The document discusses data link control and various related topics:
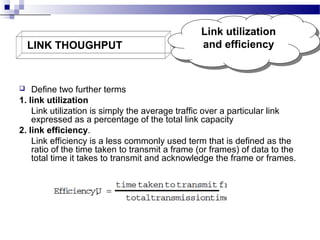
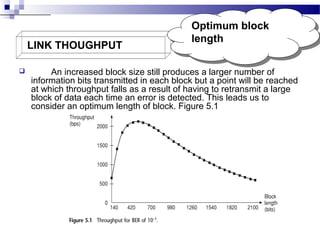
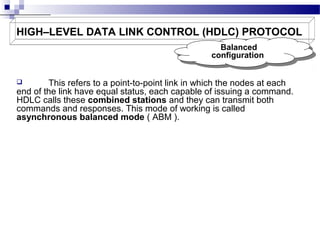
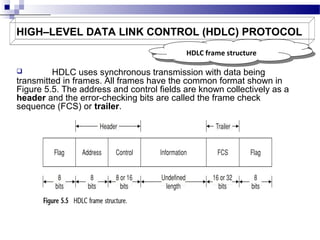
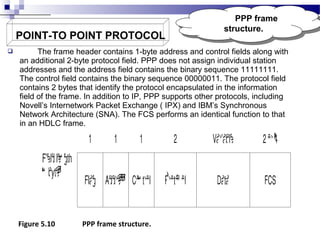
1. Link throughput is reduced by factors like frame overheads, propagation delay, acknowledgements, and retransmissions. HDLC and PPP are protocols that use frames for data transmission.
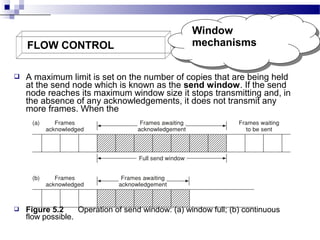
2. Flow control uses window mechanisms to regulate the maximum number of unacknowledged frames sent to prevent overflow. This affects throughput.
3. Link management procedures are needed to handle link and node failures and ensure frames are delivered properly.