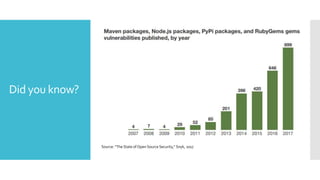
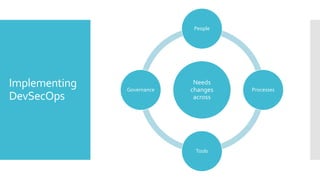
This document discusses DevSecOps, which involves infusing security practices into the development lifecycle to enable faster release cycles while maintaining security. It notes that over 53,000 cybersecurity incidents occurred in India in 2017. Implementing DevSecOps requires changes across an organization's people, processes, tools, and governance to embed security responsibilities across all teams. The typical DevSecOps pipeline shifts security left through activities like threat modeling, security testing, and monitoring throughout the development lifecycle.