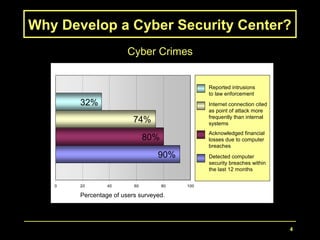
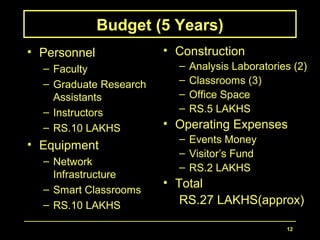
The document proposes developing a Cyber Security Center at the NM Institute of Engineering and Technology. The center would provide cyber security training, education, and research. It would serve as a hub for both private and public sectors. The objectives are to sponsor, coordinate, and provide cyber security training; serve as a resource center and broker; provide education for certification and degrees; and conduct and foster research. The proposed 5-year budget is approximately 27 lakhs for personnel, equipment, construction, and operating expenses.