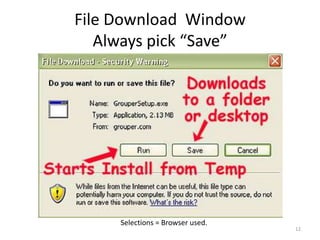
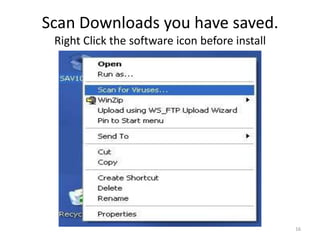
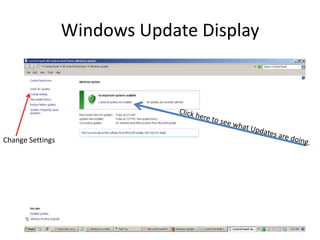
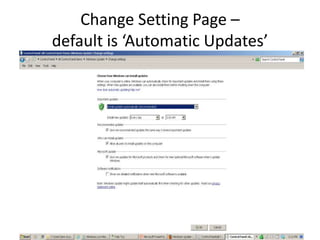
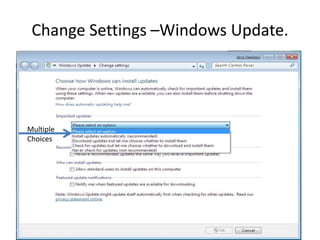
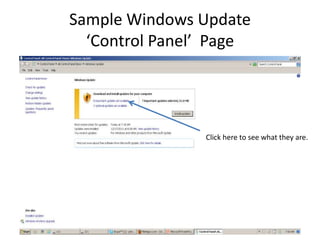
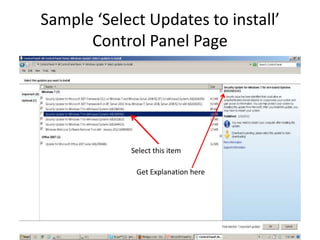
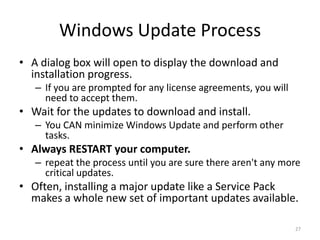
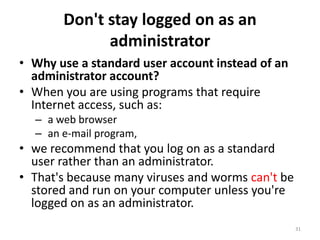
This document provides an overview of common computer tasks, including adding hardware, downloading and installing software, managing Windows updates, defining and managing firewalls, and creating and changing user accounts. It describes how to add new USB devices or other hardware, what to do if the computer doesn't recognize a new device, and why device drivers are needed. It also explains how to safely download and install software from the internet, remove unwanted programs, and change settings for Windows updates and the Windows firewall. Finally, it discusses creating separate user accounts for each person using the computer.