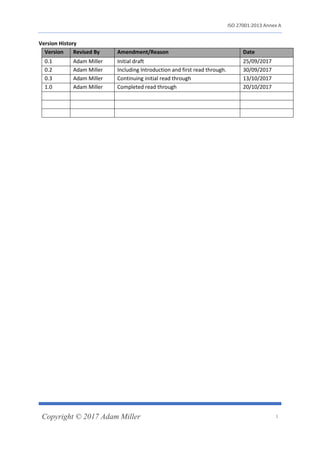
The document provides an introductory discussion on ISO's recommended controls in ISO 27001:2013 Annex A. It begins with an introduction that describes ISO 27001 and 27002 standards and the purpose of analyzing the recommended controls. It then provides a detailed explanation of each control categorized under different security topics, with the goal of helping readers better understand the requirements of ISO 27001 certification. The document contains in-depth coverage of over 50 controls across various security categories.





















































![ISO 27001:2013 Annex A
Copyright © 2017 Adam Miller 54
REFERENCES
Gamma Secure Systems Limited. (n.d.). The new versions of ISO/IEC 27001 and 27002 are now International
Standards. Retrieved from gammassl: http://www.gammassl.co.uk/27001/revision.php
Guha, S. (Director). (2014). Transition to ISO IEC 27001:2013 [Motion Picture].
Handerhan, K. (n.d.). ISC2 CISSP. Retrieved from Cybrary: https://www.cybrary.it/course/cissp/
Kosutic, D. (n.d.). ISO 27001 vs. ISO 27002. Retrieved from advisera:
https://advisera.com/27001academy/knowledgebase/iso-27001-vs-iso-27002/
Lupa, C. V. (n.d.). ISO/IEC 27001. Information Security Management System. Retrieved from Udemy:
https://www.udemy.com/isoiec-27001-information-security-management-system/learn/v4/overview
Rafiandi, A. (Director). (2015). What is ISO 27001:2013 [Motion Picture].](https://image.slidesharecdn.com/iso-27001-171020162049/85/Iso-27001-55-320.jpg)