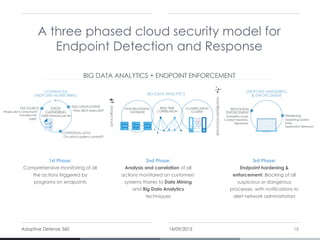
Panda Adaptive Defense 360 combines endpoint protection (EPP) and endpoint detection & response (EDR) to enhance security by classifying all running processes and constantly monitoring for suspicious behavior, ensuring comprehensive protection against cyber threats. It enables proactive detection and automated remediation while minimizing operational friction, allowing organizations to maintain productivity during security measures. This innovative solution has demonstrated significant effectiveness, blocking 100% of malware during trials and providing extensive visibility into endpoint activity.