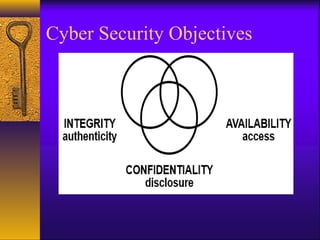
Cybersecurity is important to protect online information and systems from cyber threats. It encompasses physical, technical, and environmental security as well as regulations and third parties. As technology and internet usage increases, cyber threats are also rising. Cybersecurity objectives include confidentiality, integrity, and availability to ensure authorized access and authenticity of information and systems. Common cyber threats include viruses, hackers, malware, trojans, and password cracking. Government agencies work to secure cyberspace from these threats and secure critical infrastructure.