This document provides an overview of communication methods and collaboration tools. It discusses objectives such as identifying appropriate uses of communication methods and advantages/disadvantages of electronic communications. Specific communication methods covered include email, instant messaging, teleconferencing, blogs/RSS. The document also addresses solving common electronic communication problems through tools like network diagnostics and help/support.






![Mod3-52 MODULE 3 Living Online
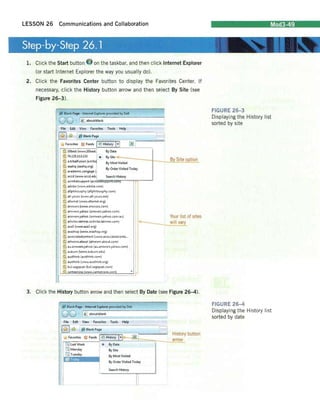
3. Click View network status and tasks to display the Network and Sharing Center window (see Figure 26-7).
FIGURE 26-7
Network and Sharing p i Center window
Ne~Nork and Sharing Center
.I~funmiJ?
USA·PC Chamberla in Intern et (This computer)
<~Chamberlain (Private nrtwork) Local and Intern et Conn ection lo.::al Area Connection
~ For sharing and discover; to wo rk pccp eriy, make S'.H e the £et:tings in your firewall program match the fcl10wing settings.
1.]. Sharing and Discovery Net'!o ri:: dIscovery Wo On Fife sharing a On
Public folder <;haring 0 Off Printer ~harin9 0 Off Pas~... ord protect ed sh aring C;; On
Media sharing " On
$hc .... n~ til the fl~-s.lnd fc!dm I1m ;,a,ing
Show me ,,!f d t ~h.)rtd n(tY;crk i Id... ,).'¢n Hti: ccmp-I,i1tt
4. In the Tasks column, click Diagnose and repair to run the Windows Network Diagnostics program. If there are no problems, then Windows will return a message similar to that in Figure 26-8. If there are problems, Windows will attempt to fix the problem or suggest other solutions.
FIGURE 26-8
Windows Network Diagnostics dialog box
~Windows Network Diagnostics ~ Windows did not find any pro blems with your Internet connection.
00 you want to report the problem to Microsoft? Additional details abo ut what went wrong
can help create a o;;olution. The report will be sent thE ned time you go online.
S~nd infonnatioo
Clo, e
5.
Click the Close button to close the dialog box.
6.
Use your word-processing program and write a summary of why you think the Diagnose and repair tool is important. Provide an example of when and how you would use this tool. Submit your assignment to your instructor.](https://image.slidesharecdn.com/lesson26-book-141013064711-conversion-gate01/85/Computer-Literacy-Lesson-26-8-320.jpg)
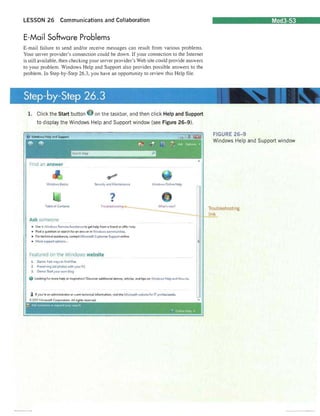


![ModJ-56 MODULE 3 Living Online
FIGURE 26-12 Troubleshooting attachment problems
Click to display a possible solution
1. In the Windows Help and Support window you opened in the last exercise, click I can't view or save an attached file (see Figure 26-12).
~ Show all
A
Troubleshoot problems with Windows Mall
If you erE: hal.·ing trouble configuring your e-mail accounts with Wlndcws Mail, you might (amider using Windows live Mail in~(!dd. All ycu need to do is enter your e-mail addr~!i and oI/indows trveMail will automatically enter the correct settings for e-mail !iervers u!;ed by many popular e-mail ser/ices, including tVindows: Live Hetmail, Yahoo!, AOL. and Gmail.
Windcw~ Live Mail includes the familiar features of Outlook E.xpreS:!i, the mail program included in Vfindows XP, and Vindow5 Mail, themail program induded in :;'ndov,,:s Vi~i!!. To download vVindows LiVE: Mail, go to the 'Vindows Live Mail .... ebsitt.
Here are solutions to some common iSSUE:s "'.lith VVindm',ls Mail.
• I don't know hO'1 to set up WindO"'iSi Mail fer m]' e-mail account.
~ I clS n t II:(;C;',I€ e-nlcil.
• i can receive. but not send, I!-mail messages.
... I can't vie'; or save "" attath~d file.
WindoYJ~ Mail blods acce5~ to certain type; of attachments that can potentially be harmful to your ccmputer. For
in~tructions on how to acces~ blocked files, see Why c~n't [ vie"AI itn attachment in '/indc';,'S fY1ail?
If you receive an att~chE:d file that is not blocked but will not open, you probably need to install a program capable of opening the file. Thi$ can occur if someone. sends you a file bye-mail. Ask thE: sender v/hat program opens the file and ho'.' you can install it. For more information, $-E:e File nllmes l;nd file: namE: 6til!'nsiom: frequently ad.:E:d qu~lons.
•
The links don't work In a mes:sdgif I received.
•
I don't understand the difference b€toM'n Wind ows f."lail, indows live Mail, and Outlook Express.
~ I have messages in m Outbox and I don't know how to send or de.ltte them.
• I can't check sp~Ulng in my messages.
•
When I d ic k an e-mail fink in my web brows E'r, it opens Inothfr e.-mail program instead of Viindows Mail.
2.
Read the information and then use your word-processing program to summarize what you learned. Close the Windows Help and Support window.
3.
Submit your word-processing document to your instructor.
Delivery Failure
E-mail delivery failure refers to a returned or "bounced" e-mail. This can happen for a number of reasons, including the following:
•
The e-mail address was mistyped.
•
The e-mail may have a virus or worm attached. The receiving program detects the problem and will not accept the message.](https://image.slidesharecdn.com/lesson26-book-141013064711-conversion-gate01/85/Computer-Literacy-Lesson-26-12-320.jpg)














![LESSON 26 Communications and Collaboration Mod3-71
FILL IN THE BLANK
Complete the following sentences by writing the correct word or words in the blanks provided.
I. Communications _ _ _ -----refers to good manners and proper beha'iors when communicating through electronic media.
2.
E-mail ________ allows you to define rules to manage incoming e-mail.
3.
________________ are one of the more popular formats used for fraudulent activities.
4.
A(n) ________ is an attempt to decei'e an audience into believing that something false is real.
5.
A(n) ________ is a program that has been Hillen. usua]lly by a hacker. to corrupt data on a computer.
PROJECTS
PROJ ECT 26-1
Access the eHow Web site at vww.ehow.coII//holl'_2003276_e-lI/ailhoaxes- scal1/s.hlll/l. This site contains an activity on HoII' 10 Learn Aboul rhe Lalesl E-mail Hoaxes (lnd Scml/s. Below the heading Instructions. there are tive steps. Read the instructions and follow the steps. Then use your word-processing program to describe how you answered each of the steps.
PROJ EeT 26-3
Using the Internet or other resources. see what you can tind about the history of instant messaging. Then answer the following questions:
1.
In what year did instant messaging become popular?
2.
What was ICQ as related to instant messaging')
3.
When did AOL adopt instant messaging')
II CRITICAL THINKING
PROJECT 26-2
Viruses have been around for quite a while. Use the Internet and other resources to research the history of early computer viruses, Prepare a report to share with your classmates on the types of viruses and the damage they caused. Also, include any information you might tind on the person who programmed the virus. if possible. Use a search engine and the keywords computer viruses or early COli/pliler vil'llses.
TEAMWORK PROJECT
Iindividuals who use e-mail for frequent communication are often annoyed by unwanted e-mail called spam. Spam is unsolicited e-mail messages that can be obnoxious, offensi'e, and a waste of your time. Some countries have laws against spam. Your Internet service provider may try to block spam before it reaches your mailbox. However. you may still be inconvenienced by junk e-mail.
Working with a partner. research spam to learn more about what it is used for. how marketers get addresses, how effective spam is, and ways you can stop spam. Then. you and your teammate should each select one of the two positions-pro spam, how effective it is and what it is meant to do: or against spam, if it is a nuisance or problem and how you can stop it before it reaches your e-mail inbox. Write a brief summary of your findings and compare them with your partner. Then. at the end of your report, answer the following questions together: Is spam ever useful0 Should there be laws to restrict sparn? Do you think you can block all spam from reaching your inbox?
If you do not have a personal e-mail address. how would you go about opening a free account for personal e-mail'? There are a number of Web sites that provide free access to e-mail, and e'en if you do not have a computer. public libraries. schools. and even some "Internet cafes" offer free or inexpensive computer access to the World Wide Web that you can use to check incoming messages and send your 0'11 e-mail. If you wanted to set up a personal e-mail account, what kind of features would you like to have for your account" You might want to investigate some Web sites. such as W'W.h(}flll([il.cOIll, IVIVW.IISa.ller. or www.yahoo.com. to tind out abollt the options available and then list the ones you think are most important. Why do you believe you would need these features for your e-mail accoun!')](https://image.slidesharecdn.com/lesson26-book-141013064711-conversion-gate01/85/Computer-Literacy-Lesson-26-27-320.jpg)
