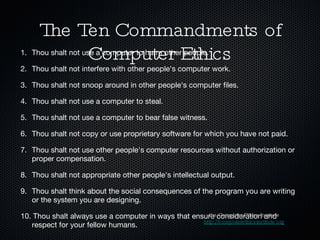
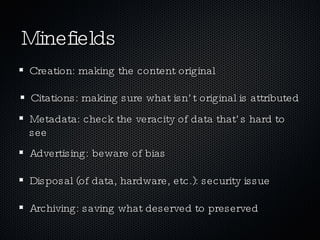
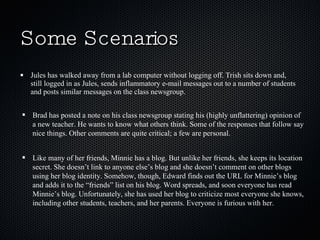
The document discusses ethics and technology in education. It outlines various ethical concerns related to technology use in schools, including privacy, intellectual property, and appropriate behavior. It provides recommendations for educators to emphasize ethical digital citizenship, such as drawing parallels between online and offline behavior, enforcing acceptable use policies, and modeling good digital practices like proper citation and critical thinking. Resources for teaching cyber ethics to students and educators are also listed.