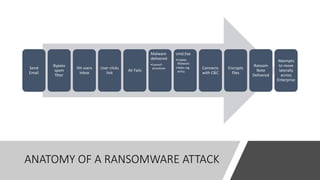
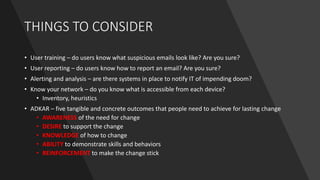
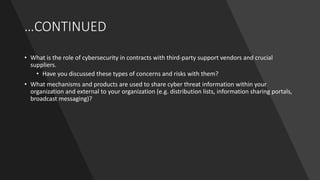
The document outlines a tabletop exercise aimed at enhancing cybersecurity awareness among senior officials, focusing on incident prevention, protection, response, and recovery. It includes a realistic ransomware attack scenario, discussion questions, and considerations for incident management and employee training. The goal is to identify cybersecurity gaps and improve organizational resilience against cyber threats.