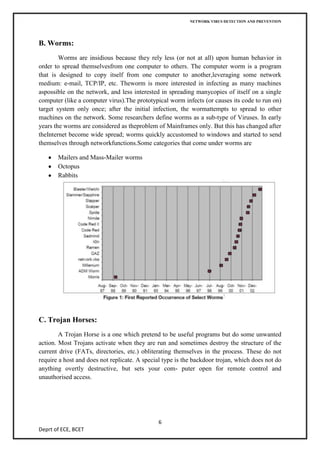
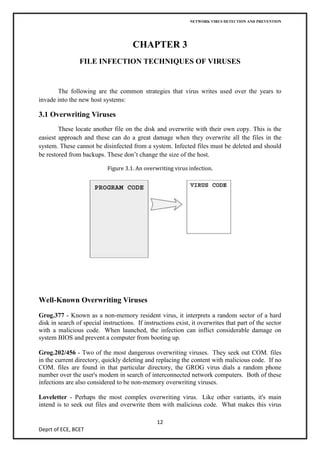
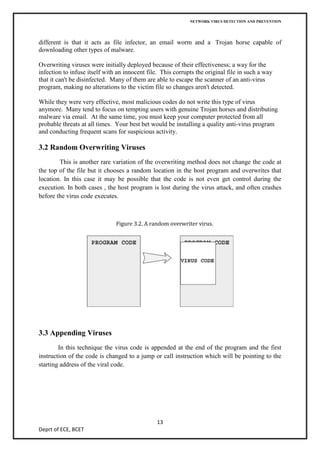
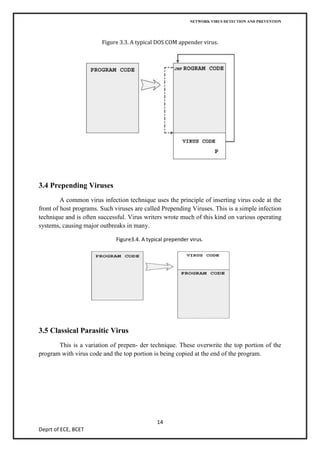
The document discusses network virus detection and prevention, describing different types of viruses like worms, Trojans, and viruses, how they spread and infect systems through various techniques like overwriting files or boot sectors. It also covers methods of identifying viruses through signature-based detection or heuristics, as well as prevention techniques like generations of antivirus software and case studies of worms like Slammer and Blaster.












![NETWORK VIRUS DETECTION AND PREVENTION
CHAPTER 5
Identification methods
One of the few solid theoretical results in the study of computer viruses is Frederick B.
Cohen's 1987 demonstration that there is no algorithm that can perfectly detect all possible
viruses.[The proof relies on the "infect" and "spread" abilities of computer viruses. While
common, the "infect" and "spread" abilities of a computer code, which create the "replicate"
ability, are not necessarily contained in malware. "Computer virus", in its recent meaning,
and "malware" are overlapping terms, but not synonymous. The difference is between a code
with the ability to "infect" and "spread" and a code with malicious purpose.
There are several methods which antivirus software can use to identify malware.
Signature based detection is the most common method. To identify viruses and other
malware, antivirus software compares the contents of a file to a dictionary of virus signatures.
Because viruses can embed themselves in existing files, the entire file is searched, not just as
a whole, but also in pieces.[16]
Heuristic-based detection, like malicious activity detection, can be used to identify
unknown viruses.
File emulation is another heuristic approach. File emulation involves executing a program in
a virtual environment and logging what actions the program performs. Depending on the
actions logged, the antivirus software can determine if the program is malicious or not and
then carry out the appropriate disinfection actions.
5.1 Signature-based detection:
Traditionally, antivirus software heavily relied upon signatures to identify malware.
This can be very effective, but cannot defend against malware unless samples have already
been obtained and signatures created. Because of this, signature-based approaches are not
effective against new, unknown viruses.
As new viruses are being created each day, the signature-based detection approach requires
frequent updates of the virus signature dictionary. To assist the antivirus software companies,
the software may allow the user to upload new viruses or variants to the company, allowing
the virus to be analyzed and the signature added to the dictionary. Signatures are obtained by
human experts using reverse engineering. An example of software used in reversed
engineering is Interactive Disassembler. Such a software does not implement antivirus
protection, but facilitates human analysis.
Although the signature-based approach can effectively contain virus outbreaks, virus authors
have tried to stay a step ahead of such software by writing "oligomorphic", "polymorphic"
and, more recently, "metamorphic" viruses, which encrypt parts of themselves or otherwise
20
Deprt of ECE, BCET](https://image.slidesharecdn.com/networkvirusdetectionprevention-120429070606-phpapp01/85/Network-virus-detection-prevention-20-320.jpg)






![NETWORK VIRUS DETECTION AND PREVENTION
REFERENCES
[1] Peter Szor, The Art of Computer Virus and Defence, Harlow, England: Addison Wesely
Professional, 2005.
[2] Norman, Norman book on Computer Virus, Norman ASA, 2003.
[3] Dan Xu, Xiang Li, and Xian Fan Wang, Mechanisms for Spreading of Computer Virus on
the Internet: An Overview, IEEE Computer Society 2004, 601-606.
[4] Darrell M. Kienzie, and Matthew C. Elder, Recent Worms: A Survey and Trends,
Washington, DC, USA: WORM-2003
[5] David Moore, Vern Paxson, Stefan Savage, Colleen, Stuart Staniford and Nicholas
Weaver, Inside the Slammer Worm, IEEE Security and Privacy, 2003.
[6] Thomas Subendorfer, Arno Wagner, TheusHossmann, and Bernhard Plattner, Flow-Level
Traffic Analysis of the Blaster and Sobig Worm Outbreaks in an Internet Backbone,
Springer-Verlag Berlin Heidelberg 2005.
[7] Nicholas Weaver, Vern Paxson, Stuart Staniford, and Robert Cunnigham, A Taxonomy of
Computer Worms, Washington, DC, USA: WORM-2003.
[8] H. Kopka and P. W. Daly, A Guide to LATEX, 3rd ed. Harlow, England: Addison-
Wesley, 1999.
31
Deprt of ECE, BCET](https://image.slidesharecdn.com/networkvirusdetectionprevention-120429070606-phpapp01/85/Network-virus-detection-prevention-31-320.jpg)