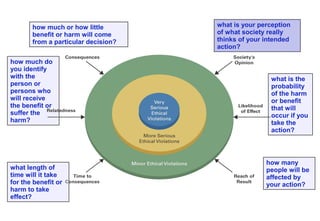
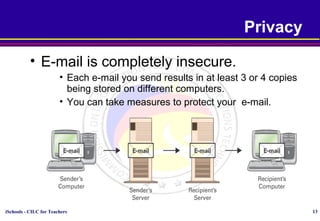
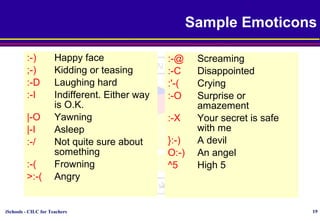
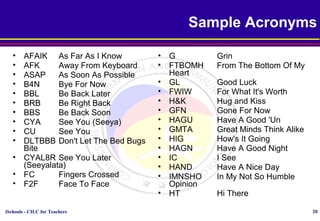
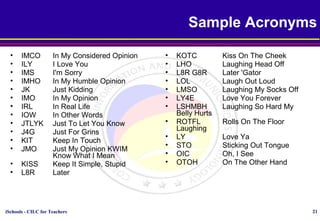
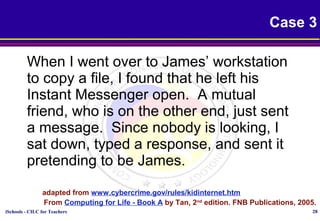
This document discusses various topics relating to cyber ethics including privacy, intellectual property, computer crime, and professional responsibilities. It provides definitions for key terms like privacy, intellectual property, piracy, and spyware. It also outlines the ten commandments of computer ethics and guidelines for netiquette when communicating online. Sample emoticons and acronyms are given. The document concludes with presenting three case studies related to ethics in accessing others' files and information without permission.