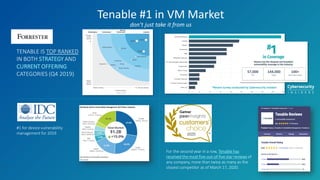
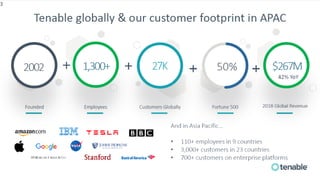
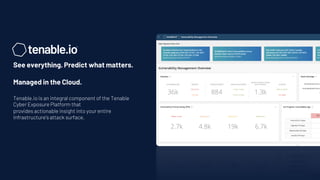
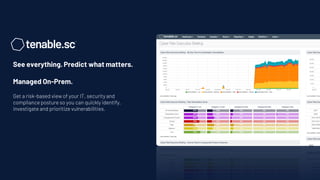
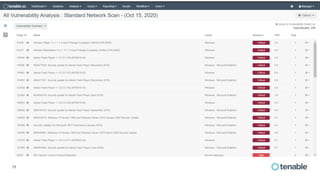
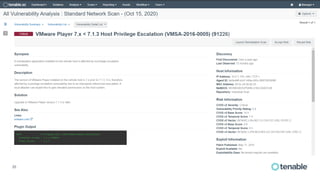
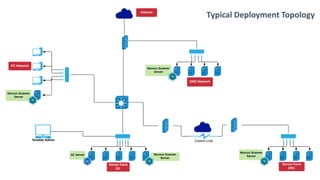
Tenable has been recognized as a leader in risk-based vulnerability management, receiving top reviews and ranking first in device vulnerability management as of 2020. The company offers a comprehensive approach to assessing and securing various infrastructures, including cloud and operational technology environments, by utilizing a wide range of vulnerability management tools and continuous monitoring. Their solutions aim to provide visibility, predict threats, and enhance security across all attack surfaces, enabling organizations to effectively manage cyber risks.