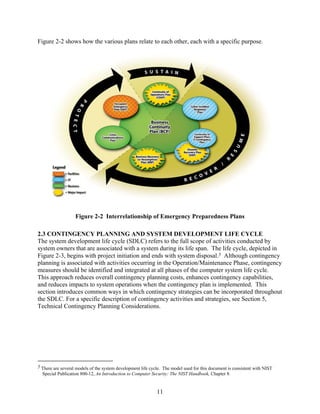
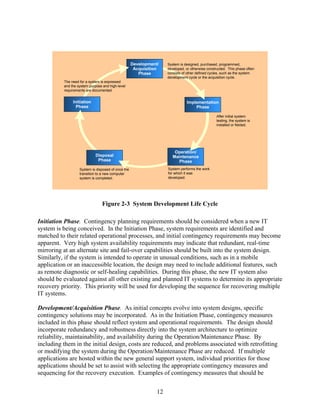
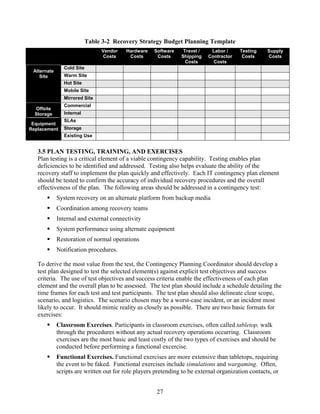
This document provides guidance for developing effective IT contingency plans. It outlines a seven-step contingency planning process that includes developing policy, conducting business impact analysis, identifying preventive controls and recovery strategies, developing and testing a contingency plan, and maintaining the plan. It also discusses considerations for contingency planning for different types of IT systems like desktops, servers, web sites, networks and mainframes. The goal is to help organizations establish thorough plans and procedures to enable quick and effective IT system recovery following a disruption.








![1. INTRODUCTION
Information technology (IT) and automated information systems are vital elements in most
business processes. Because these IT resources are so essential to an organization’s success, it is
critical that the services provided by these systems are able to operate effectively without
excessive interruption. Contingency planning supports this requirement by establishing thorough
plans and procedures and technical measures that can enable a system to be recovered quickly
and effectively following a service disruption or disaster.
IT contingency planning refers to a coordinated strategy involving plans, procedures, and technical
measures that enable the recovery of IT systems, operations, and data after a disruption. Contingency
planning generally includes one or more of the approaches to restore disrupted IT services:
Restoring IT operations at an alternate location
Recovering IT operations using alternate equipment
Performing some or all of the affected business processes using non-IT (manual) means
(typically acceptable for only short-term disruptions).
This document provides guidance to individuals responsible for preparing and maintaining IT
contingency plans. The document discusses essential contingency plan elements and processes,
highlights specific considerations and concerns associated with contingency planning for various
types of IT systems, and provides examples to assist readers in developing their own IT
contingency plans. This document supersedes Federal Information Processing Standard
Publication (FIPS PUB) 87, Guidelines for ADP Contingency Planning.
1.1 AUTHORITY
This document has been developed by the National Institute of Standards and Technology
(NIST) in furtherance of its statutory responsibilities under the Computer Security Act of 1987
and the Information Technology Management Reform Act of 1996 (specifically, 15 United
States Code [U.S.C.] 278 g-3 (a)(5)). This is not a guideline within the meaning of 15 U.S.C.
278 g-3 (a)(3). These guidelines are for use by federal organizations that process sensitive
information. They are consistent with the requirements of the Office of Management and Budget
(OMB) Circular A-130, Appendix III.
This document may be used by nongovernmental organizations on a voluntary basis. It is not
subject to copyright.
Nothing in this document should be taken to contradict standards and guidelines made
mandatory and binding upon federal agencies by the Secretary of Commerce under statutory
authority. Nor should these guidelines be interpreted as altering or superseding the existing
authorities of the Secretary of Commerce; the Director, OMB; or any other federal official.
1](https://image.slidesharecdn.com/contingencyplanningguide-13040880119244-phpapp02/85/Contingency-Planning-Guide-9-320.jpg)


![IT System: *
An IT system is identified by defining boundaries around a set of processes, communications, storage,
and related resources (an architecture).
All components of an IT system need not be physically connected (e.g., [1] a group of stand-alone
personal computers (PCs) in an office; [2] a group of PCs placed in employees’ homes under defined
telecommuting program rules; [3] a group of portable PCs provided to employees who require mobile
computing capability for their jobs; and [4] a system with multiple identical configurations that are
installed in locations with the same environmental and physical controls.
* As defined in NIST Special Publication 800-18, Guide for Developing Security Plans for Information
Technology Systems
1.4 AUDIENCE
Managers within federal organizations and those individuals responsible for IT security at system
and operational levels can use the principles presented in this document. This description
includes the following personnel:
Managers responsible for overseeing IT operations or business processes that rely on IT
systems
System administrators responsible for maintaining daily IT operations
Information System Security Officers (ISSOs) and other staff responsible for
developing, implementing, and maintaining an organization’s IT security activities
System engineers and architects responsible for designing, implementing, or modifying
information systems
Users who employ desktop and portable systems to perform their assigned job functions
Other personnel responsible for designing, managing, operating, maintaining, or using
information systems.
In addition, emergency management personnel who may need to coordinate facility-level
contingency may use this document with IT contingency planning activities. The concepts
presented in this document are not specific to government systems and may be used by private
and commercial organizations.
1.5 DOCUMENT STRUCTURE
This document is designed to logically lead the reader through the process of designing an IT
contingency planning program applicable to a wide range of organizations, evaluating the
organization’s needs against recovery strategy options and technical considerations, and
documenting the recovery strategy into an IT contingency plan. The contingency plan would
serve as a “user’s manual” for executing the strategy in the event of a disruption. Where
possible, examples or hypothetical situations are included to provide greater understanding.
4](https://image.slidesharecdn.com/contingencyplanningguide-13040880119244-phpapp02/85/Contingency-Planning-Guide-12-320.jpg)










![Preventive controls should be documented in the contingency plan, and personnel associated
with the system should be trained on how and when to use the controls. These controls should
be maintained in good condition to ensure their effectiveness in an emergency.
3.4 DEVELOP RECOVERY STRATEGIES
Recovery strategies provide a means to restore IT operations quickly and effectively following a
service disruption. The strategies should address disruption impacts and allowable outage times
identified in the BIA. Several alternatives should be considered when developing the strategy,
including cost, allowable outage time, security, and integration with larger, organization-level
contingency plans.
The selected recovery strategy should address the potential impacts identified in the BIA and
should be integrated into the system architecture during the design and implementation phases of
the system life cycle. The strategy should include a combination of methods that complement
one another to provide recovery capability over the full spectrum of incidents. A wide variety of
recovery approaches may be considered; the appropriate choice depends on the incident, type of
system and its operational requirements.10 Specific recovery methods further described in
Section 3.4.2 should be considered and may include commercial contracts with cold, warm, or
hot site vendors, mobile sites, mirrored sites, reciprocal agreements with internal or external
organizations, and service level agreements (SLAs) with the equipment vendors. In addition,
technologies such as Redundant Arrays of Independent Disks (RAID), automatic fail-over,
uninterruptible power supply (UPS), and mirrored systems should be considered when
developing a system recovery strategy.
3.4.1 Backup Methods
System data should be backed up regularly. Policies should specify the frequency of backups
(e.g., daily or weekly, incremental or full), based on data criticality and the frequency that new
information is introduced. Data backup policies should designate the location of stored data,
file-naming conventions, media rotation frequency, and method for transporting data offsite.
Data may be backed up on magnetic disk, tape, or optical disks (such as compact disks [CDs]).
The specific method chosen for conducting backups should be based on system and data
availability and integrity requirements. These methods include electronic vaulting, mirrored
disks (using direct access storage devices [DASD] or RAID),11 and floppy disks.
It is good business practice to store backed-up data offsite. Commercial data storage facilities
are specially designed to archive media and protect data from threatening elements. If using
offsite storage, data is backed up at the organization’s facility and then labeled, packed, and
transported to the storage facility. If the data is required for recovery or testing purposes, the
organization contacts the storage facility requesting specific data to be transported to the
10 Section 5.0, IT System Specific Contingency Considerations, provides detailed discussion of recovery methods applicable to
specific IT systems.
11 DASD and RAID are discussed in Section 5.0.
19](https://image.slidesharecdn.com/contingencyplanningguide-13040880119244-phpapp02/85/Contingency-Planning-Guide-27-320.jpg)














![notified of the incident. Damage assessment procedures may be unique for the particular system;
however, the following areas should be addressed:
Cause of the emergency or disruption
Potential for additional disruptions or damage
Area affected by the emergency
Status of physical infrastructure (e.g., structural integrity of computer room, condition of
electric power, telecommunications, and heating, ventilation, and air-conditioning
[HVAC])
Inventory and functional status of IT equipment (e.g., fully functional, partially
functional, and nonfunctional)
Type of damage to IT equipment or data (e.g., water damage, fire and heat, physical
impact, and electrical surge)
Items to be replaced (e.g., hardware, software, firmware, and supporting materials)
Estimated time to restore normal services.
Personnel with damage assessment responsibilities should understand and be able to perform
these procedures in the event the paper plan is unavailable during the situation. Once the impact
to the system has been determined, the appropriate teams should be notified of updated
information and planned response to the situation. Notifications should be executed using the
procedures described in Section 4.2.1.
4.2.3 Plan Activation
The IT contingency plan should be activated only when the damage assessment indicates that
one or more of the activation criteria for that system are met. If an activation criterion is met, the
Contingency Planning Coordinator or CIO (as appropriate) should activate the plan.26
Activation criteria for events are unique for each organization and should be stated in the
contingency planning policy statement. Criteria may be based on—
Safety of personnel and/or extent of damage to the facility
Extent of damage to system (e.g., physical, operational, or cost)
Criticality of the system to the organization’s mission (e.g., critical infrastructure
protection asset)
Anticipated duration of disruption.
26 For this document, it is assumed that either the IT Contingency Planning Coordinator or the CIO has the authority to
implement the contingency plan. That authority may vary based on the organization or system; however, the individual with
this authority should be designated clearly in the plan. Only one individual should have this authority and a successor should
be clearly identified to assume that responsibility if necessary.
36](https://image.slidesharecdn.com/contingencyplanningguide-13040880119244-phpapp02/85/Contingency-Planning-Guide-44-320.jpg)