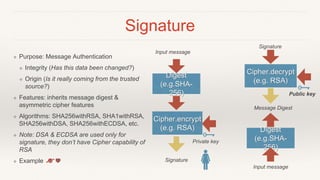
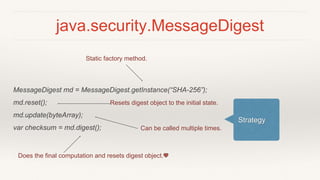
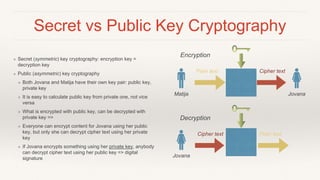
This document provides an introduction to cryptography in Java, covering key topics like cryptographic algorithms, encryption, signatures, hashing, and their usage in Java. It explains symmetric and asymmetric encryption, how algorithms like AES and RSA work, and how Java implements cryptography through interfaces like Cipher and MessageDigest. Design patterns like Strategy and Factory are used to encapsulate algorithms. Examples are provided to demonstrate signing, encrypting, and hashing data in Java applications using the cryptography APIs. The goal is to improve awareness of cryptography and make its usage in Java straightforward and easy to understand.








![javax.crypto.Cipher
KeyGenerator keyGenerator = KeyGenerator.getInstance("AES");
keyGenerator.init(192);
SecretKey secretKey = keyGenerator.generateKey();
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
byte[] cipherText = cipher.doFinal(plainText);
cipher.init(Cipher.DECRYPT_MODE, secretKey);
byte[] decryptedPlainText = cipher.doFinal(cipherText);
Auxiliary stuff to get a random/session key.
Algorithm / Mode / Padding
Initialisation of the Cipher object.
update() , doFinal(): do the work
Initialisation of the Cipher object: decrypt mode
Decrypt.](https://image.slidesharecdn.com/introductiontocryptography-230303193524-9c08279c/85/Introduction-to-Cryptography-pptx-12-320.jpg)