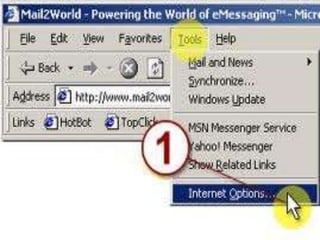
Cookies are small text files stored on a user's computer that are connected to a particular domain. Each cookie can store up to 4kB of data and a maximum of 20 cookies can be stored per domain. Cookies act as unique identifiers that allow websites to store and retrieve personal information from a user's previous visits. While cookies can improve a user's experience by pre-filling forms, they also allow third parties to track a user's browsing activity across different websites. Users have options for controlling which cookies are accepted and deleting existing cookies to protect their privacy.