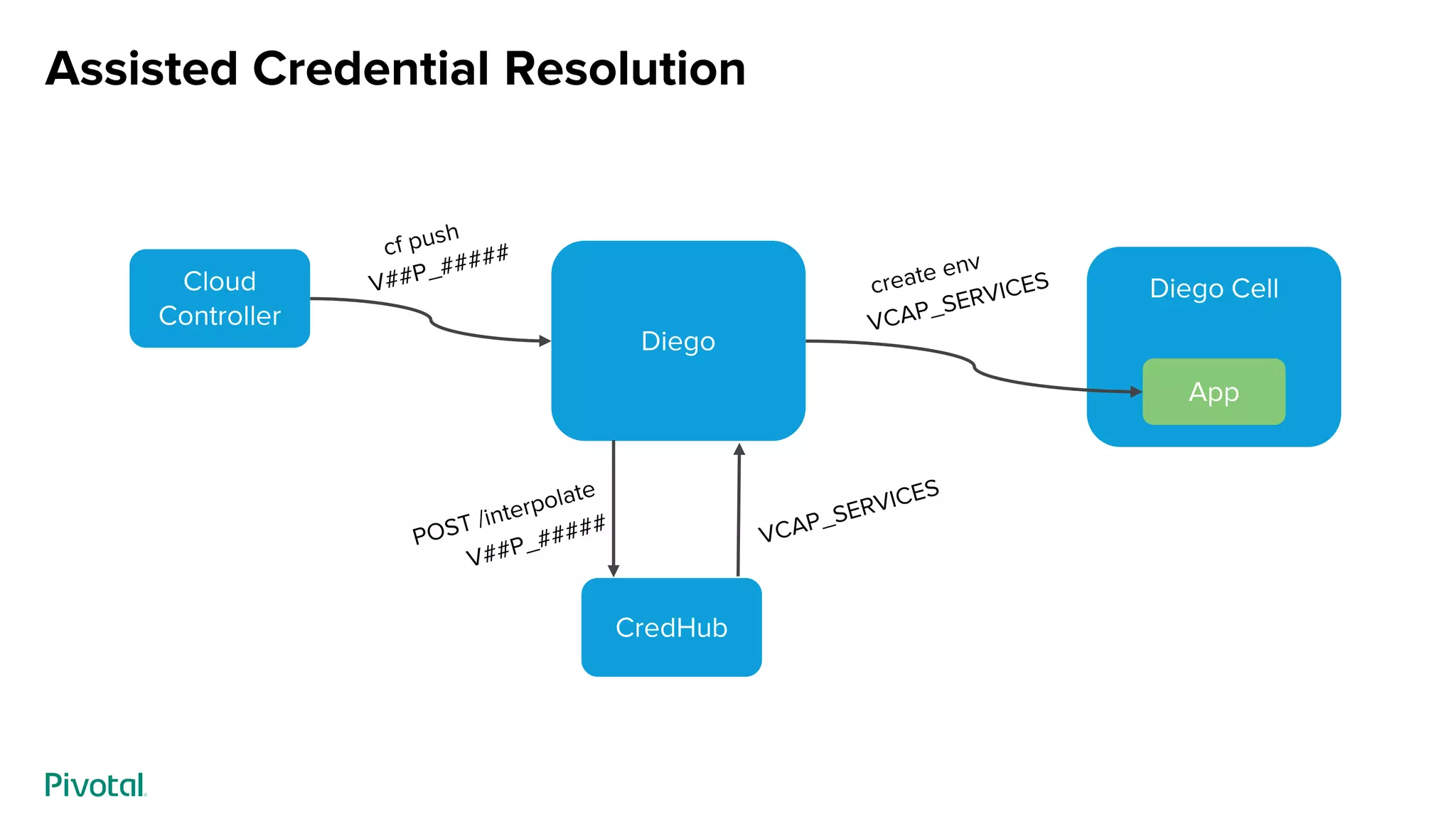
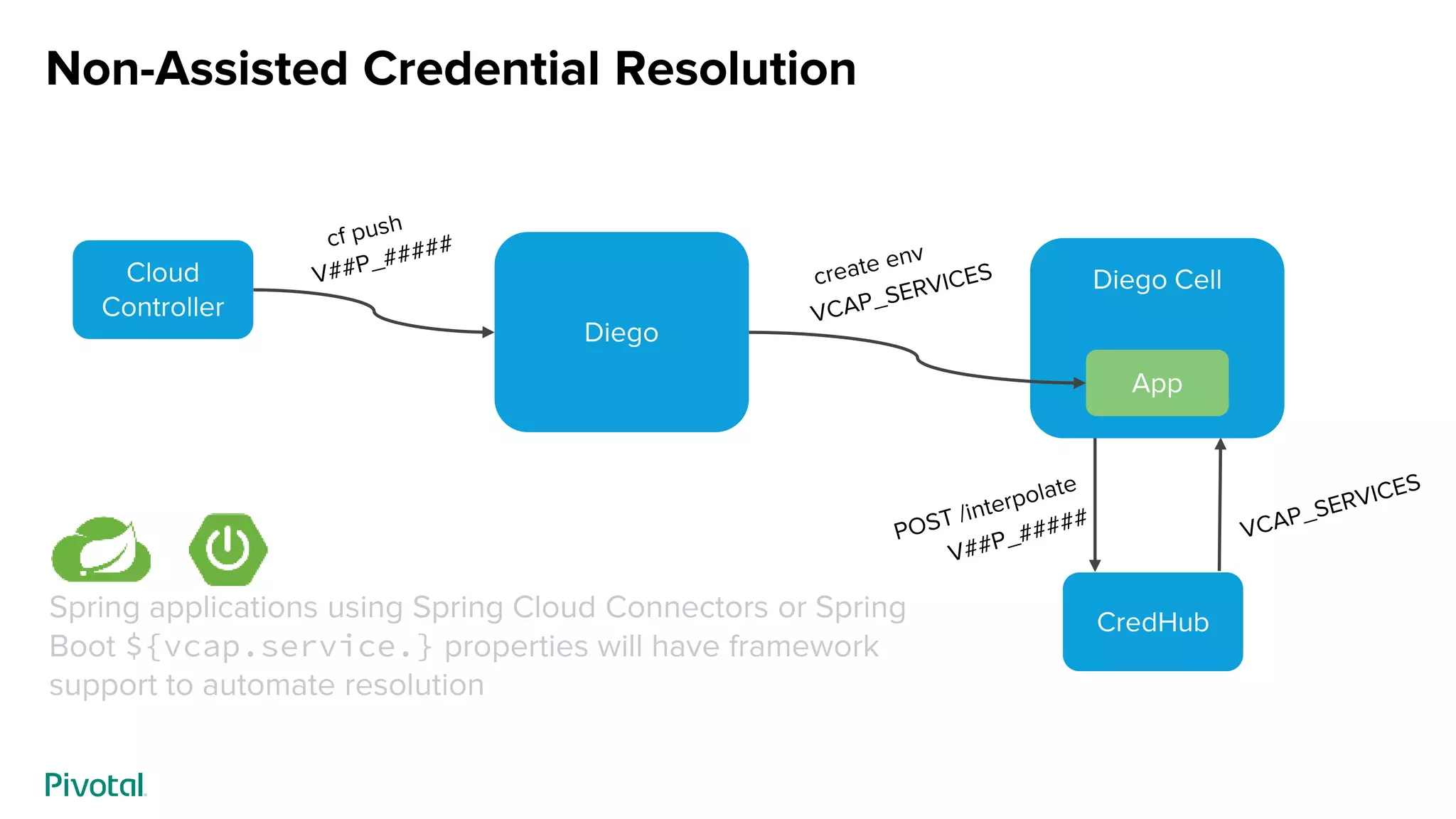
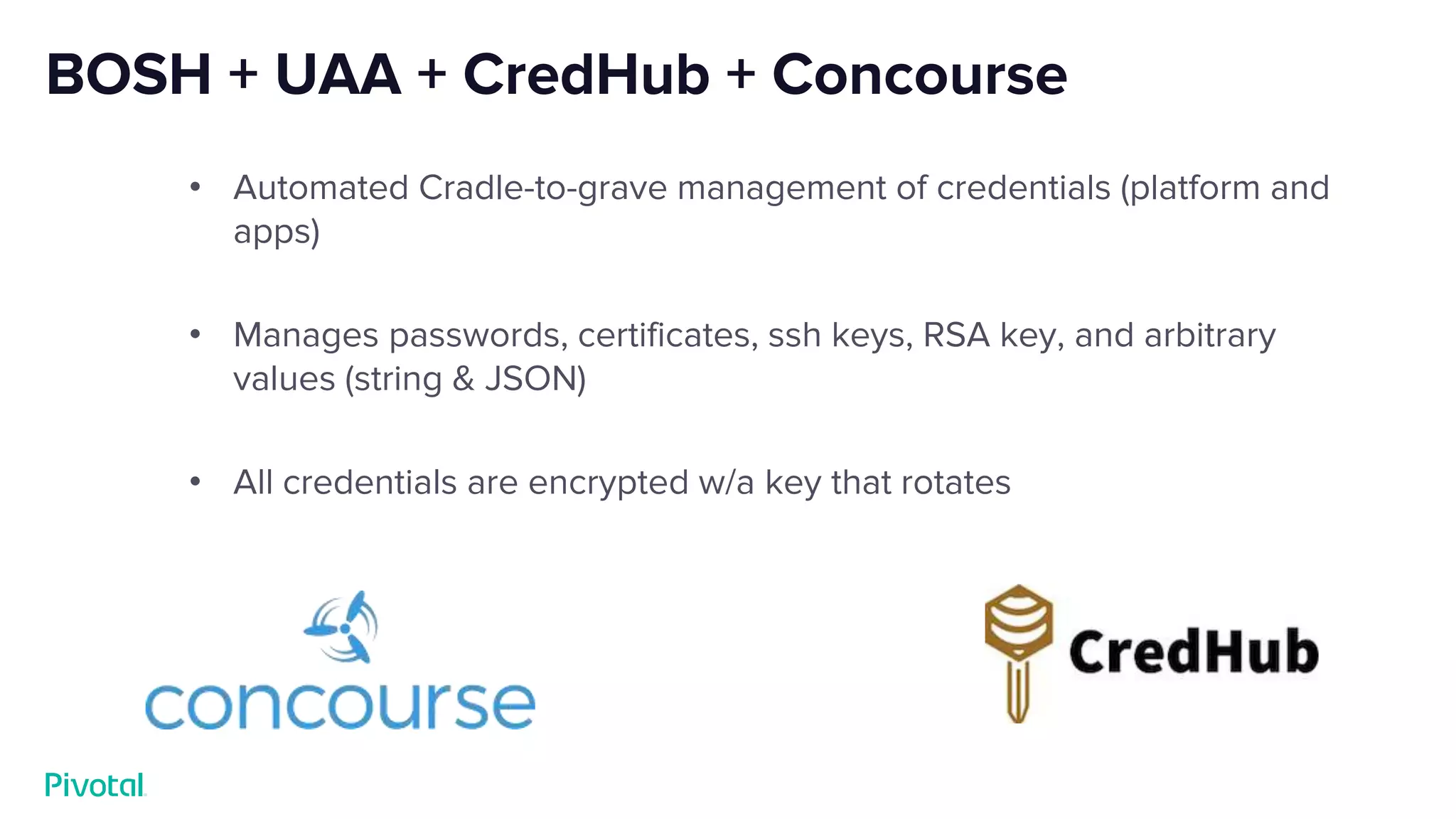
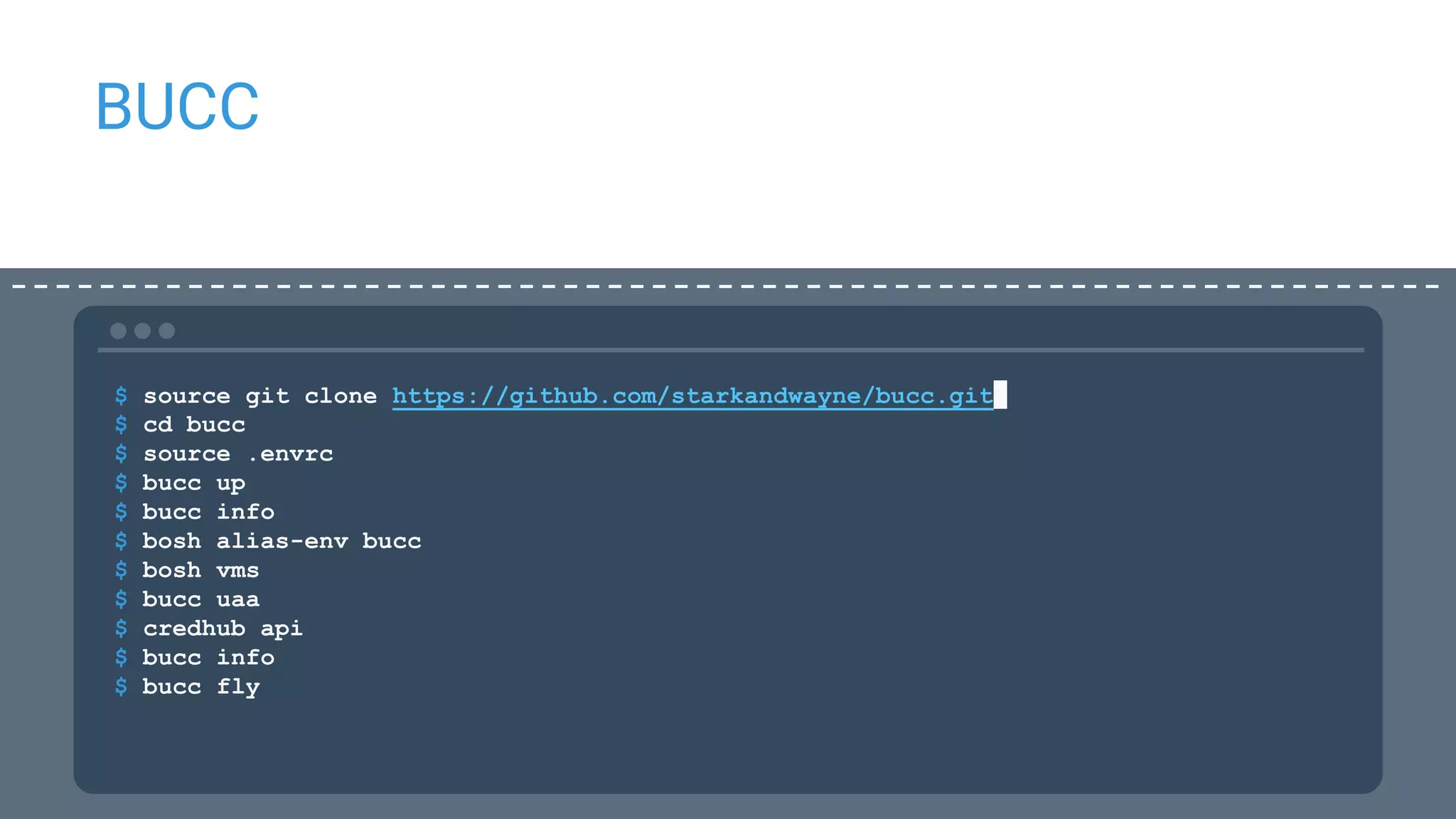
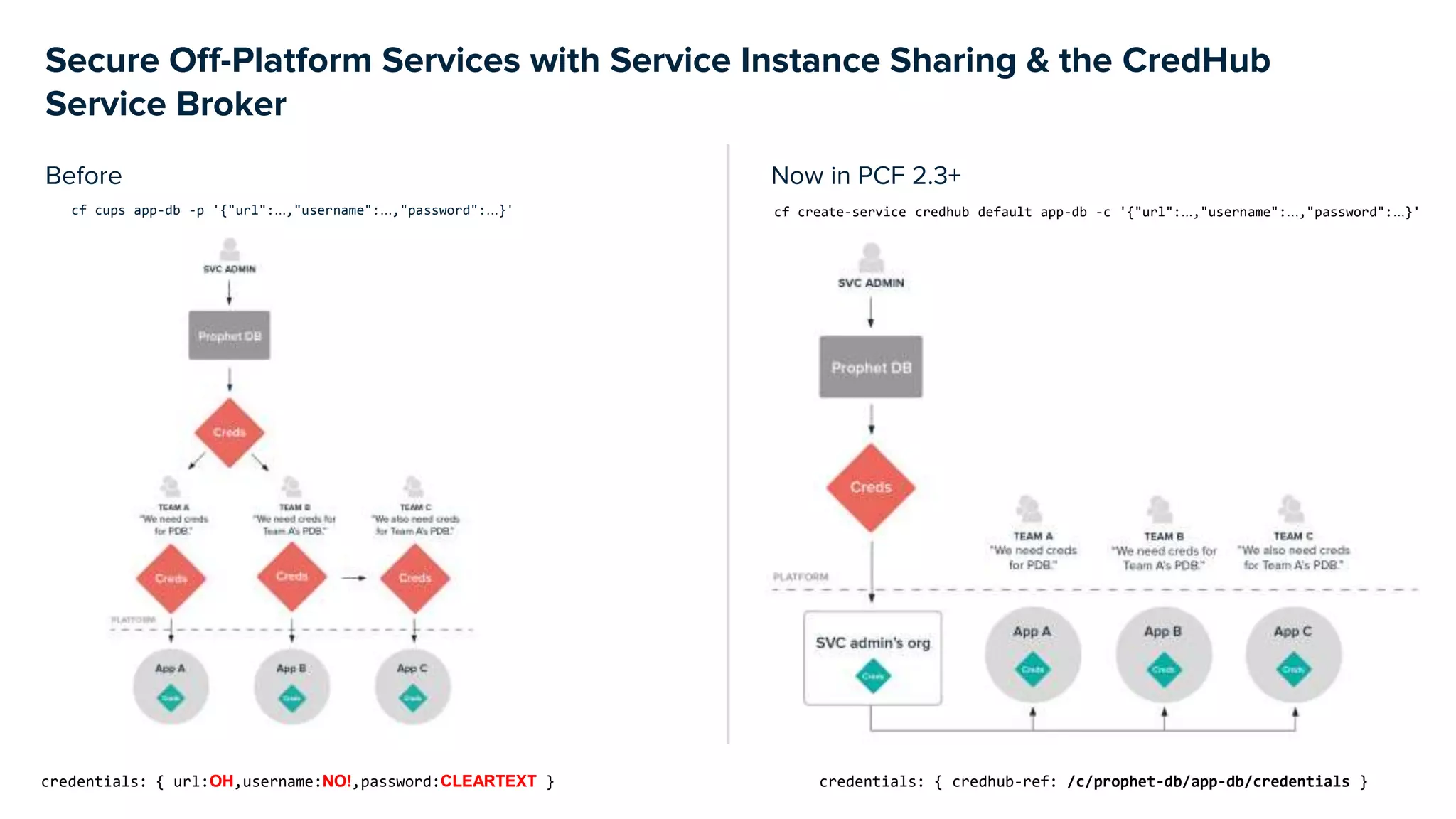
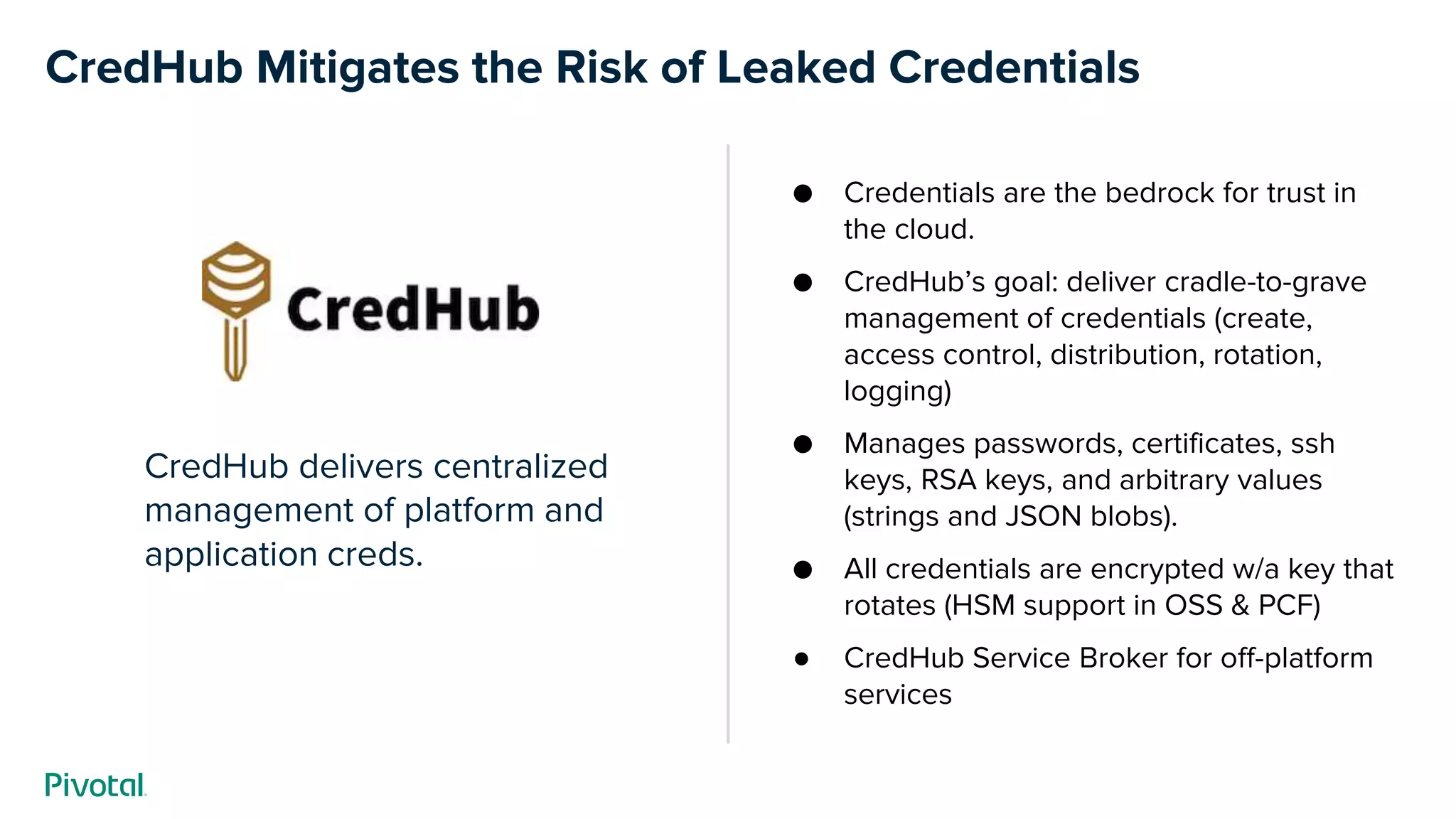
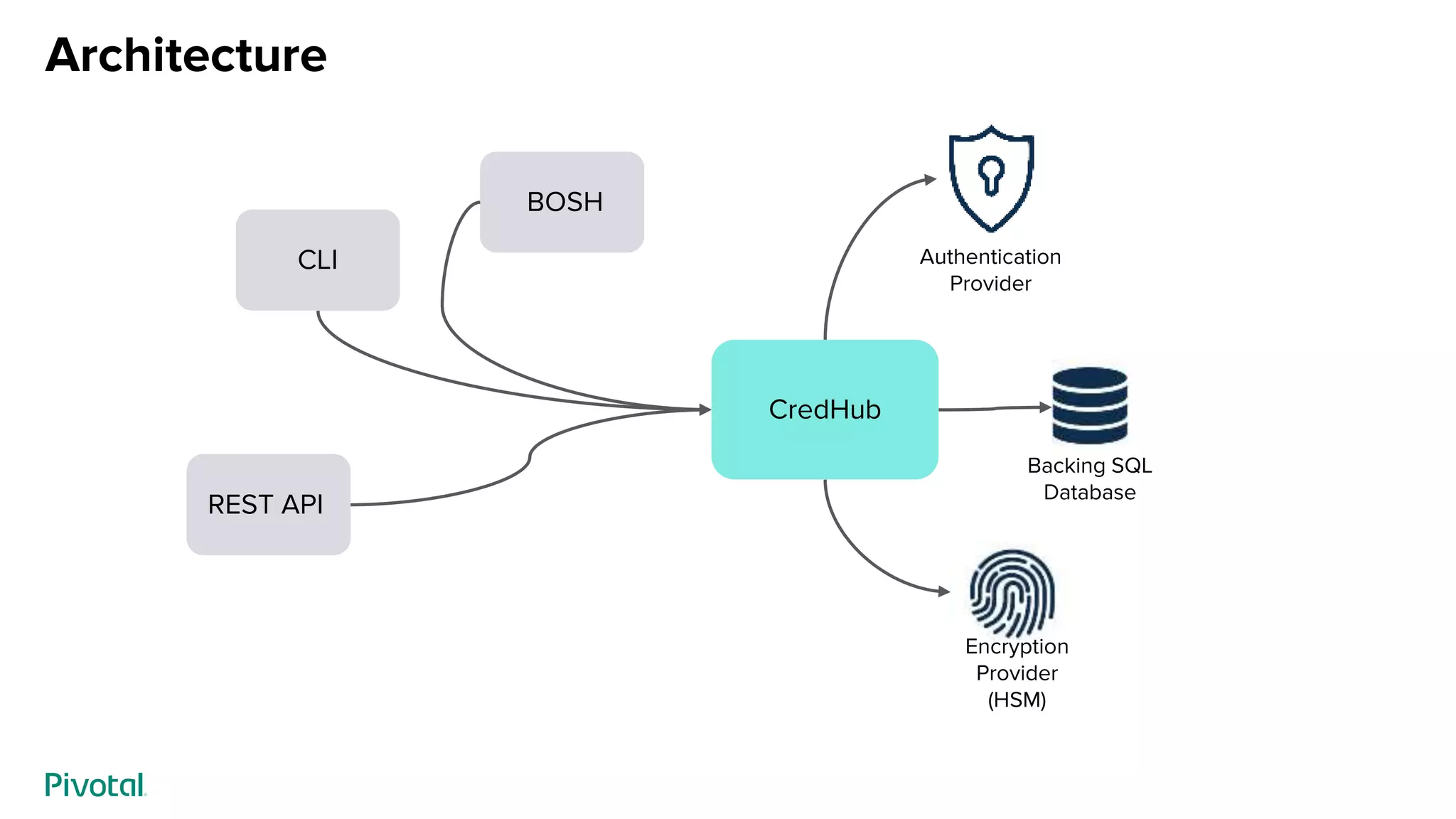
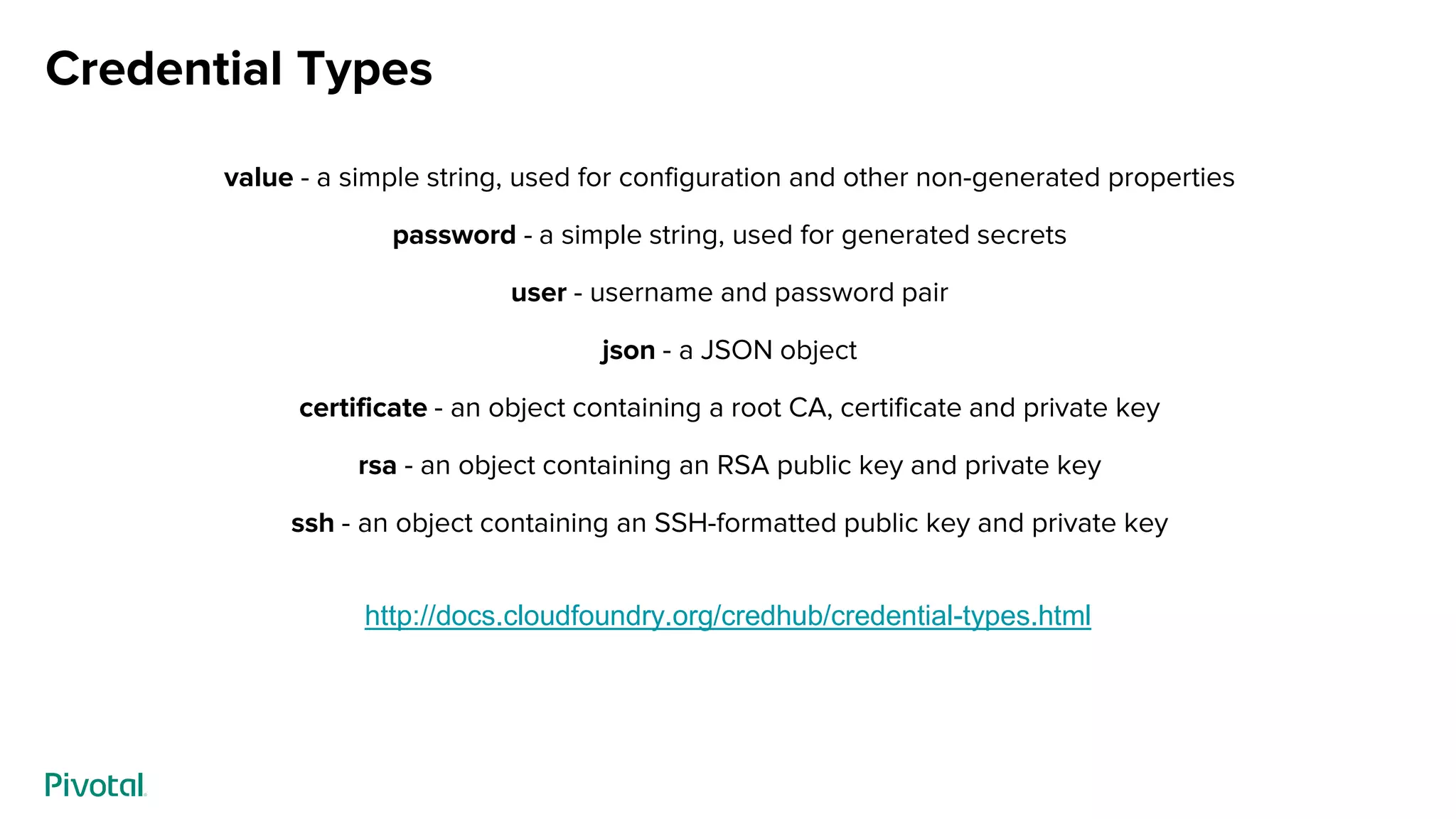
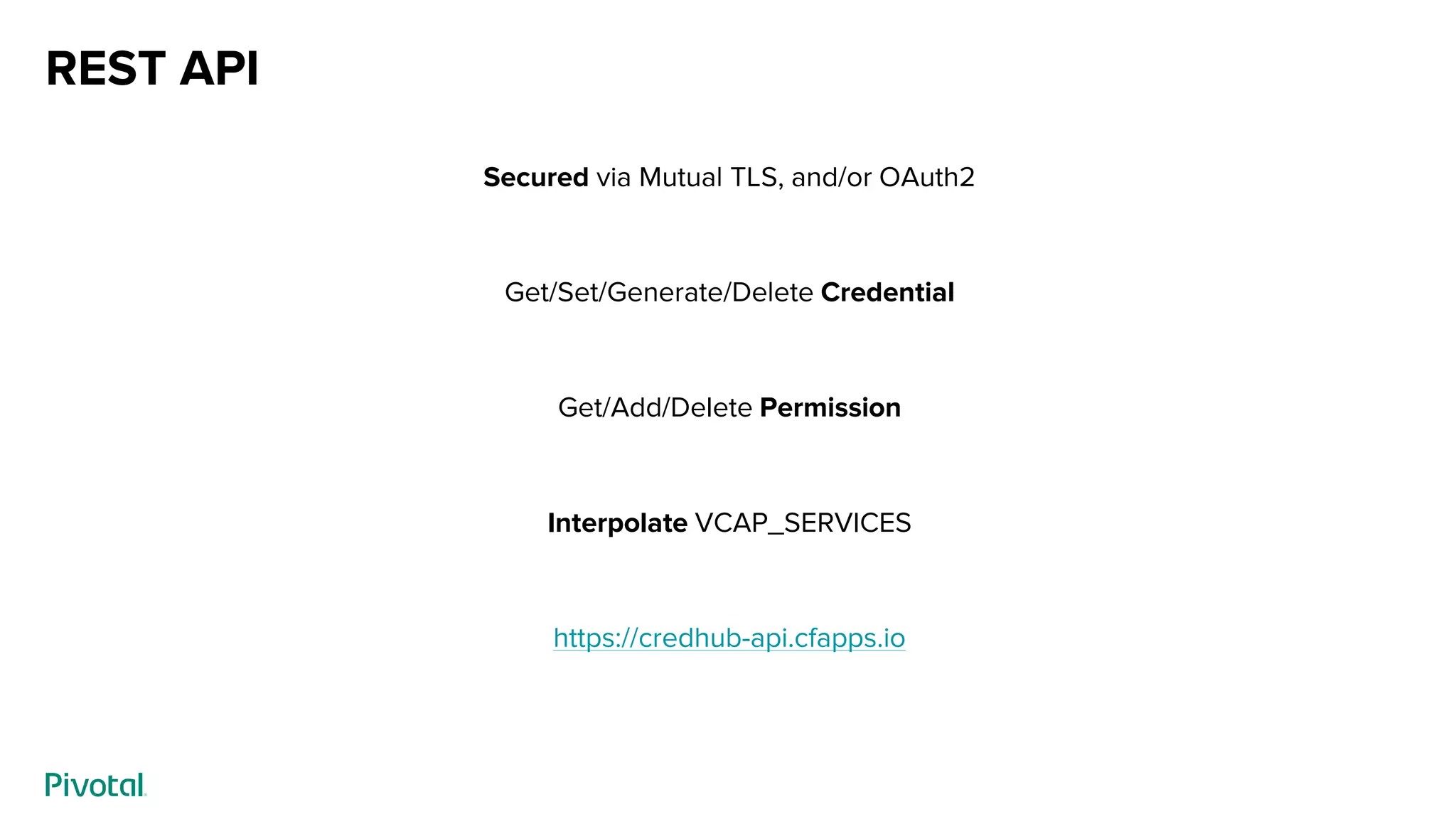
This document discusses CredHub, a tool for centralized credential management. It delivers cradle-to-grave management of credentials, including creation, access control, distribution, rotation, and logging. Credentials are encrypted at rest and include passwords, certificates, SSH keys, and arbitrary values. The document outlines CredHub's architecture, credential types, REST API, language bindings, service bindings workflow, and availability. It demonstrates how CredHub improves security when used with platforms and pipelines.

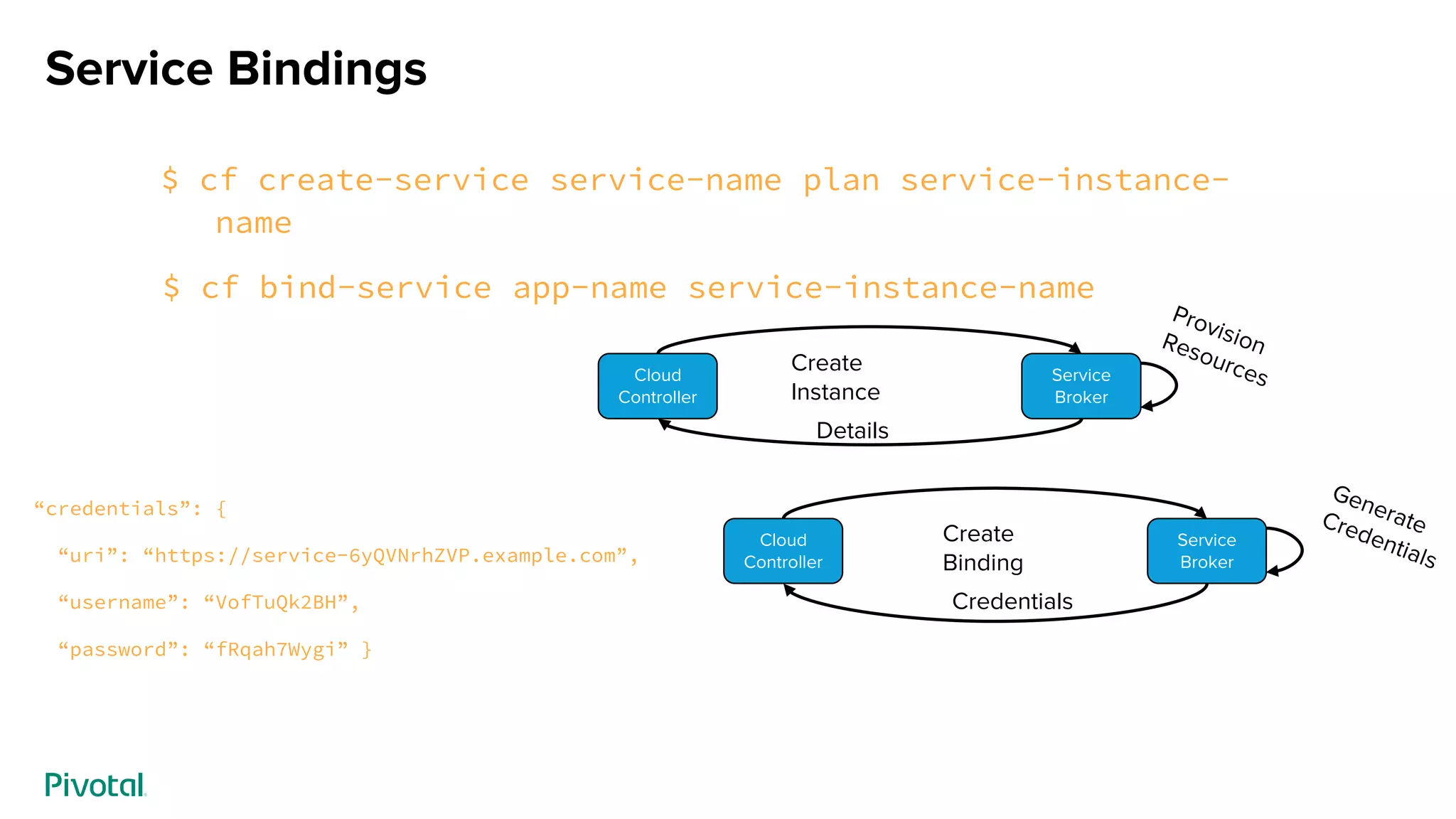
![Service Bindings
$ cf env app-name
“VCAP_SERVICES”: {
“service-name”: [{
“credentials”: {
“uri”: “https://service-6yQVNrhZVP.example.com”,
“username”: “VofTuQk2BH”,
“password”: “fRqah7Wygi”
},
}]
}](https://image.slidesharecdn.com/credhub-springonetourstl2019-190214173507/75/Secure-Credential-Management-with-CredHub-DaShaun-Carter-Sharath-Sahadevan-8-2048.jpg)
![Service Bindings With CredHub
$ cf bind-service app-name service-instance-name
create binding
credentials with credhub-ref
PUT /data
“credentials”: {
“uri”: “https://service-6yQVNrhZVP.example.com”,
“username”: “VofTuQk2BH”,
“password”: “fRqah7Wygi” }
“credentials”: {
“credhub-ref”:
“/c/my-broker/[instance-id]/[binding-id]/credentials” }
Cloud
Controller
Service
Broker
CredHub](https://image.slidesharecdn.com/credhub-springonetourstl2019-190214173507/75/Secure-Credential-Management-with-CredHub-DaShaun-Carter-Sharath-Sahadevan-10-2048.jpg)
![Service Bindings
$ cf env app-name
“VCAP_SERVICES”: {
“service-name”: [{
“credentials”: {
“credhub-ref”: “/c/my-broker/[instance-id]/[binding-
id]/credentials”
},
}]
}](https://image.slidesharecdn.com/credhub-springonetourstl2019-190214173507/75/Secure-Credential-Management-with-CredHub-DaShaun-Carter-Sharath-Sahadevan-11-2048.jpg)
![Credential Interpolation
CredHub
“VCAP_SERVICES”: {
“my-service”: [{
“credentials”: {
“credhub-ref”: “/c/my-broker/1111/2222/credentials”
},
}]
}
“VCAP_SERVICES”: {
“service-name”: [{
“credentials”: {
“uri”: “https://service-6yQVNrhZVP.example.com”,
“username”: “VofTuQk2BH”,
“password”: “fRqah7Wygi”
},
}]
}
POST /interpolate
interpolated credentials](https://image.slidesharecdn.com/credhub-springonetourstl2019-190214173507/75/Secure-Credential-Management-with-CredHub-DaShaun-Carter-Sharath-Sahadevan-12-2048.jpg)