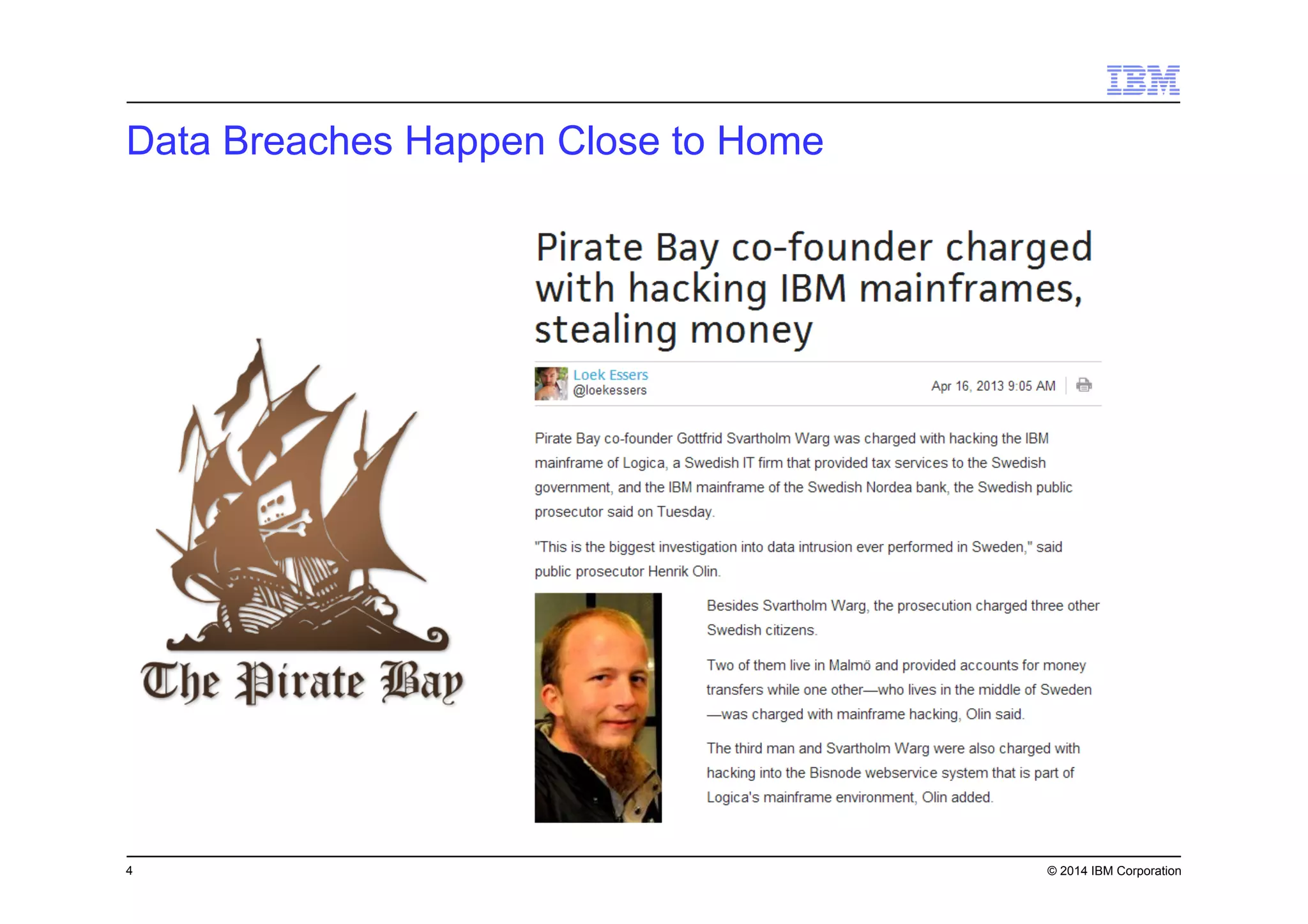
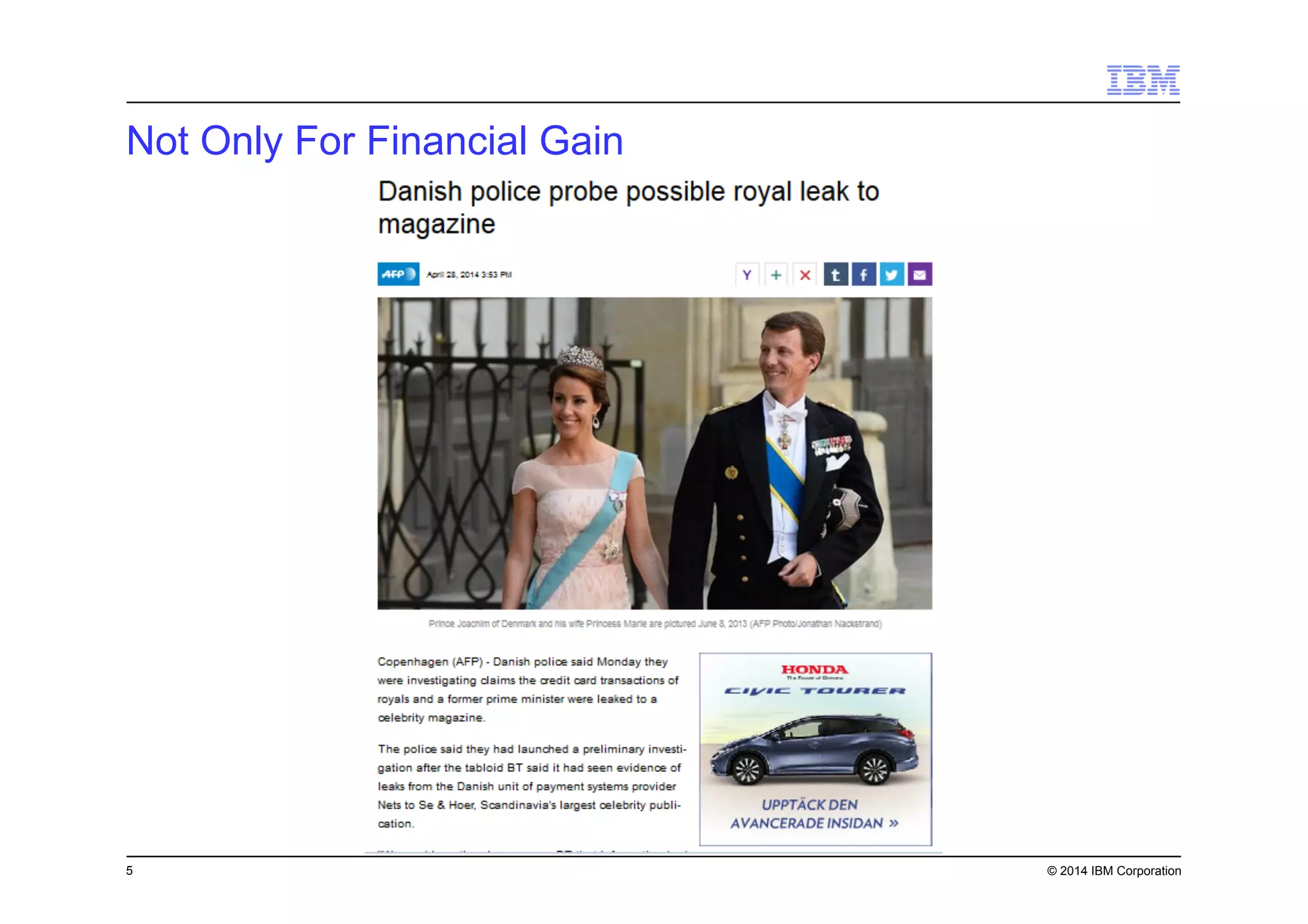
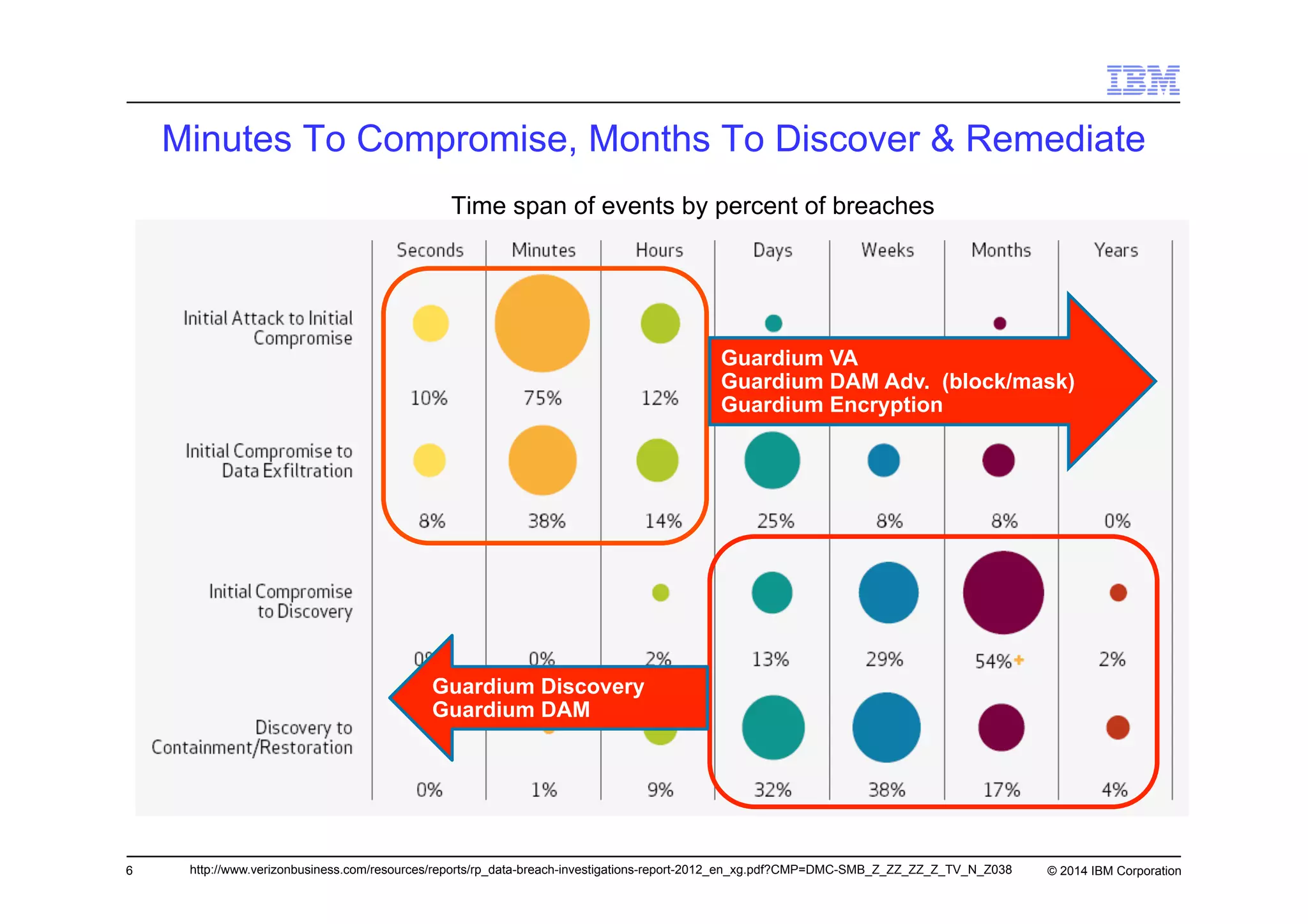
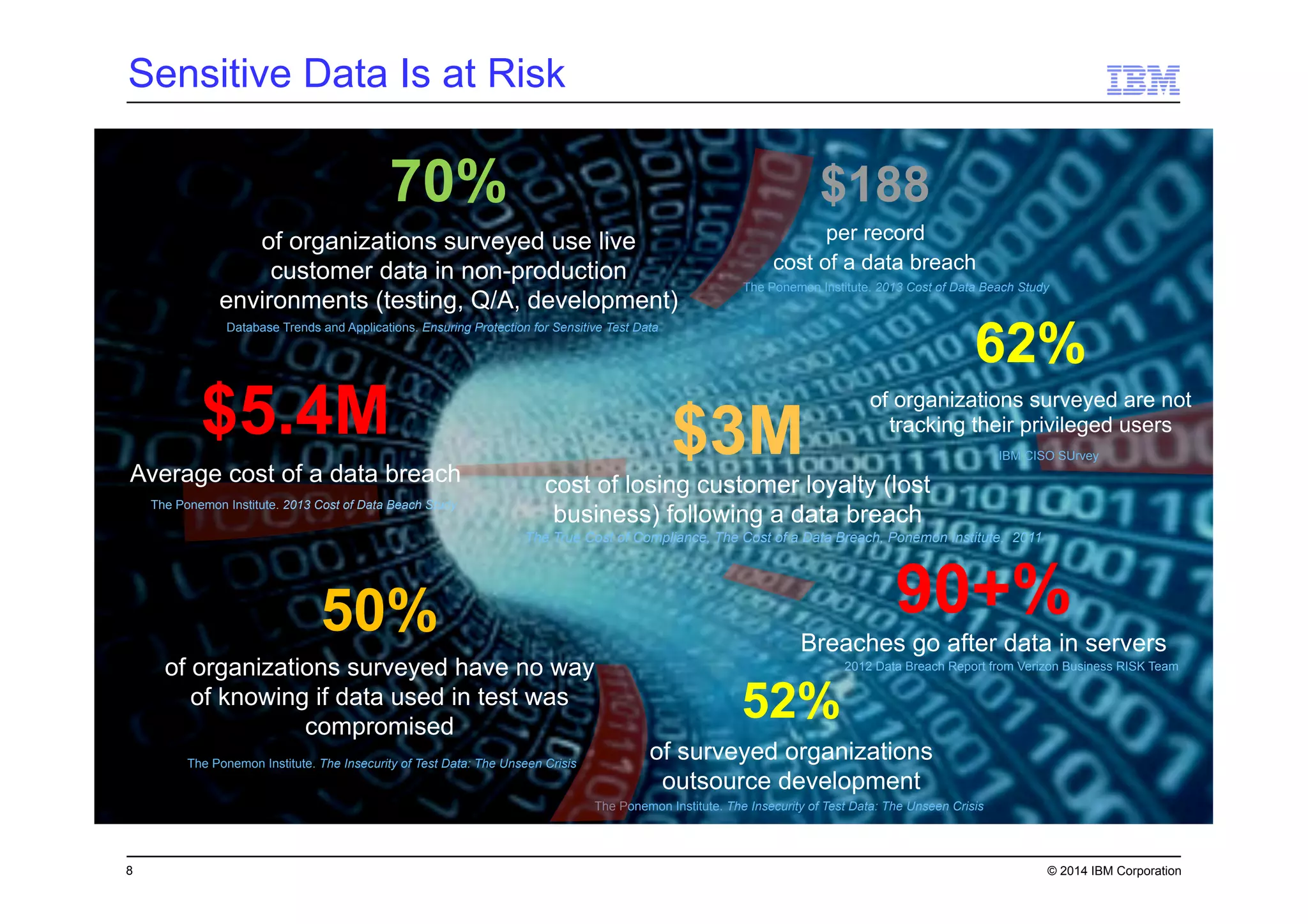
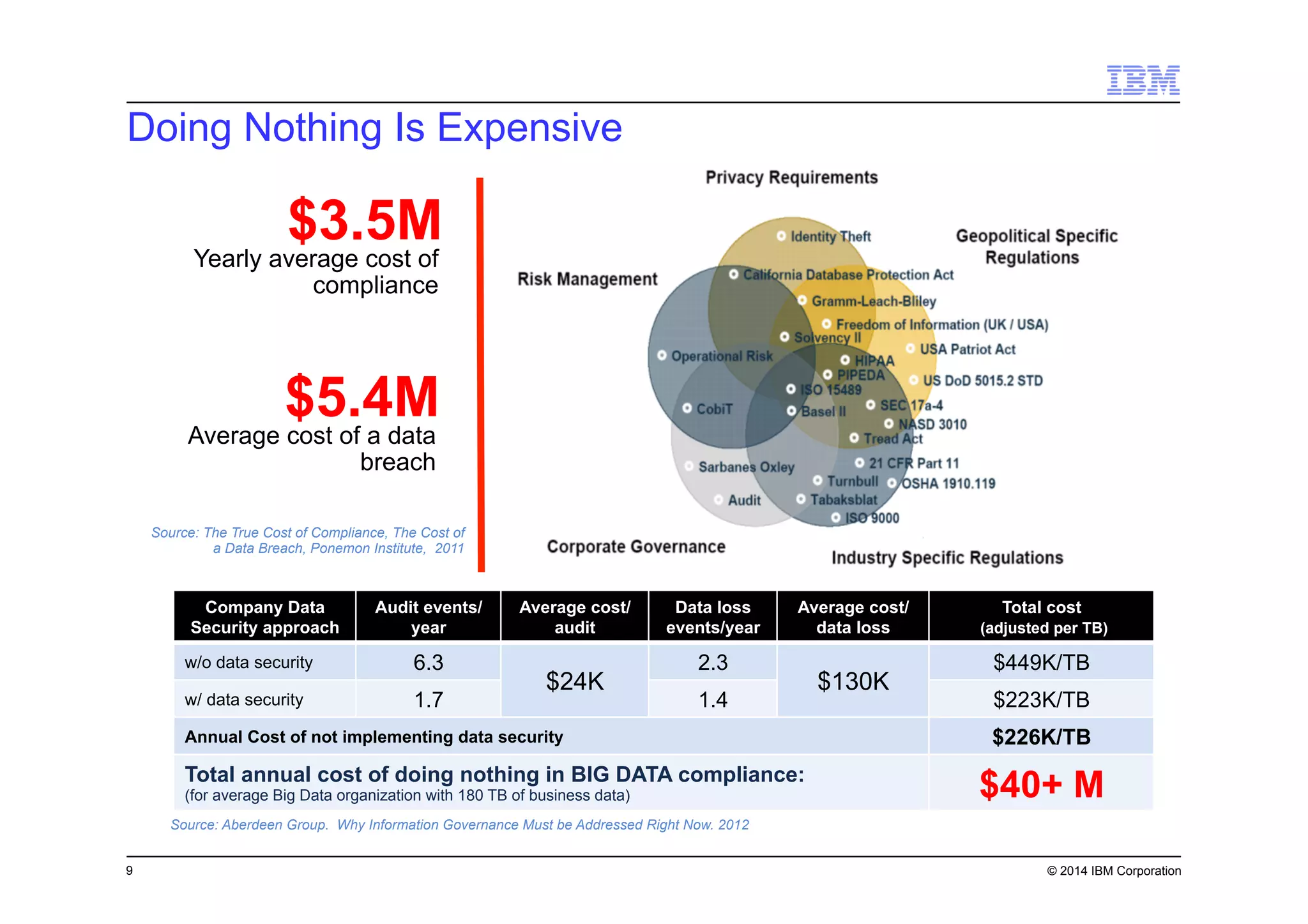
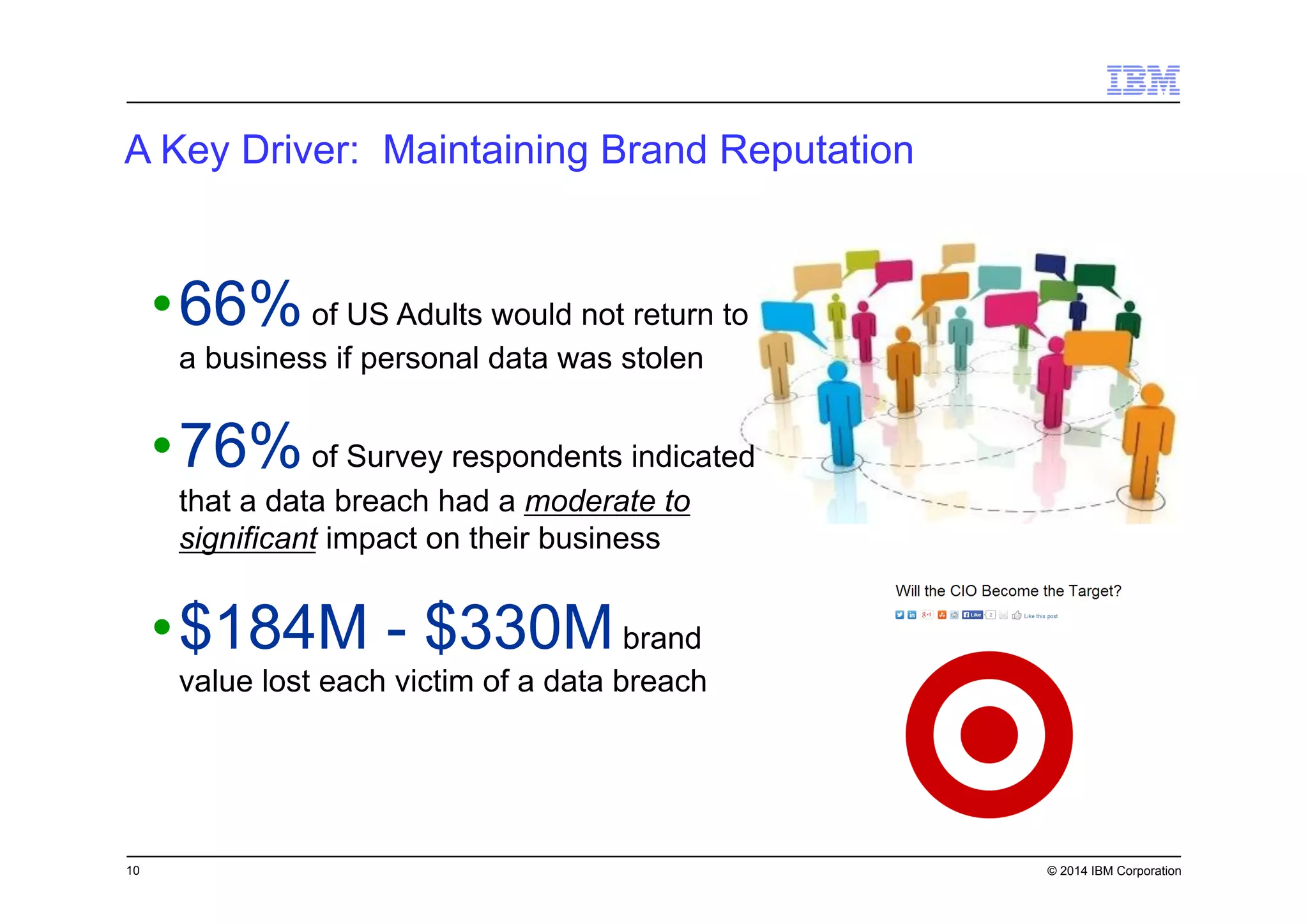
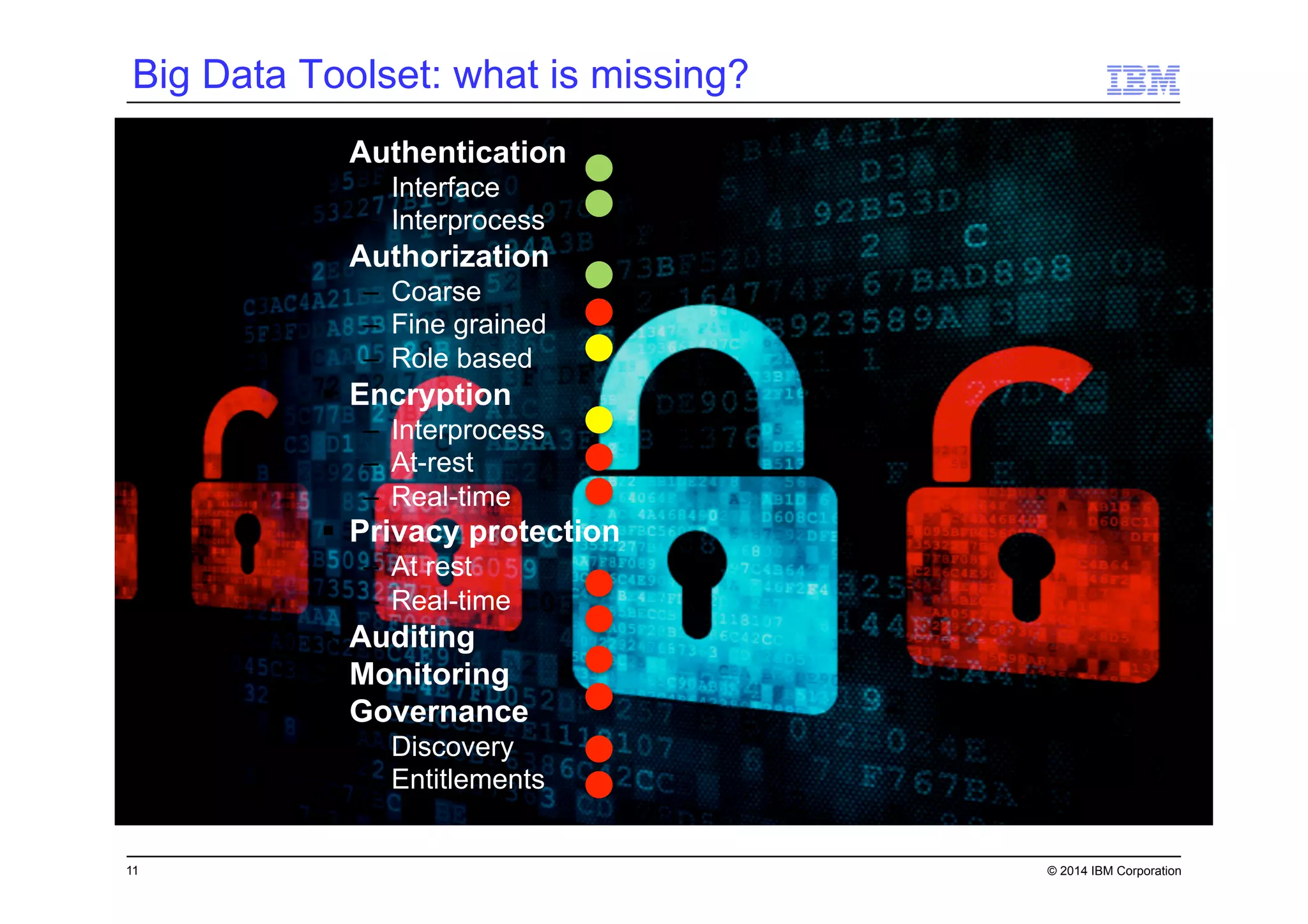
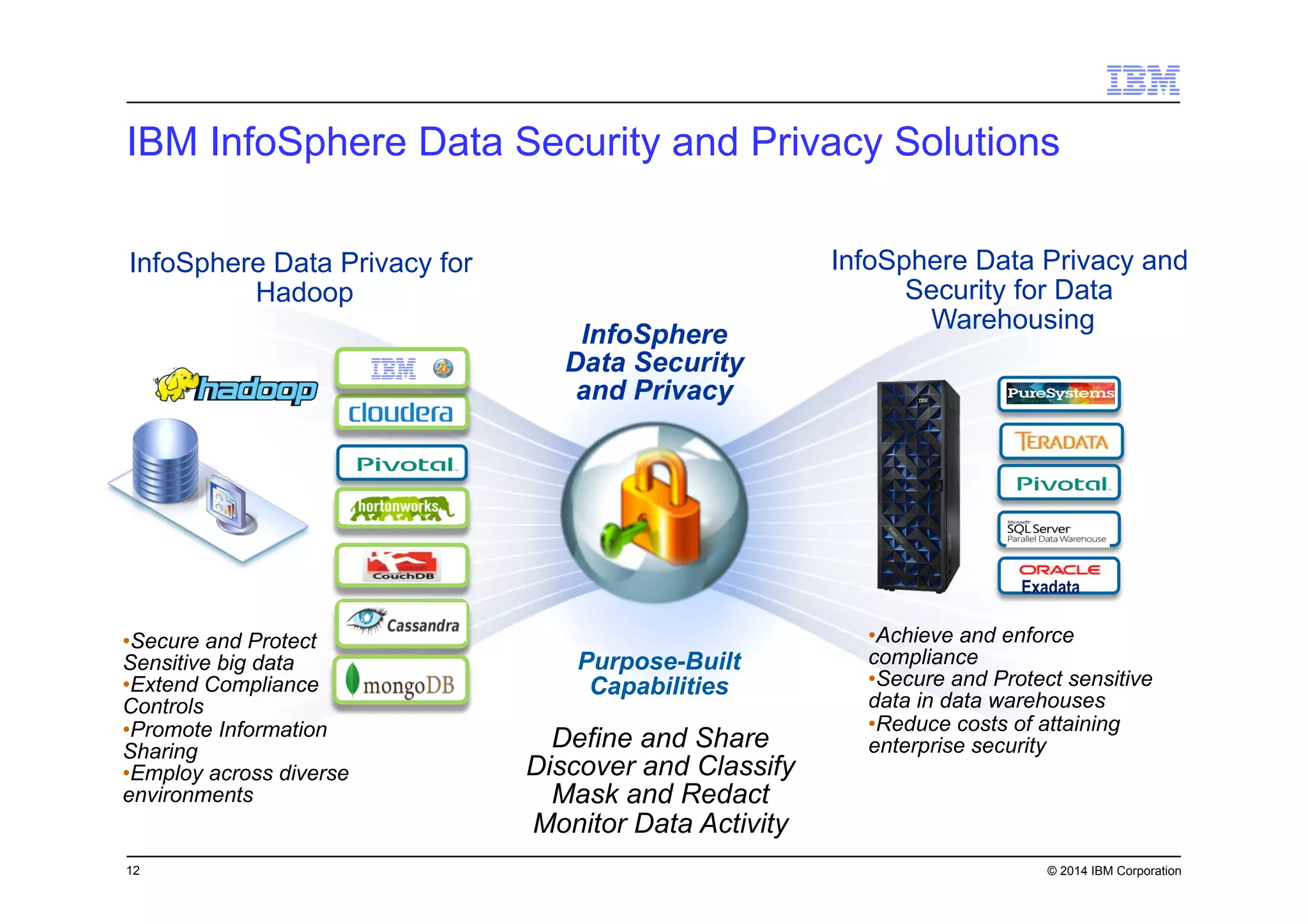
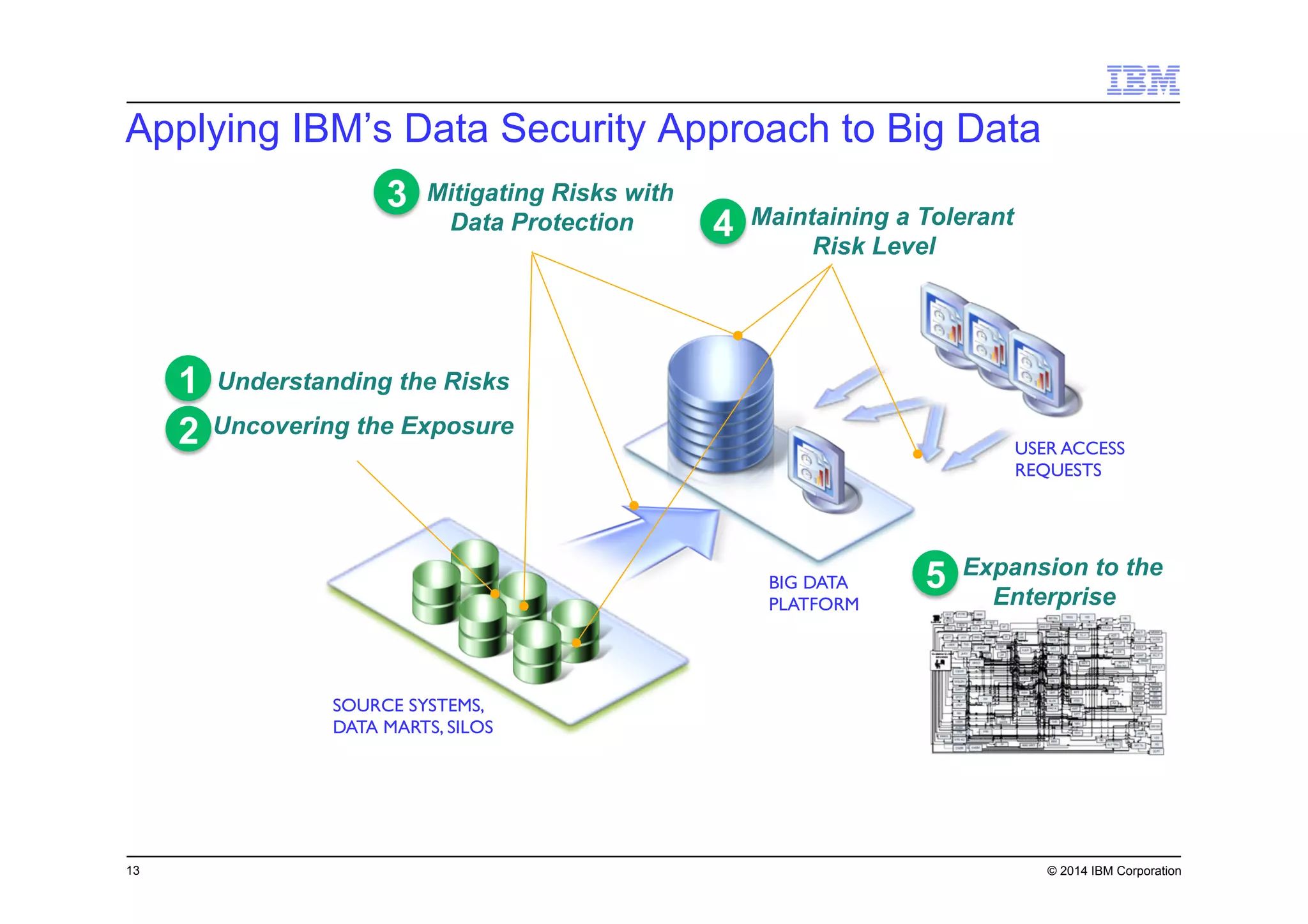
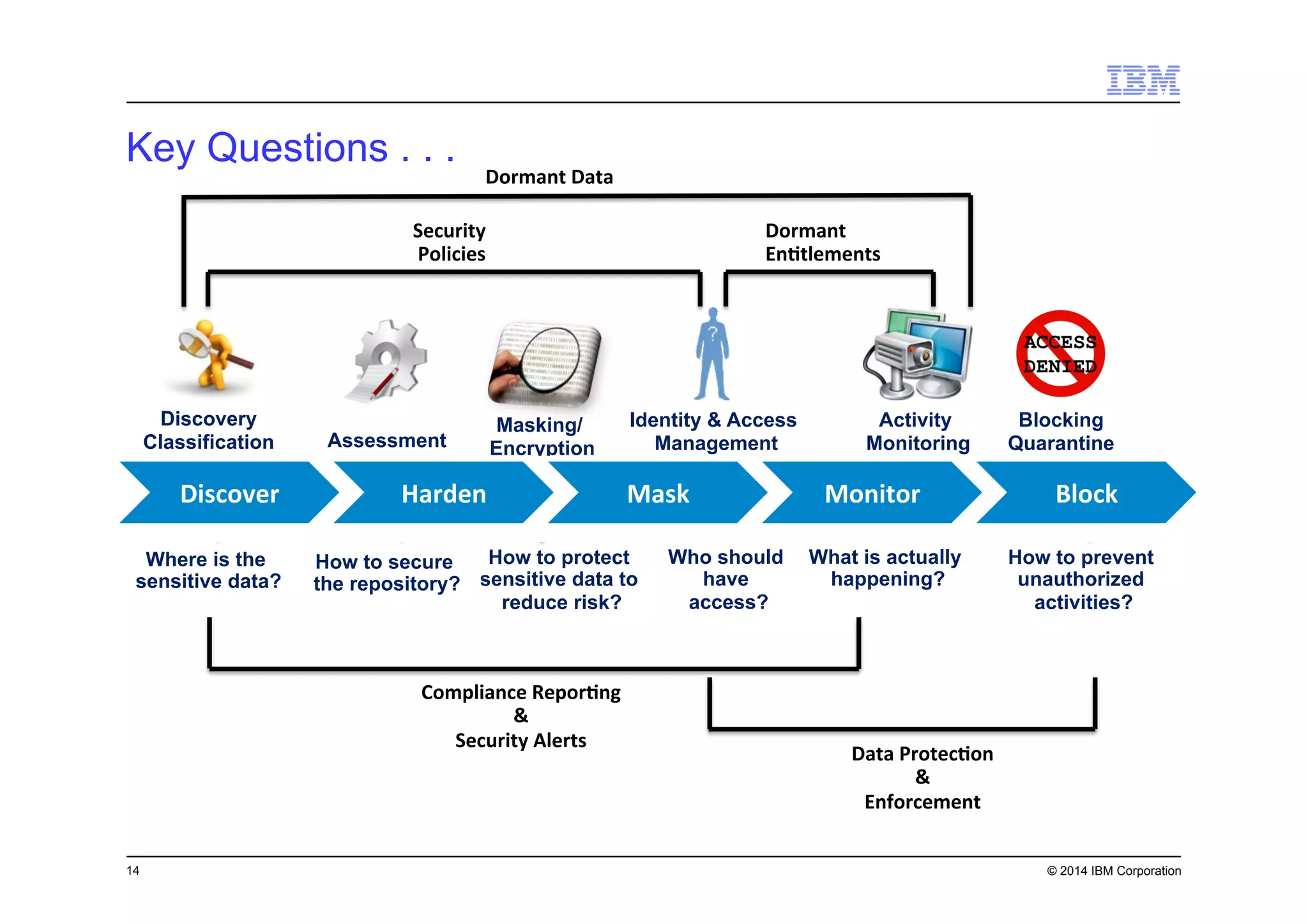
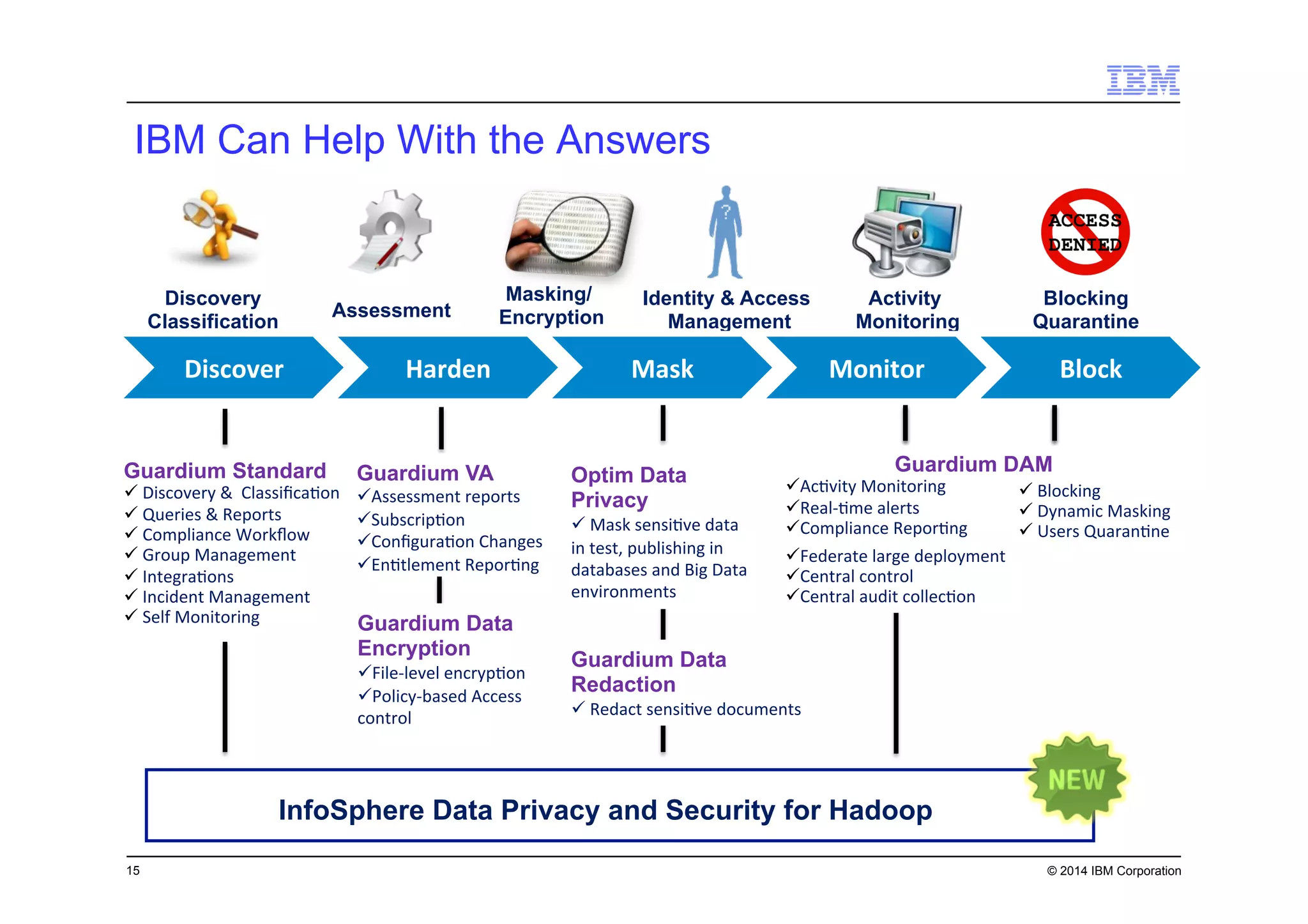
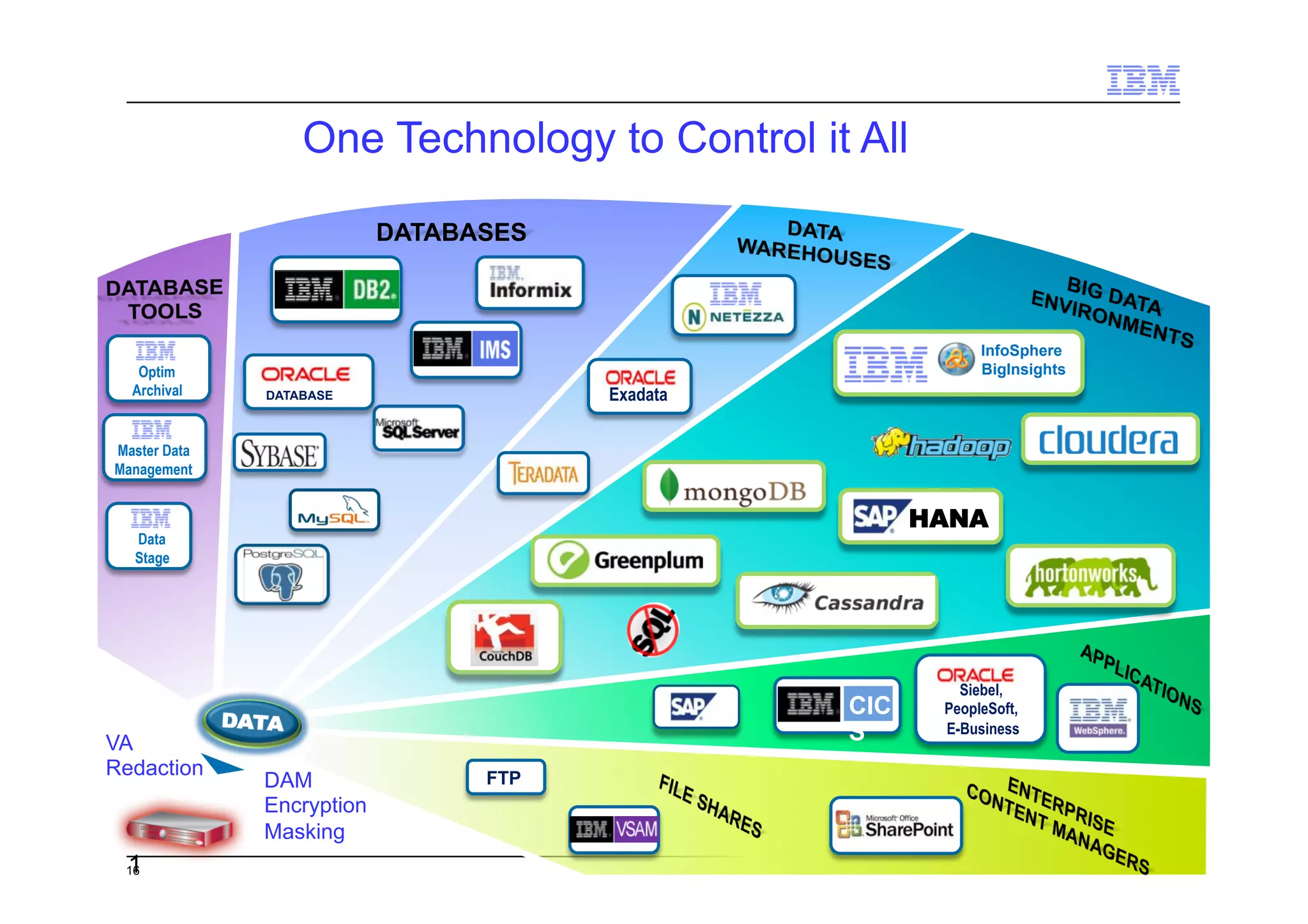
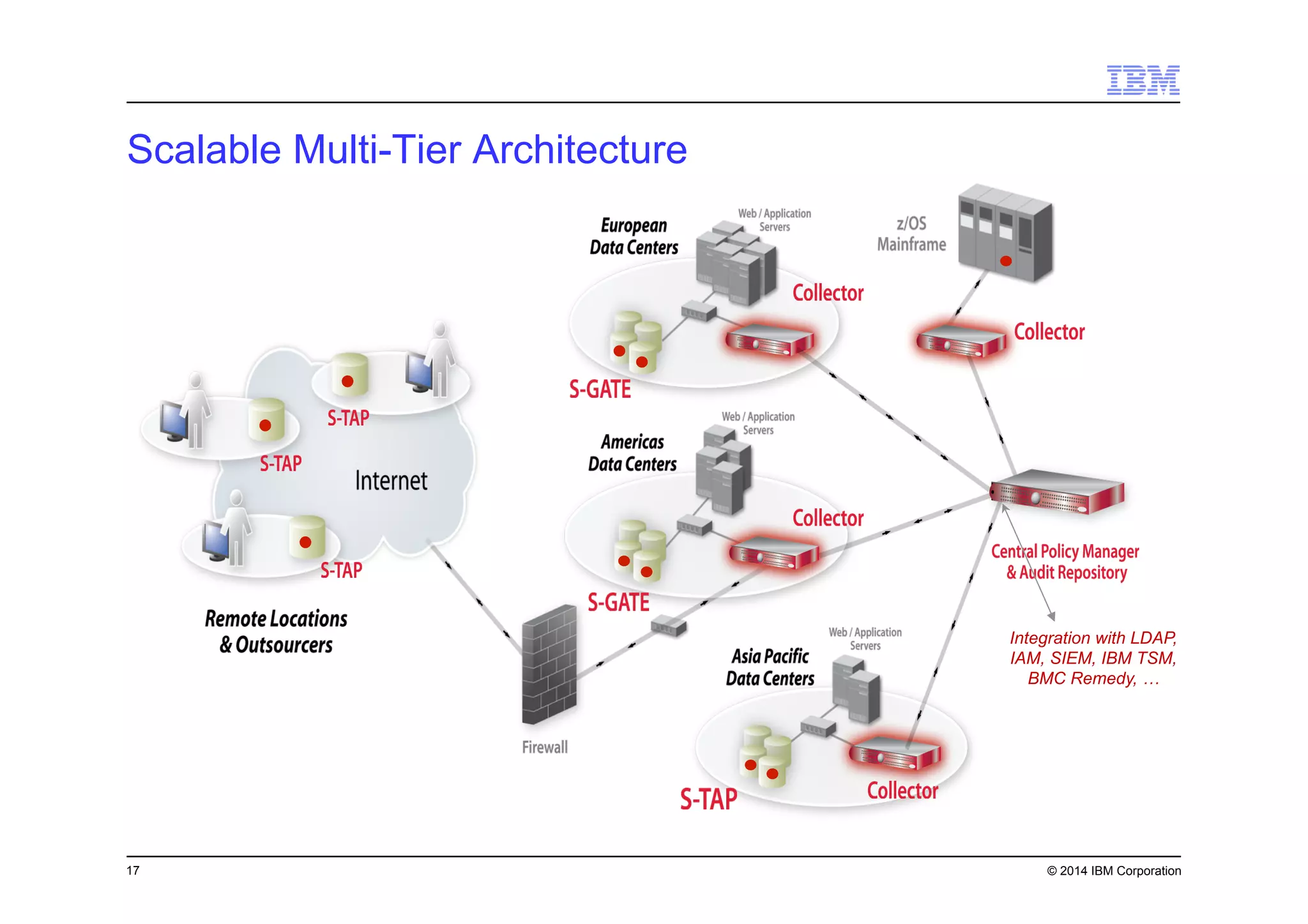
This document discusses data security challenges in big data environments. It notes that data breaches are common and costly for organizations. Several examples of recent breaches are provided that impacted companies like Target, a Canadian government agency, and healthcare providers. The document advocates for the IBM Guardium suite of data security products to help secure sensitive data across different systems and platforms through discovery, monitoring, masking, encryption and other techniques. It argues these tools are needed to reduce risks, costs, and protect brand reputation for organizations working with big data.