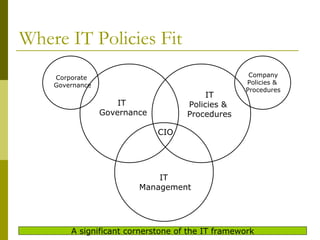
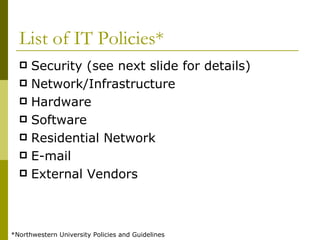
The document discusses the importance of having IT policies for organizations. It provides reasons for developing IT policies such as preventing abuse of resources, protecting ownership and employees, and meeting regulatory requirements. The document also outlines where IT policies fit within an organization's overall governance structure and lists examples of common IT policy topics such as security, network infrastructure, software, and email policies.