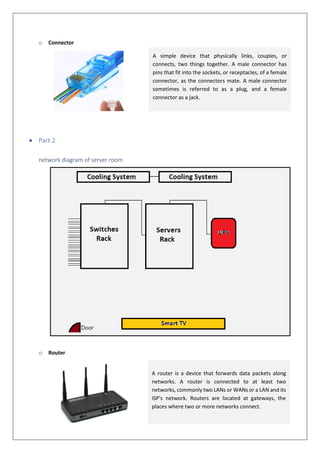
This document provides information about various computer networking concepts and components. It discusses networking faceplates, cables, connectors, routers, switches, wireless access points and controllers. It also covers networking protocols like IP addressing and topics like file downloading, uploading and network troubleshooting. The document is meant as a guide for a practical computer networking lab session.