Cloude computing notes for Rgpv 7th sem student
- 1. Govindyadav
- 2. Govindyadav
- 3. Govindyadav
- 4. Govindyadav Que-Characteristics of Cloud Computing as per NIST National Institute of Standards and Technology (NIST) is an agency under the scope of US Department of Commerce. NIST is responsible for defining standards in Science and Technology. The Computer Security Division of NIST has provided a formal Definition and Characteristics of Cloud computing. NIST five essential characteristics of Cloud Computing 1. On demand self-service 2. Broad network access 3. Resource pooling 4. Rapid Elasticity 5. Measured service 1. On Demand Self service Computer services such as Email, Application Network, or Server service can be provided without requiring interaction with each service provider. Self-service means that the consumer performs all the actions needed to acquire the service himself, instead of going through an IT department. For example – The consumer’s request is then automatically processed by the cloud infrastructure, without human intervention on the provider’s side.
- 5. Govindyadav 2. Broad NetworkAccess Cloud capabilities are available over the network and accessed through standard mechanism that promote use by heterogeneous client such as mobile phone, laptop 3. Resourcepooling – The providers computing resources are pooled together to serve multiple customers, with different physical and virtual resources dynamically assigned and reassigned according to the customers demand. – There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify lication at a higher level of abstraction (e.g. contry, state, or datacenter). – Example of resources include storage, processing, memory, and network bandwidth. 4. Rapidelasticity – Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. – To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time. 5. Measuredservice – Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g. storage, processing, bandwidth, and active use account). – Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
- 6. Govindyadav 6. Multi-tenancy In a private cloud, the customers are also called tenants, can have different business divisions inside the same company. In a public cloud, the customers are often entirely different organizations. Most public cloud providers use the multi-tenancy model. Multi- tenancy allows customers to run one server instance, which is less expensive and makes it easier to deploy updates to a large number of customers. Que- Cloud computing reference model------- Service Models The resource stack provided as part of the cloud solution and the responsibilities which fall between the agency and the cloud provider define service models. NIST SP 800-145 outlines the possible service models that may be employed during a cloud implementation. Software as a Service (SaaS). Thecapability gives the customer use of the provider’s applications running on the provider’s cloud infrastructure. The applications are accessible from various client devices through a thin client interface such as a web browser (e.g., web-based email). The customer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user-specific application configuration settings. The SaaS model provides the highest level of abstraction in which the provider is managing the facilities, the interaction between software and hardware and the software itself. The provider is responsible for the highest amount of security and data protection under this model, and the customerwill negotiate into the service contractwith the provider. Platform as a Service (PaaS). Thecapability provides the customer the ability to deploy onto the cloud infrastructure customer-created or acquired applications created using programming languages and tools supported by the provider. PaaS adds a layer of integration with application development frameworks, middleware capabilities that allow developers to build applications on the platform with programming languages and tools
- 7. Govindyadav supported by the stack. The customer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly application hosting environment configurations. Security is a shared responsibility with the provider responsible for the underlying platform infrastructure, and the customeris responsible for securing the applications developedon the platform. Infrastructure as a Service (IaaS). The capability provides the customer provision processing, storage, networks, and other fundamental computing resources where the customer is able to deploy and run arbitrary software, which can include operating systems and applications. The computing infrastructure is typically deployed as a virtual environment. The customer does not manage or control the underlying cloud infrastructure but has control over operating systems; storage, deployed applications, and possibly limited controlof select networking components (e.g., host firewalls). The customeris responsible for the highest amount of security and data protection under this model. Deployment Models- ----Types of Clouds:-There are four different cloud models that you can subscribe according to business needs: 1. Private Cloud: Here, computing resources are deployed for one particular organization. This method is more used for intra-business interactions. Where the computing resources can be governed, owned and operated by the same organization. 2. Community Cloud: Here, computing resources are provided for a community and organizations. 3. Public Cloud: This type of cloud is used usually for B2C (Business to Consumer) type interactions. Here the computing resource is owned, governed and operated by government, an academic or business organization. 4. Hybrid Cloud: This type of cloud can be used for both type of interactions - B2B (Business to Business) or B2C ( Business to Consumer). This deployment method is called hybrid cloud as the computing resources are bound together by different clouds.
- 8. Govindyadav Que:-Overview of cloud applications: ECG Analysis in the cloud-- Example of health monitoring system is ECG machine which is used to measure the Heart-Beat of Human body and the output is get printed on the graph paper. The analysis of the shape is used to identify arrhythmias, and it is the most common way of detecting the heart diseases. Here the meaning of arrhythmias means “not having a steady rhythm”, “an arrhythmic heartbeat” means a heart beat which is not in it’s rhythm. Now we will let this concept enter into the cloud computing. Cloud computing technologies allows the remote monitoring of a patient’s heart beat data. Through this way the patient at risk can be constantly monitored without going to the hospital for ECG analysis. At the same time the Doctor’s can instantly be notified with cases that need’s their attention.
- 9. Govindyadav Here in this fig there are different types of computing devices equipped with ECG sensors to constantly monitor the patient’s heart beat. The respective information is transmitted to the patient’s mobile device that will immediately forwarded to the cloud- hosted web services for analysis. The entire web services from the front end of a platform that is completely hosted in the cloud that consist of three layers:Saas,Paas,Iaas. Protein structure prediction A protein is composed of long chains of amino acids joined together by peptide bonds. The various structures of protein help in the designing of new drugs and the various sequences of proteins from its three-dimensional structure in predictive form is known as a Protein structure prediction.
- 10. Govindyadav Gene: A gene is the basic physical and functional unit of heredity. Genes, which are made up of DNA, act as instructions to make molecules, such as proteins. In humans, genes vary in size from a few hundred DNA bases to more than 2 million bases. Gene expression: Gene expression is the process by which information from a gene is used in the synthesis of a functional gene product, such as proteins. Some of the tools for gene expression analysis are- AltAnalyze Dchip geWorkbench 2.5.1 from NCI. Babelomics suit Myrna Cloud-CoXCS, is a machine learning classification system for gene expression datasets on the Cloud infrastructure. It is composed of three components:CoXCS, Aneka, and Cloud computing infrastructure.
- 11. Govindyadav Gene expression technology, allows for the monitoring of the expression levels of thousands of genes at once. As a direct result of recent advances technology, it is now feasible to obtain gene expression profiles of tissue samples at relatively low costs. The gene expression software’s, such as as Myrna, uses cloud computing, an Internet-based method of sharing computer resources. Cloud computing bundles together the processing power of the individual computers using the Internet. A number of firms with large computing centers like Amazon, Microsoft etc, rent unused computers over the Internet for a fee. Cloud computing makes economic sense because cloud vendors are very efficient at running and maintaining huge collections of computers. Researchers struggling to keep pace with their sequencing instruments can use the cloud to scale up their analyses while avoiding the headaches associated with building and running their own computer center. Satellite Image Processing
- 12. Govindyadav Satellite Image Processing is an important field in research and development and consists of the images of earth and satellites taken by the means of artificial satellites. Firstly, the photographs are taken in digital form and later are processed by the computers to extract the information. Statistical methods are applied to the digital images and after processing the various discrete surfaces are identified by analyzing the pixel values. The satellite imagery is widely used to plan the infrastructures or to monitor the environmental conditions or to detect the responses of upcoming disasters. In broader terms we can say that the Satellite Image Processing is a kind of remote sensing which works on pixel resolutions to collect coherent information about the earth surface. Majorly there are four kinds of resolutions associated with satellite imagery. These are: Spatial resolution– It is determined by the sensors Instantaneous Field of View(IFoV) and is defined as the pixel size of an image that is visible to the human eye being measured on the ground. Since it has high resolving power or the ability to separate and hence is termed as Spatial Resolution. Spectralresolution – This resolution measures the wavelength internal size and determines the number of wavelength intervals that the sensormeasures. Temporal resolution– The word temporal is associated with time or days and is defined as the time that passes between various imagery cloud periods. Radiometric resolution – This resolution provides the actual characteristics of the image and is generally expressed in bits size. It gives the effective bit depth and records the various levels of brightness of imaging system. CRM and ERP in Cloud Computing –
- 13. Govindyadav What is CRM? CRM stands for Customer Relationship Management and is a software that is hosted in cloud so that the users can access the information using internet. CRM software provides high level of security and scalability to its users and can be easily used on mobile phones to access the data. Now a days, many business vendors and service providers are using these CRM software to manage the resources so that the user can access them via internet. Moving the business computation from desktop to the cloud is proving a beneficial step in both the IT and Non-IT fields. Some of the major CRM vendors include Oracle Siebel, Mothernode CRM, Microsoft Dynamics CRM, Infor CRM, SAGE CRM, NetSuite CRM. Advantages: Few advantages of using CRM are as follows: High reliability and scalability Easy to use Highly secured Provides flexibility to users and service providers Easily accessable What is ERP? ERP is an abbreviation for Entity ResourcePlanning and is a software similar to CRM that is hosted on cloud servers which helps the enterprises to manage and manipulate their business data as per their needs and user requirements. ERP software follows pay per use methodologies of payment, that is at the end of the month, the enterprise pay the amount as per the cloud resources utilized by them. There are various ERP vendors available like Oracle, SAP, Epicor, SAGE, Microsoft Dynamics, Lawson Softwares and many more. Advantages: Few advantages of using ERP softwares are: Costeffective High mobility Increase in productivity No security issues Scalable and efficient
- 14. Govindyadav Unit-2 Cloud Computing Architecture The broad divisions of cloud architecture are: Front-end Back-end It is the responsibilityof the back-end to provide the security of data for cloud users along with the traffic control mechanism.The server also provides the middleware which helps to connectdevices & communicate with each other. Figure - Cloud Computing Architecture:
- 15. Govindyadav Front End Front-end is the side that is visible to the client, customer, or user. Front- end pieces include the user interface and the client’s computersystem or network that is used for accessing the cloud system. You have probably noticed that differentcloud computing systems use differentuser interfaces—forexample, not only can you choose from a variety of web browsers (including Chrome, Safari, Firefox,etc.), but the Google Docs user interface is differentthan that of Salesforce.
- 16. Govindyadav Back End--- On the other hand, the back-end pieces are on the side used by the service provider. These include various servers, computers, data storage systems, virtual machines, and programs that together constitute the cloud of computing services. The back-end side also is responsible for providing security mechanisms, traffic control, and protocols that connect networked computers for communication. Que:---Types of Cloud Cloud computing is an Internet-based computing in which shared the pool of resources are available over a broad network access,these resources can e provisioned or released with minimum management efforts and service provider interaction. There are four types of cloud: 1. Public cloud 2. Private cloud 3. Hybrid cloud 4. Community cloud Public cloud: Public cloud are managed by third parties which provide cloud services over the internet to public, these services are available as pay-as-you-go billing mode. They offersolutions for minimizing IT infrastructure costs and act as a good option for handling peak loads on the local infrastructure. They are a goto option for small enterprises,which are able to start their businesses without large upfront investments by completelyrelying on public infrastructure for their IT needs. A fundamental characteristic of public clouds is multitenancy.A public cloud is meant to serve multiple users, not a single customer.A user requires a virtual computing environment that is separated,and most likely isolated, from other users.
- 17. Govindyadav Private cloud : Private clouds are distributed systems that work on a private infrastructure and providing the users with dynamic provisioning of computing resources. Instead of a pay-as-you-go modelas in public clouds,there could be other schemes in that take into account the usage of the cloud and proportionally billing the differentdepartments or sections of an enterprise. Hybrid cloud: Hybrid cloud is a heterogeneous distributed system resulted by combining facilities of public cloud and private cloud. For this reason they are also called. Community cloud: A community cloud in computing is a collaborative effortin which infrastructure is shared between several organizations from a specificcommunity with common concerns,whether managed internally or by a third-party and hosted internally or externally.
- 18. Govindyadav The cloud computing portability and interoperability categories to consider are thus: Data Portability Application Portability Platform Portability Application Interoperability Platform Interoperability Management Interoperability Publication and AcquisitionInteroperability .Cloud computing business process management: is the use of (BPM) tools that are delivered as software services (SaaS) over a network. Cloud BPM business logicis deployed on an application server and the businessdata resides in cloud storage.
- 19. Govindyadav .Cloud service management and operations referto all the activities that an organization does to plan, design,deliver, operate, and control the IT and cloud services that it offers to customers. Service management includes the operational aspects of your applications and services.
- 20. Govindyadav
- 21. Govindyadav Virtualization Virtualization changes the hardware-software relations and is one of the foundational elements of cloud computing technology that helps utilize cloud computing capabilities to the full. Storage Virtualizing Using this technique gives the user an ability to pool the hardwarestoragespace fromseveralinterconnected storagedevices into a simulated single storage device that is managed fromone single command console. This storagetechnique is often used in storagearea networks. Storagemanipulation in the cloud is mostly used for backup, archiving, and recovering of data by hiding the real and physicalcomplex storage architecture. Administrators can implement it with softwareapplications or by employing hardwareand softwarehybrid appliances. Server Virtualization This technique is the masking of server resources. Itsimulates physicalservers by changing their identity, numbers, processorsand operating systems. This spares the user fromcontinuously managing complex server resources. Italso makes a lot of resources available for sharing and utilizing, while maintaining the capacity to expand them when needed. Data Virtualization This kind of cloud computing virtualization technique is abstracting the technical details usually used in data management, such as location, performanceor format, in favor of broader access and more resiliency that are directly related to business needs. Desktop Virtualizing As compared to other types of virtualization in cloud computing, this model enables you to emulate a workstation load, rather than a server. This allows the user to access the desktop remotely. Since the workstation is essentially running in a data center server, access to it can be both more secureand portable.
- 22. Govindyadav Application Virtualization Softwarevirtualization in cloud computing abstracts the application layer, separating it fromthe operating system. This way the application can run in an encapsulated formwithout being dependant upon the operating system underneath. In addition to providing a level of isolation, an application created for one OS can run on a completely different operating system. .Virtualization benefits Protectionfrom System Failures. Technologyis always at the risk of crashing down at the wrong time. ... Hassle-free Transferof Data. You can easily transfer data from a physical storage to a virtual server, and vice versa. ... Firewall and Security. ... SmootherIT Operations. ... Cost-Effective Strategy. Virtual Local Area Network (VLAN):- A virtual local area network (VLAN) is a logical group of workstations, servers and network devices that appear to be on the same LAN despite their geographicaldistribution. A VLAN allows a network of computers and users to communicate in a simulated environment as if they exist in a single LAN and are sharing a single broadcastand multicast domain. VLANs are implemented to achieve scalability, security and ease of network management and can quickly adapt to changes in network requirements and relocation of workstations and server nodes. Higher-end switches allow the functionality and implementation of VLANs. The purpose of implementing a VLAN is to improve the performance of a network or apply appropriate security features. The key benefits of implementing VLANs include: Allowing network administrators to apply additional security to network communication
- 23. Govindyadav Making expansion and relocation of a network or a network device easier Providing flexibility because administrators are able to configure in a centralized environment while the devices might be located in differentgeographicallocations Decreasing the latency and traffic load on the network and the network devices,offering increased performance VLANs also have some disadvantages and limitations as listed below: High risk of virus issues because one infected system may spread a virus through the whole logical network Equipmentlimitations in very large networks because additional routers might be needed to control the workload More effective at controlling latency than a WAN, but less efficient than a LAN Virtual SAN (VSAN) is radically simple,hyper-converged storage for virtualized environments. Hyper-converged Infrastructure (HCI) leverages the hypervisor to deliver compute,networking and shared storage from a single x86 platform. In addition to being incredibly simple to deployand provision, Virtual SAN allows you to scale storage and compute resources, eliminating costly forklift upgrades. Every VSAN cluster can scale out one node at a time or scale up by adding capacity to existing hosts, and achieve over 8 PB of raw storage capacity. simplicity, agility, manageability and cost savings
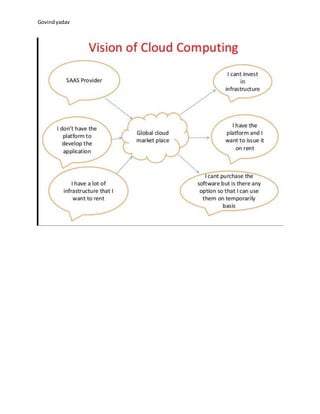
- 24. Govindyadav UNIT-5 MARKET BASED MANAGEMENT OF CLOUD The Real Potential of cloud computing resides is the fact that it actually facilitates the establishment of a market for trading IT utilities. Market oriented cloud computing (MOCC):- Market oriented cloud computing is the presence of a virtual market place where IT Service are trader and dynamically. Reference model of market oriented cloud computing (MOCC):- MOCC originated from the coordination of several components service consumers, service providers, and other entities that make trading between these two groups possible. There are three major components of cloud exchange are:- • Directory:-the market directory contains a listing of all the published services that are available in the cloud marketplace. • Auctioneer:-the auctioneer is in charge of keeping track of the running auctions in the market place and of verifying that the auctions for services are properly conducted and that malicious market players are prevented from performing illegal activities.
- 25. Govindyadav Bank:-the bank is the component that takes care of the financial aspectof all the operations happening in the virtual market place. Marketoriented architecture for datacenters:- The major components of architecture are:- • Brokers:-they submit their service requests from anywhere in the world to the cloud. • SLA resource allocator:-it is a kind of interface between users and cloud service provider which enable the SLA oriented resource management. • Service requestexaminer and admission control:-it interprets the submitted request for QoS requirement before determining whether to accept or reject the request. Based on the resource availability in the loud and other parameter decide. • Pricing:-it is in charge of billing based on the resourceutilization and some factors. Some factor are request time, type etc. • Accounting:-maintains the actual storage usage of resources by request so that the final coat can be charged to the users. • VM monitor:-keeps the track on the availability of VMs and their resources.
- 26. Govindyadav • Dispatcher:-the dispatcher mechanism starts the execution of admitted requests on allocated VMs. • Cloud request monitor:-it keeps the track on execution of request in order to be in tune with SLA. WHY CLOUD FEDERATION? CLOUD FEDERATION STACK Creating a cloud federation involves research and development at different levels: conceptual, logical and operational, and infrastructural. Third Party Cloud Services : A cloud service provider is a third-partycompanyofferinga cloud-based platform, infrastructure, application or storage services. Much like a homeowner wouldpay for a utility such as electricityor gas, companies typicallyhave to only pay for the amount of cloud services they use, as business demands require. Apart from the pay-per-use model, cloud service providers also give companies a wide range of benefits. Businesses can take advantage of scalabilityandflexibilityby not being limitedto physical constraints of on-
- 27. Govindyadav premises servers, the reliabilityof multiple data centres with multiple redundancies, customisation by configuringservers to your preferences and responsive load balancingthat can easilyrespond to changingdemands. However, businesses shouldalso evaluate the security considerations of storing information in the cloud to ensure that industry-recommended access and compliance managementconfigurations andpractices are enacted and met.
- 28. Govindyadav