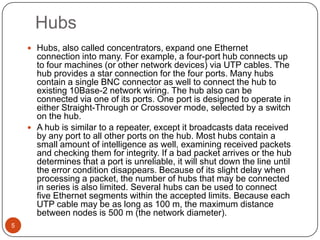
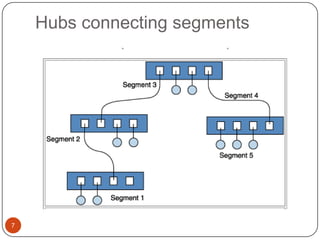
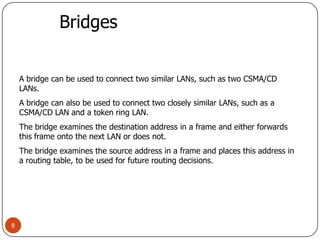
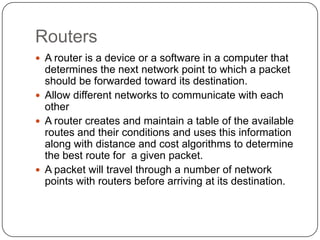
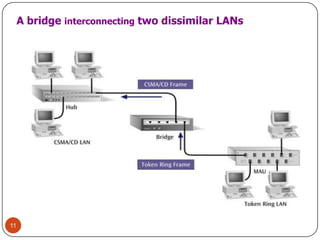
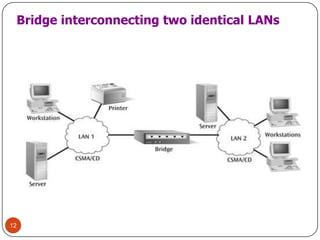
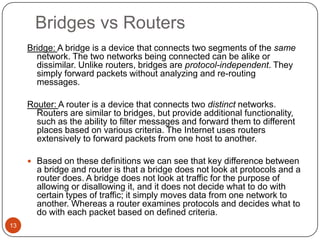
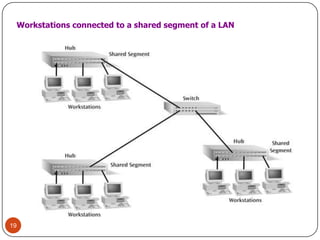
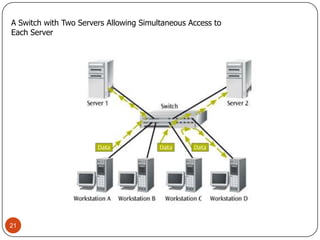
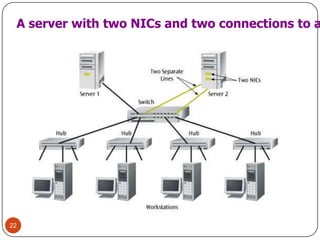
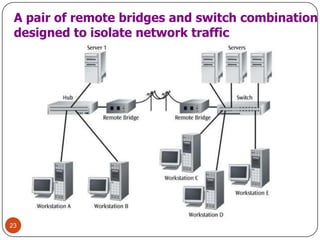
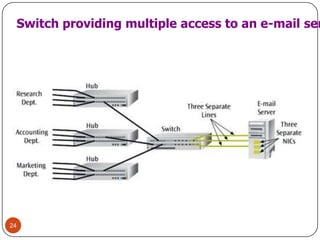
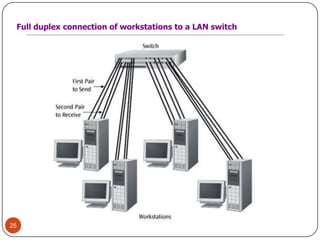
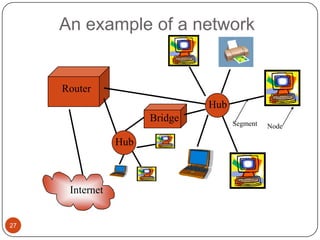
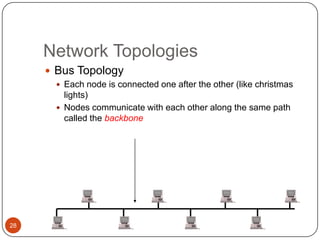
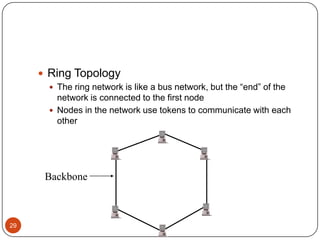
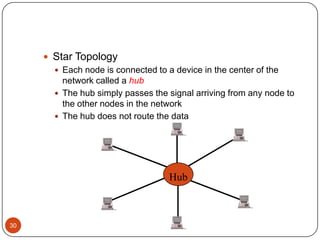
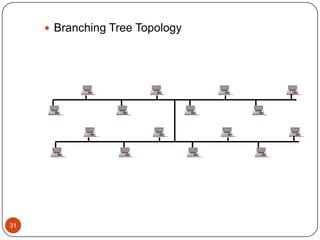
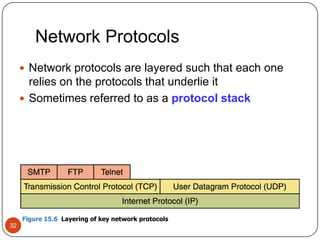
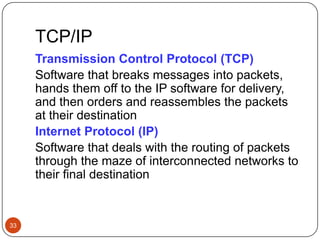
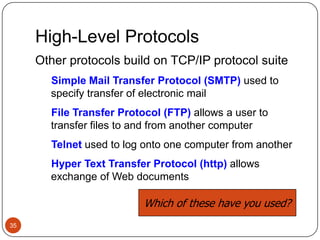
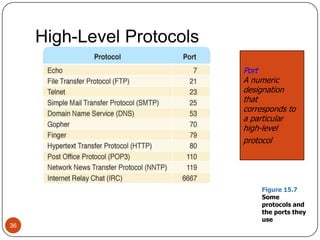
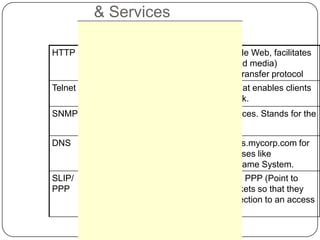
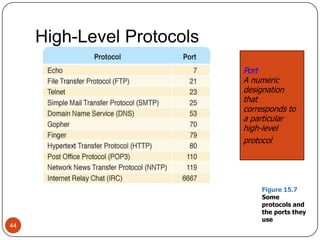
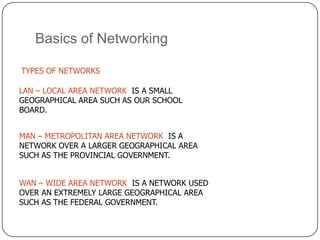
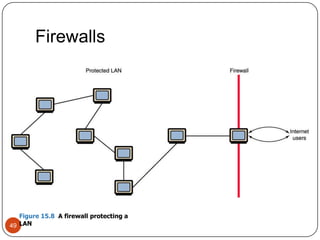
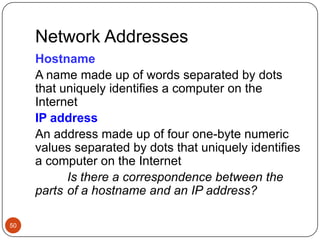
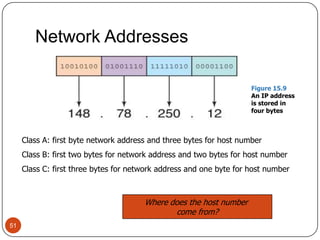
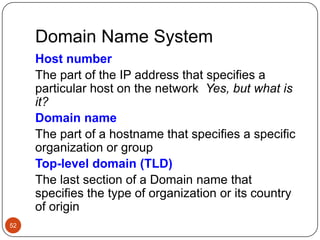
Computer networking devices allow computers to communicate over a network. A network interface card (NIC) connects each computer to the network. Hubs connect multiple devices and broadcast all data to every port. Switches examine destination addresses and forward frames to the specific port, improving efficiency over hubs. Routers connect different networks and determine the best route to forward packets between networks.