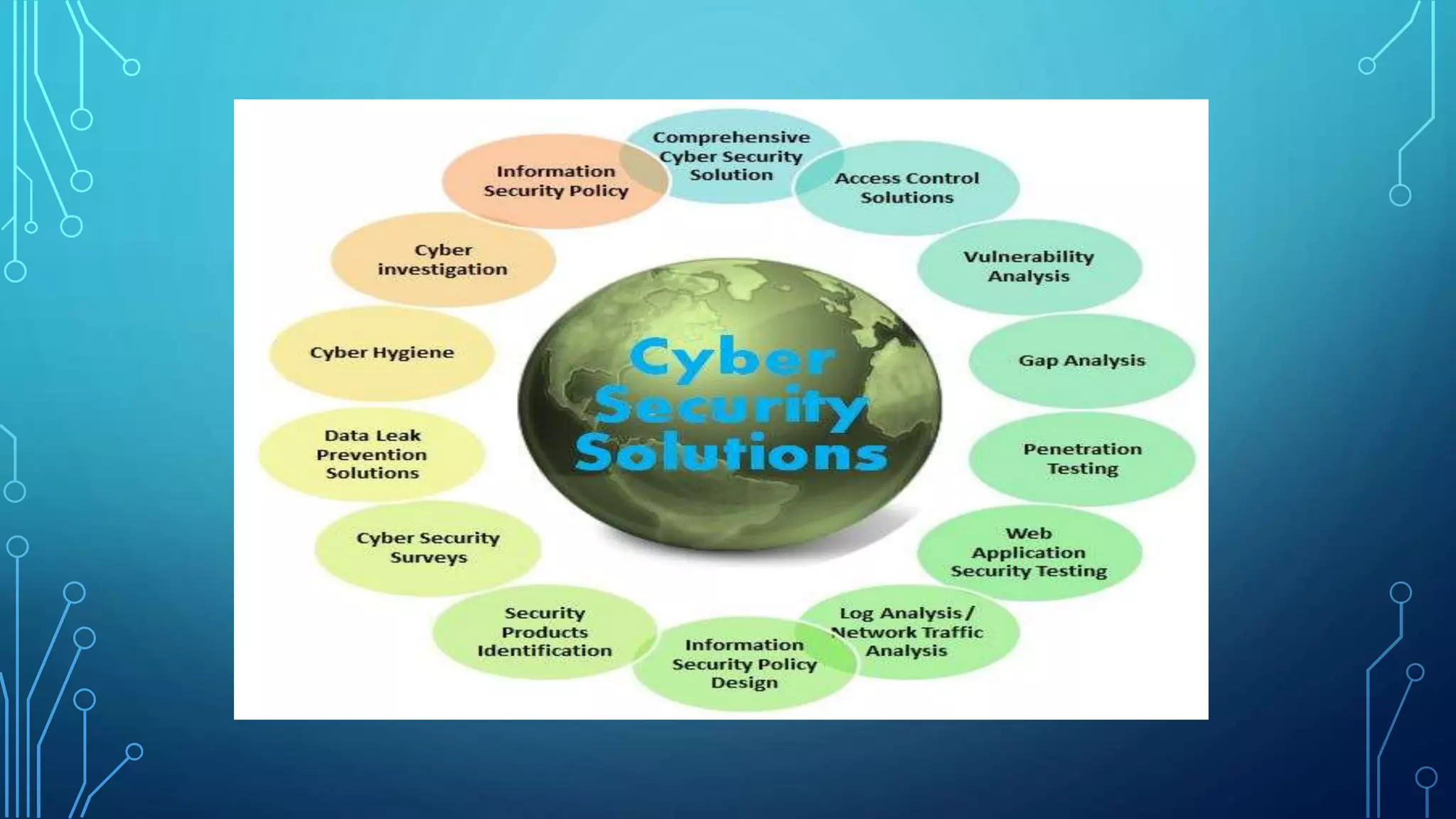
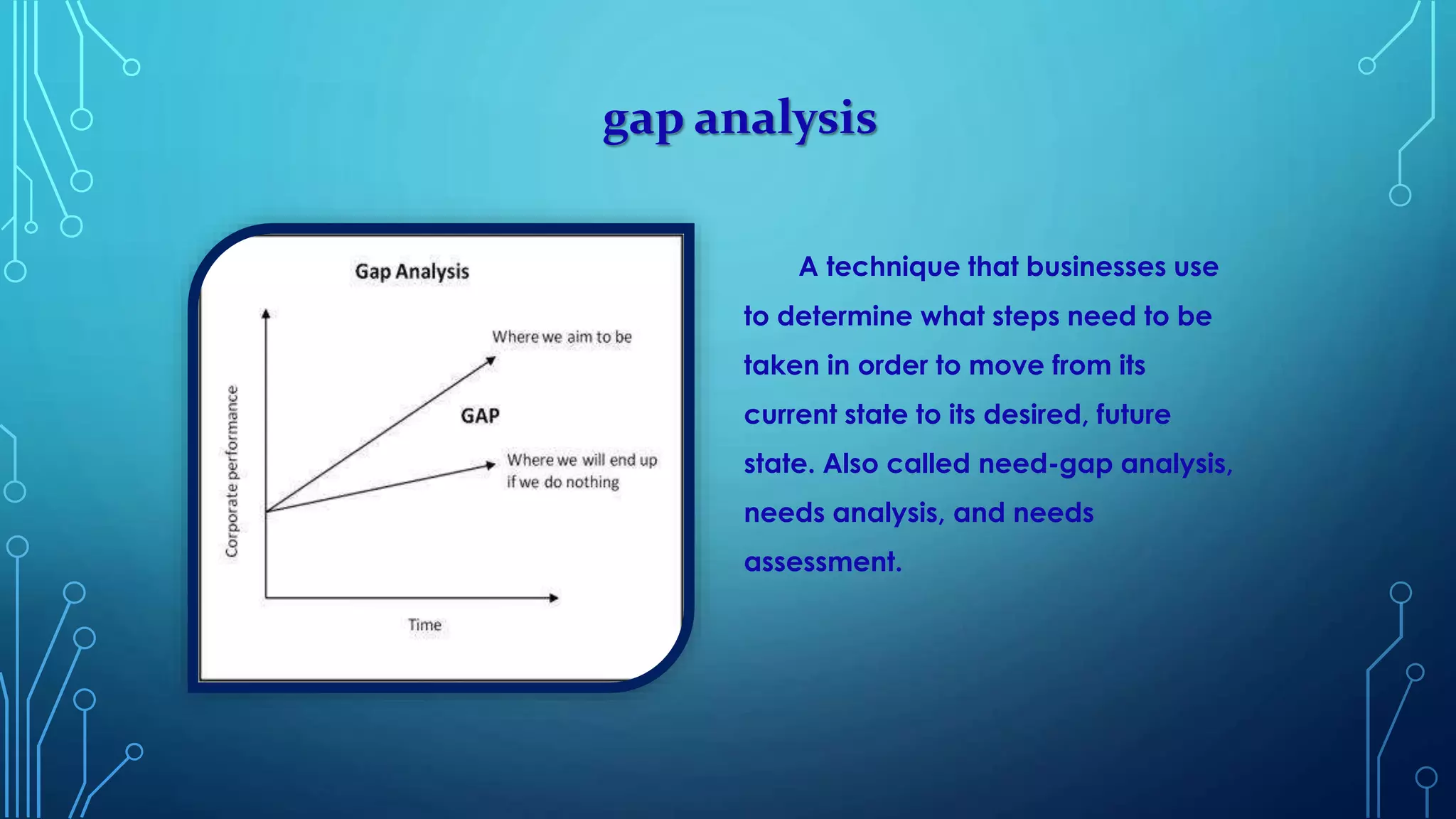
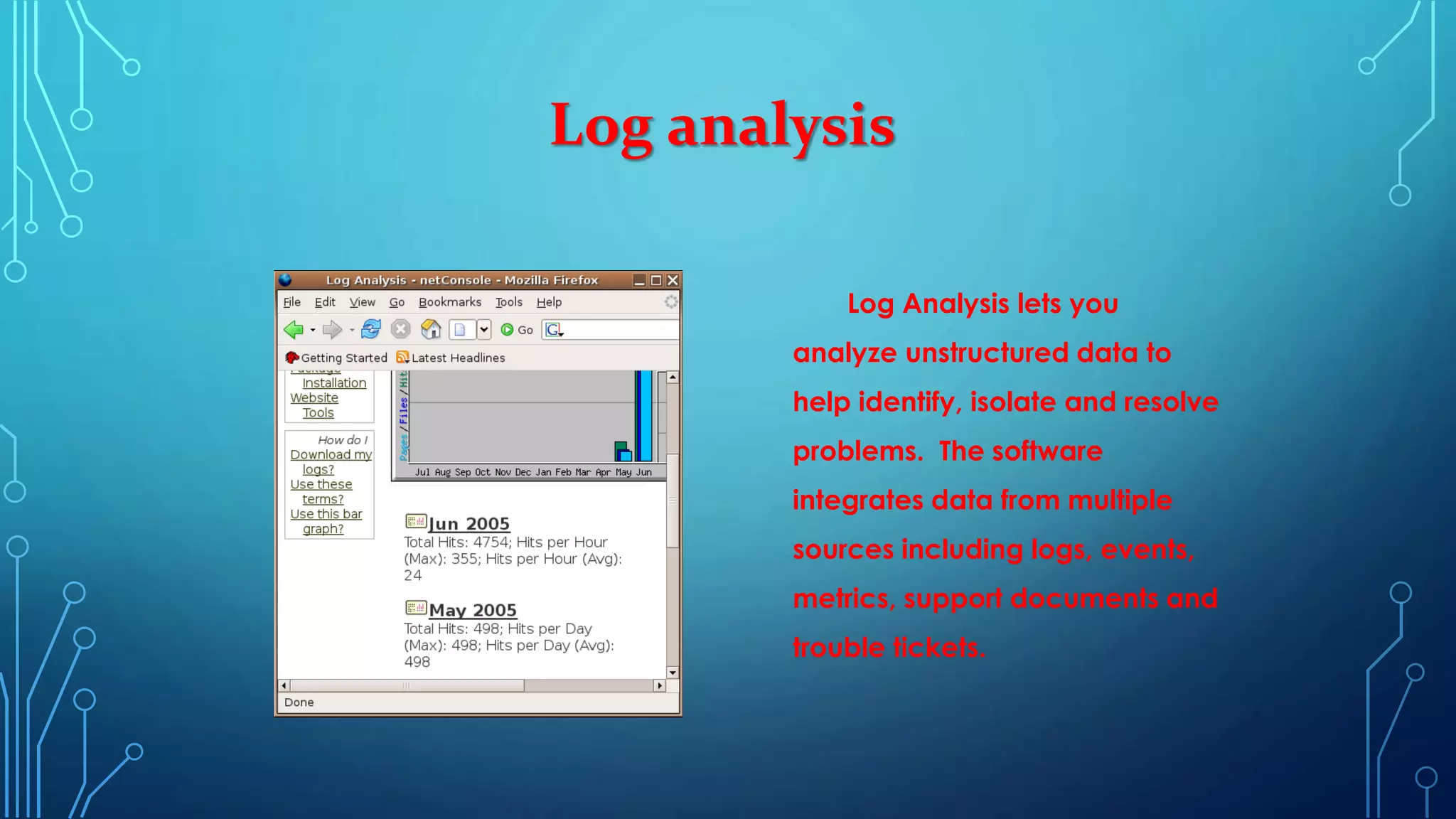
The document provides an overview of various cyber security solutions and concepts. It discusses 13 sections related to cyber security including access control solutions, vulnerability analysis, gap analysis, penetration testing, web application security, log analysis, network traffic analysis, information security policy design, and security products identification. Each section provides 1-3 paragraphs explaining the topic and key considerations.