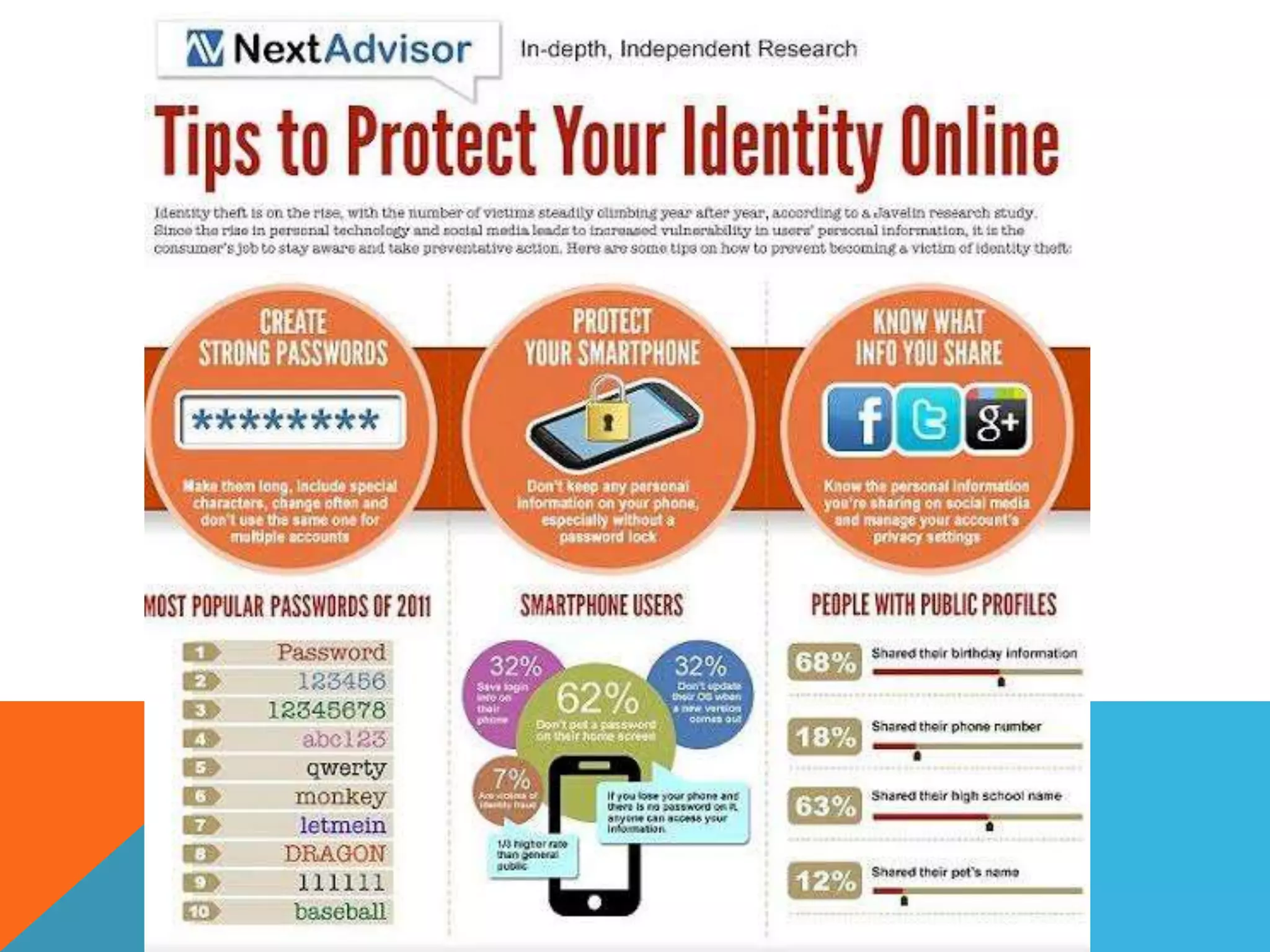
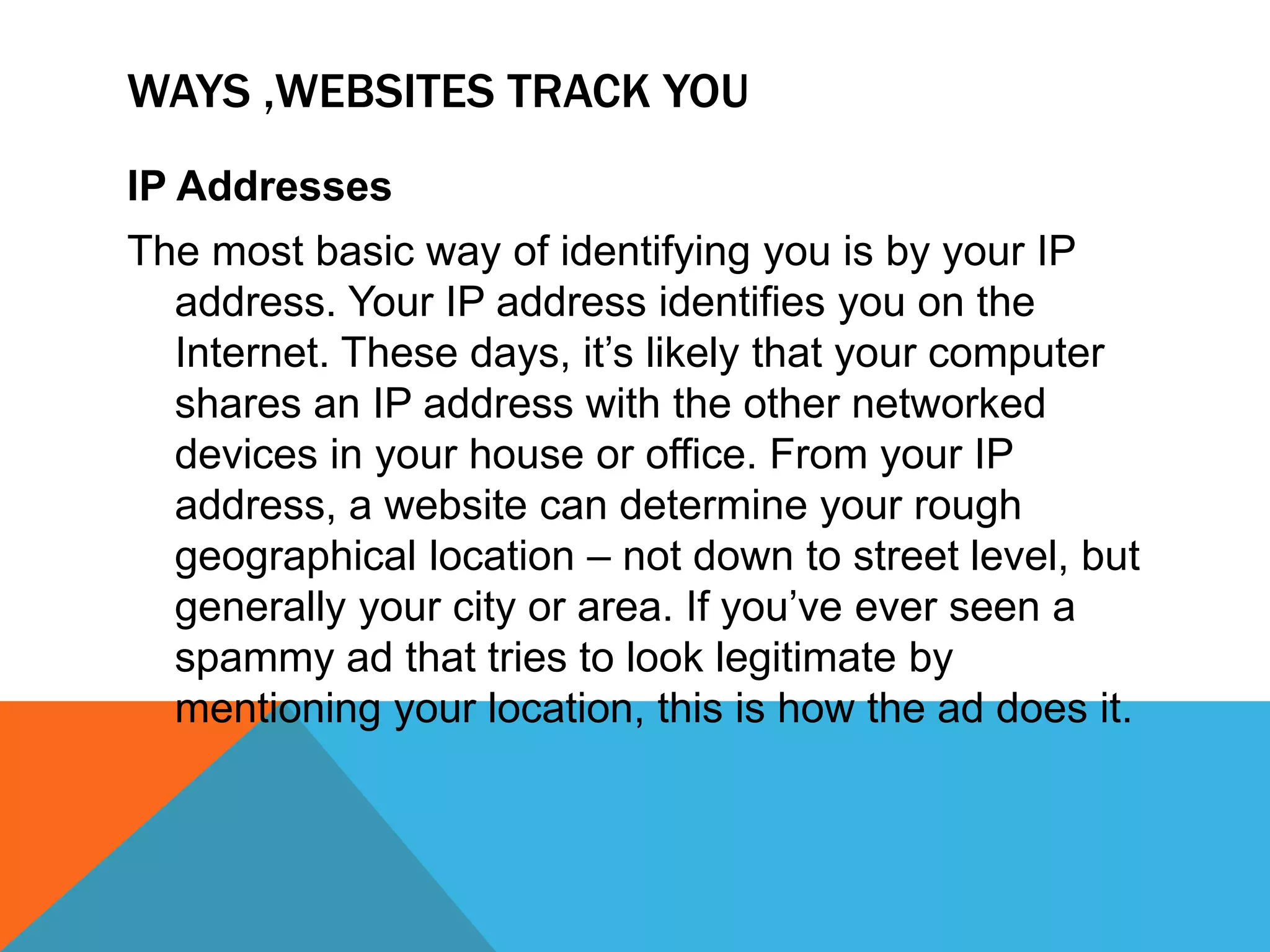
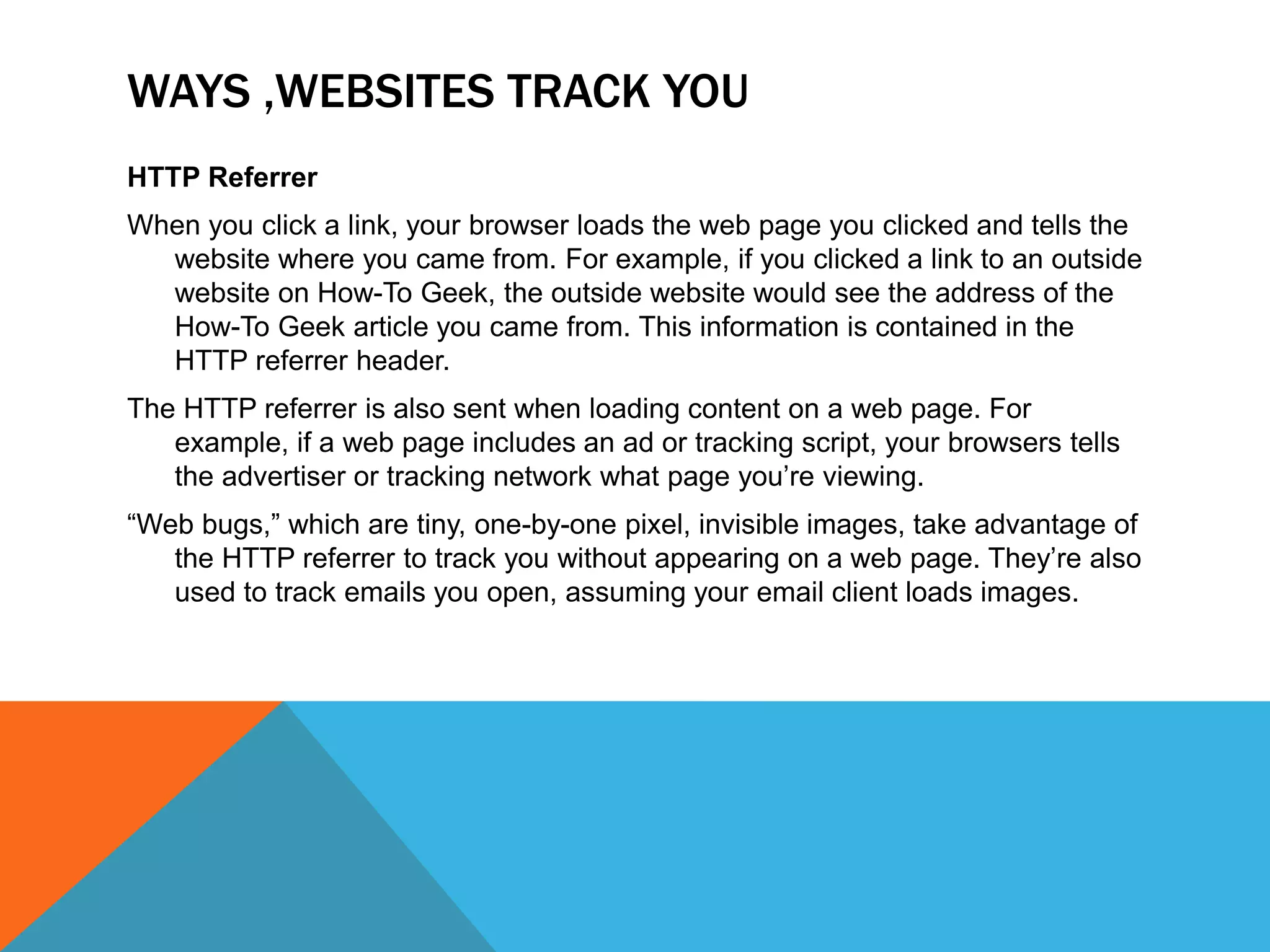
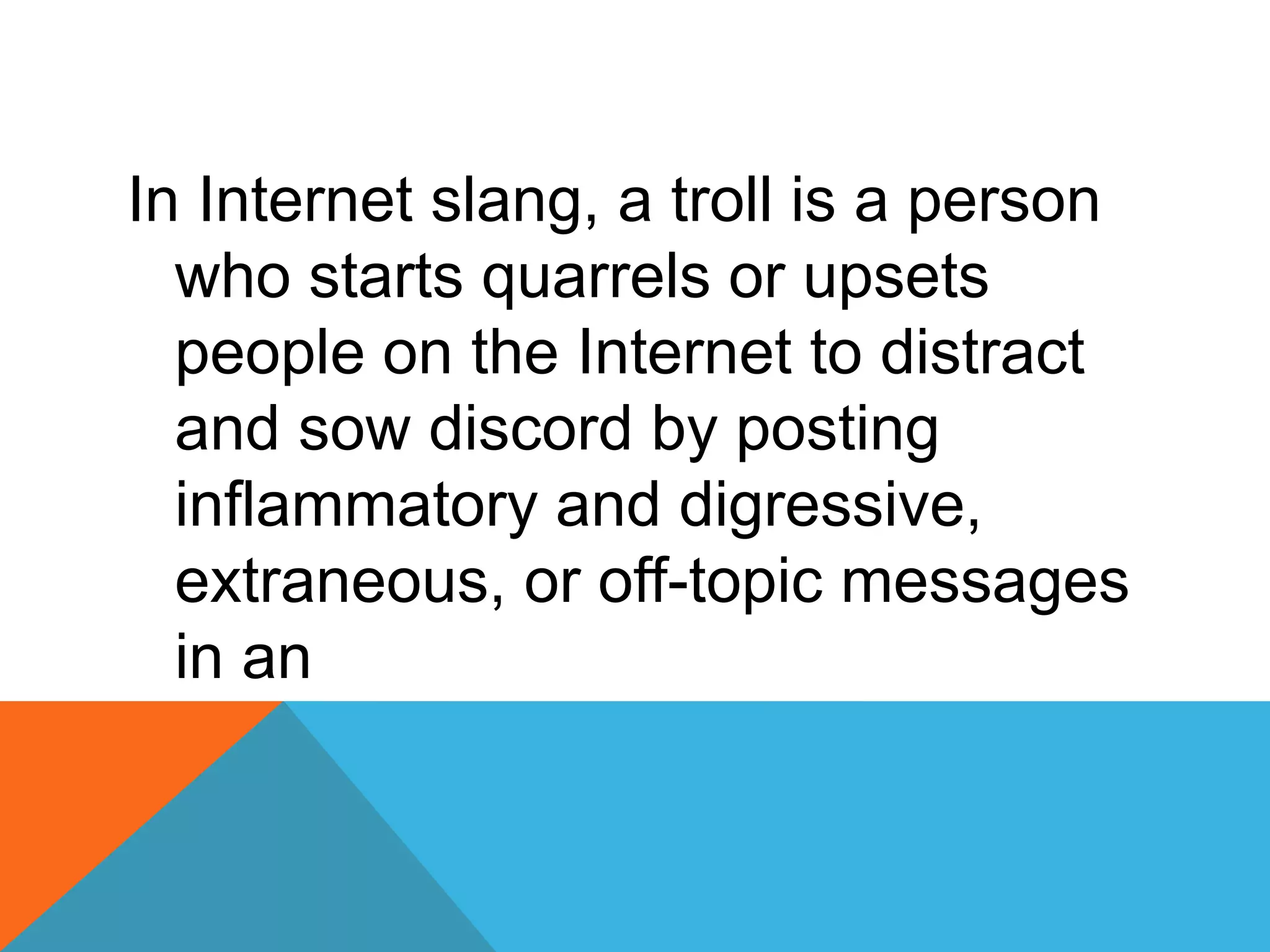
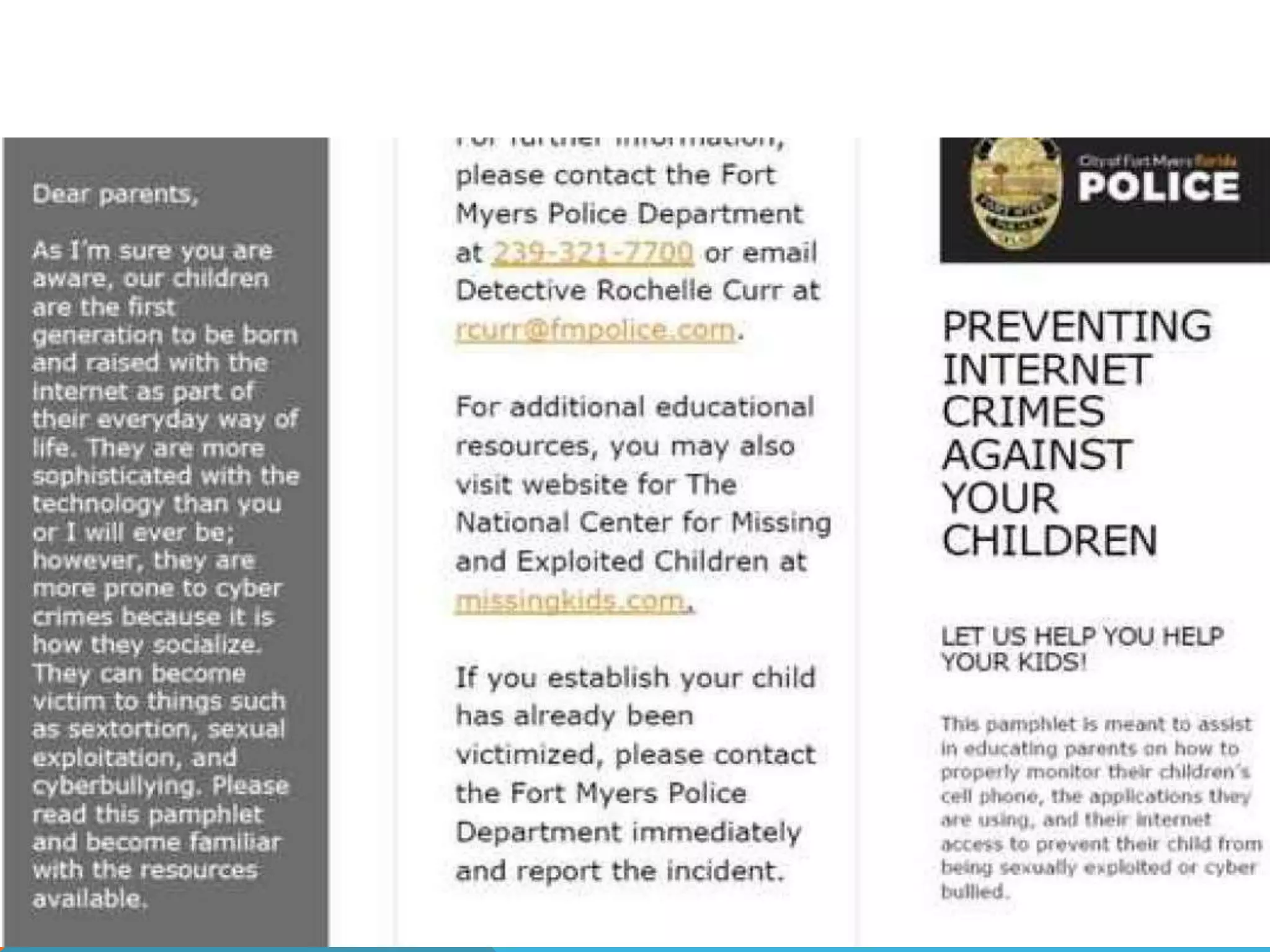
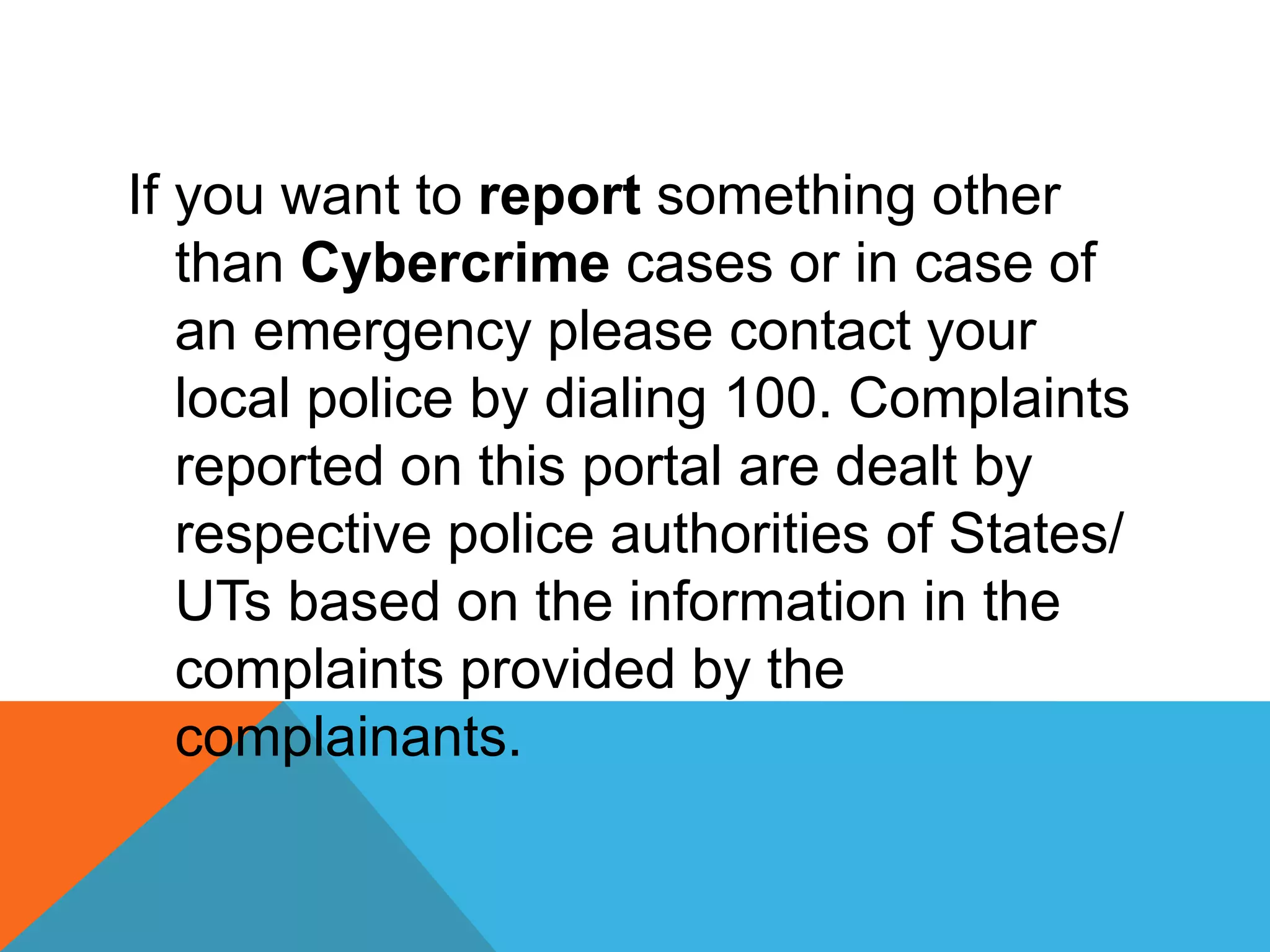
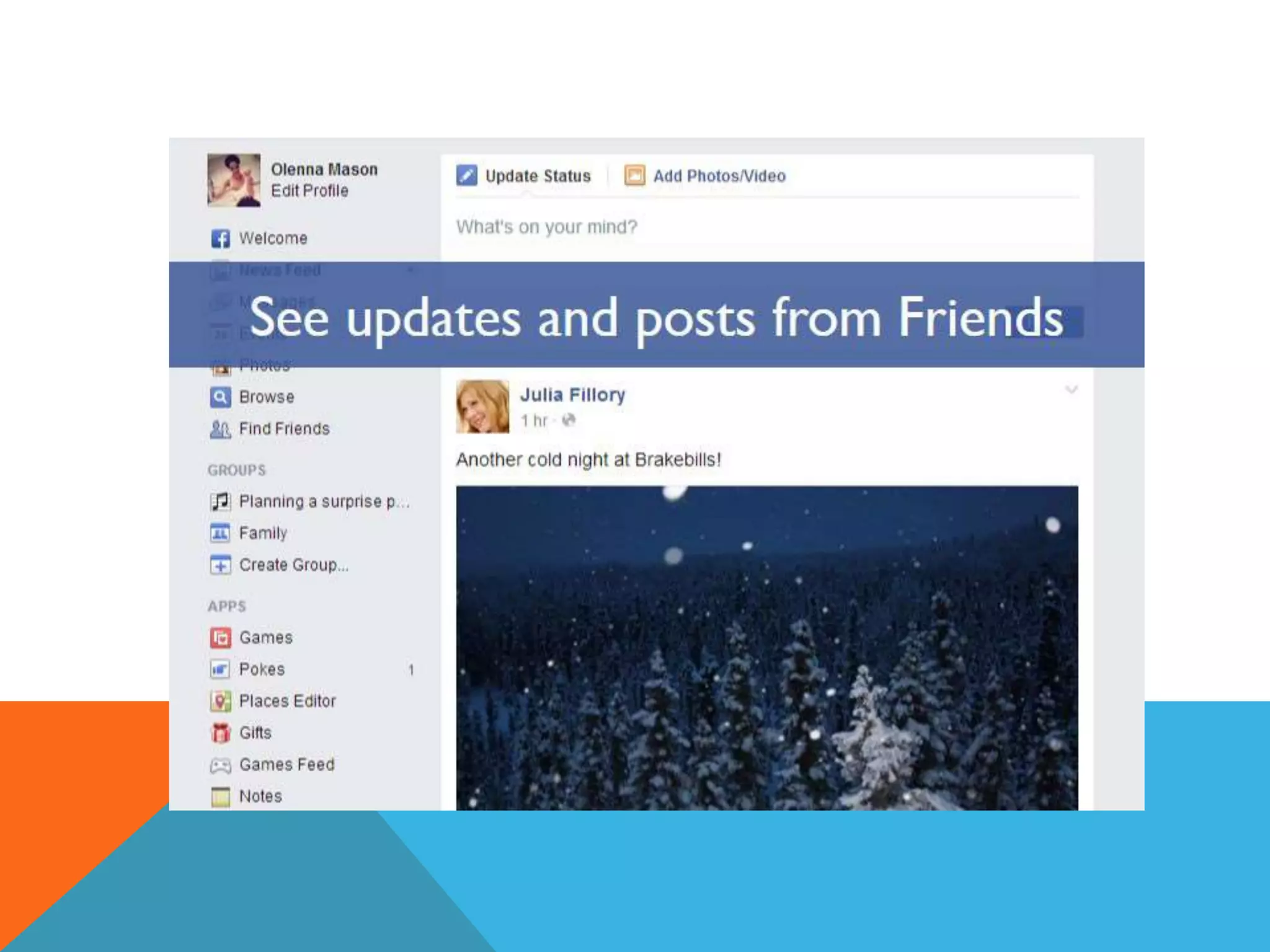
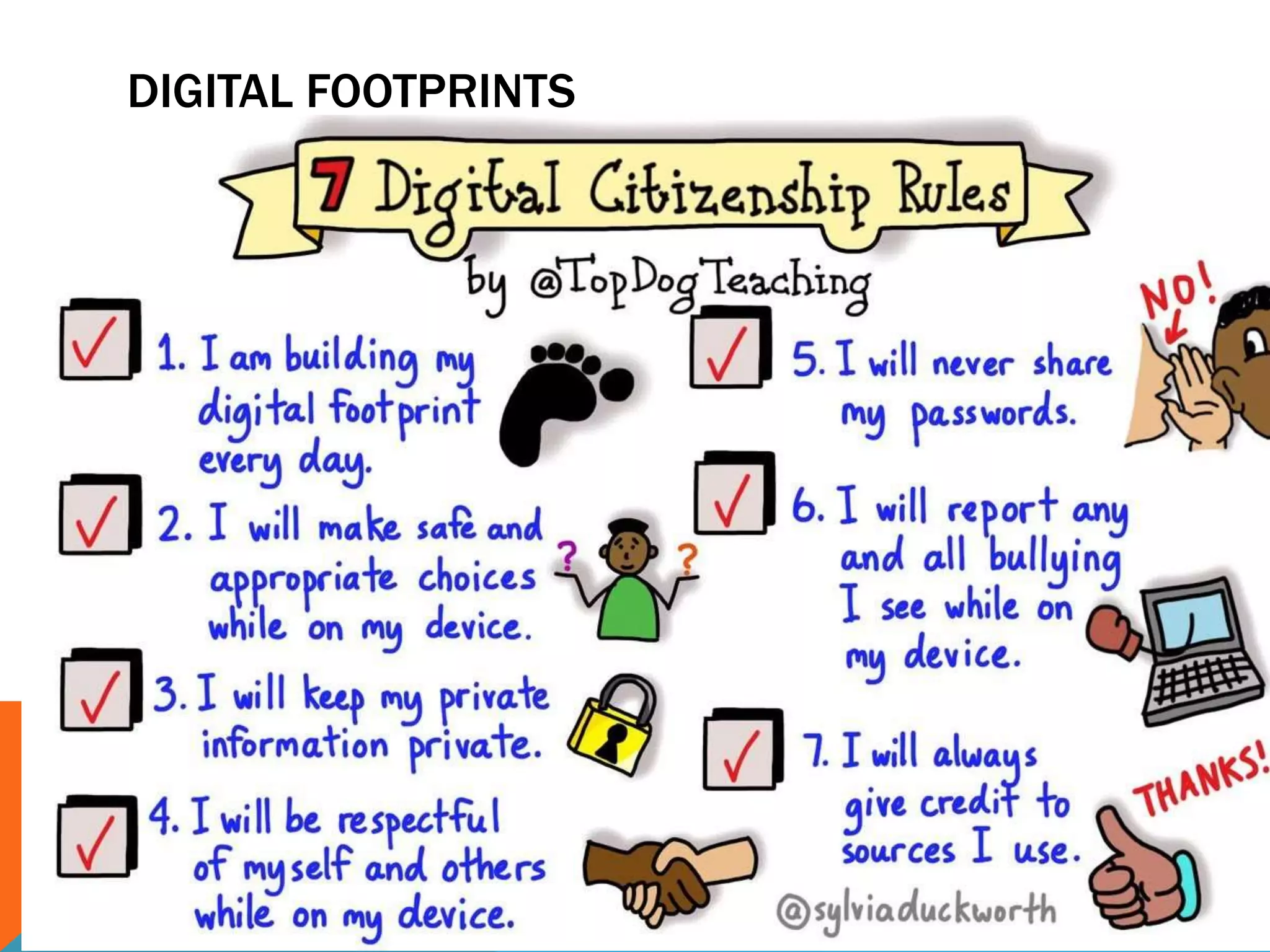
This document discusses various topics related to cyber ethics and online privacy and security. It provides tips for safe browsing, discusses how websites can track users through IP addresses, cookies, and other techniques. It also outlines best practices for ensuring confidentiality of information online and defines different types of cyber crimes like cyberbullying, cyber trolls, and more.