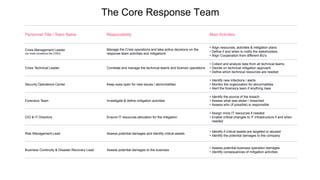
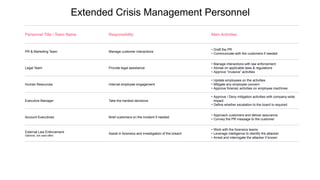
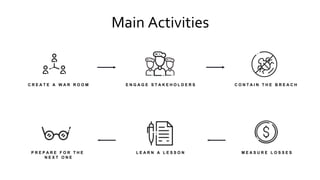
The document outlines a comprehensive incident response framework for managing cyber security incidents, emphasizing the distinction between events, notable events, and incidents. It details the roles and responsibilities of various teams during a crisis, including the crisis management leader, technical teams, and public relations. Additionally, it stresses preparation for potential crises and the necessity of a structured approach to mitigate risks and manage communications effectively.