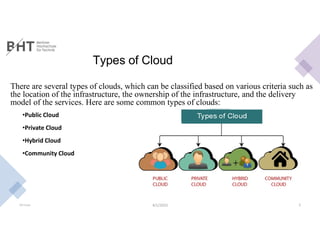
The document discusses cloud computing, including its definition, history, benefits, types of clouds, service models, security considerations, popular providers, and conclusions. Specifically, it defines cloud computing as the delivery of computing services over the internet, notes that the concept began taking shape in the late 1990s and early 2000s with companies like Salesforce and Amazon introducing early cloud offerings, and outlines key benefits as cost savings, scalability, flexibility, reliability, and security. It also describes common cloud types, service models of infrastructure as a service, platform as a service, and software as a service, and reviews security measures and popular providers like Amazon Web Services, Microsoft Azure, and Google Cloud Platform.