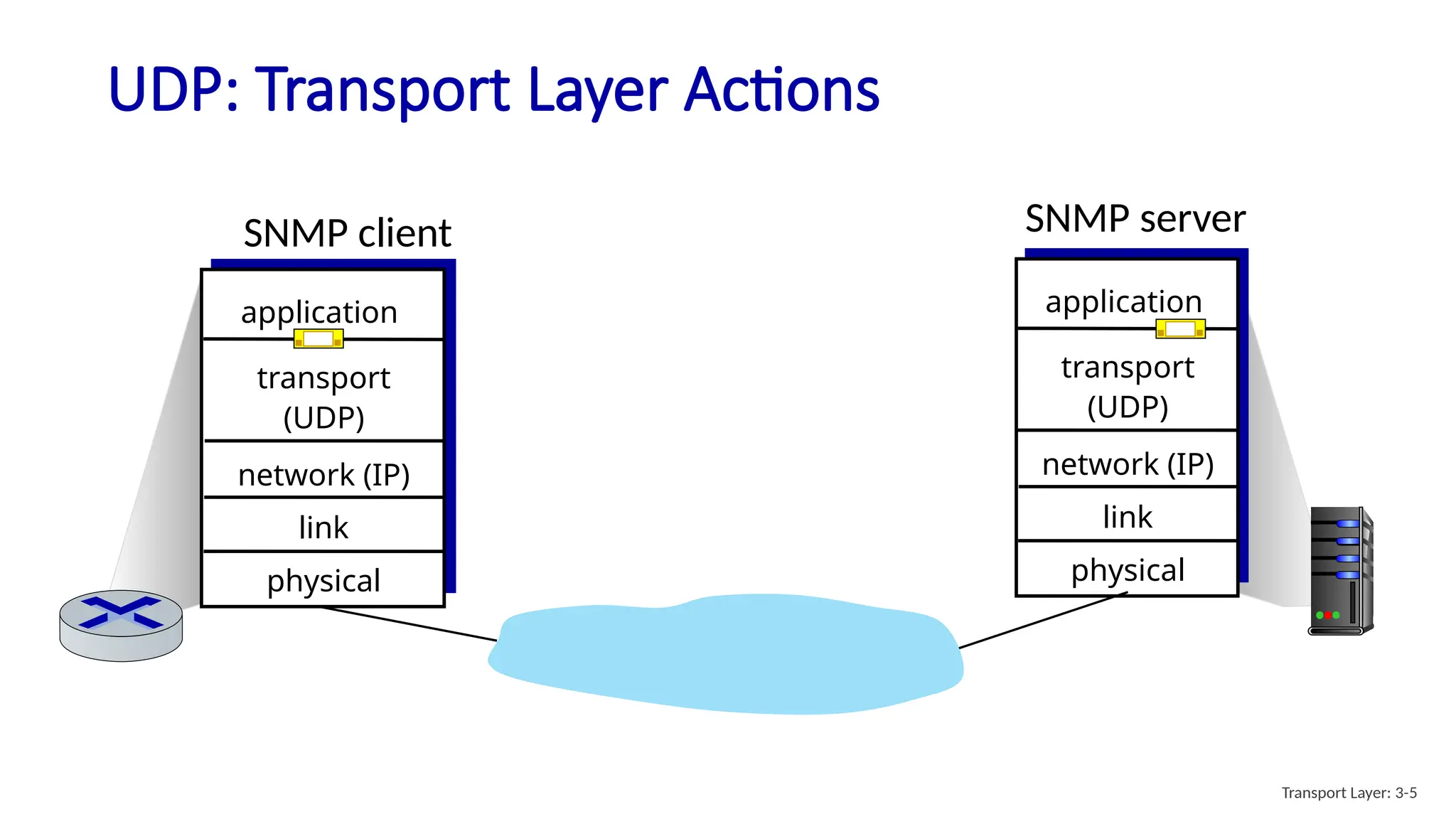
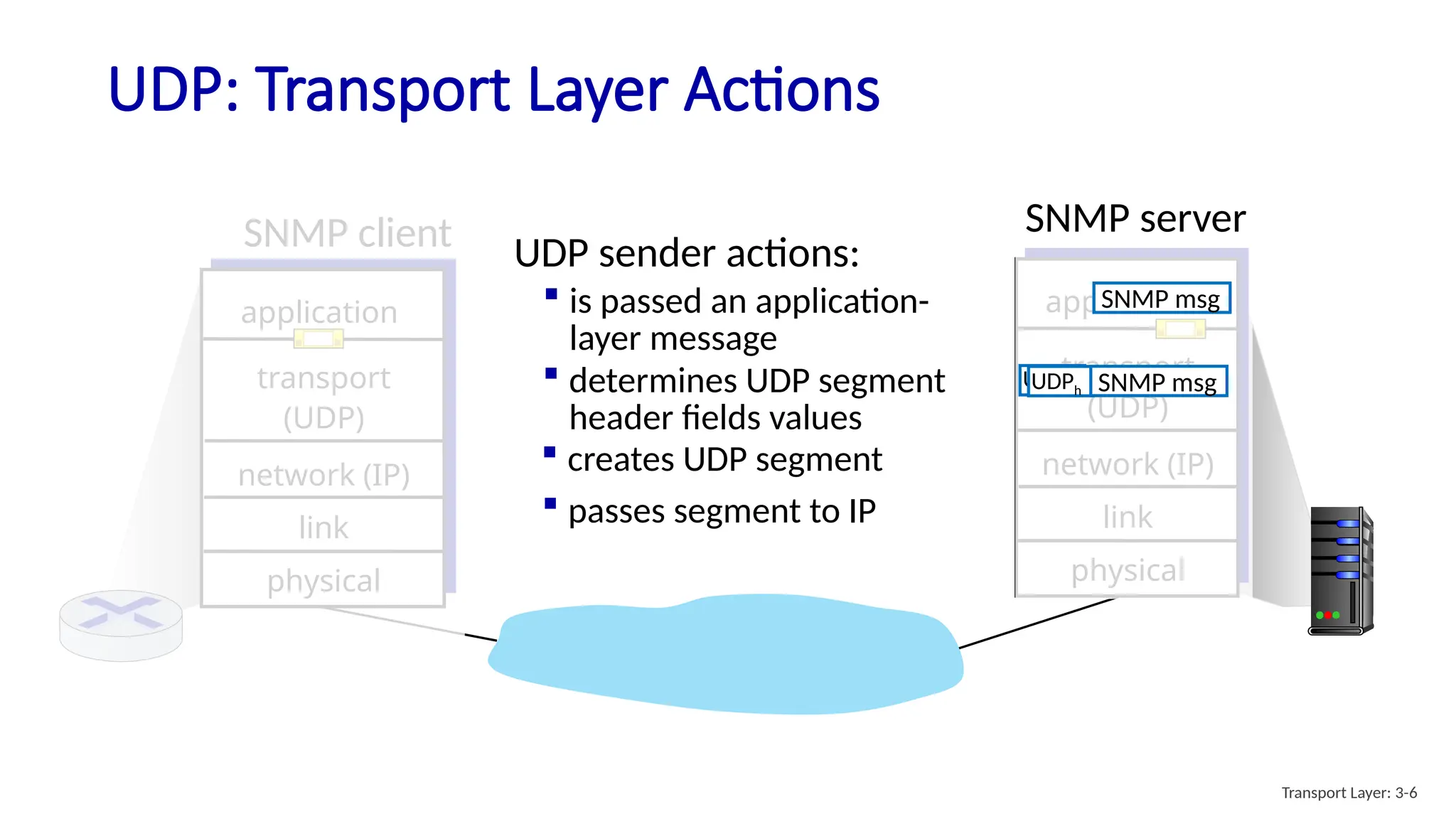
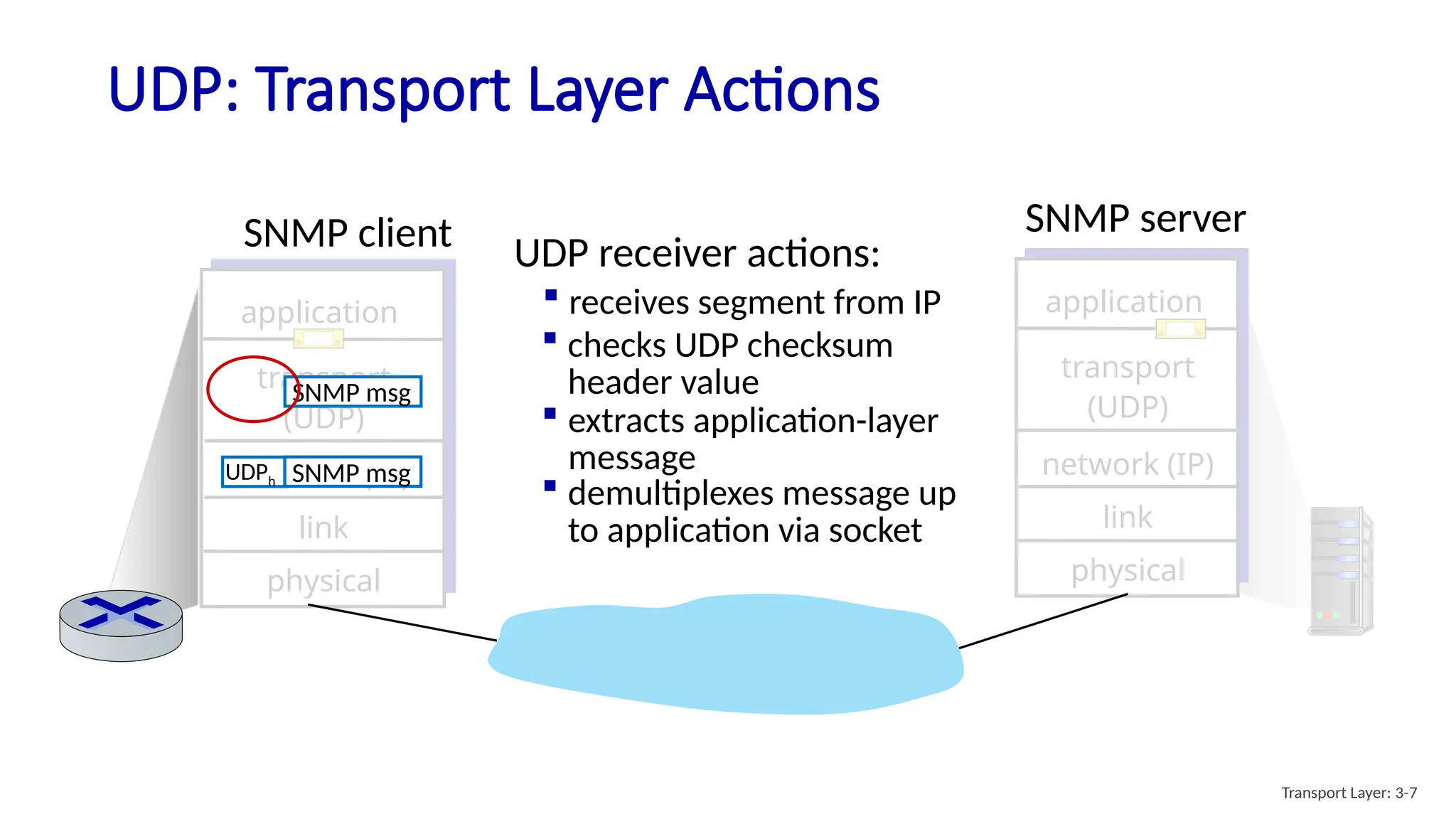
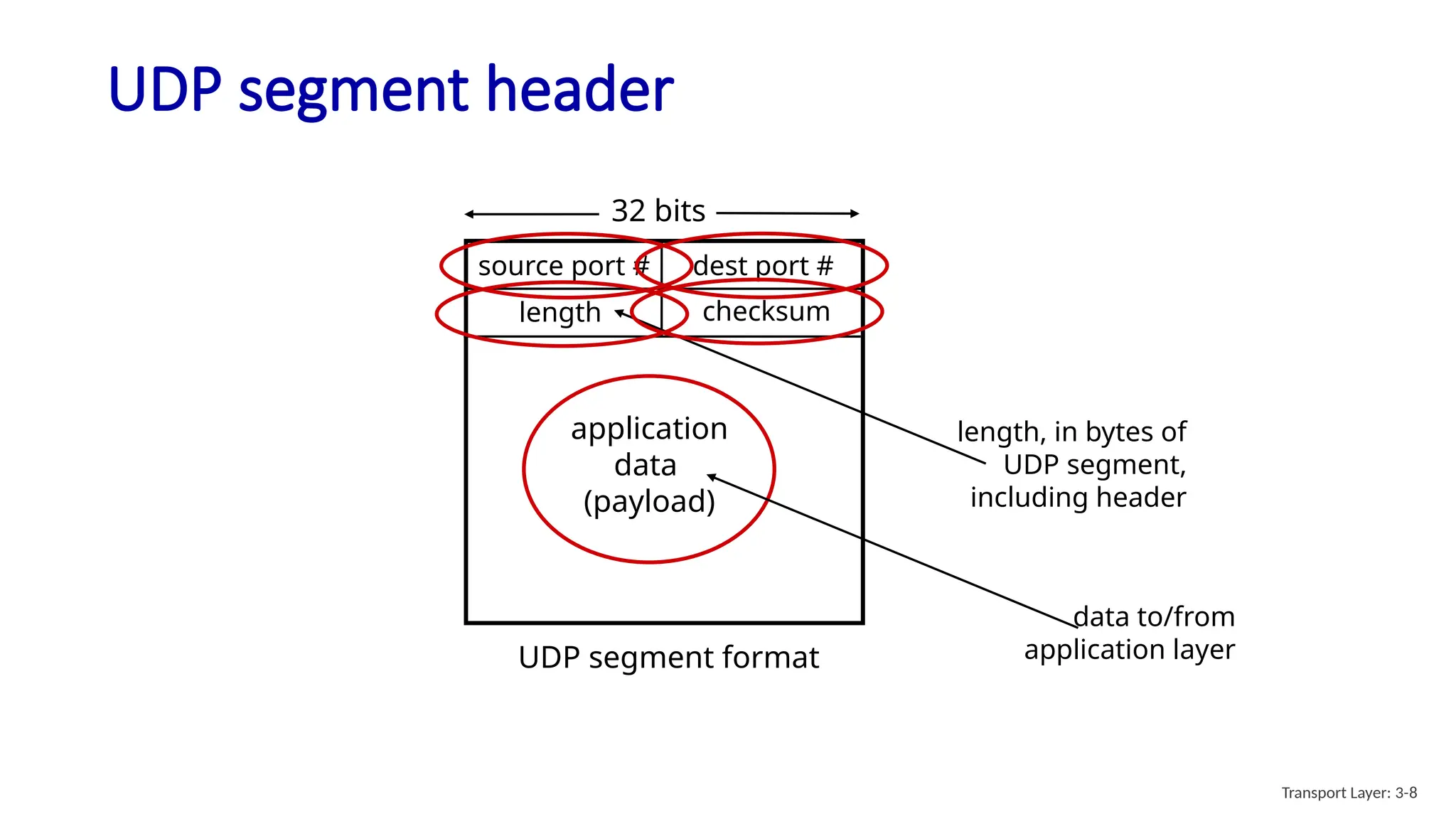
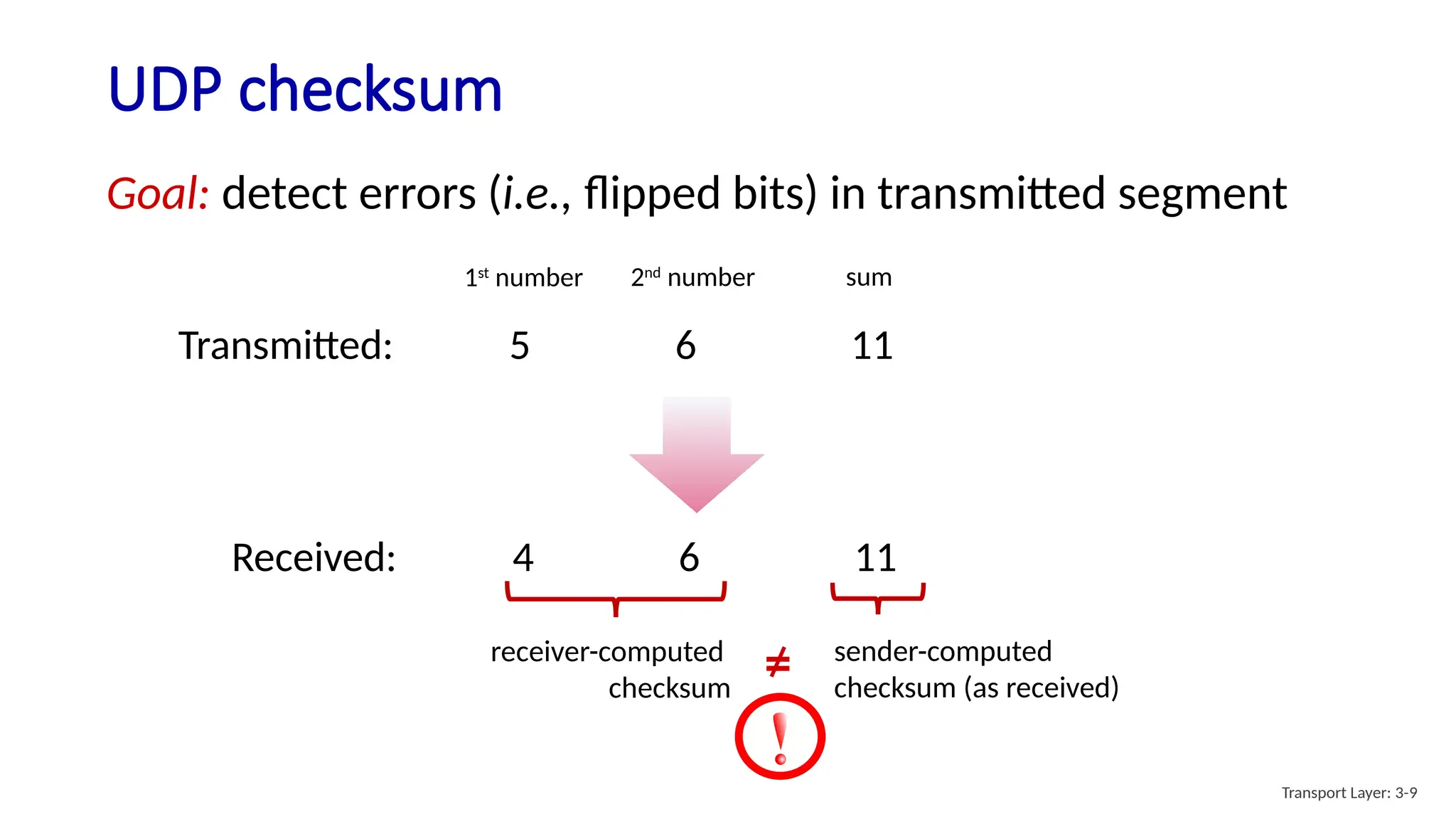
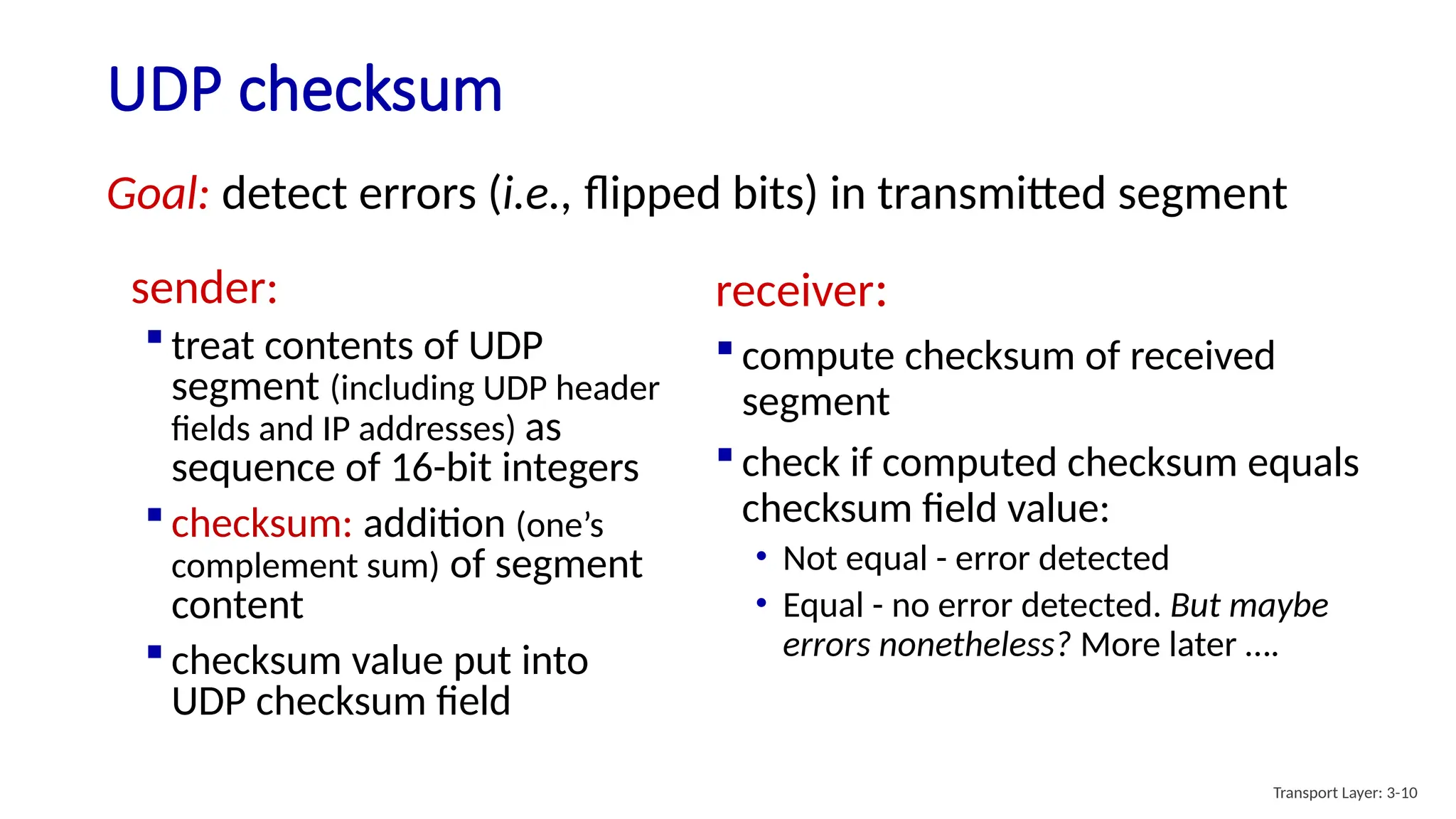
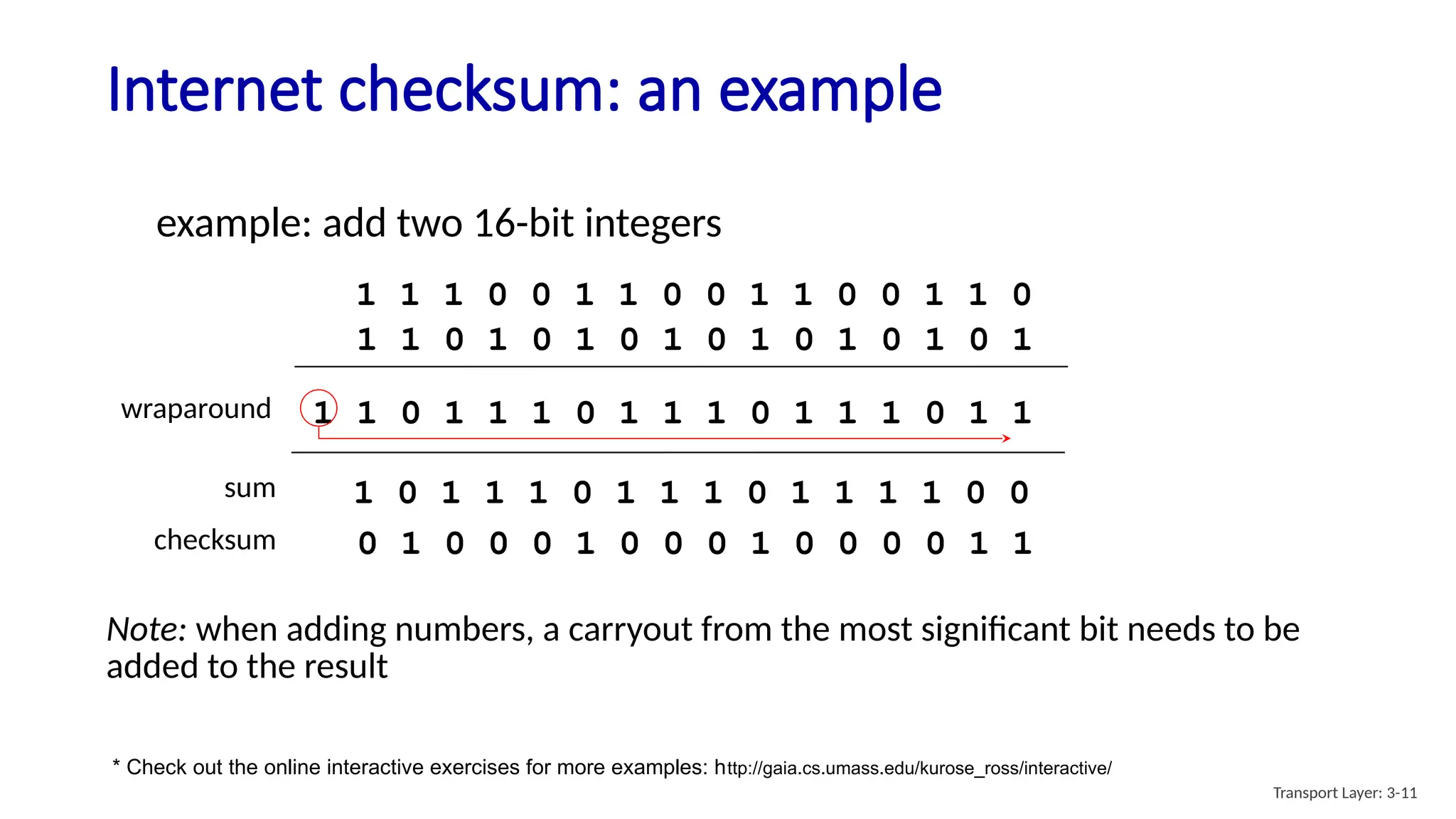
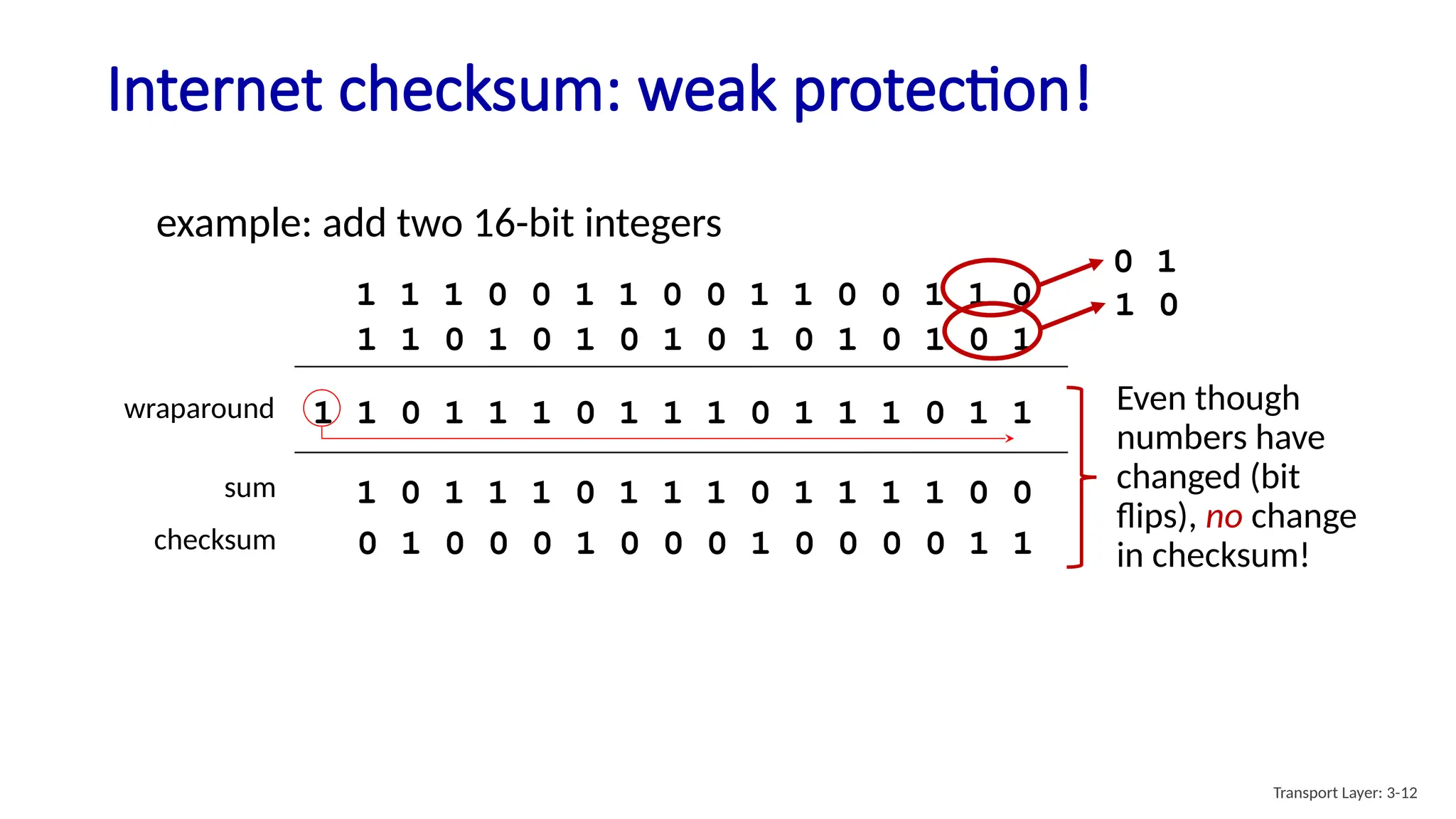
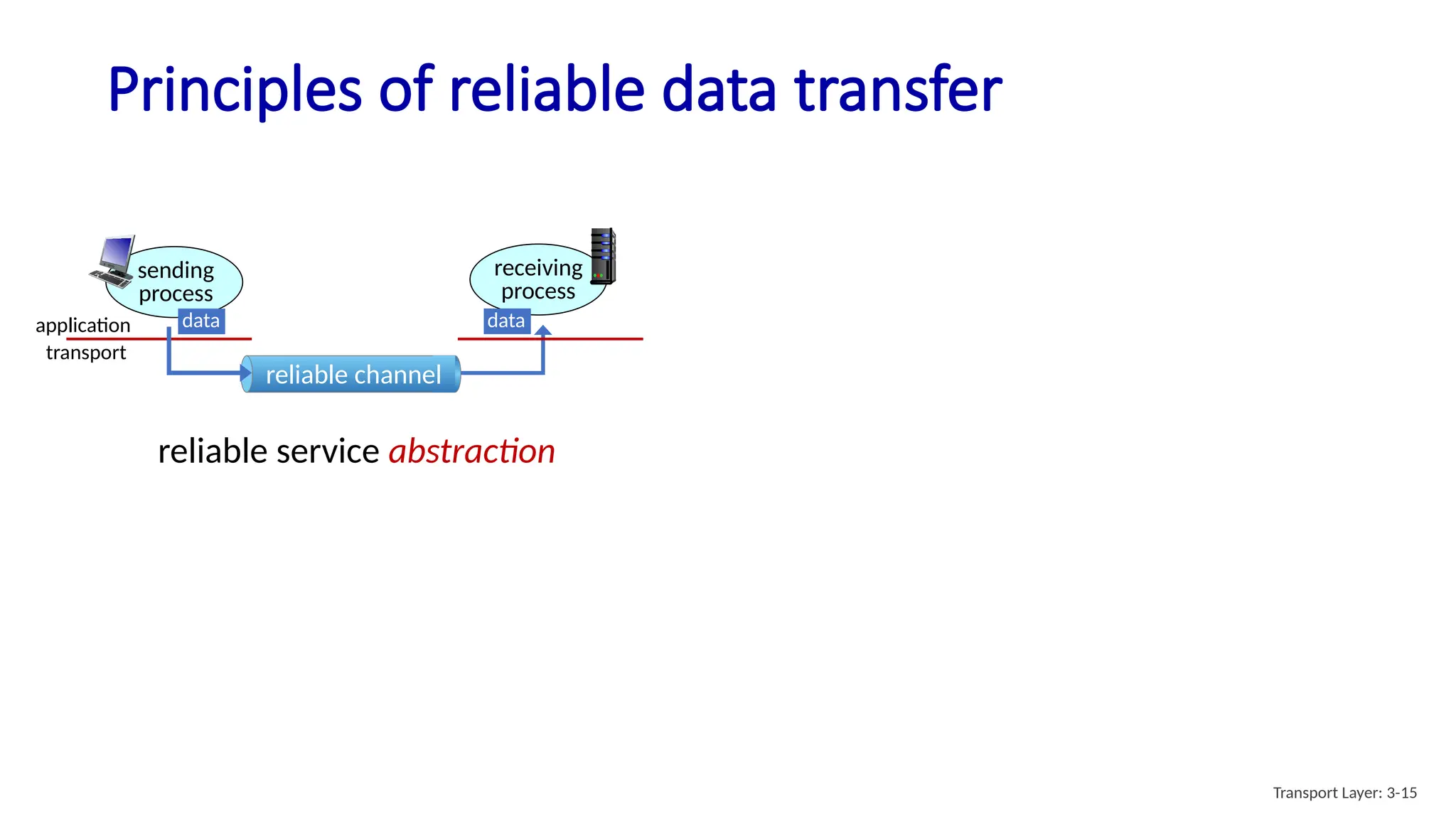
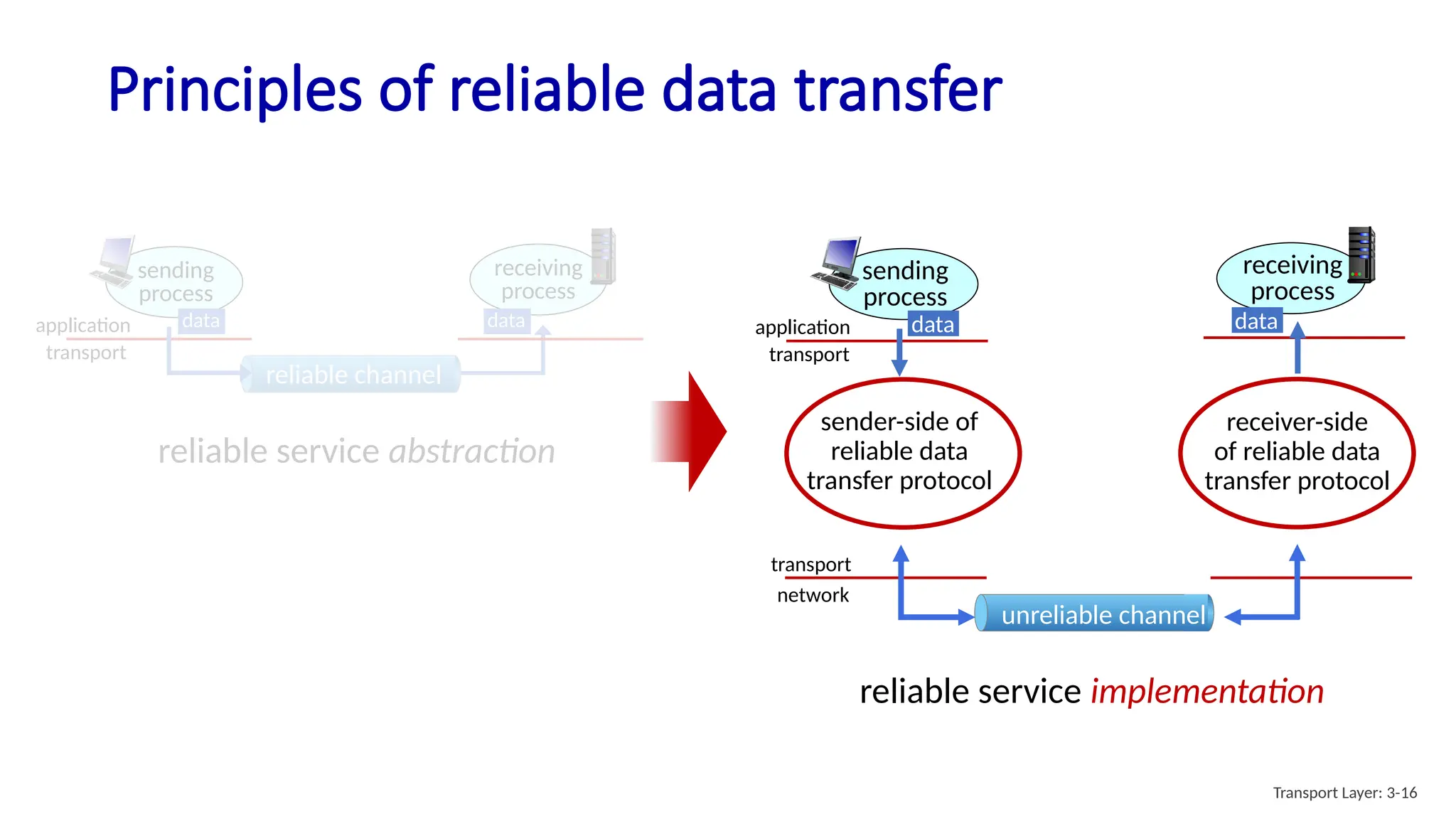
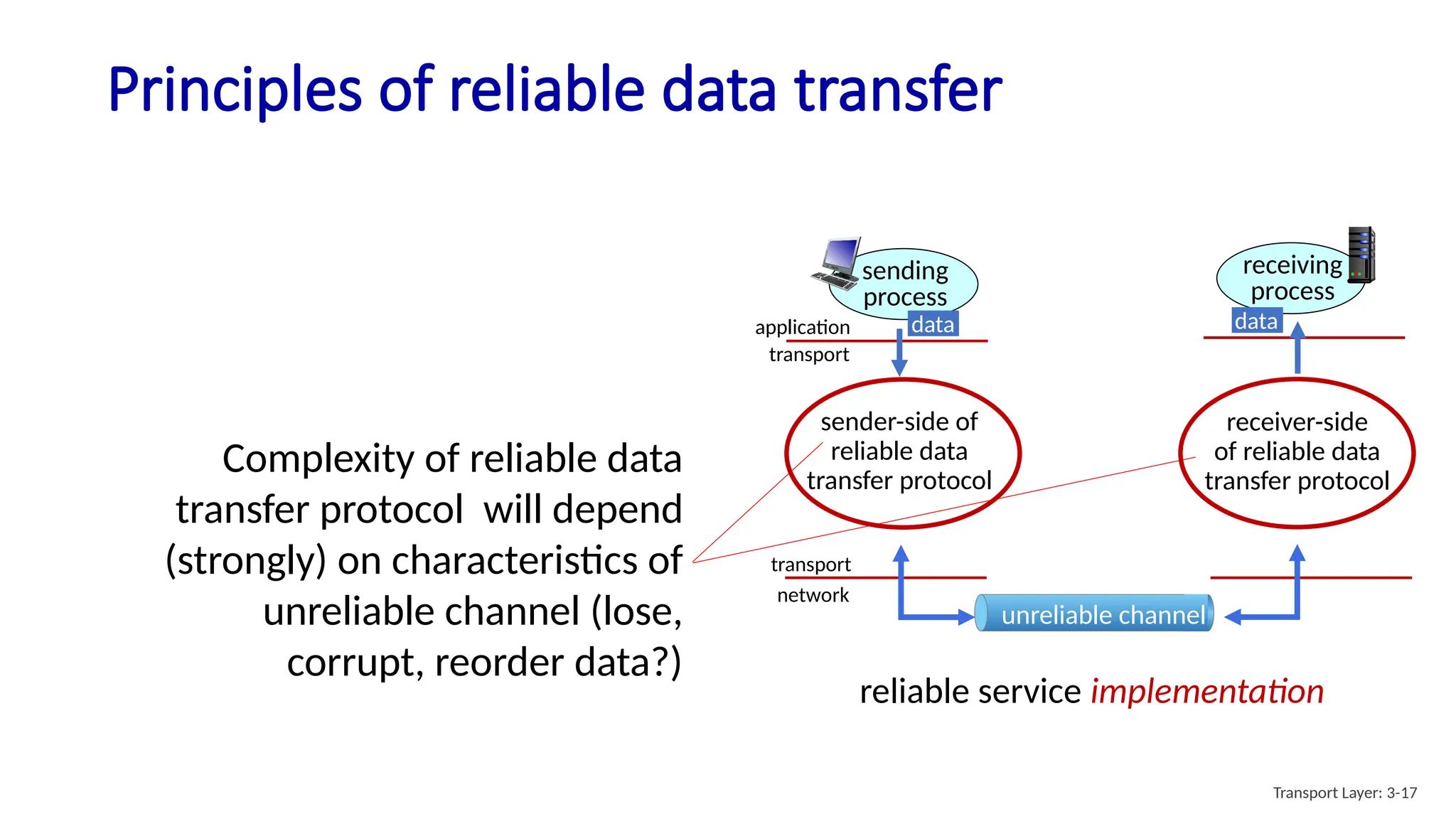
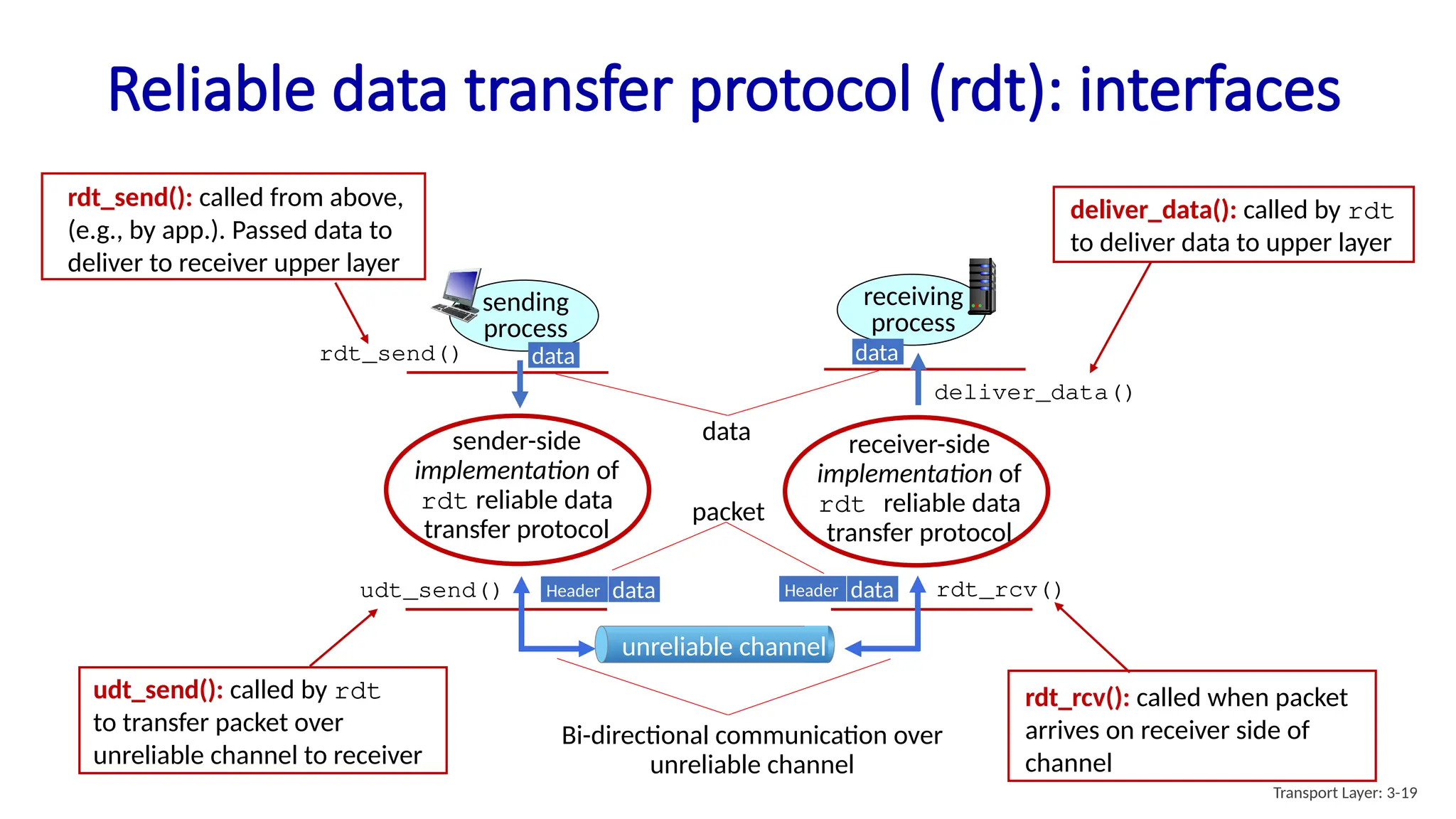
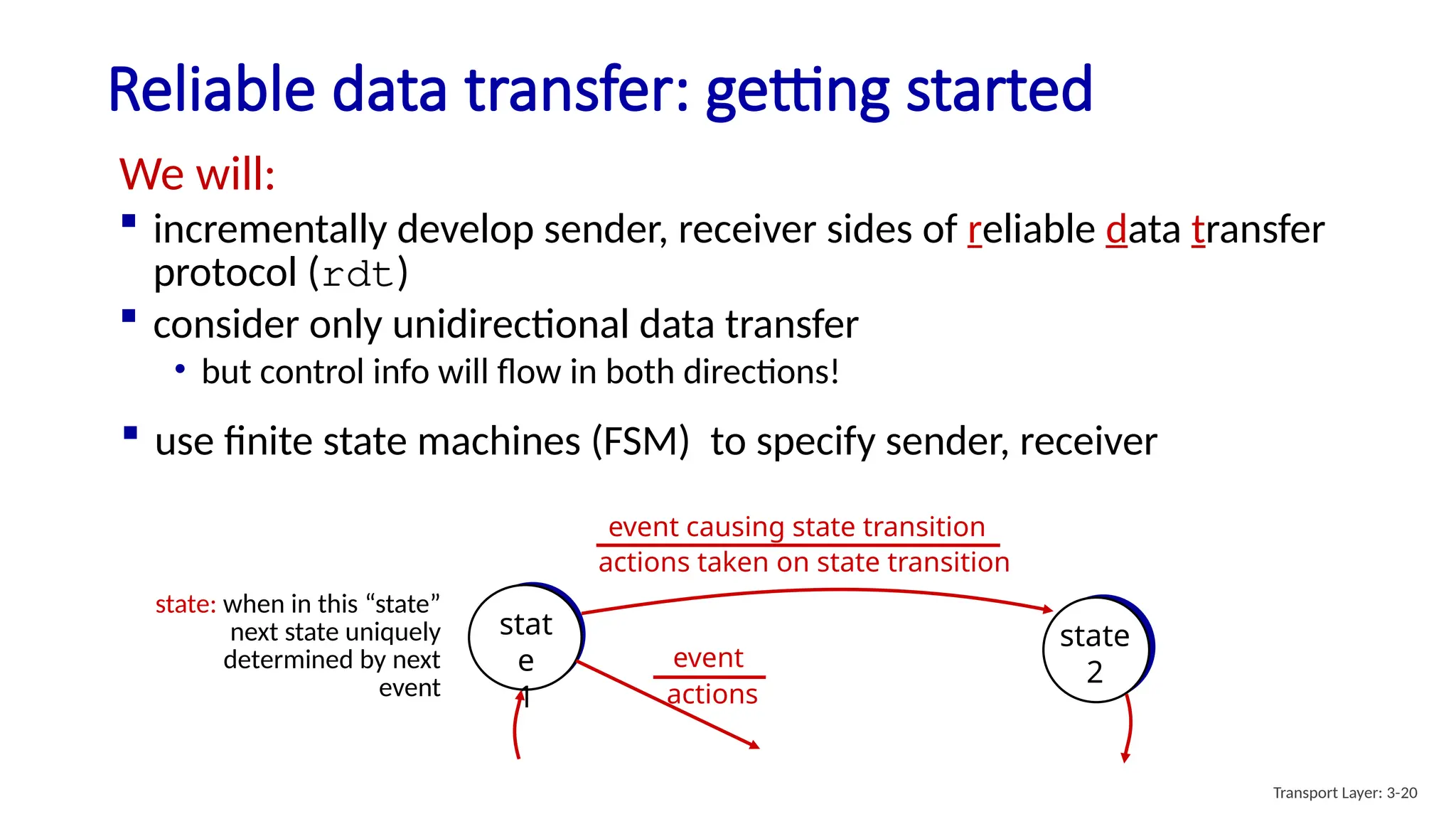
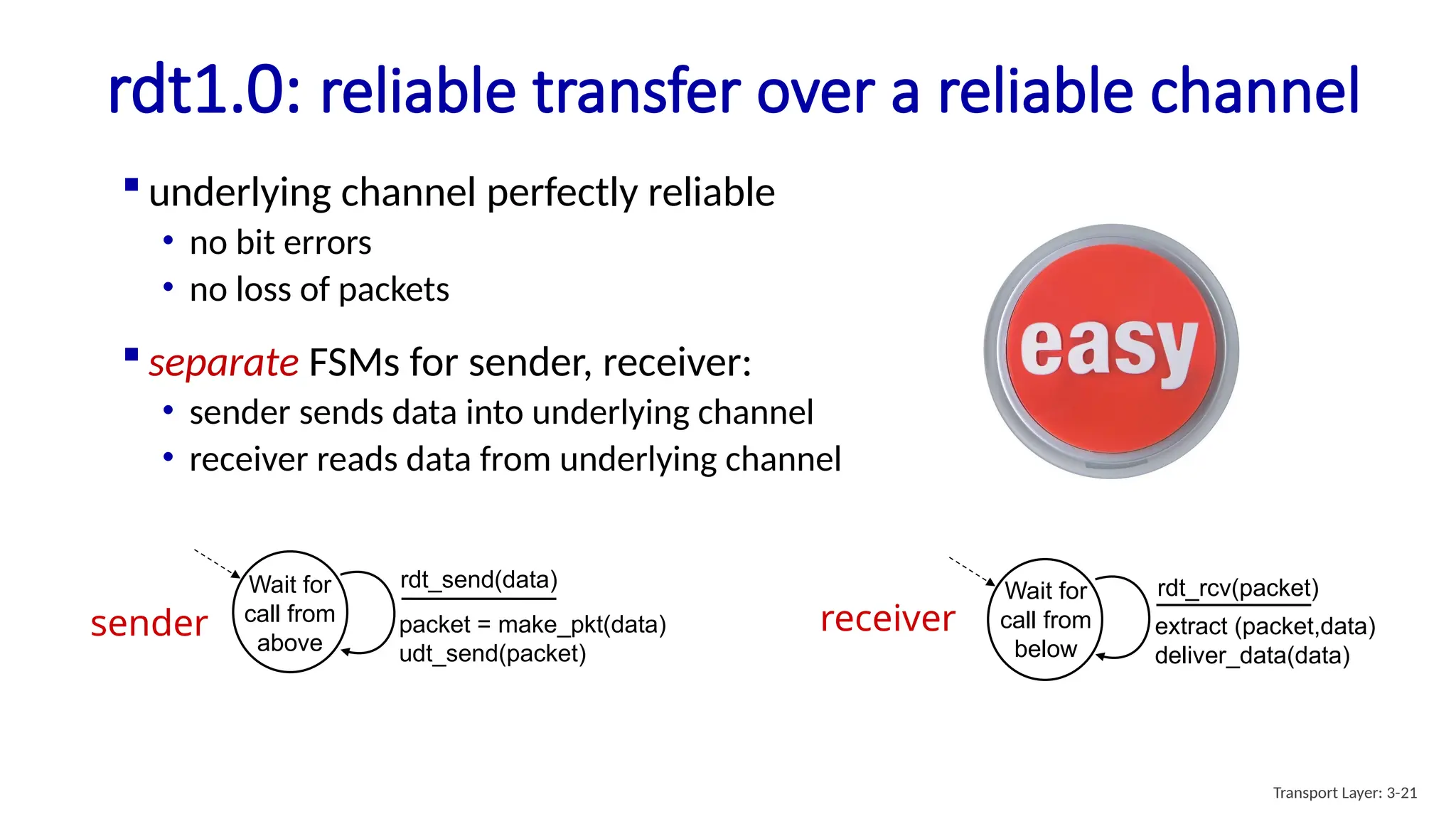
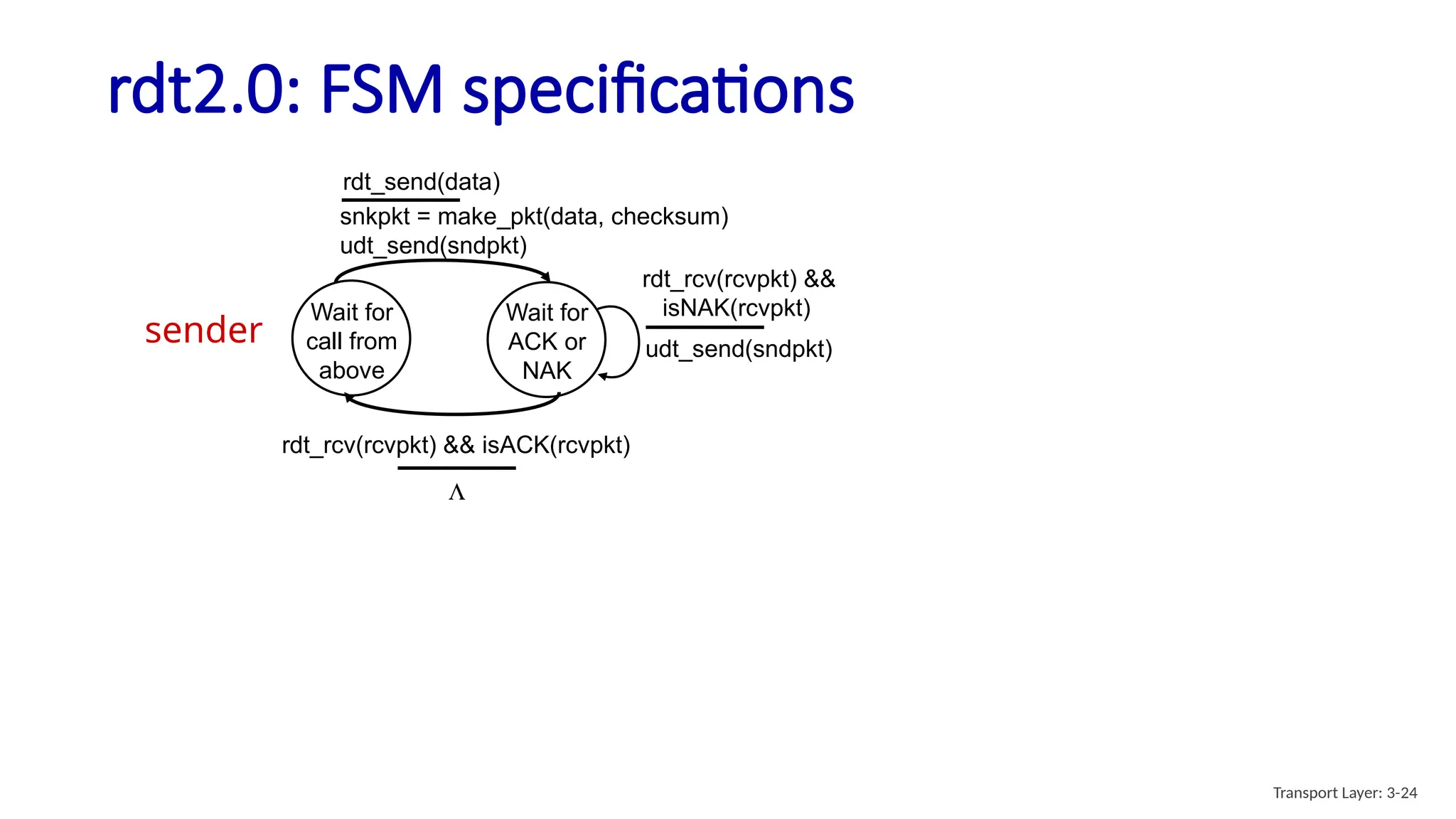
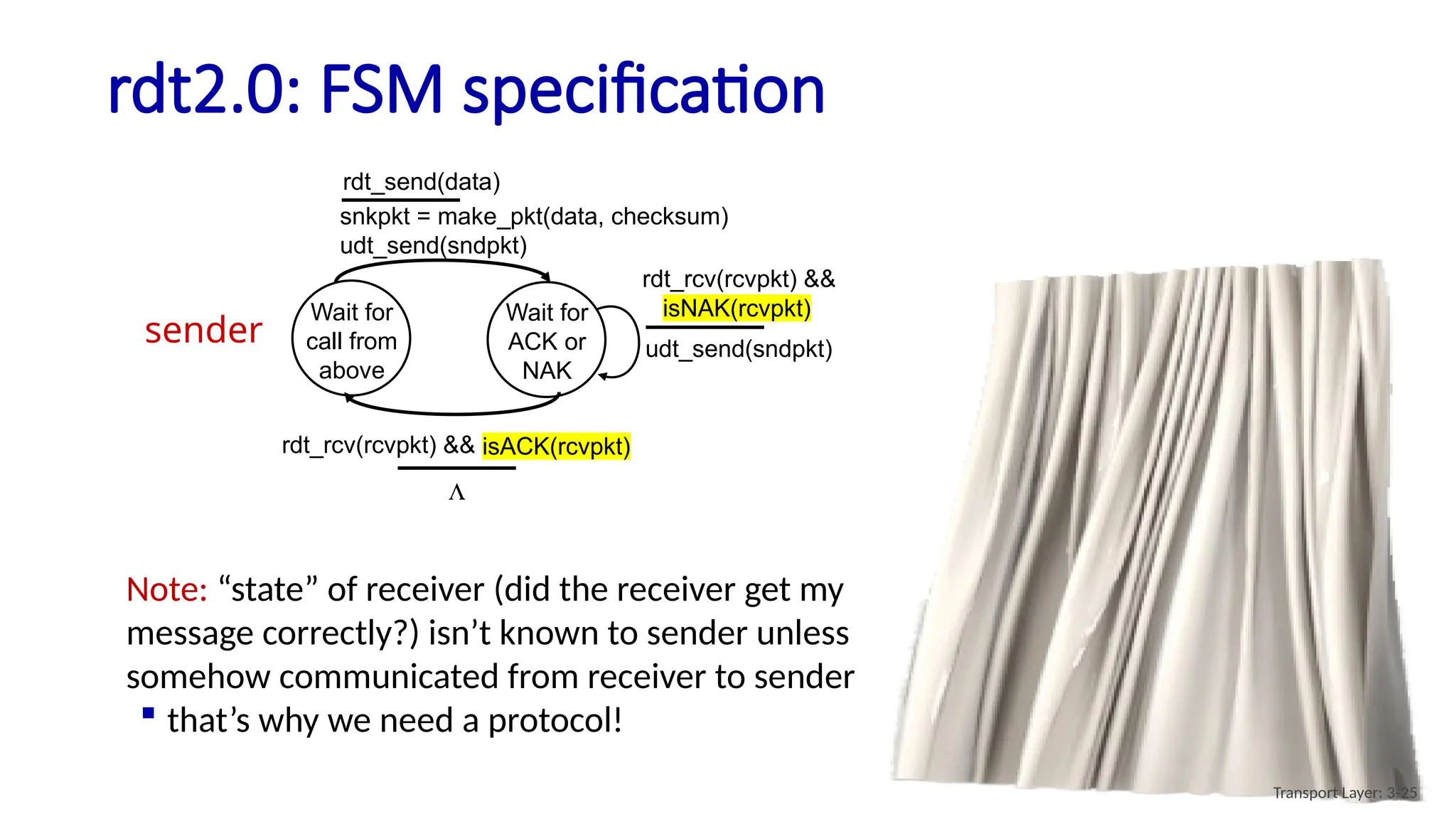
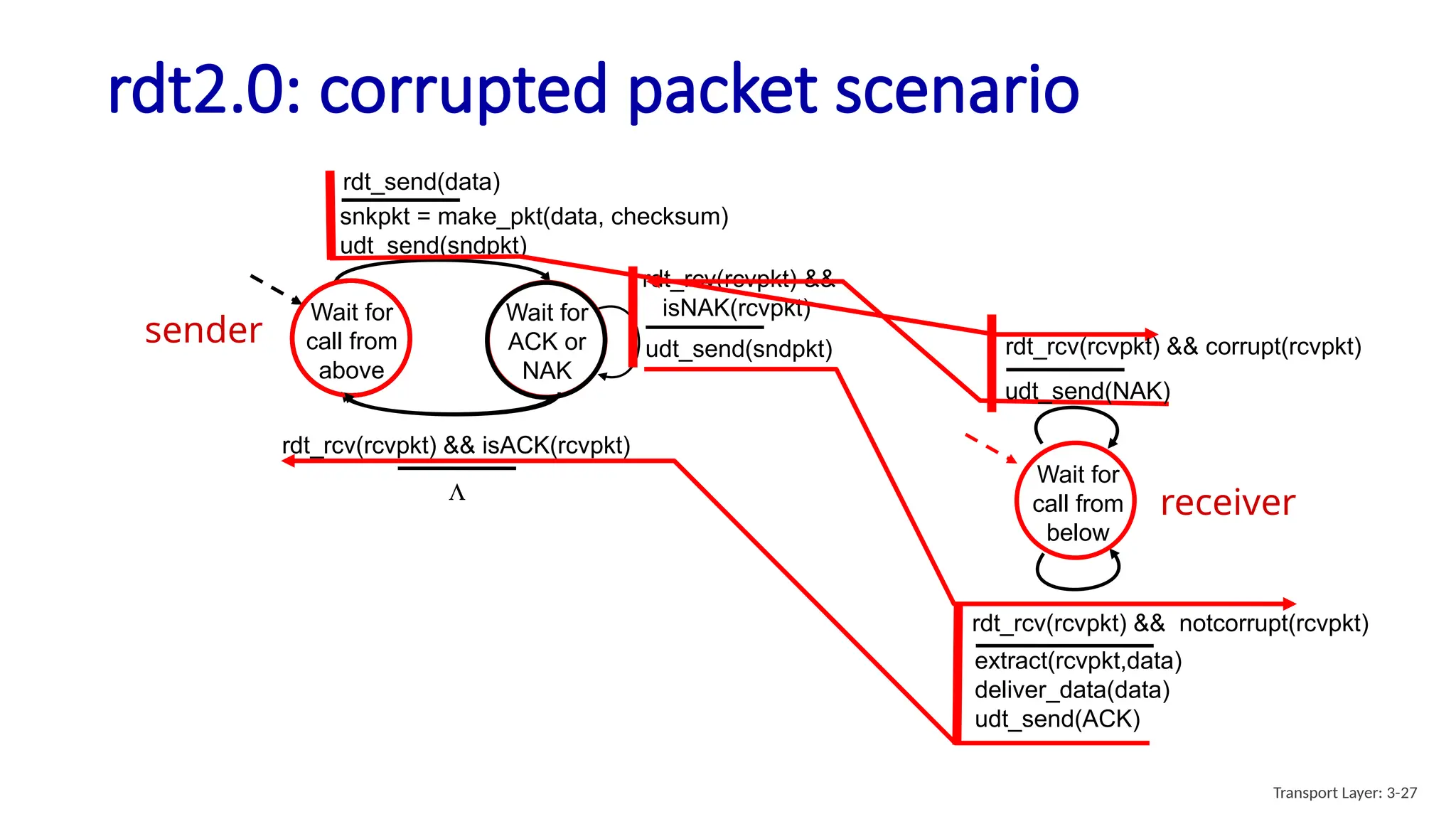
Chapter 3 discusses transport-layer services, focusing on the User Datagram Protocol (UDP) and its features such as connectionless transport and lack of congestion control. UDP is characterized as a 'best effort' service allowing for rapid transmission, commonly used in applications like streaming and Simple Network Management Protocol (SNMP). It emphasizes the need for reliability at the application layer when required, alongside principles of reliable data transfer and error detection methods like checksums.

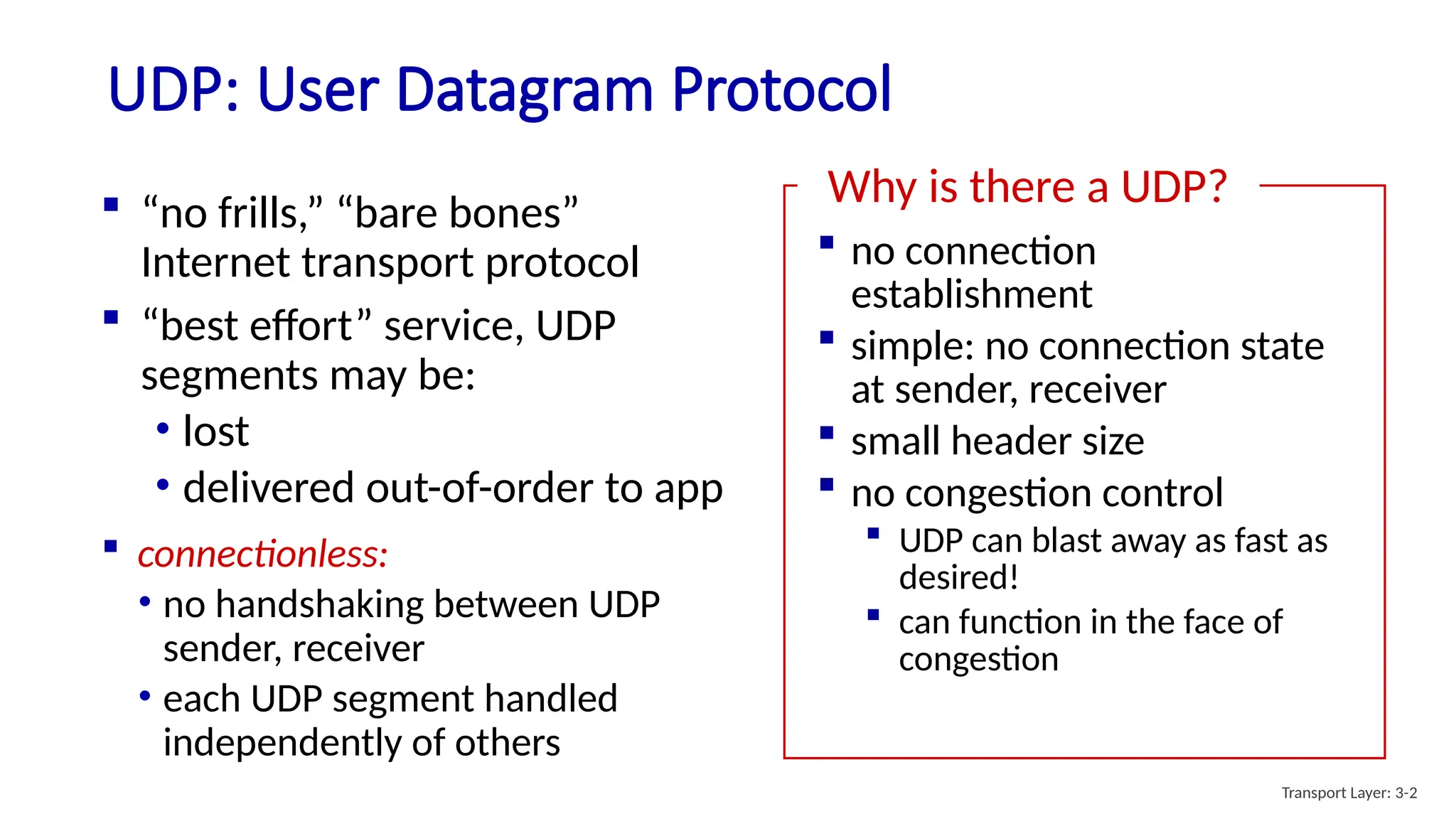
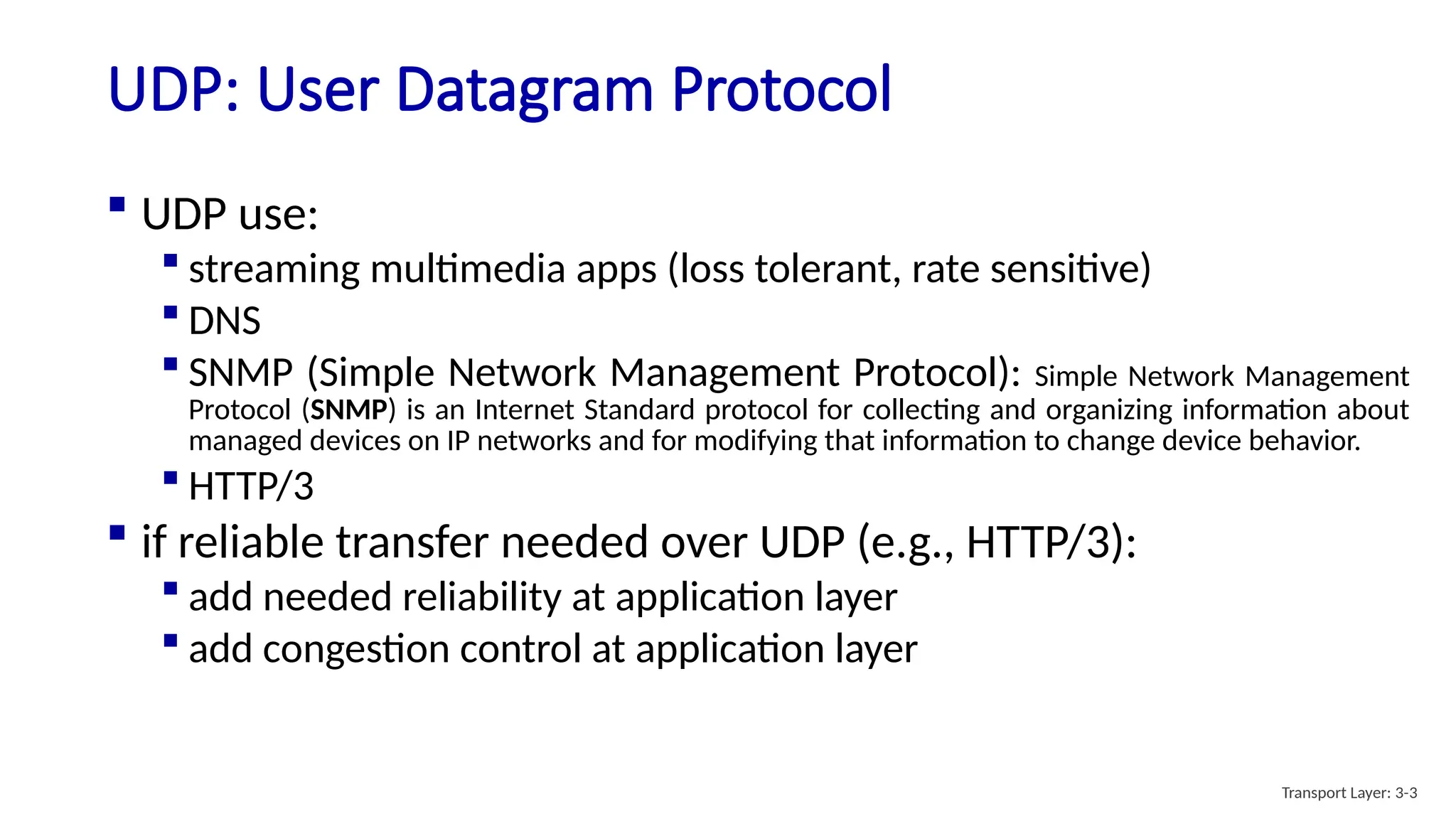
![UDP: User Datagram Protocol [RFC 768]
Transport Layer: 3-4](https://image.slidesharecdn.com/lecture15transportlayerpart021-241215053909-90fb2785/75/Lecture-15-Transport-Layer-Part02-1-pptx-4-2048.jpg)