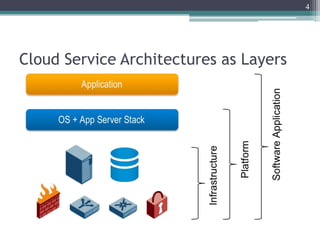
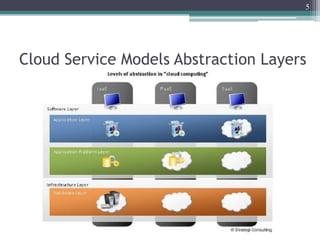
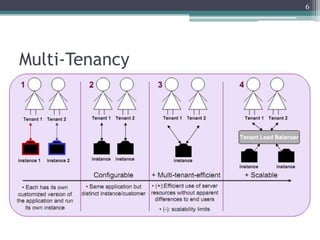
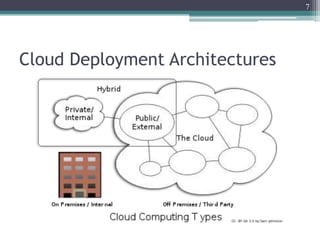
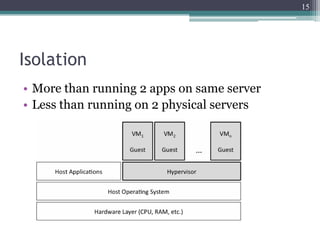
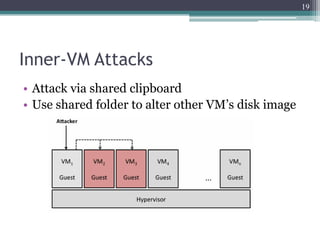
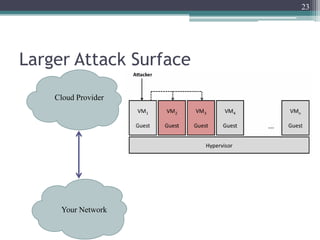
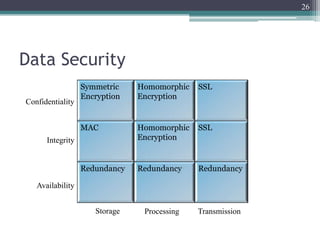
The document discusses security issues related to cloud computing including traditional problems like data loss and downtime as well as new issues introduced by cloud architectures like lack of a security perimeter, increased attack surface from virtualization, and challenges around data confidentiality, integrity and availability when data is stored, processed and transmitted remotely in the cloud. Virtualization introduces additional security risks around hypervisor vulnerabilities, VM isolation, and state restoration that could allow compromised VMs to persist.