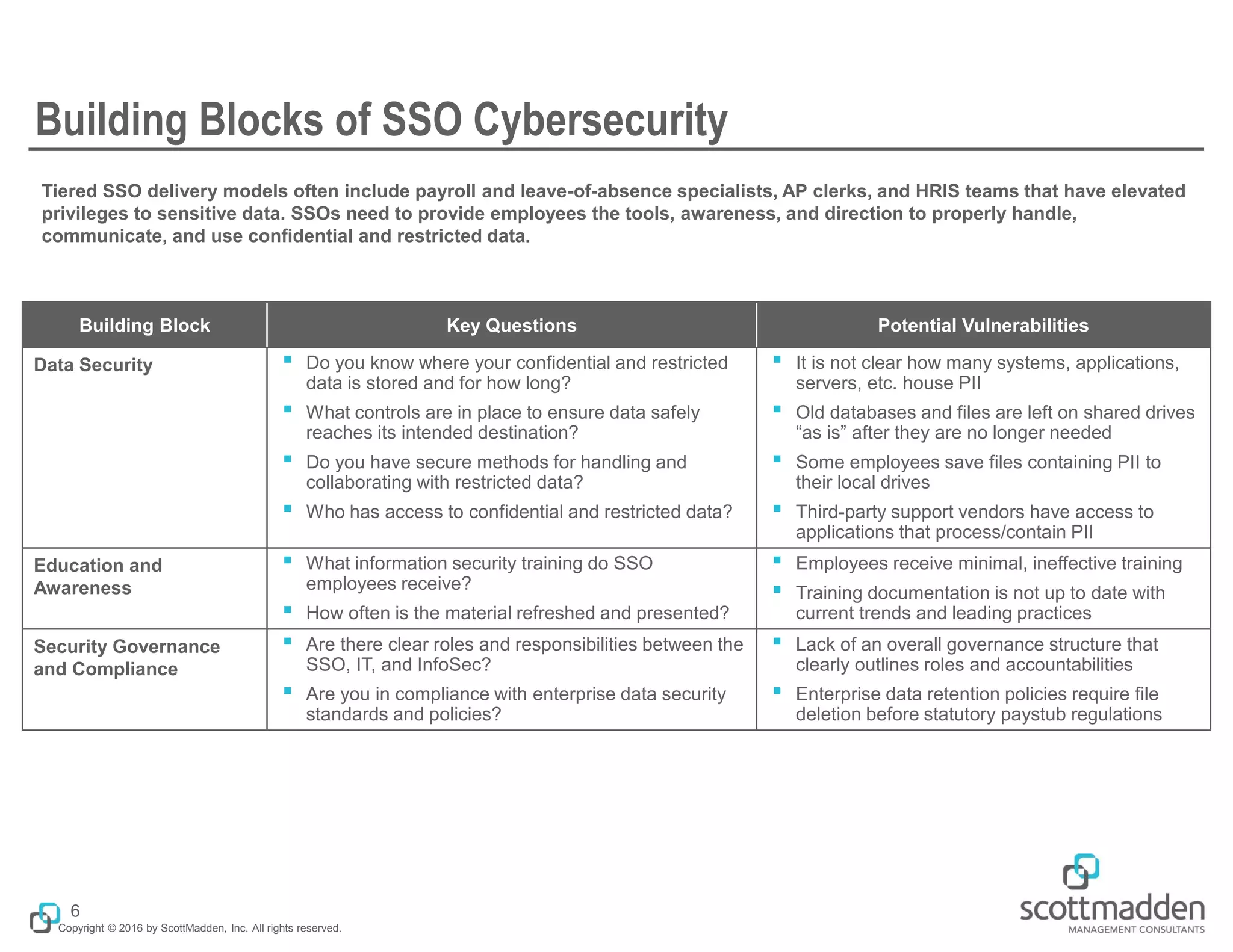
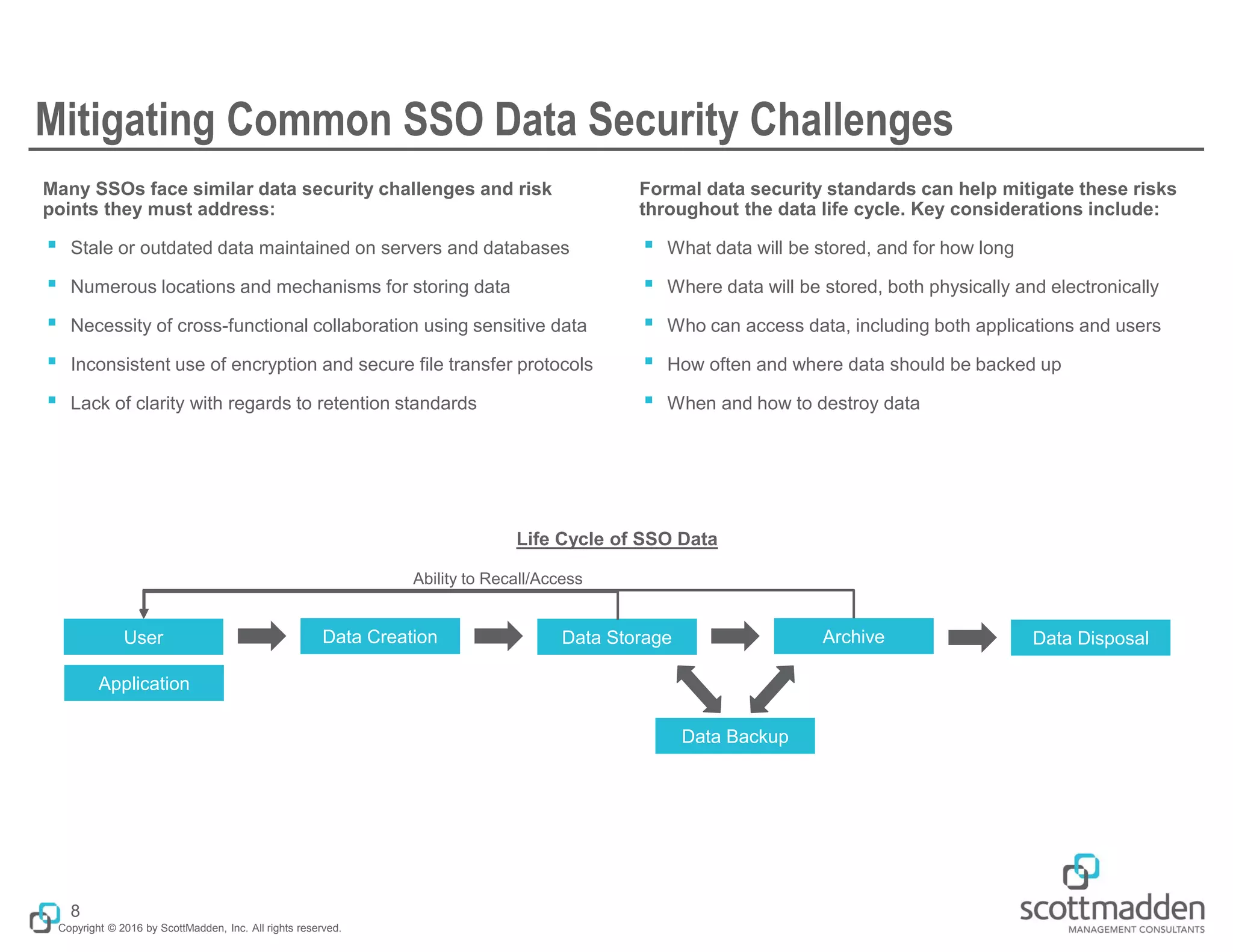
The document discusses the importance of cybersecurity in shared services organizations (SSOs), emphasizing the risks associated with handling sensitive data and the need for robust cybersecurity programs. It outlines common types of cyber threats, the rising prevalence of such attacks, and key factors contributing to vulnerabilities within SSOs. The document also provides strategies for building effective cybersecurity frameworks, including data security, employee education, and governance practices.