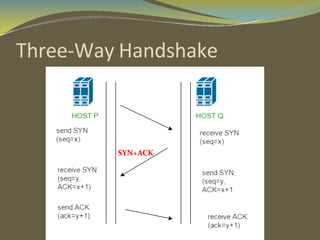
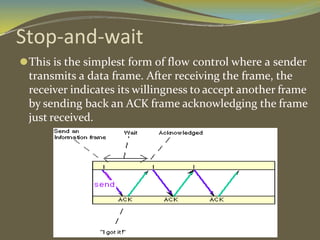
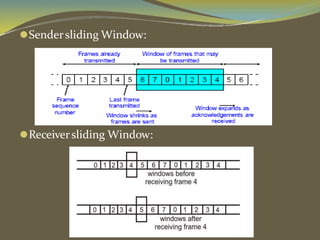
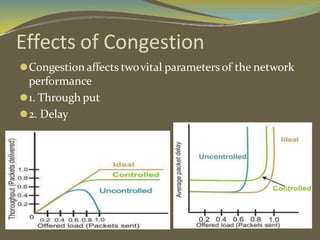
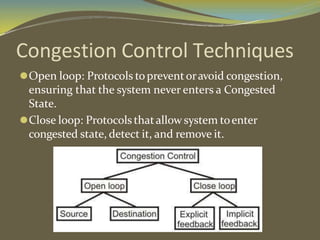
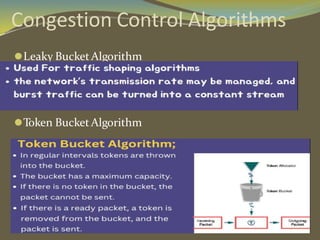
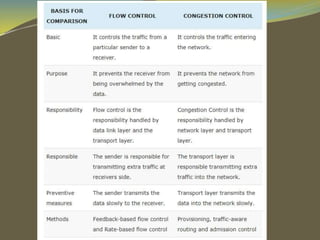
The document discusses various aspects of connection establishment and data transmission reliability in computer networks. It describes how connection-oriented transport protocols like TCP require a connection to be established before data exchange using either a two-way or three-way handshake. The three-way handshake involves a SYN, SYN-ACK, and ACK sequence to synchronize sequence numbers and negotiate parameters. Flow control mechanisms like stop-and-wait and sliding windows are used to ensure reliable data delivery. Congestion control is also important to manage network load and avoid degradation in performance.