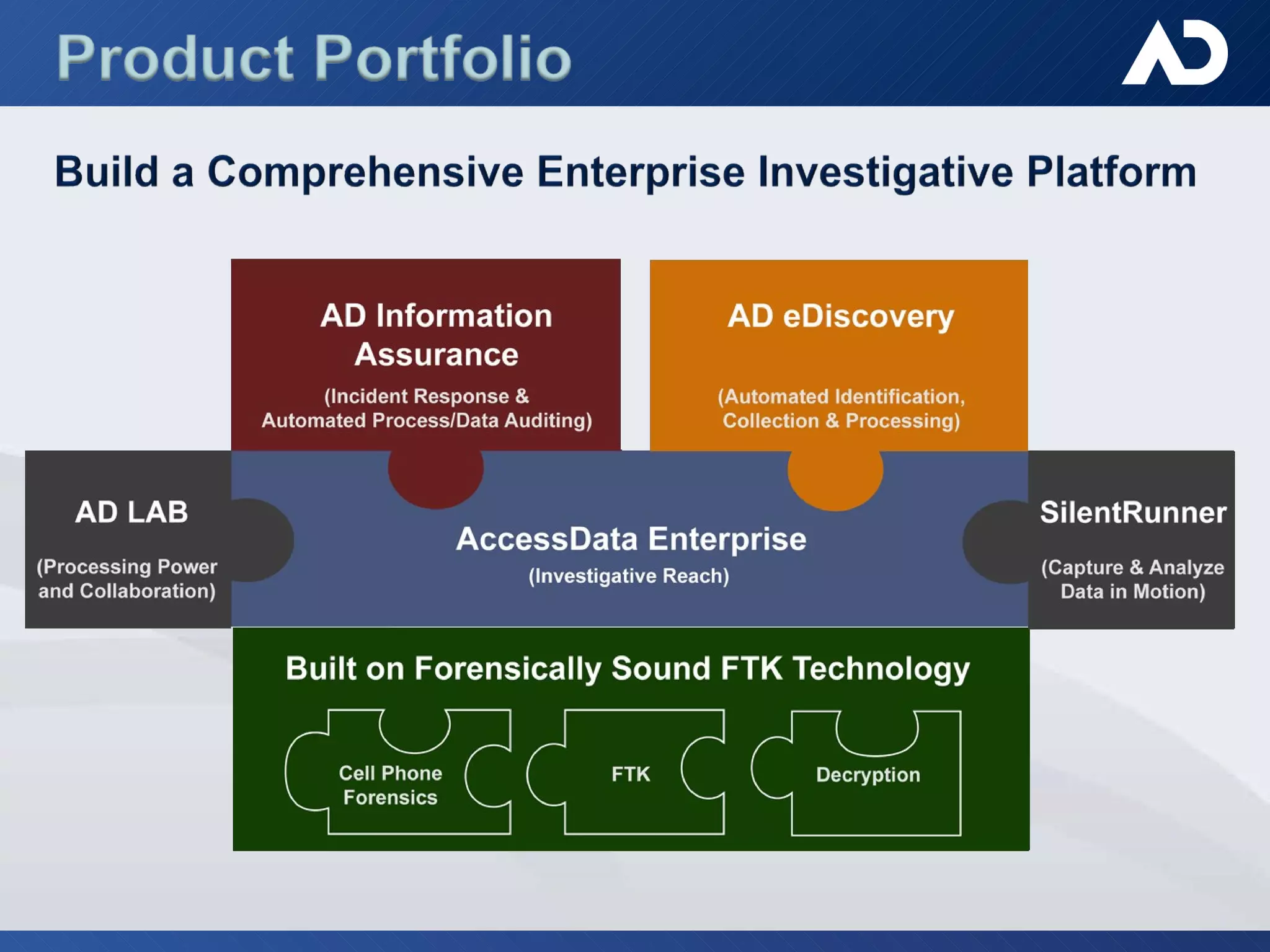
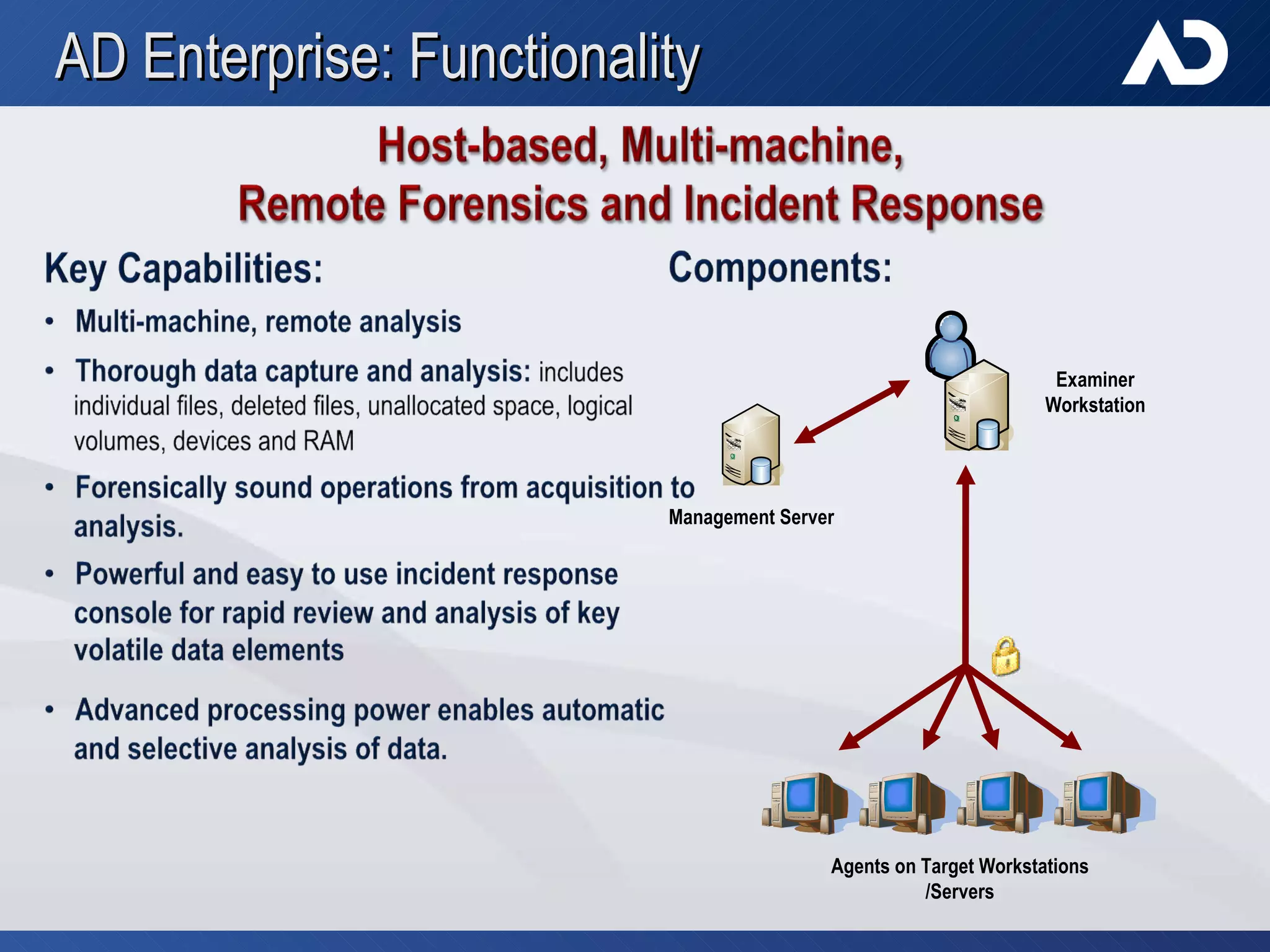
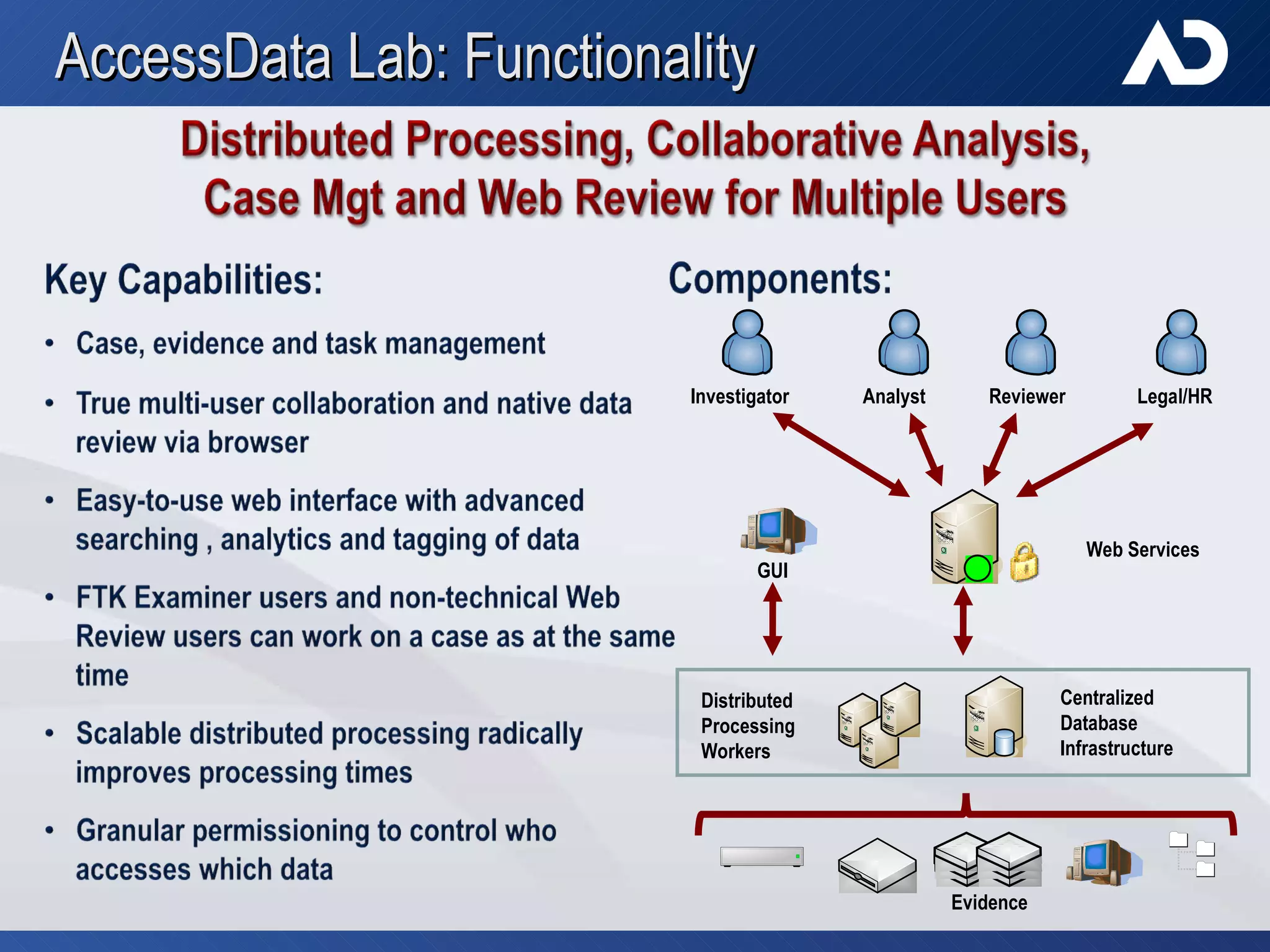
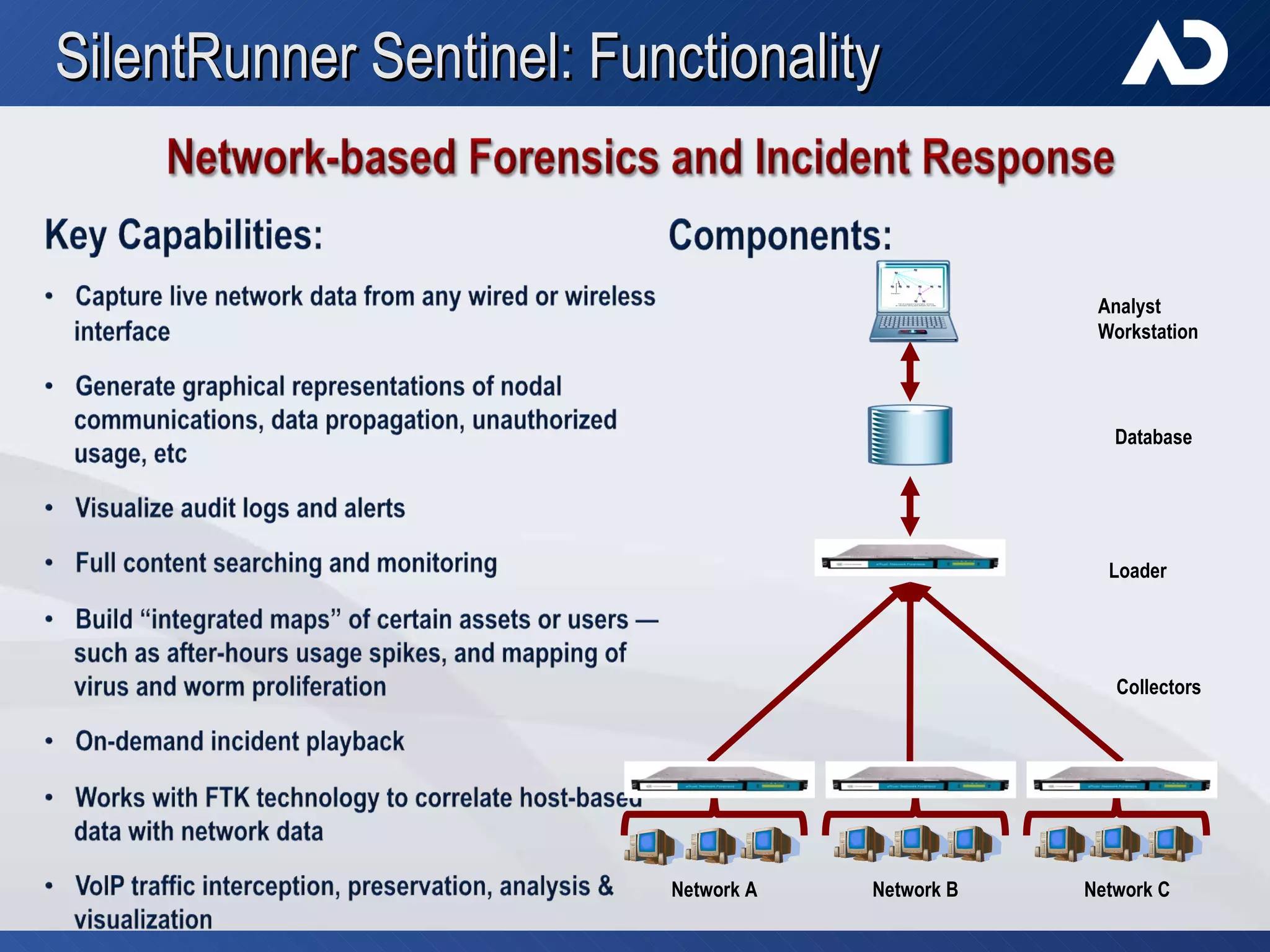
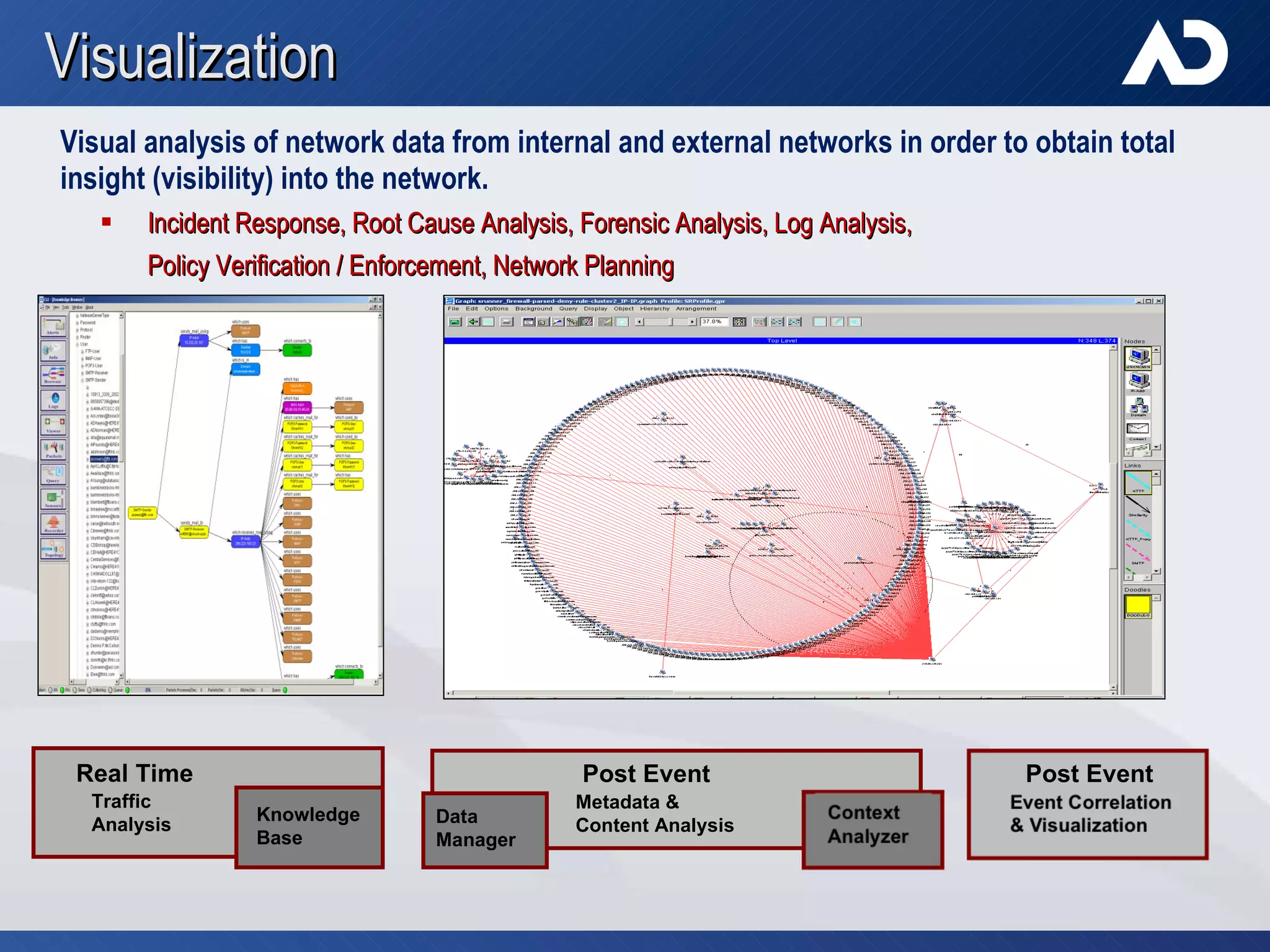
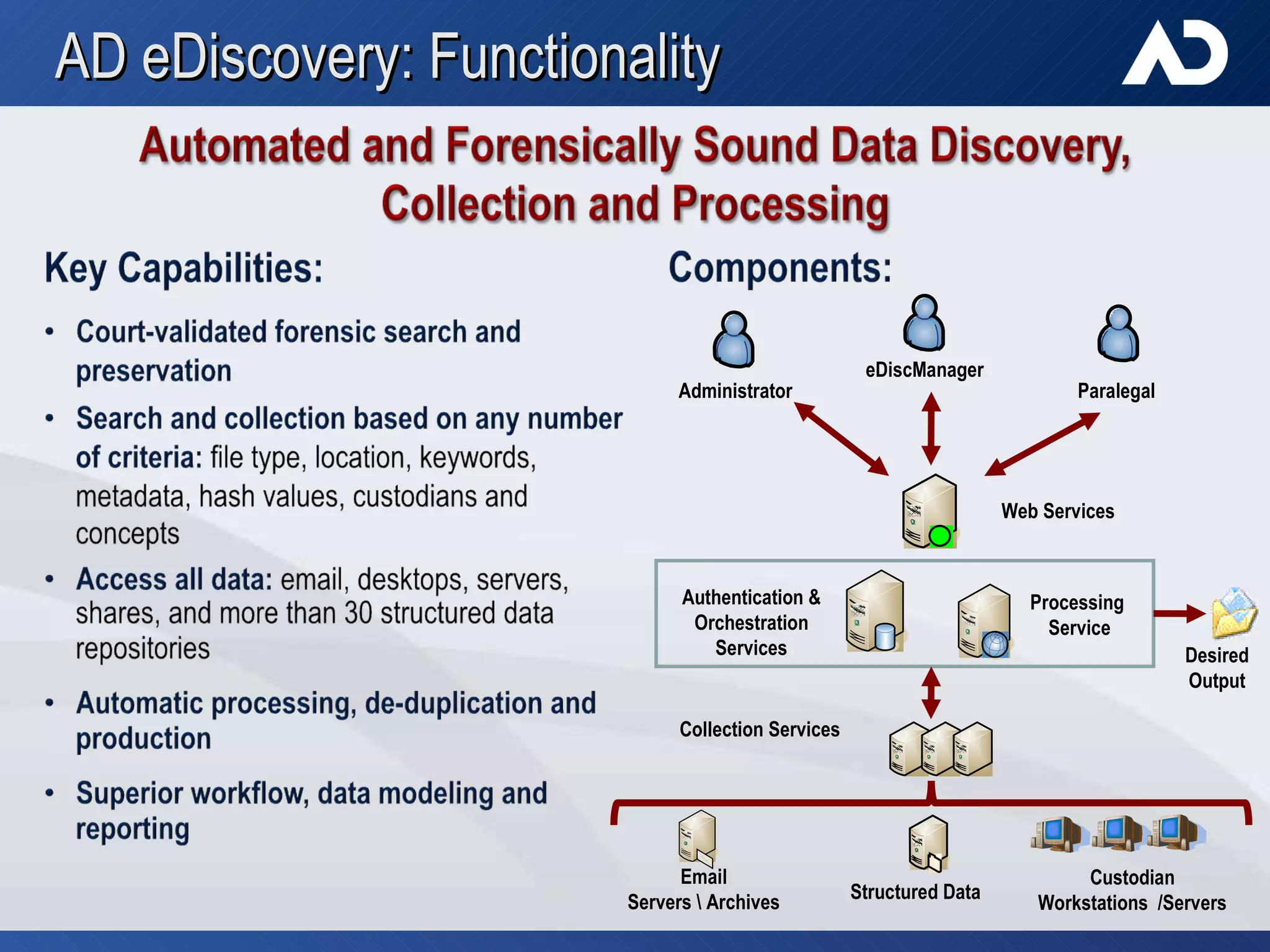
AccessData, founded in 1987 in Lindon, Utah, specializes in digital forensic tools, particularly the Forensic Toolkit (FTK), which is widely used for email analysis and digital investigation. The company trains over 6,000 individuals yearly and serves a diverse clientele, including federal agencies and major corporations, amidst the increasing complexity of data and cybercrime. Their solutions facilitate evidence collaboration, data automation, and comprehensive network analysis, addressing modern investigative challenges.