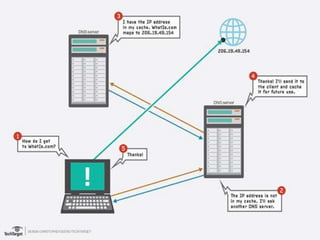
The document discusses the Domain Name System (DNS) and how it works. DNS maps domain names that people use, like facebook.com, to IP addresses like 31.13.72.36 that computers use to locate websites. DNS works in a hierarchical structure, with DNS servers answering requests from inside and outside their domains and passing requests between each other until the authoritative server for that domain is reached. Caching responses promotes efficiency by allowing servers to quickly respond to repeat requests.