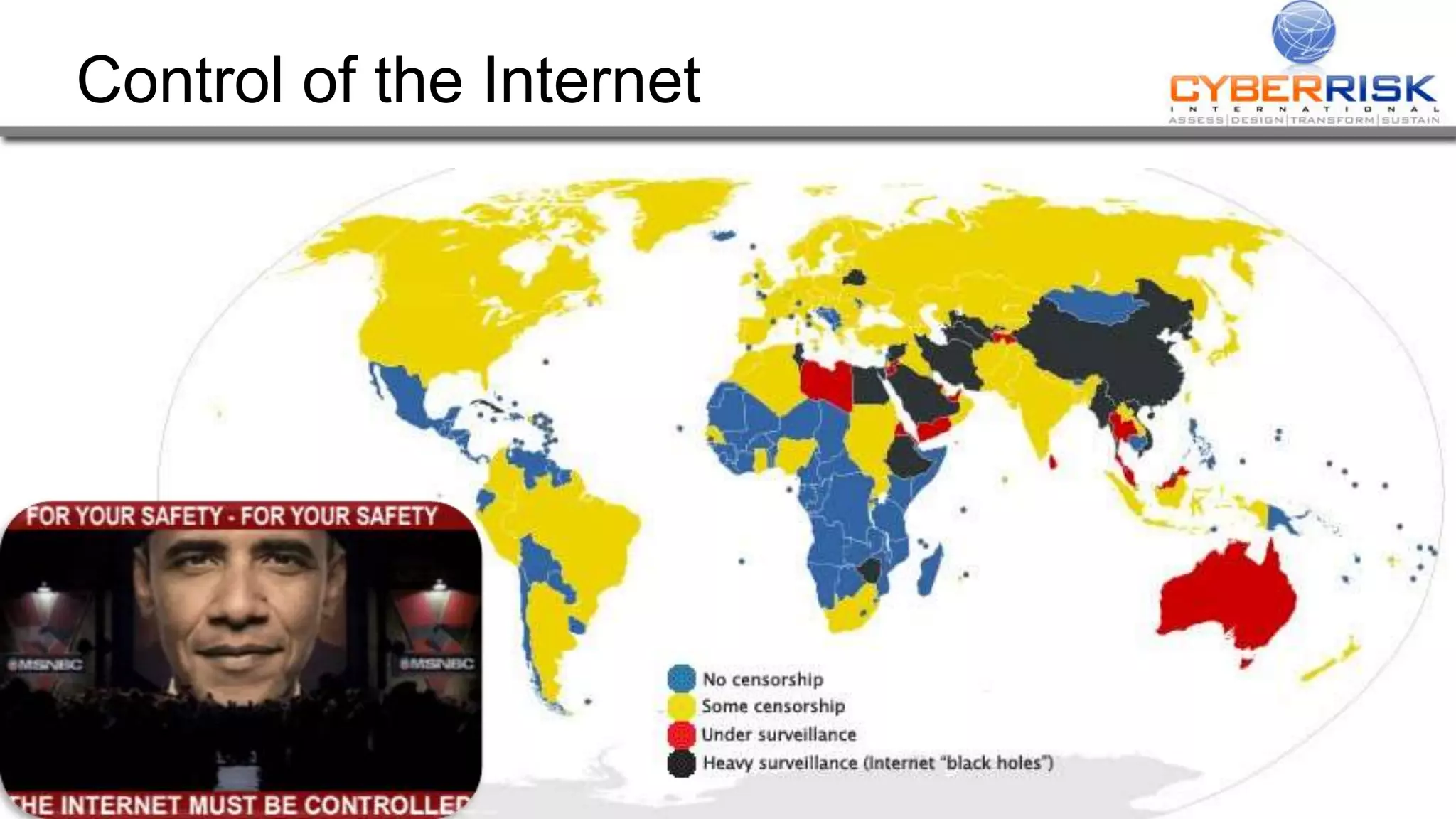
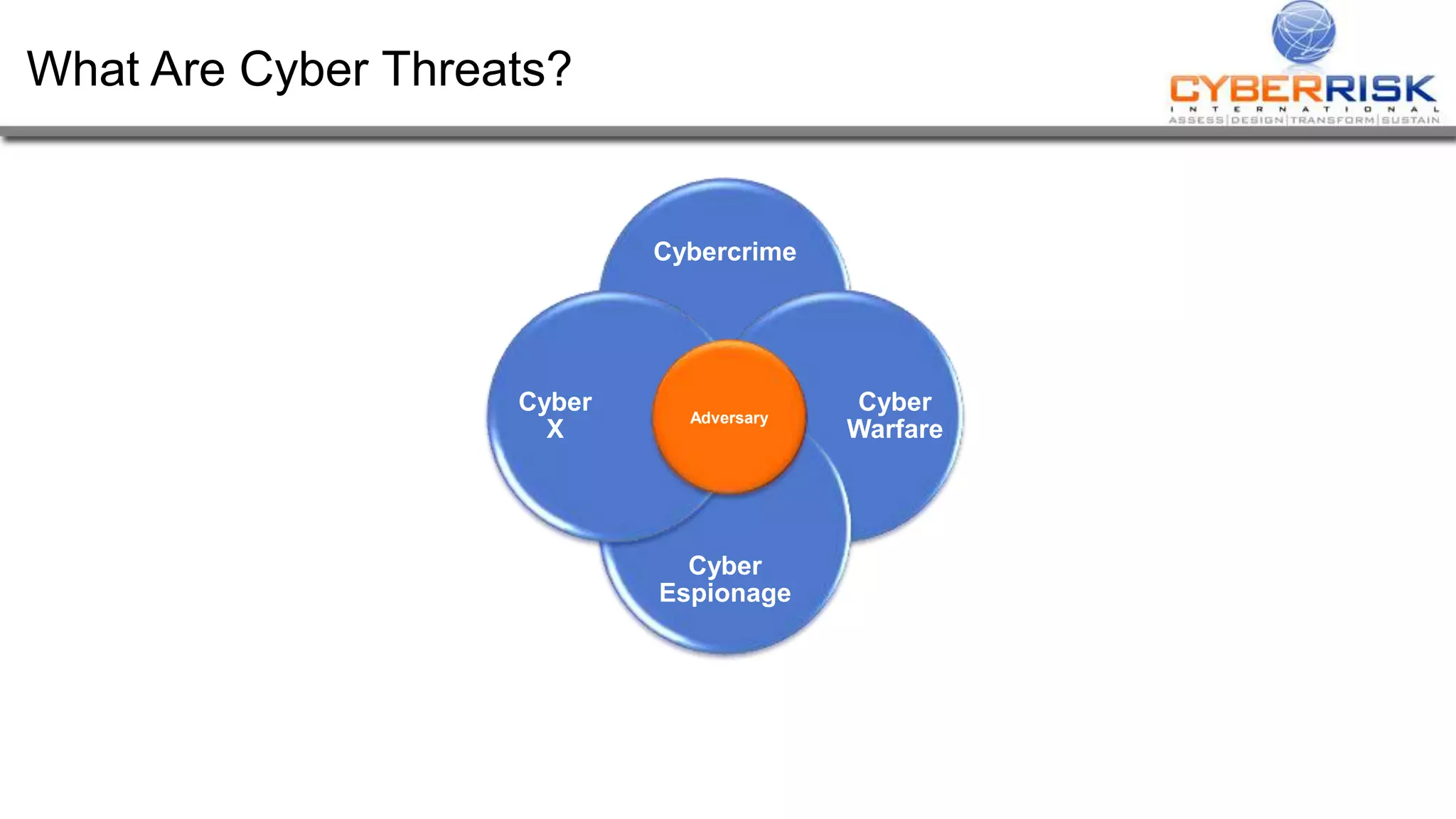
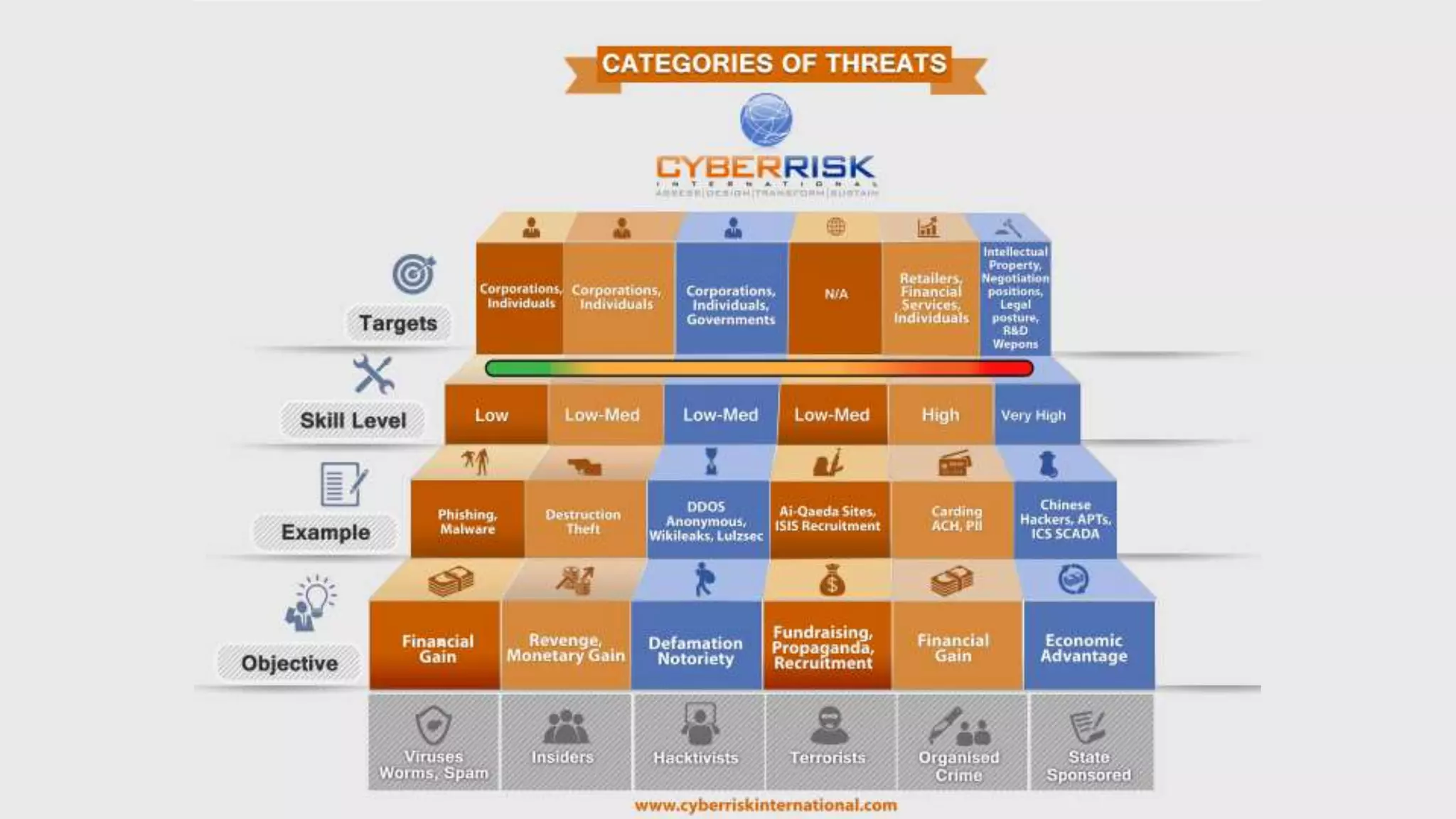
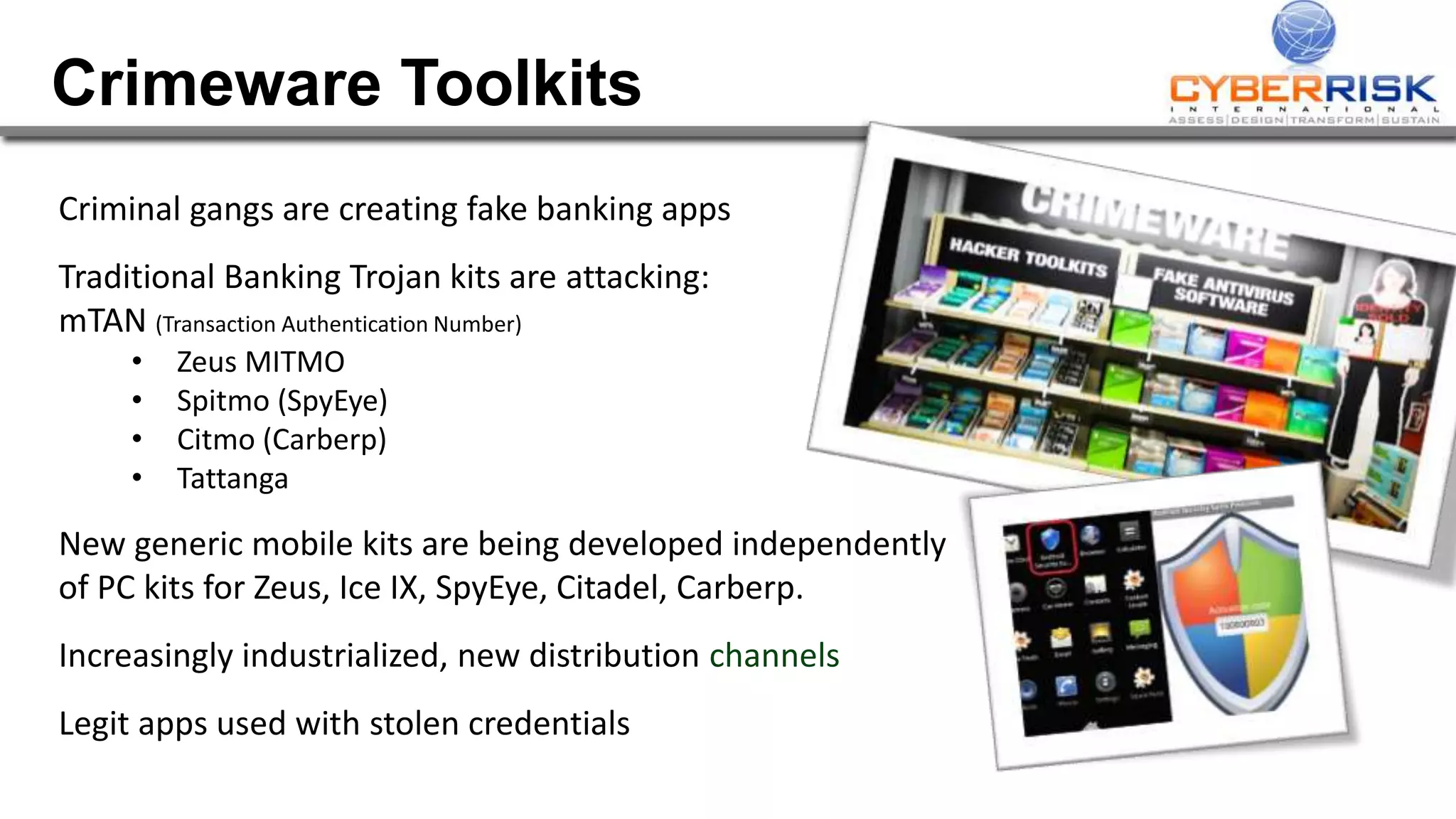
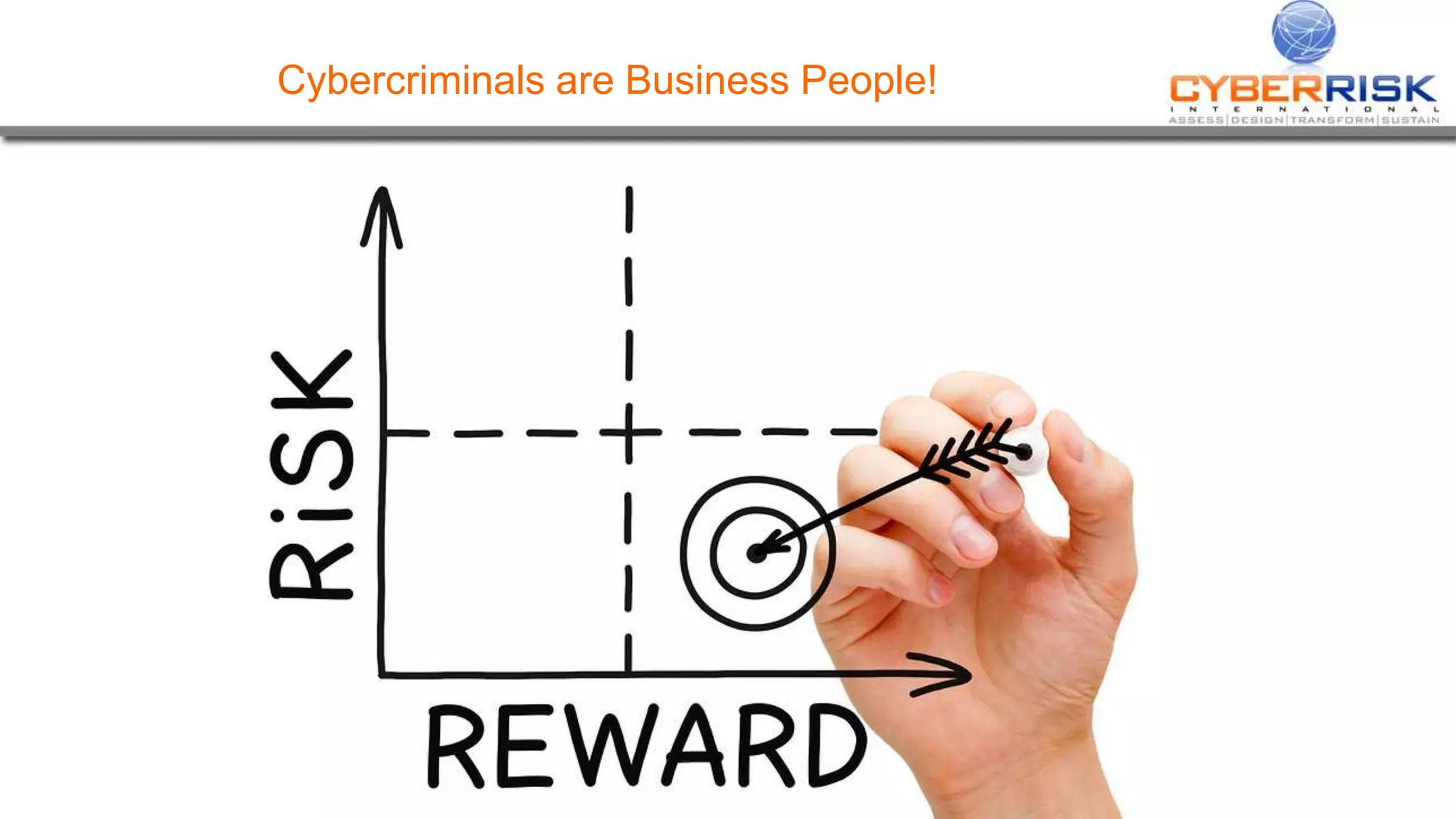
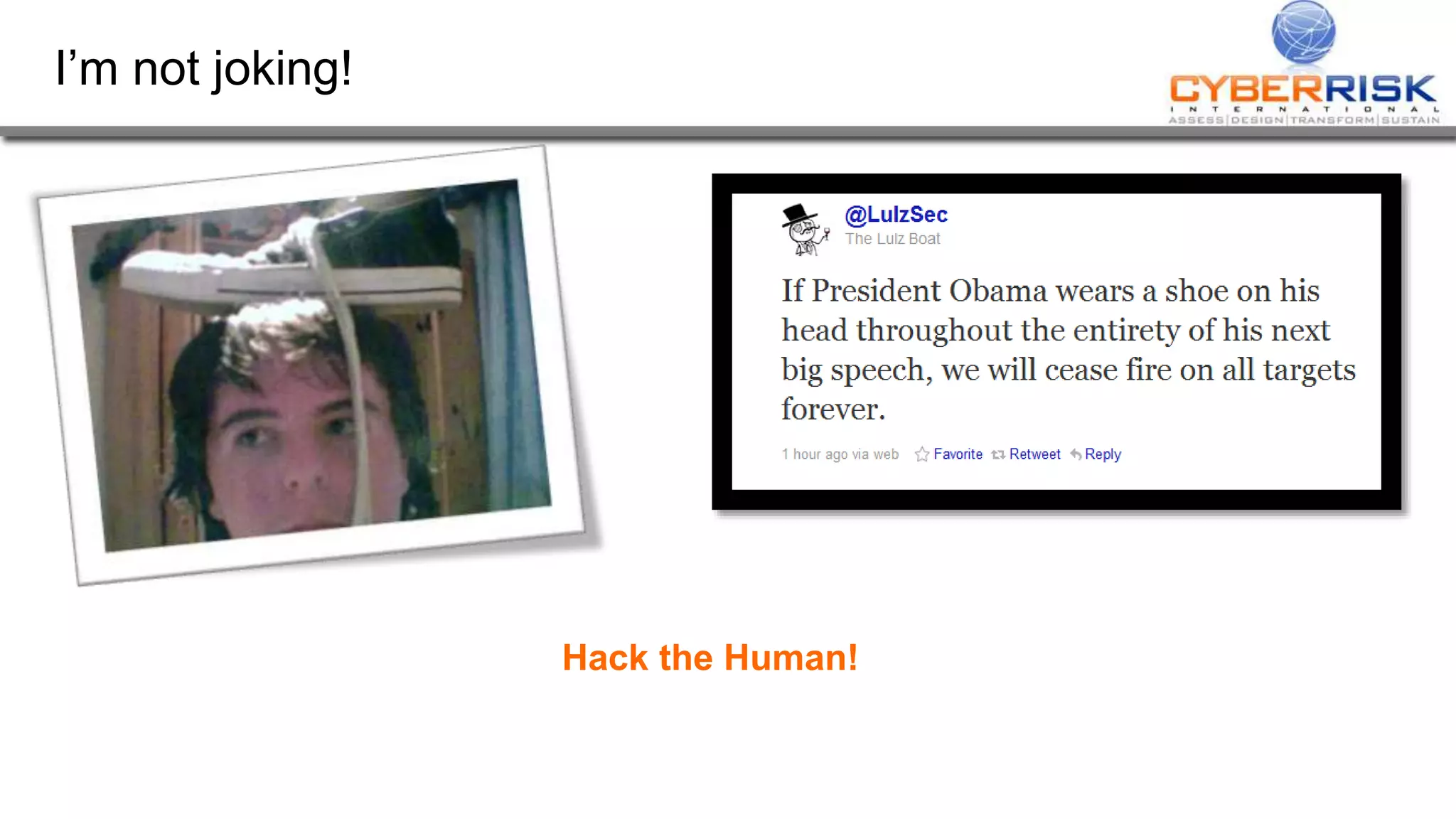
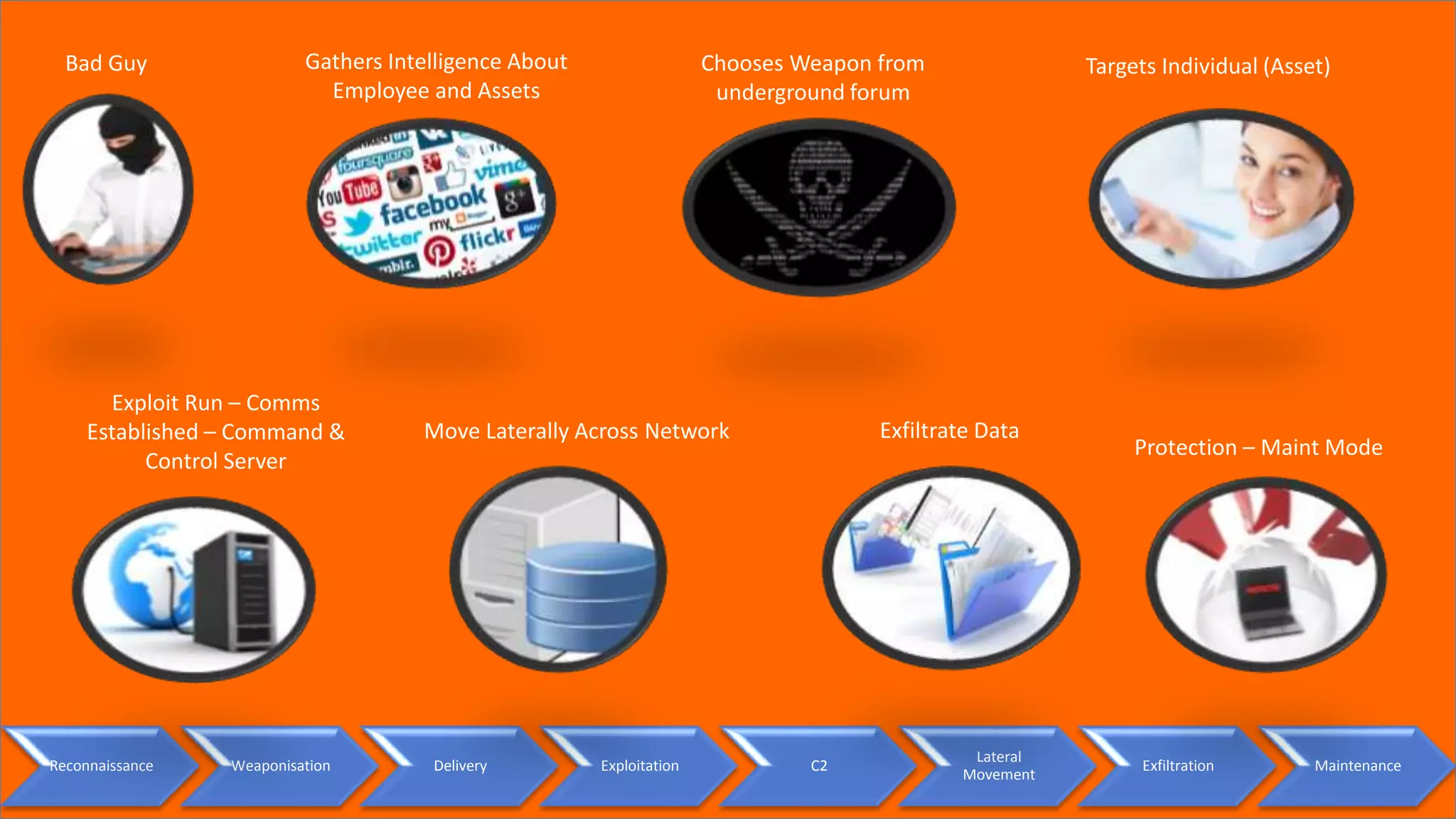
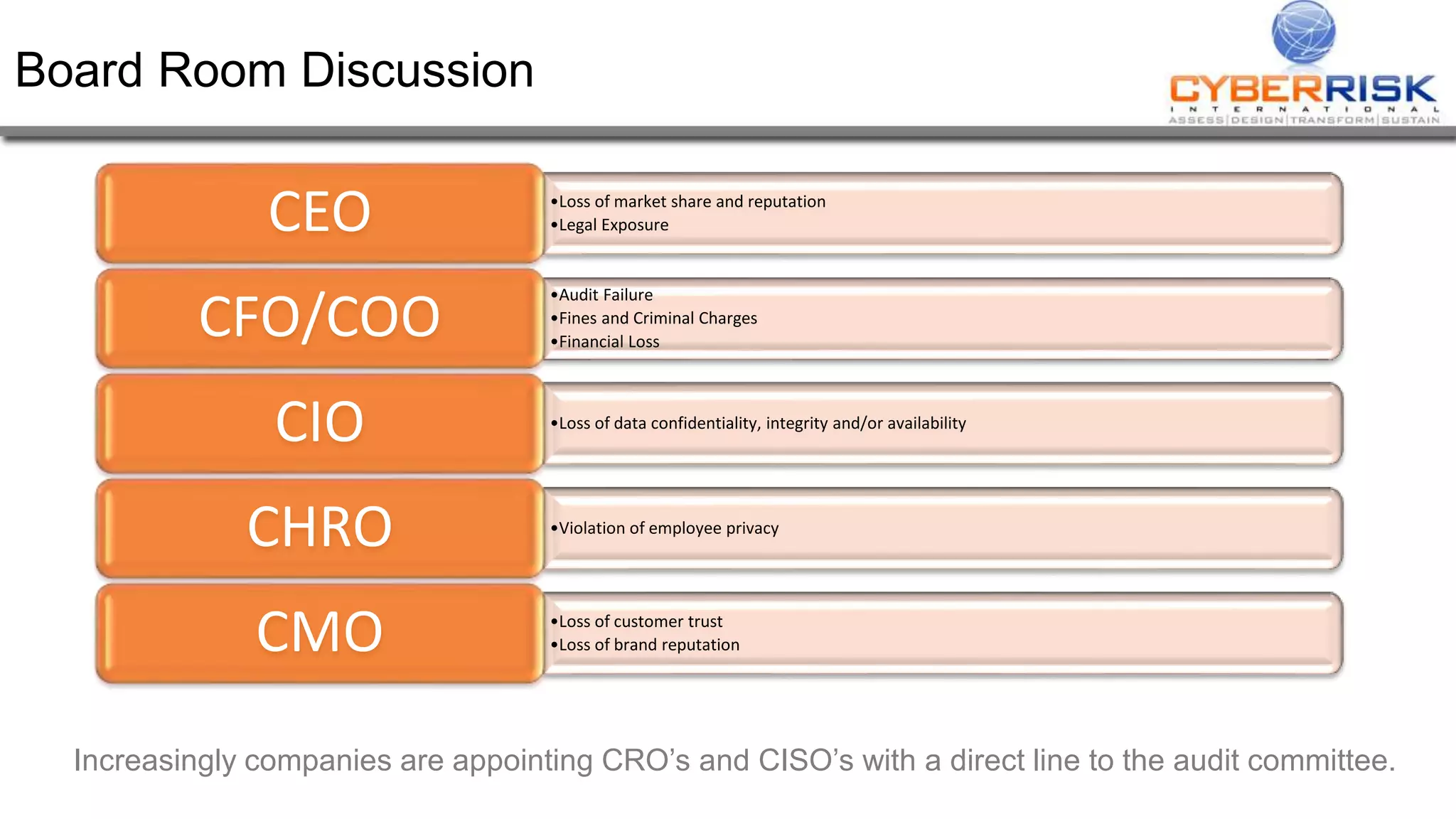
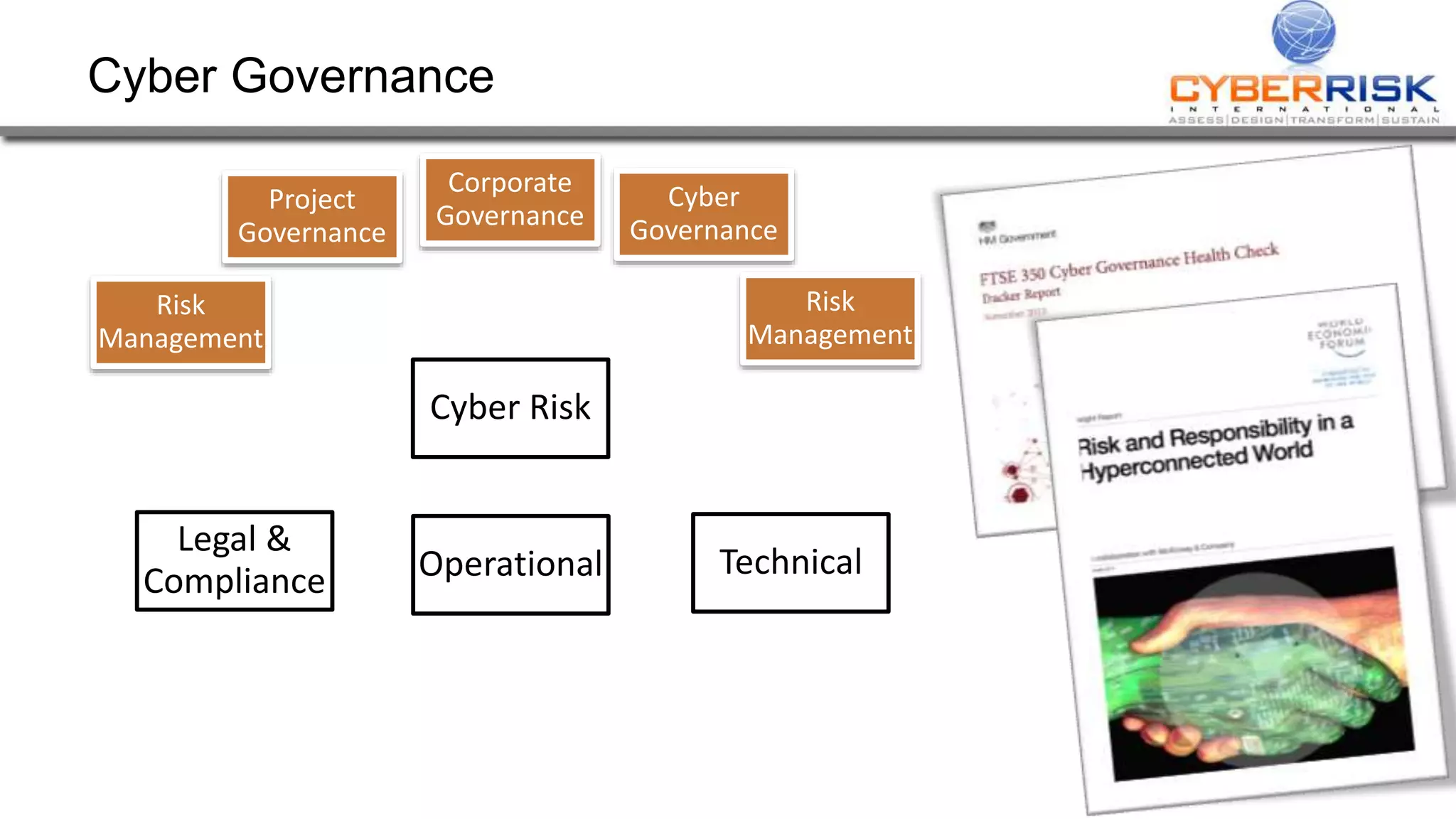
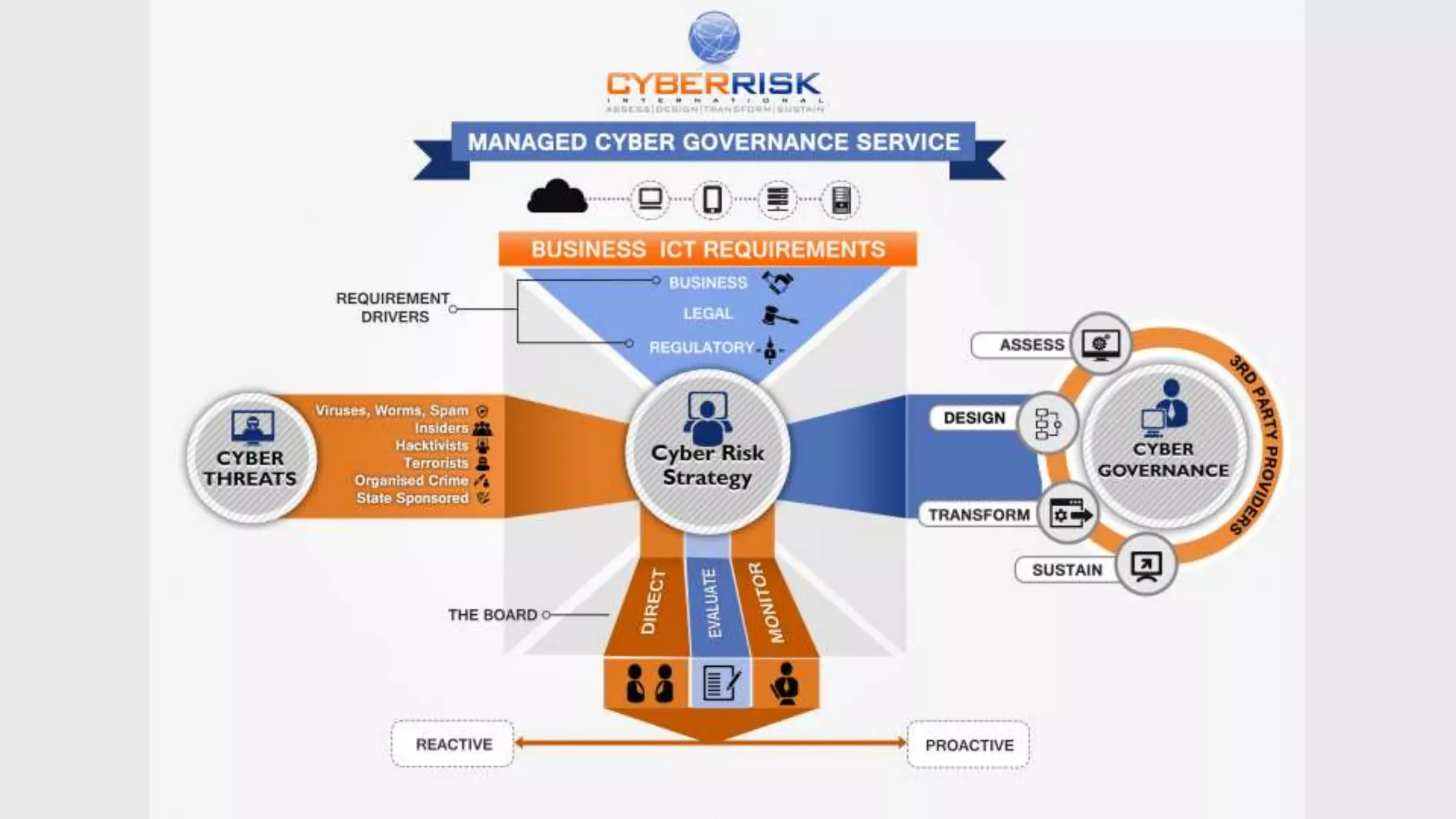
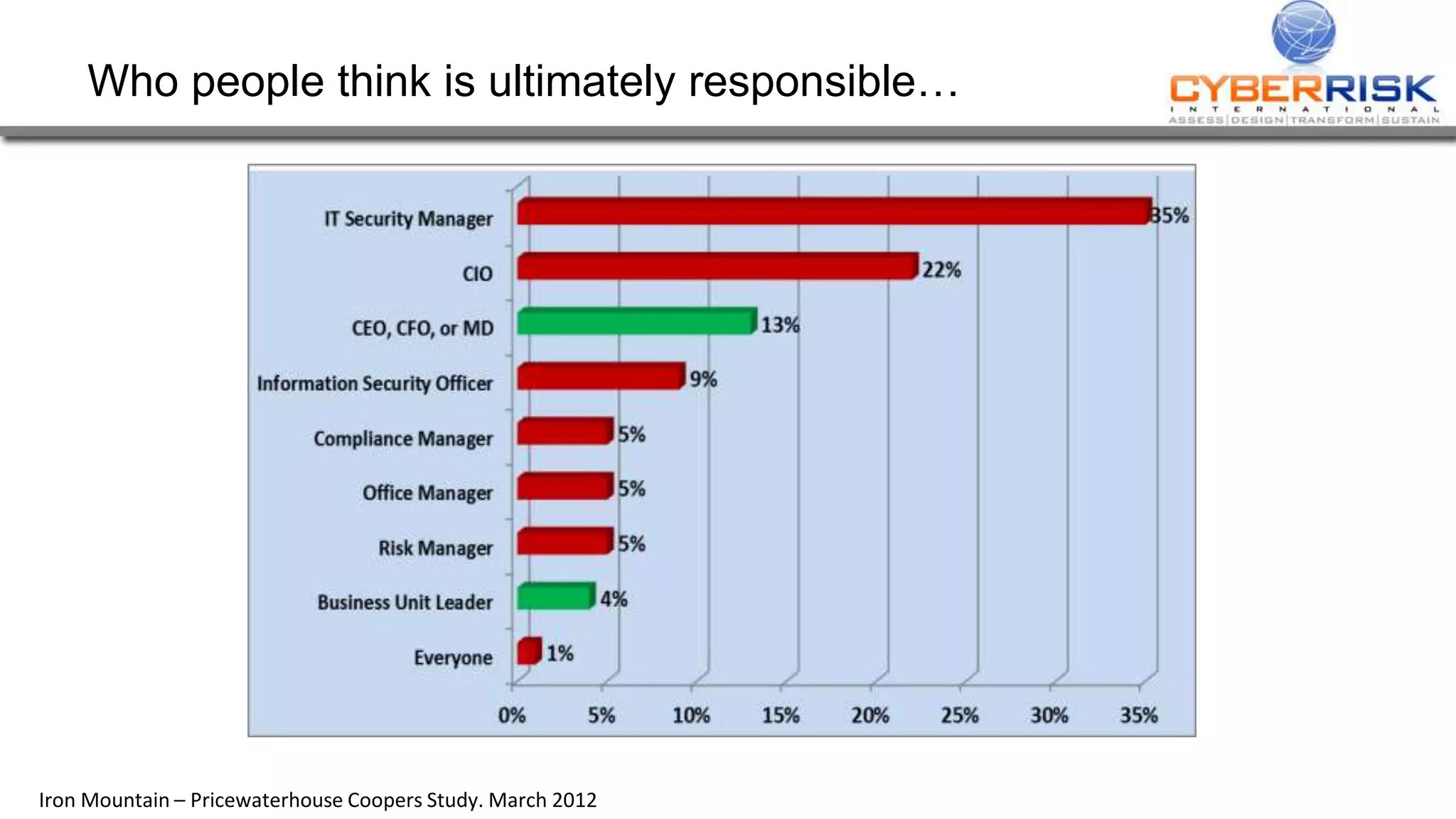
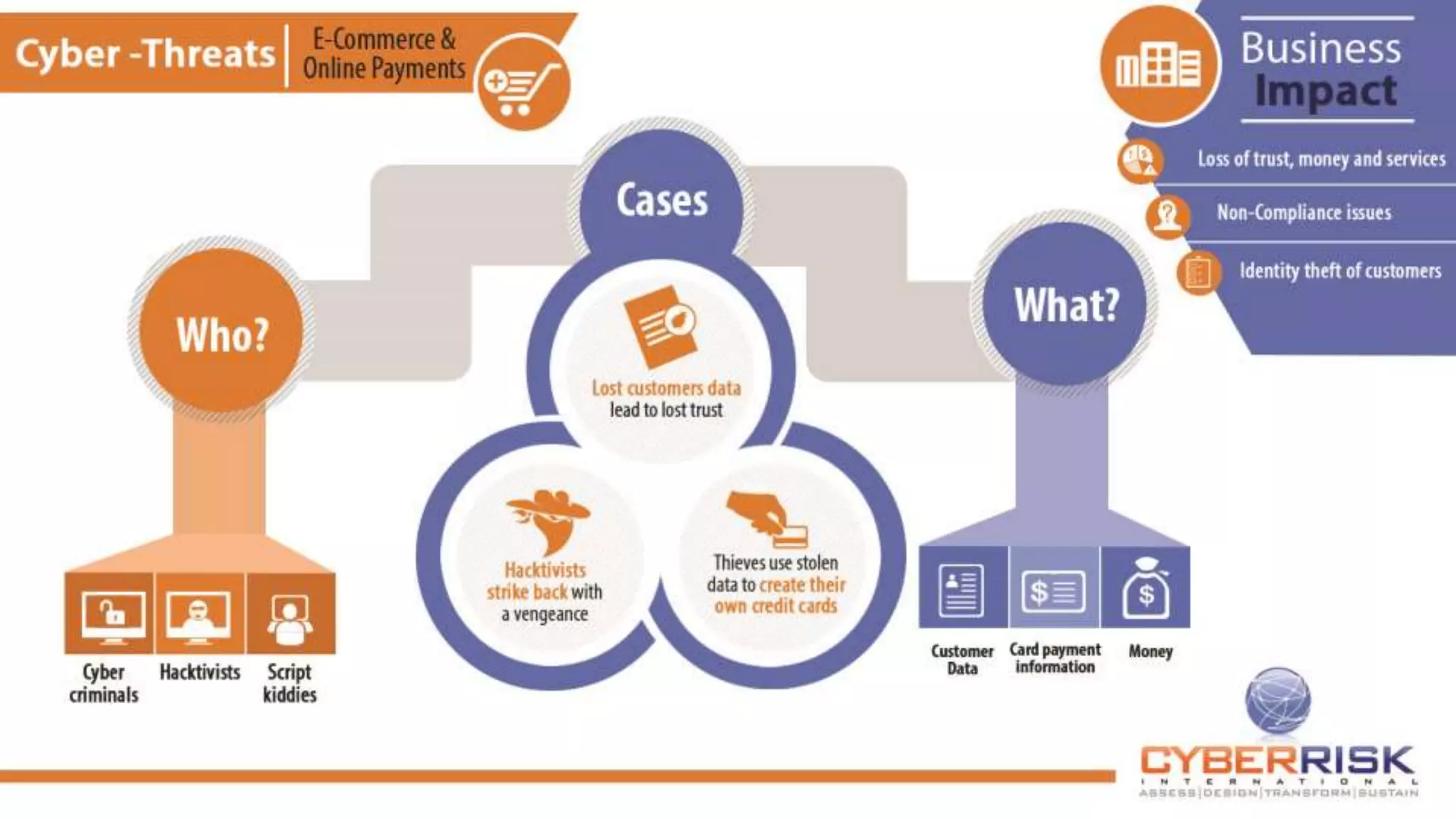
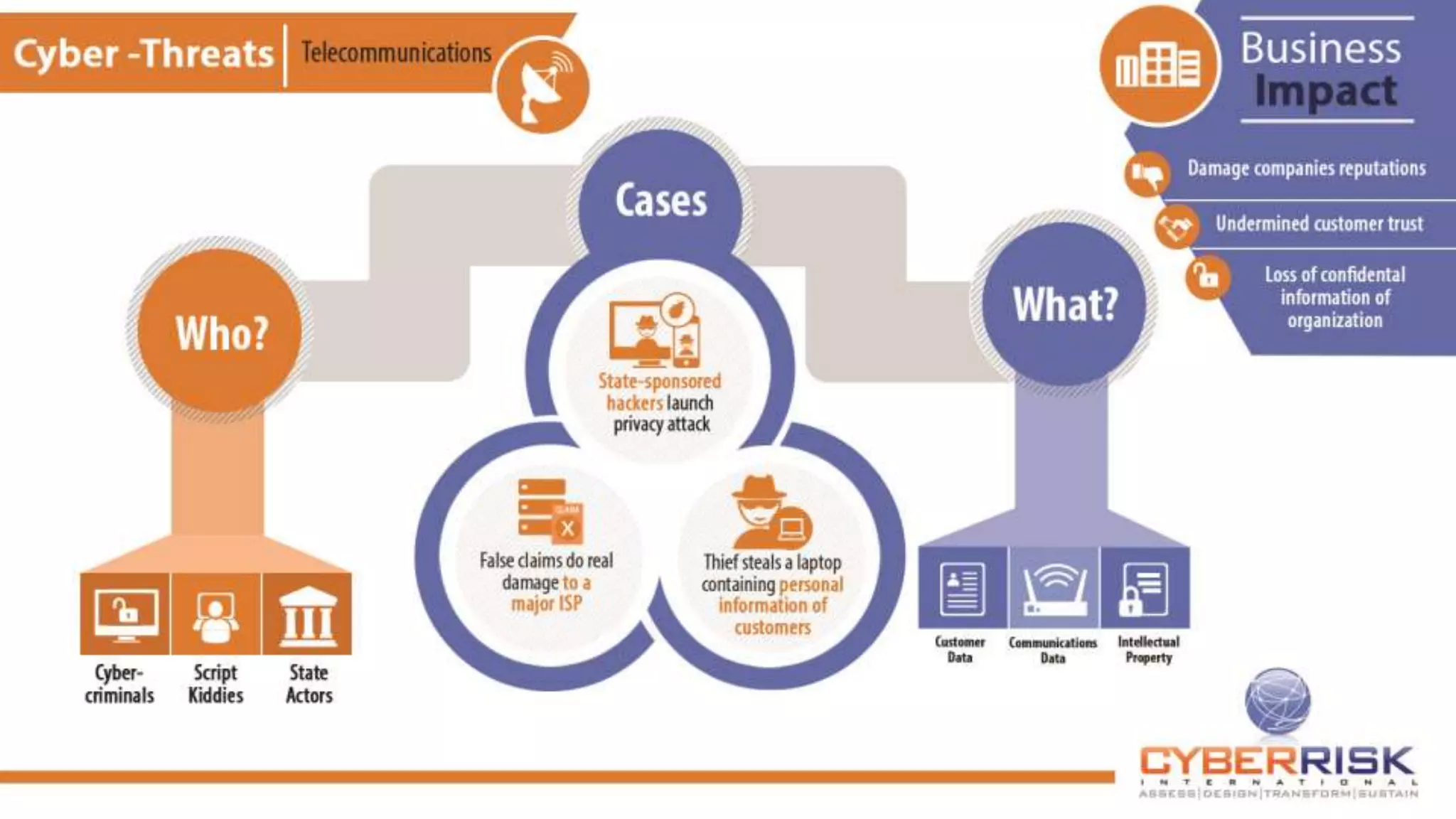
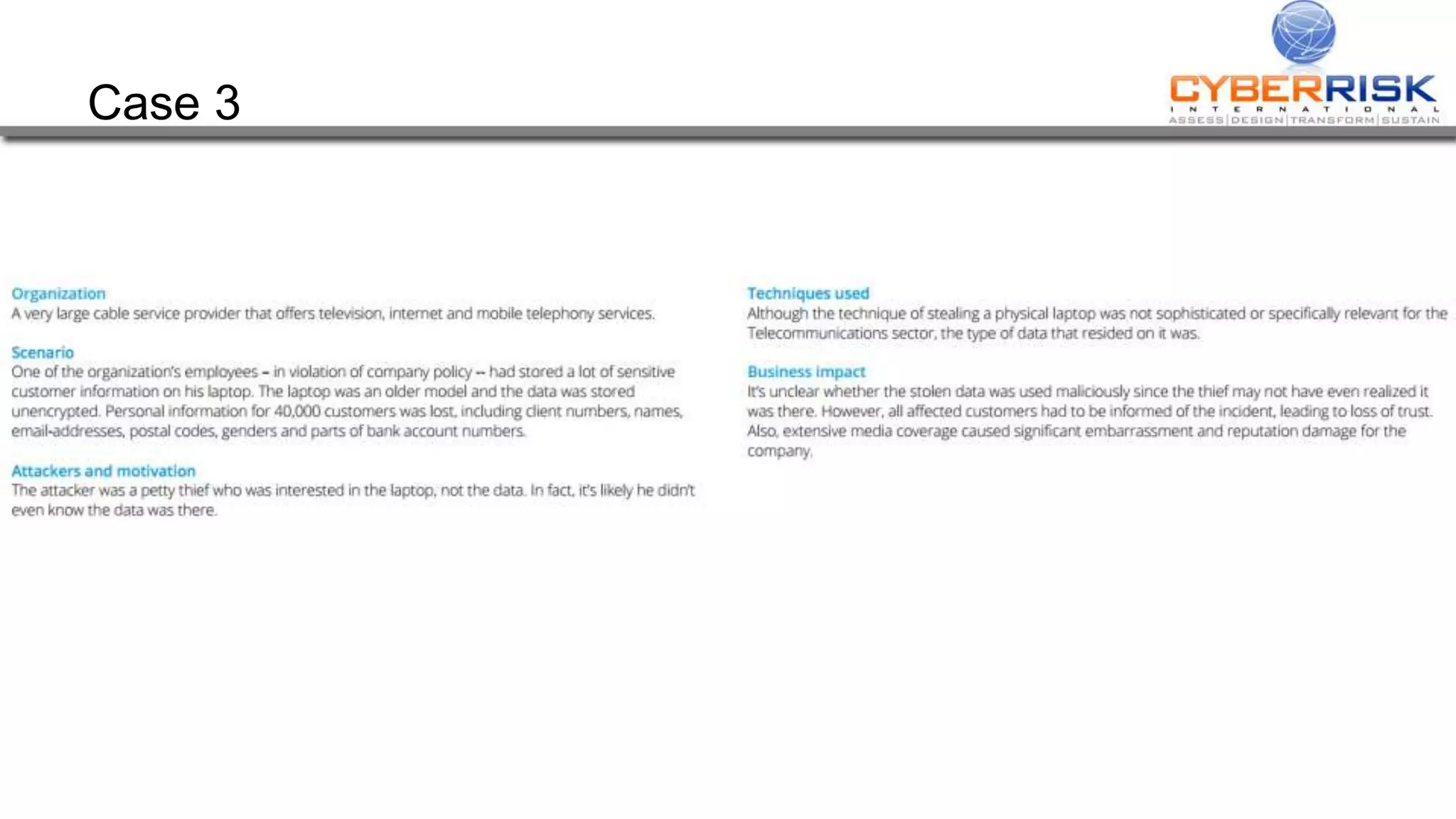
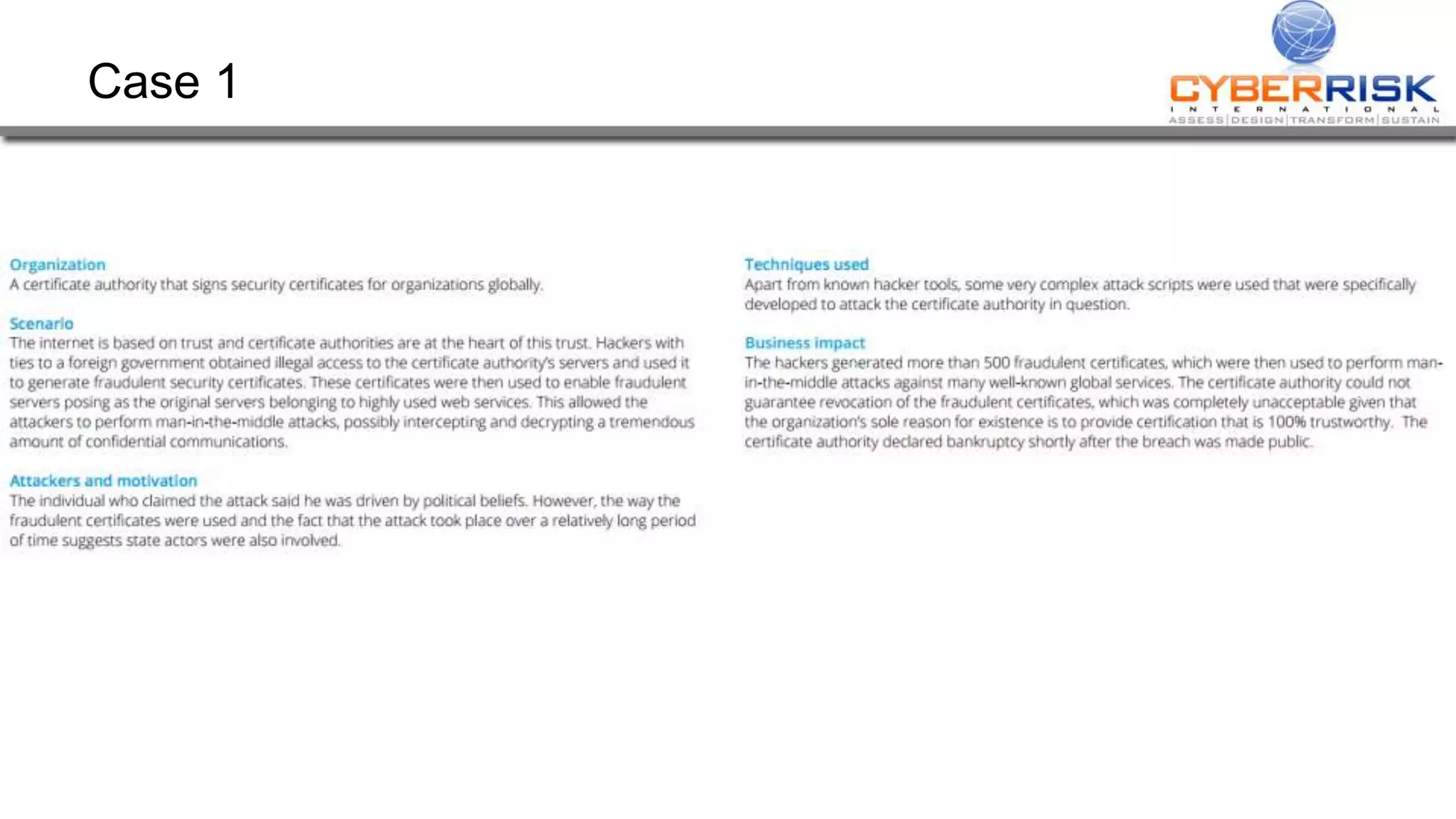
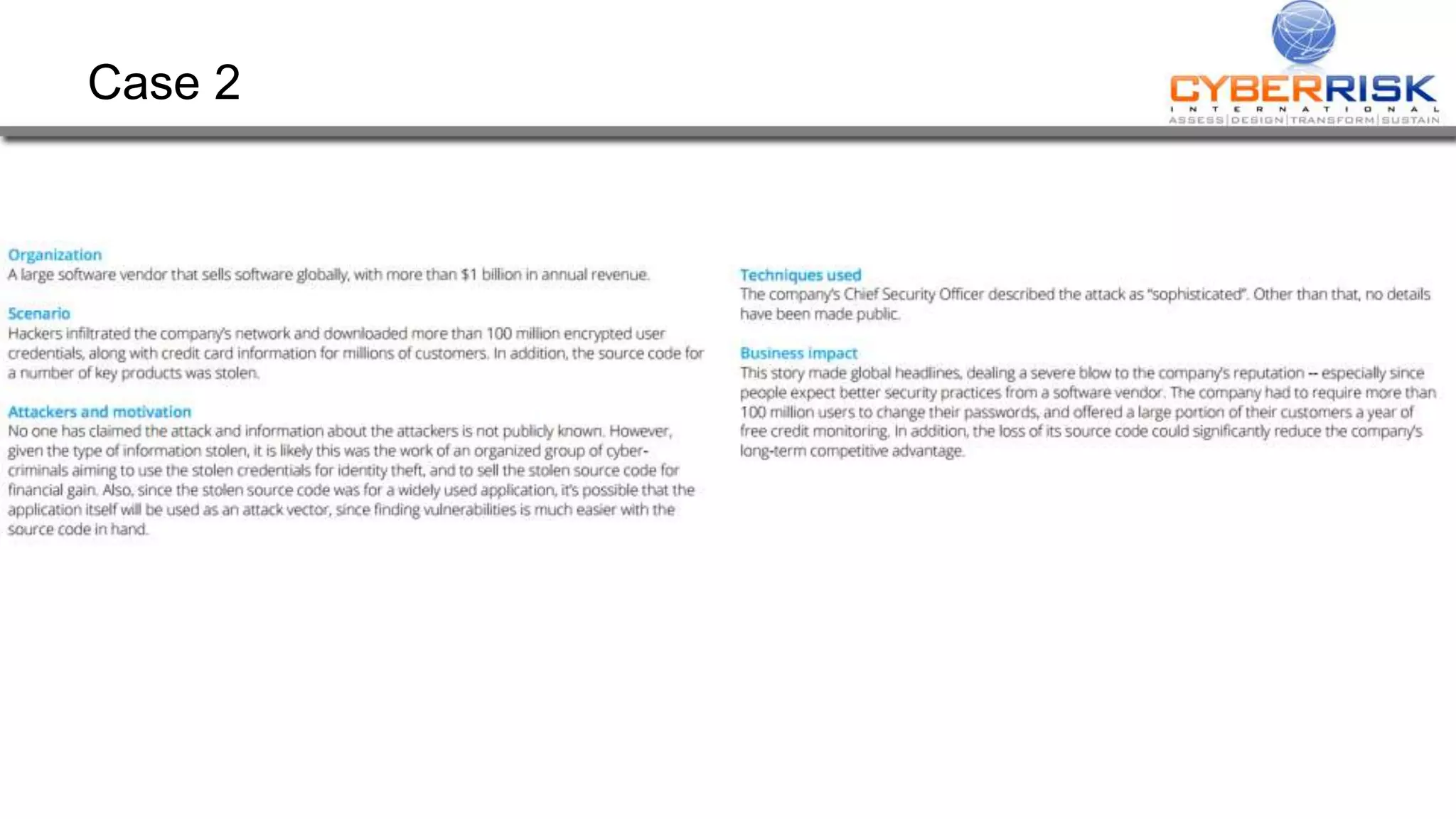
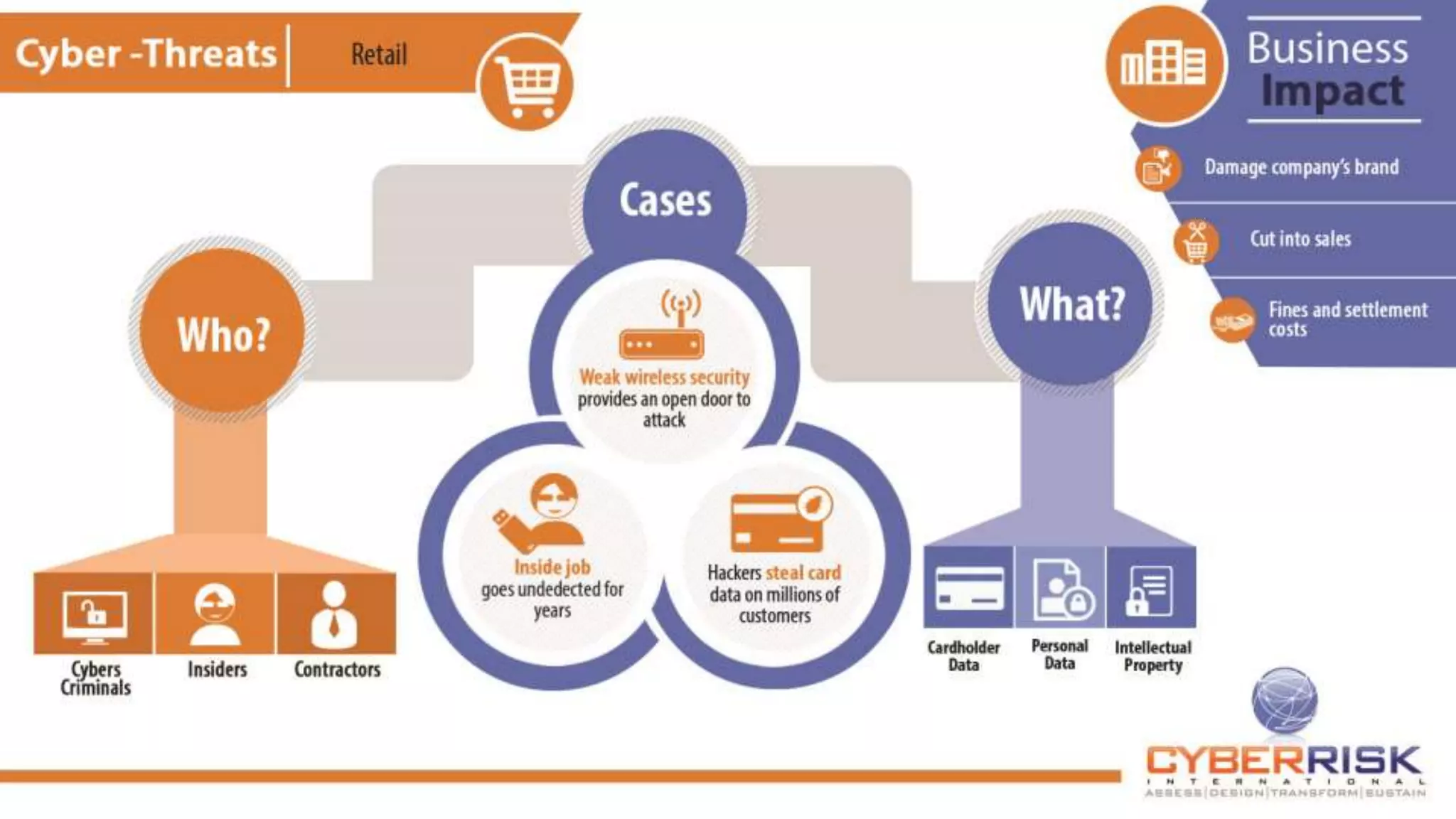
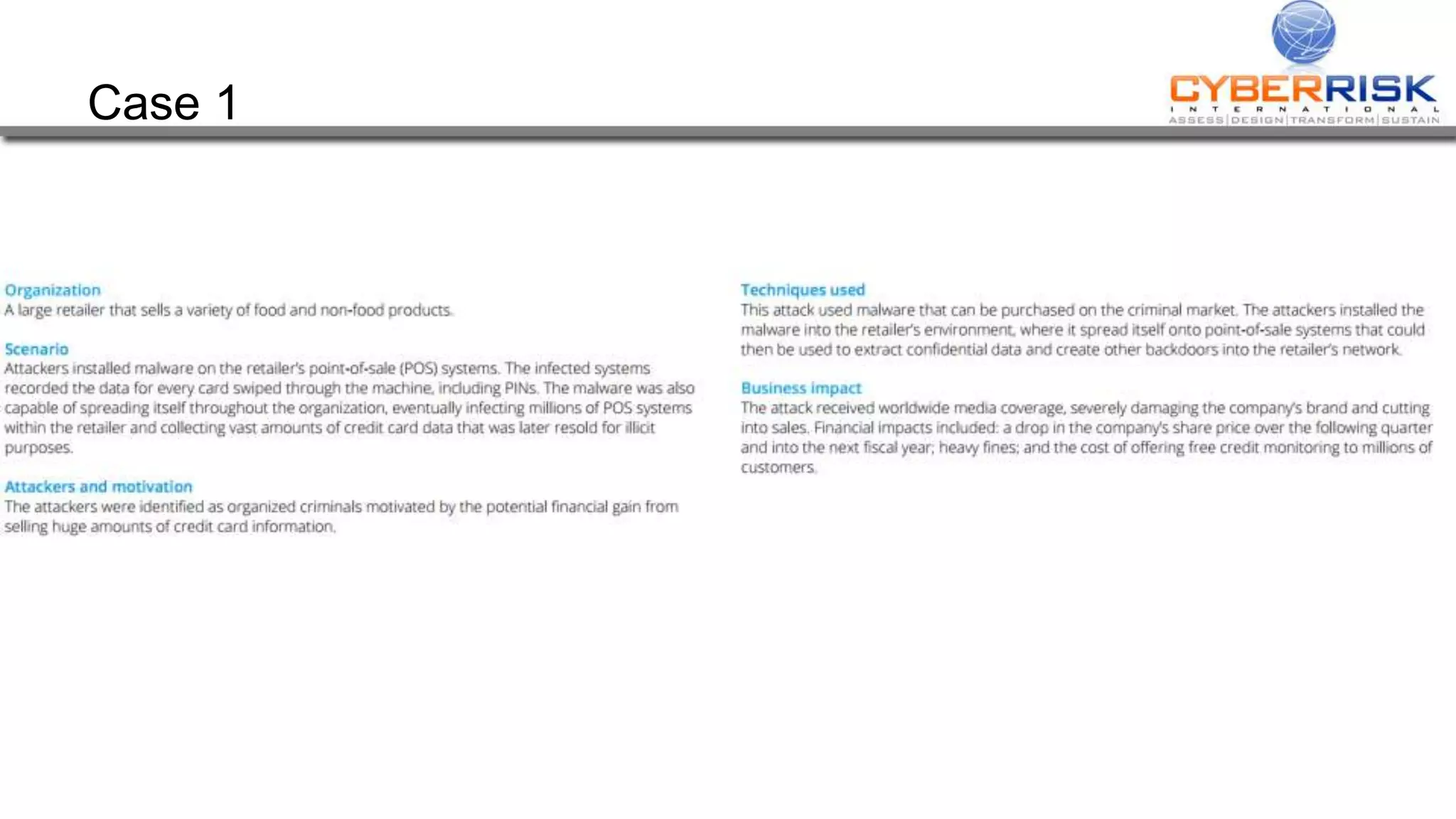
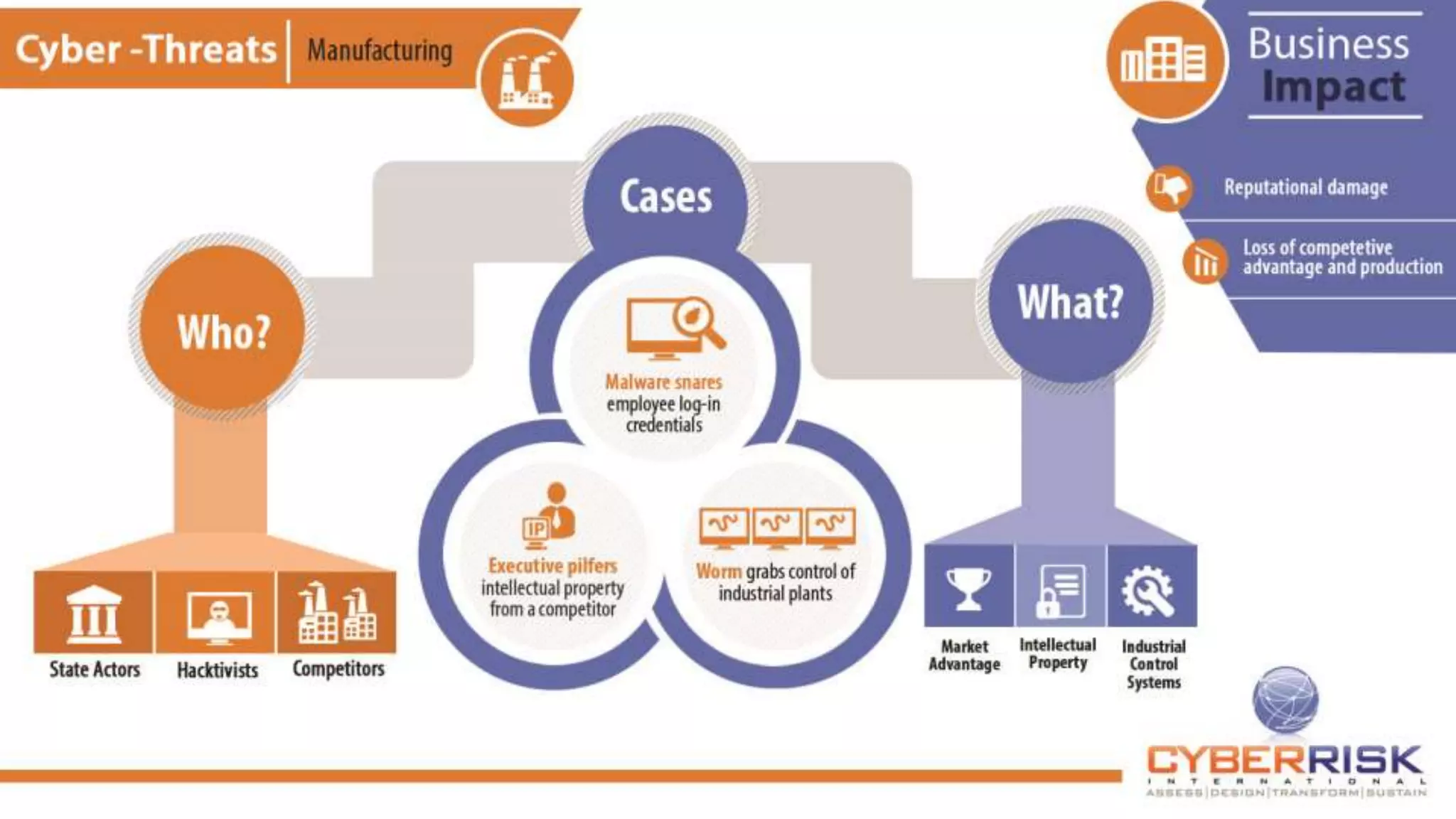
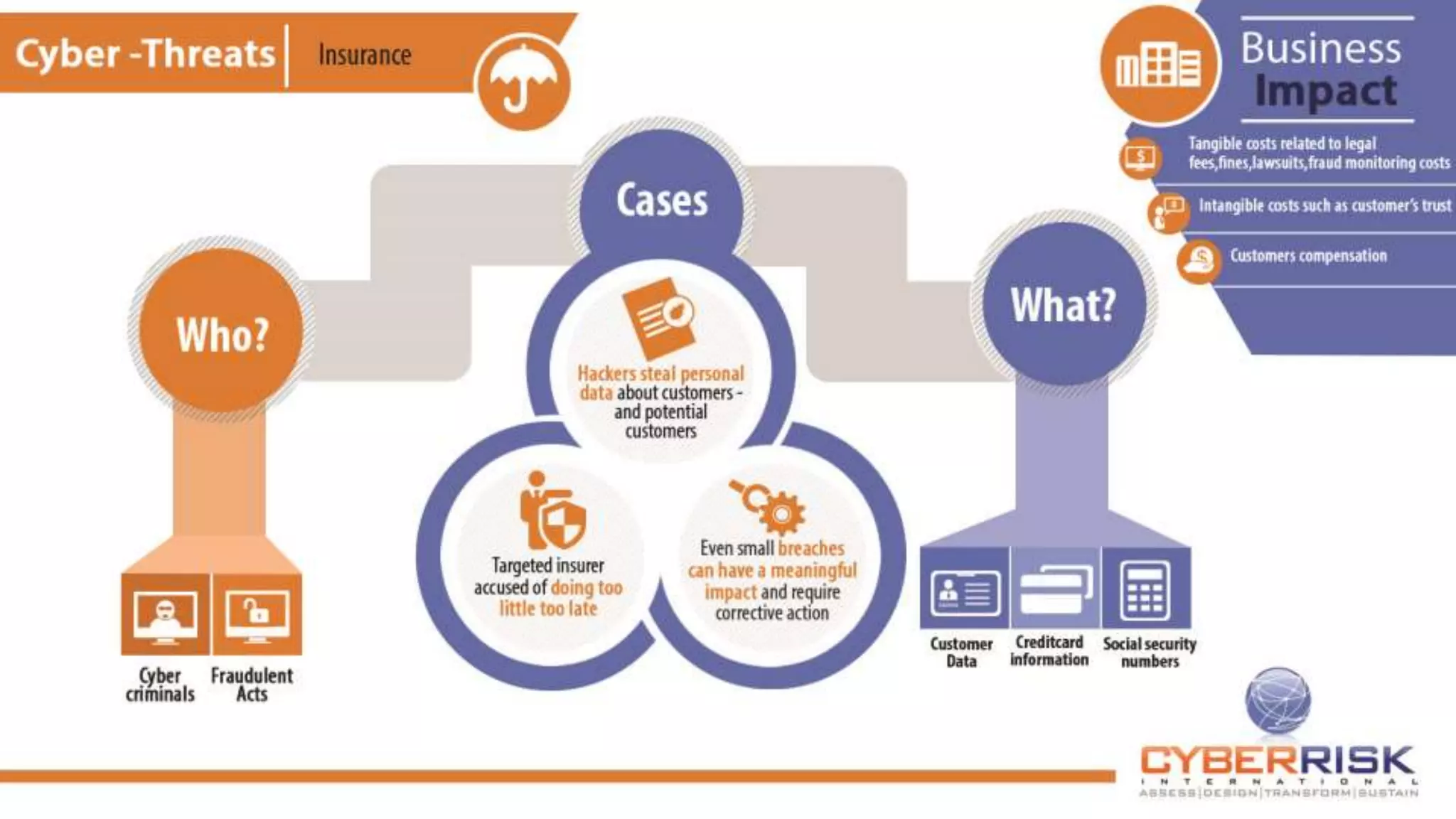
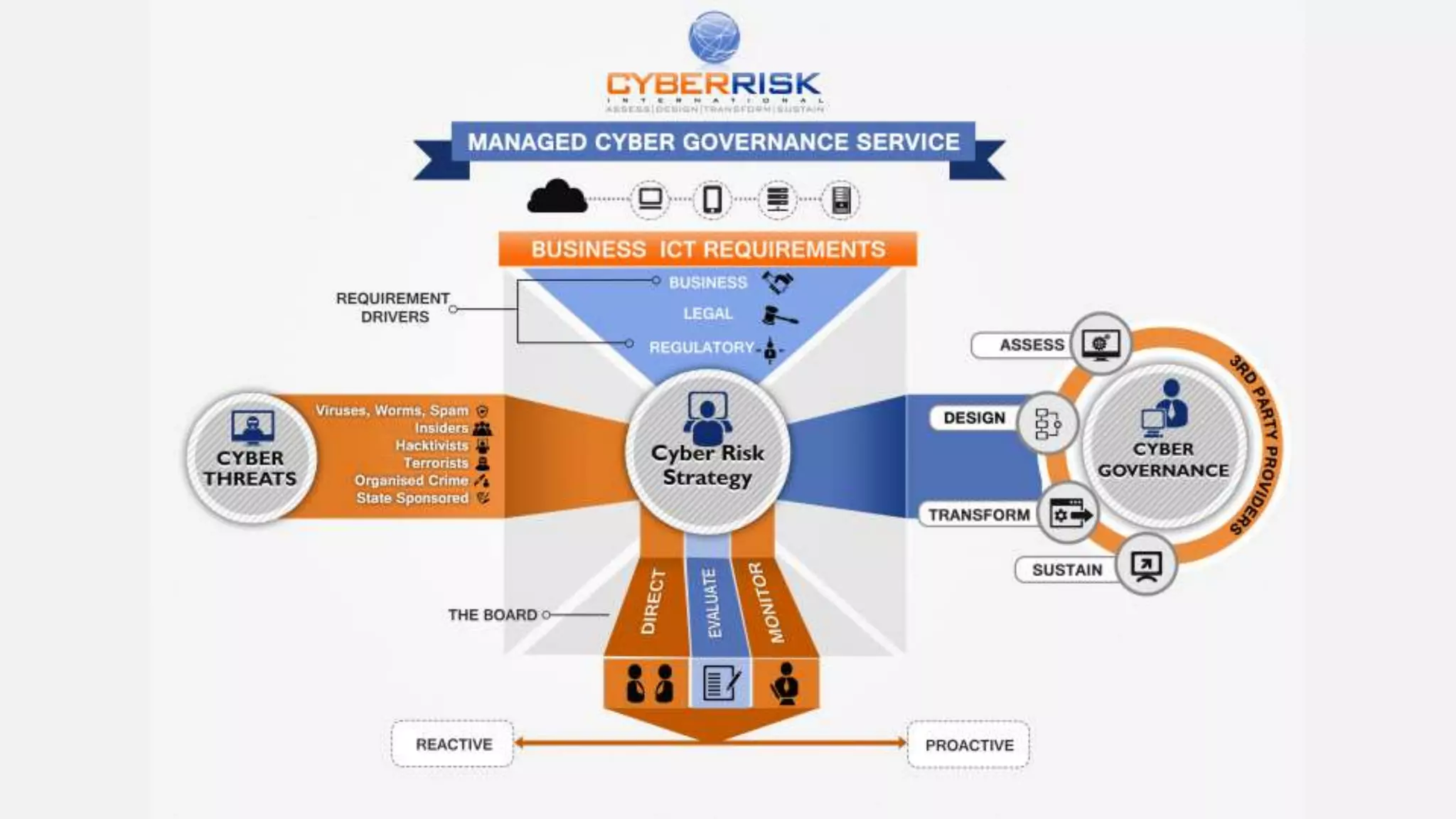
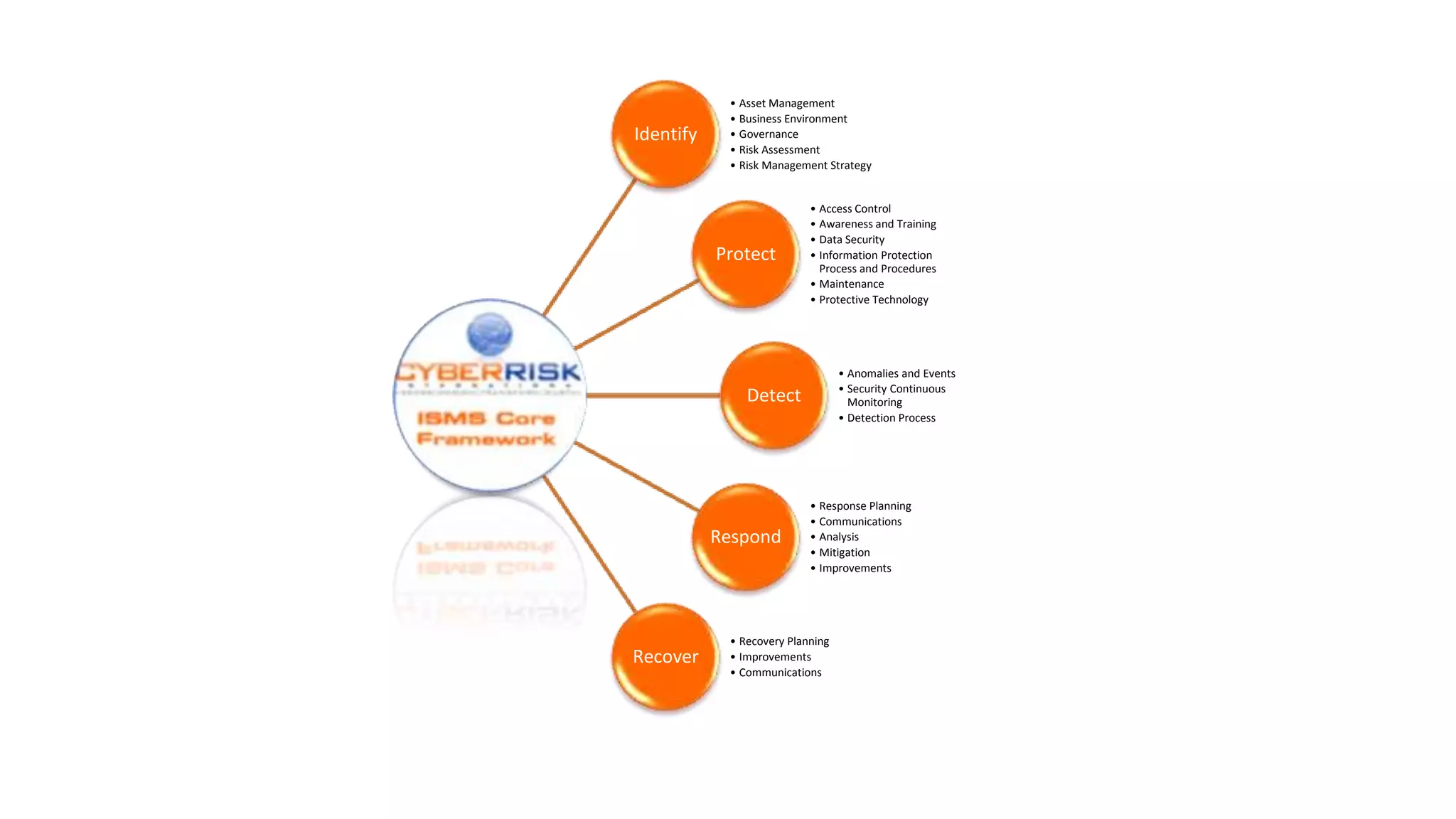
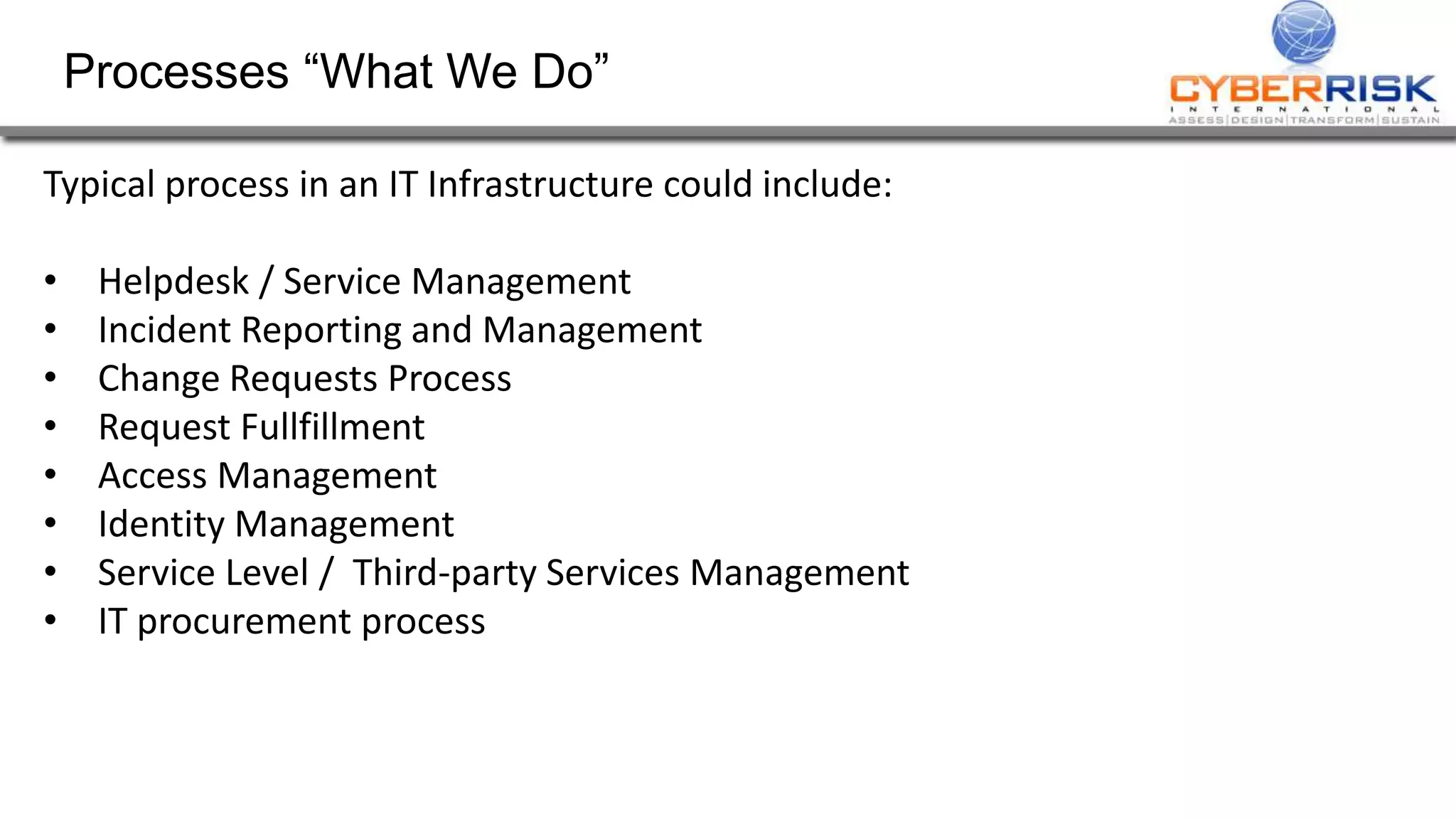
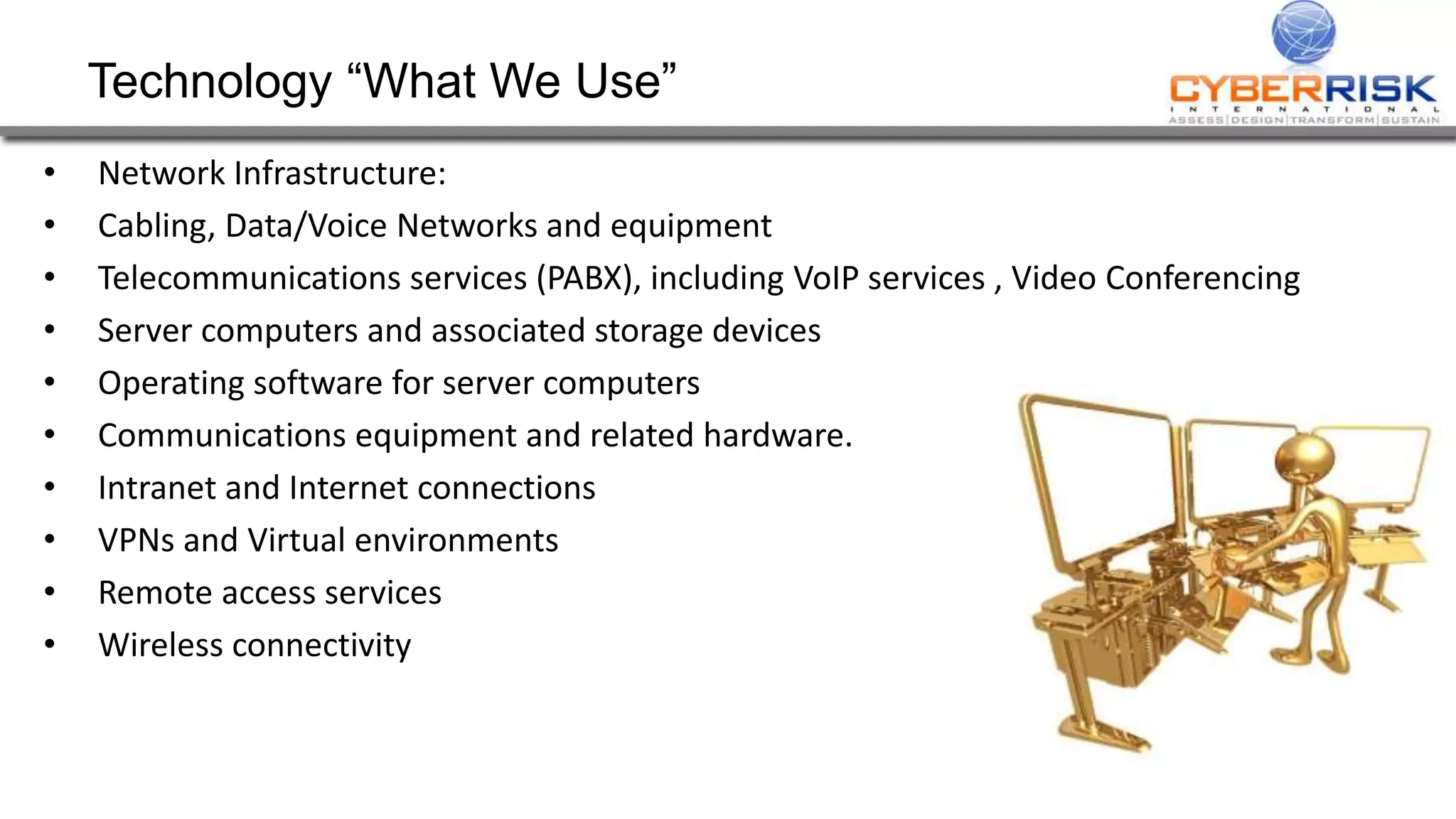
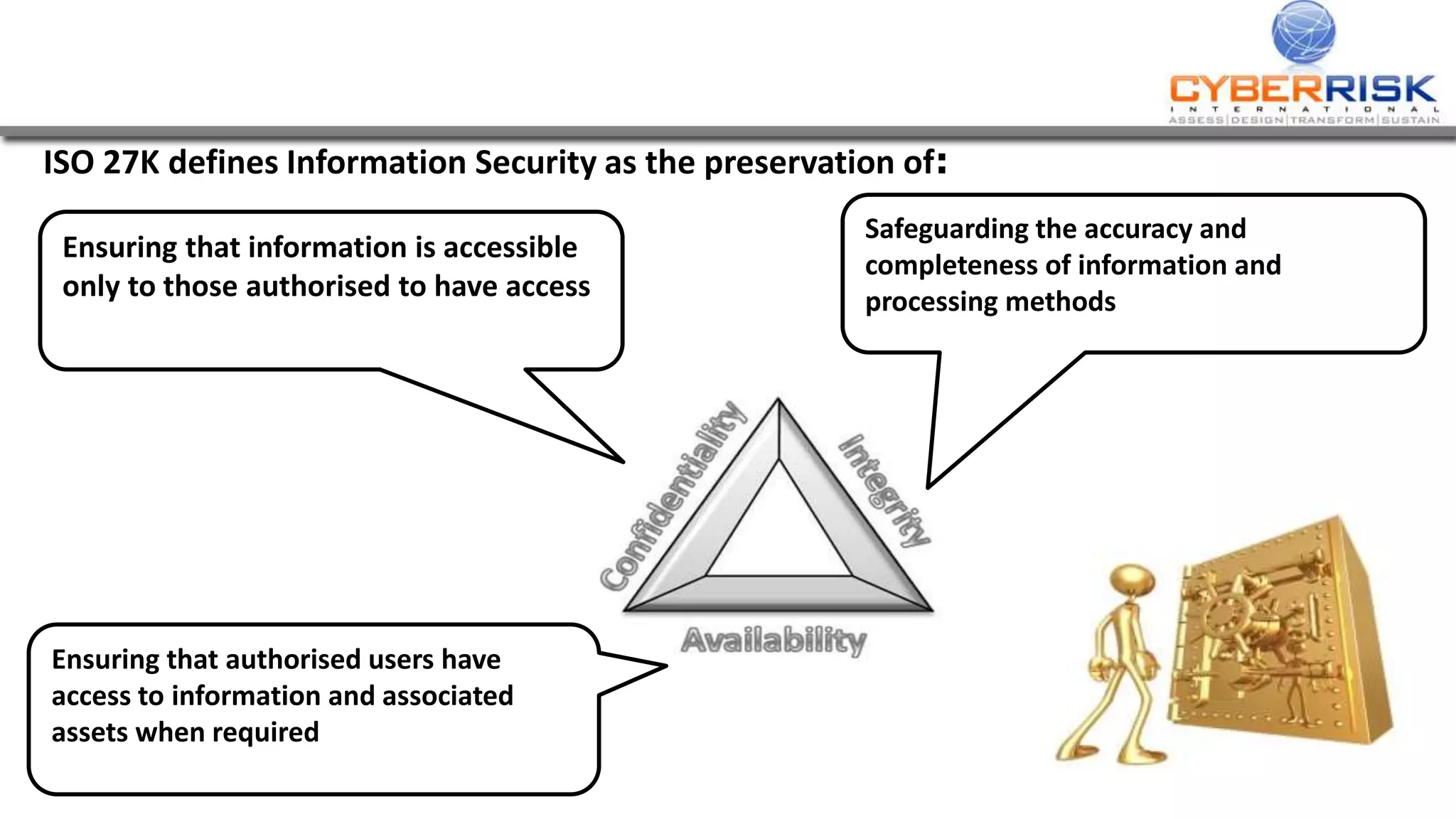
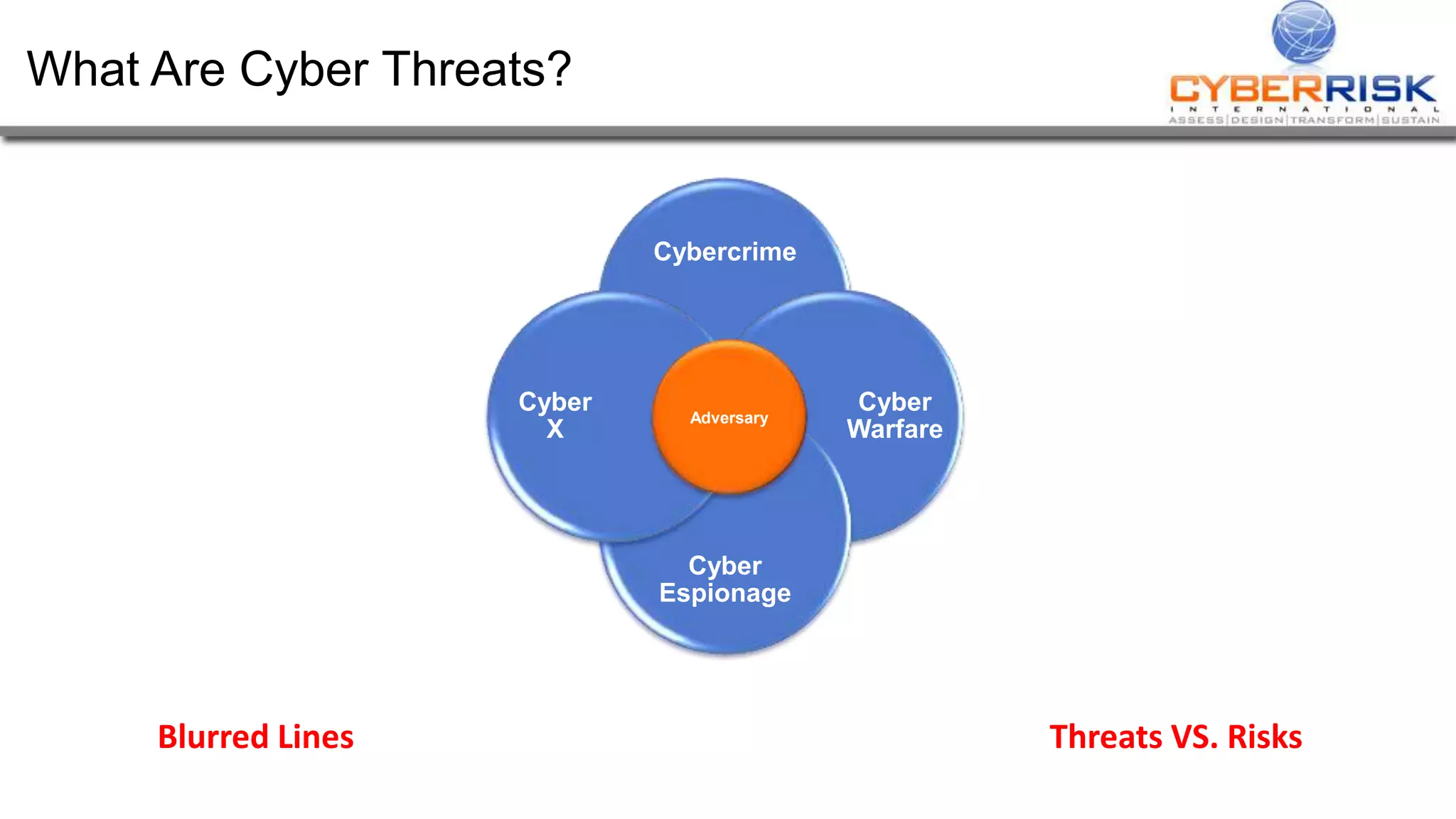
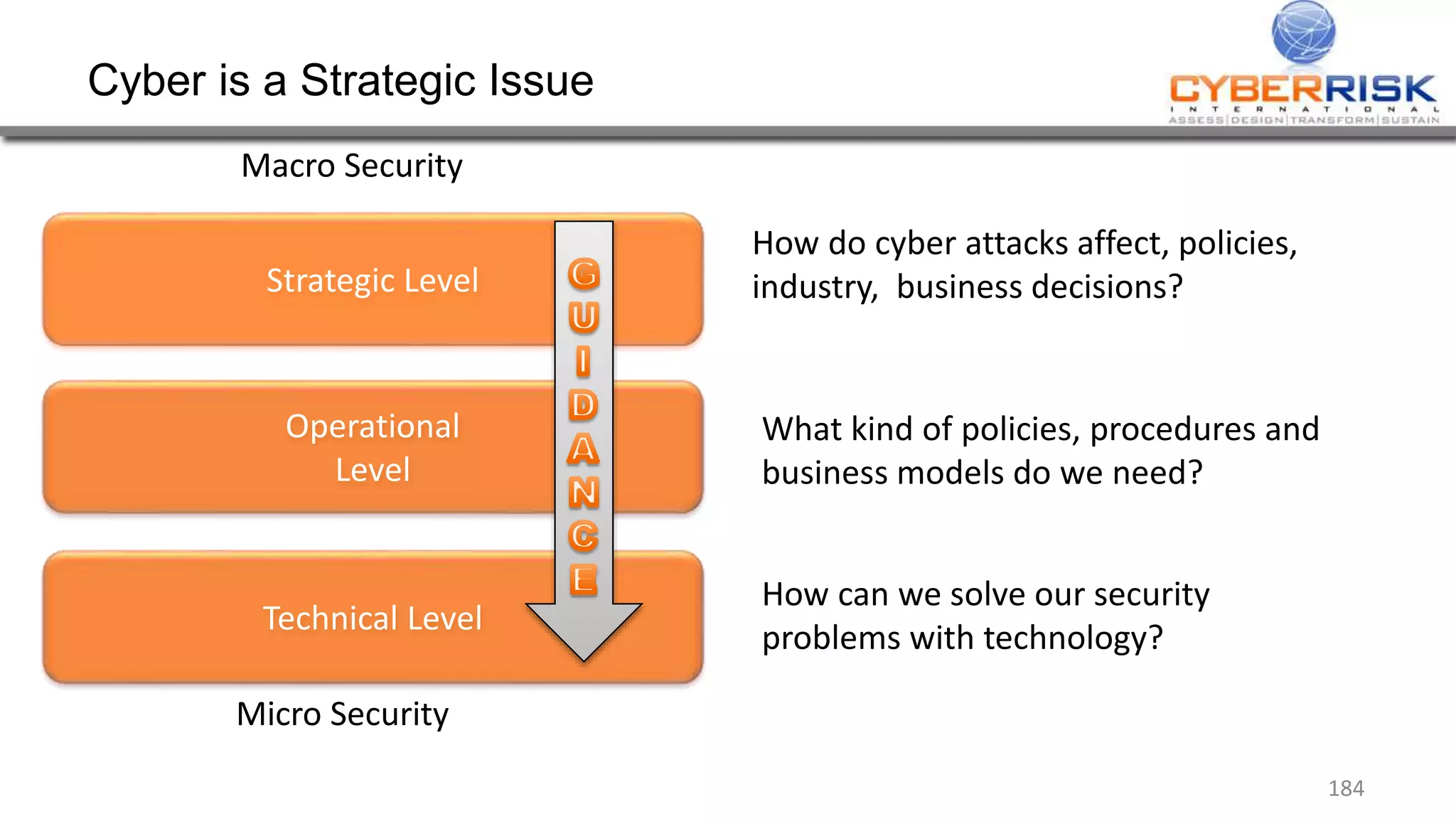
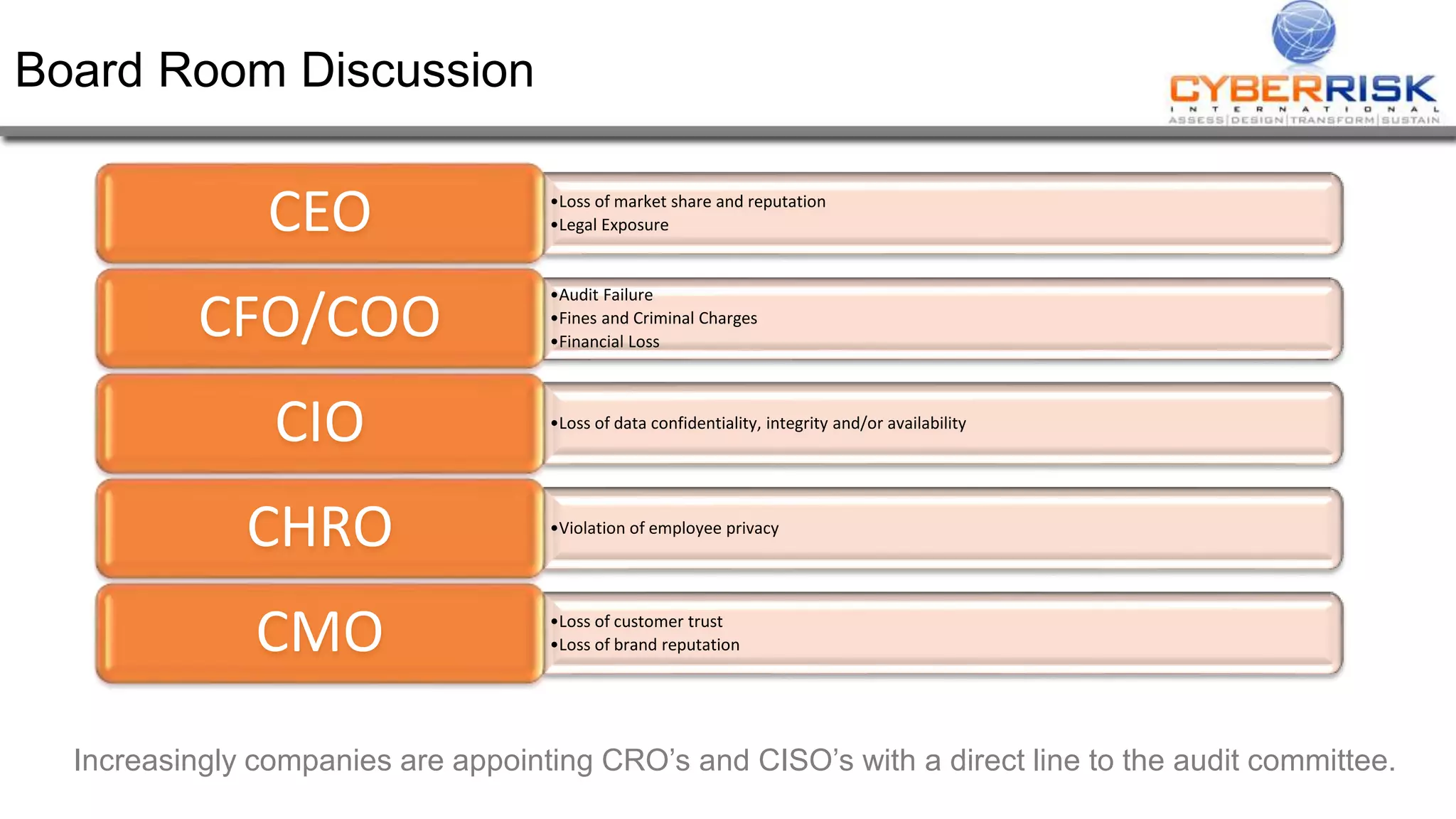
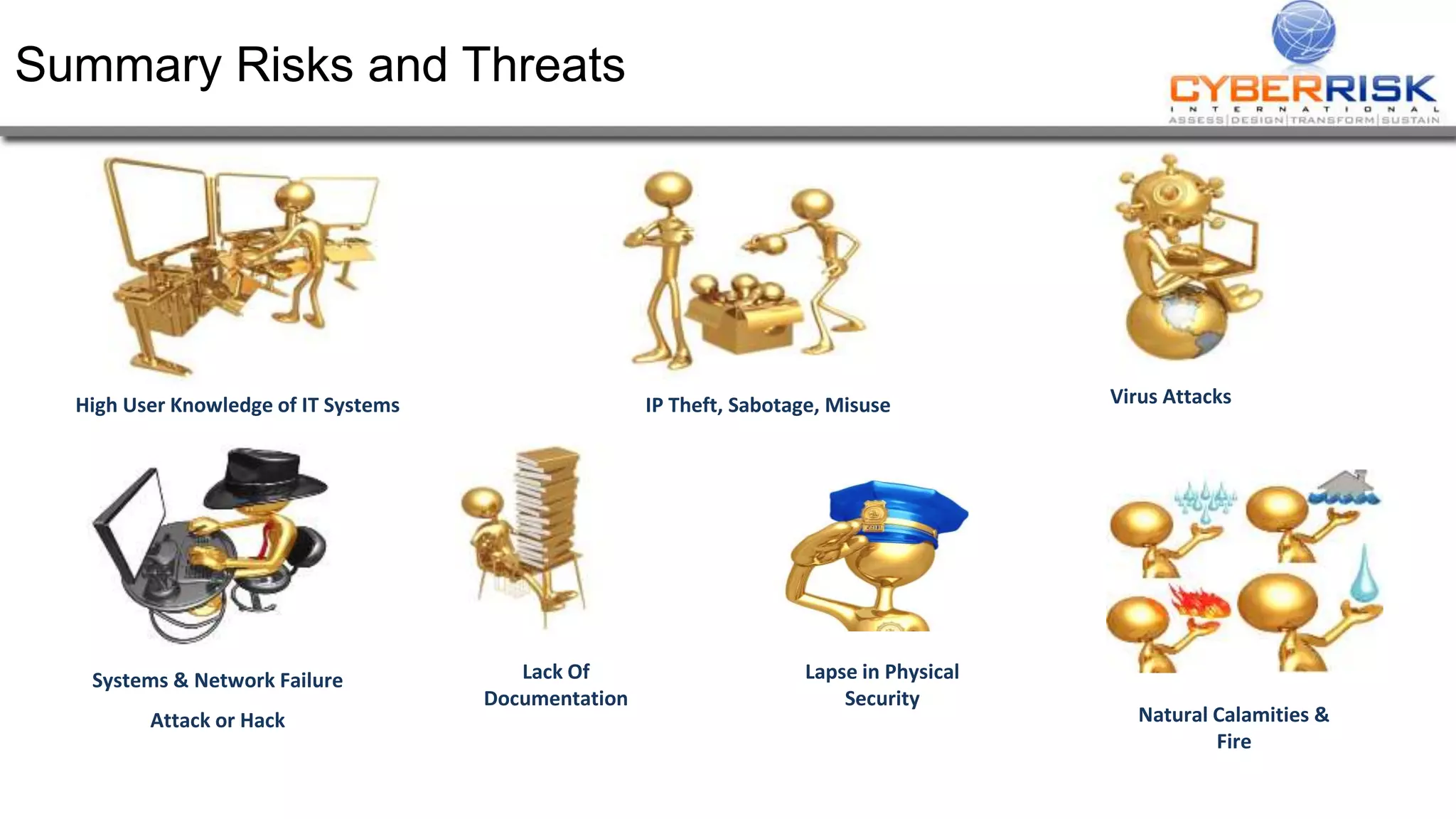
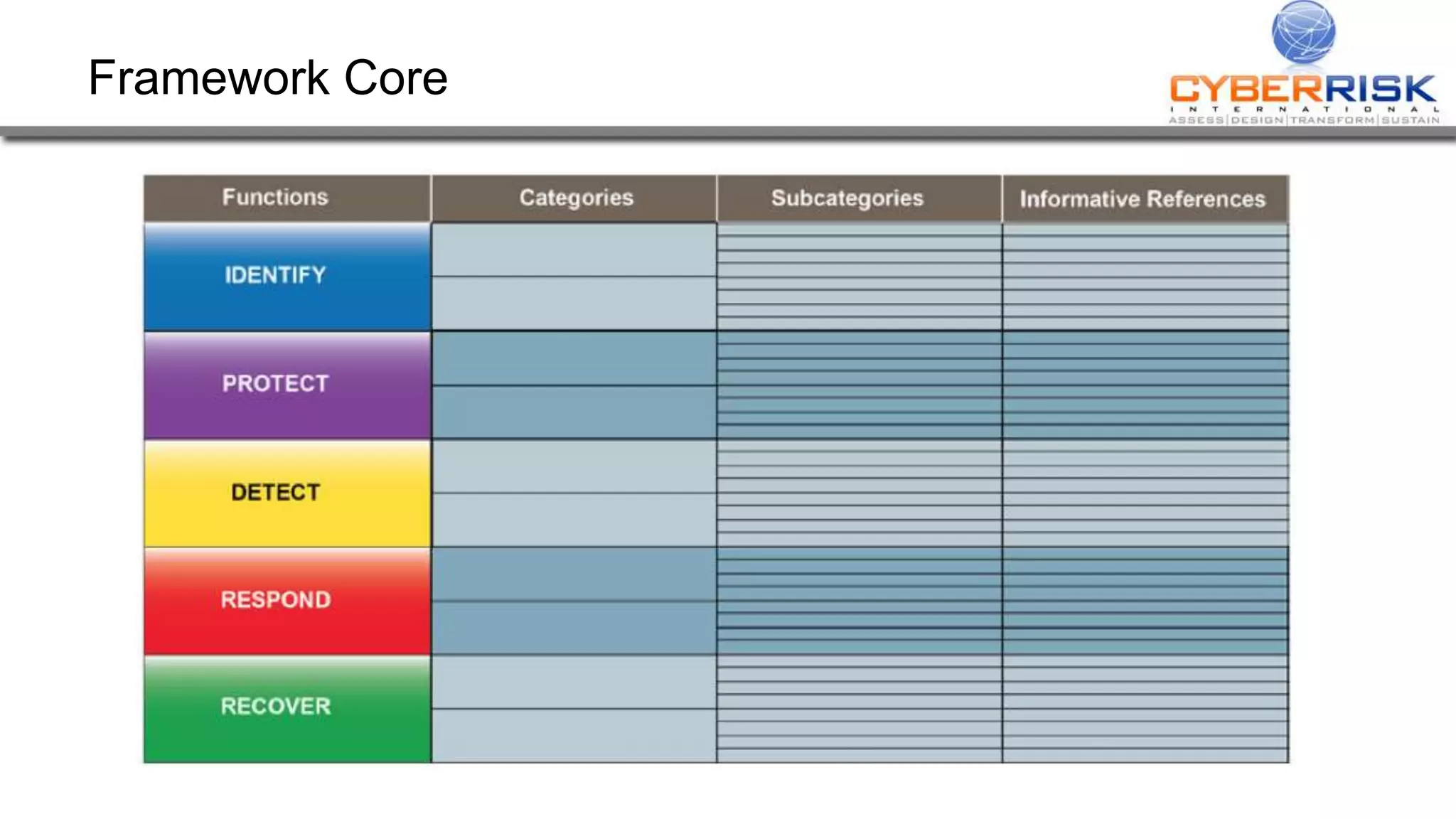
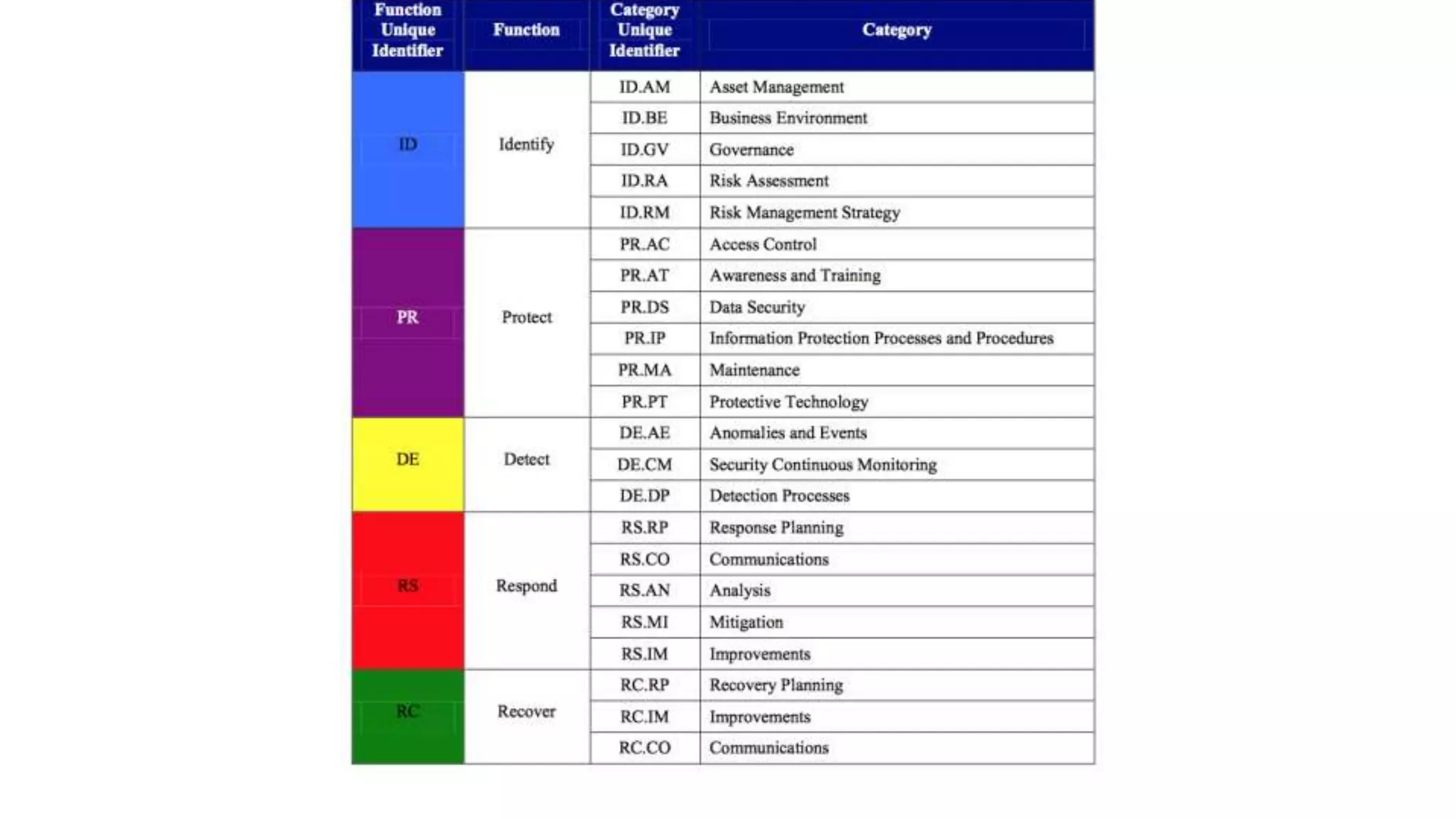
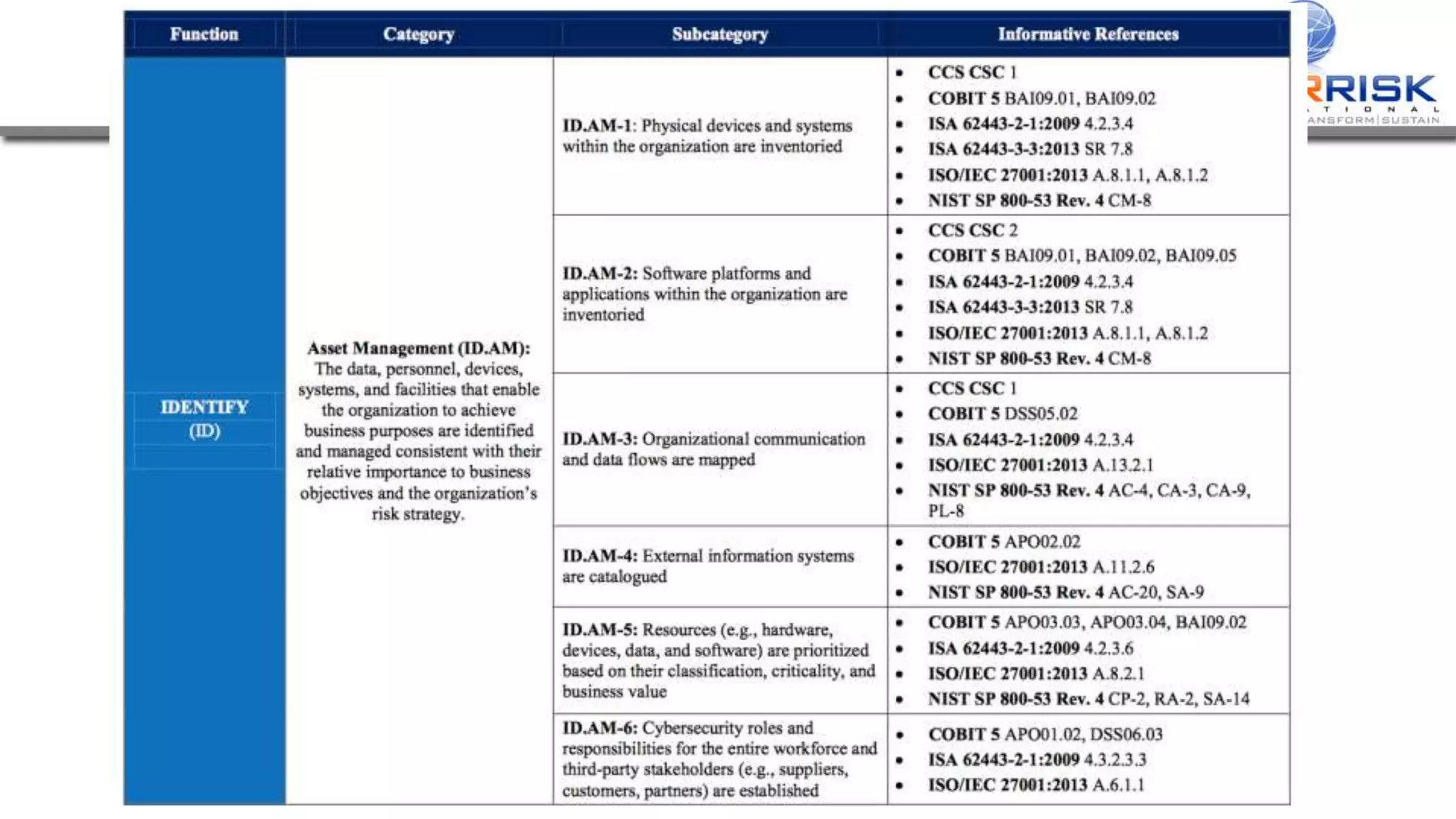
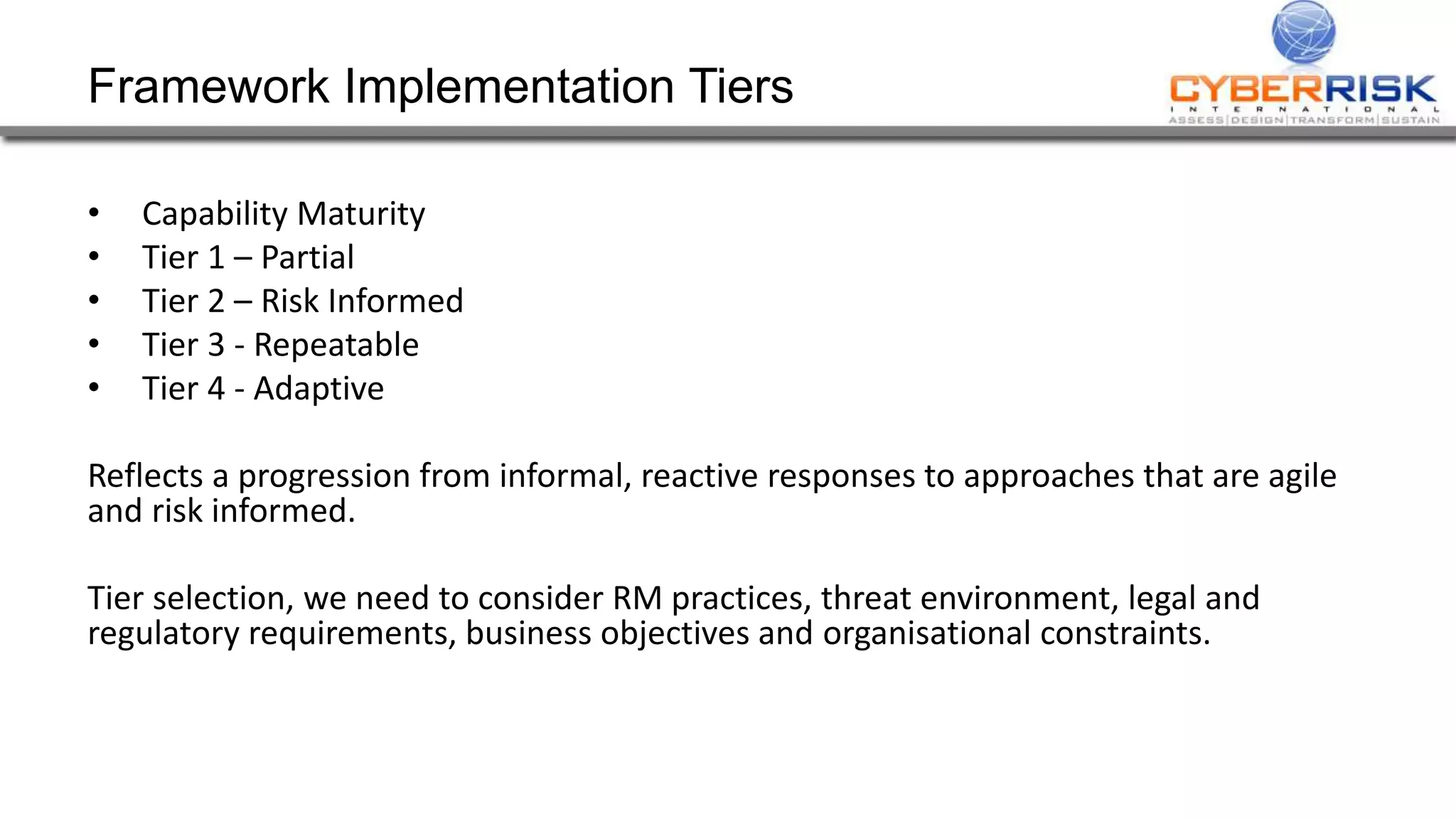
This document provides a high-level summary of a cybersecurity briefing presented by Paul C Dwyer on March 26th 2015. It discusses various cyber threats including cybercrime, cyber warfare, cyber espionage, and more. Specific topics covered include the cyber threat landscape, what cyber threats want to achieve, cybercrime drivers and statistics, the progression of threats over the past 10 years, cybercrime tools and operations, and predictions for the future of cybersecurity challenges.