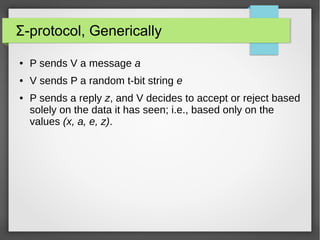
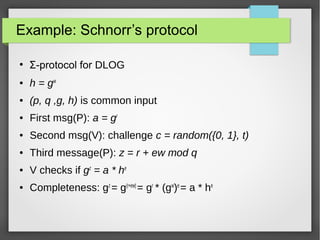
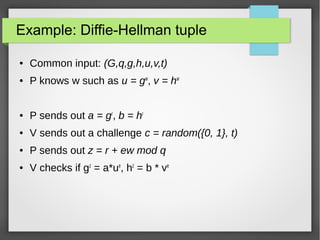
This document summarizes a talk on Sigma protocols and zero-knowledge proofs. Sigma protocols form the basis for building efficient zero-knowledge proofs. They allow a prover to convince a verifier that they know a secret witness for a statement, without revealing the witness. Schnorr's protocol is provided as a simple example of a Sigma protocol for proving knowledge of discrete logarithms. More advanced applications include building zero-knowledge proofs for statements involving AND, OR, and other logical combinations. Sigma protocols can also construct commitment schemes, non-interactive zero-knowledge proofs, and digital signatures when combined with cryptographic primitives like hash functions and random oracles.