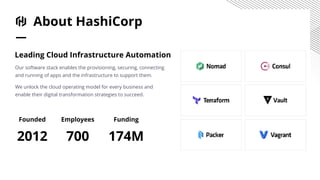
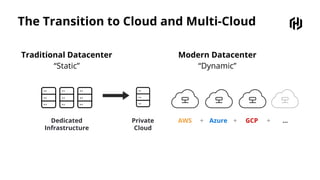
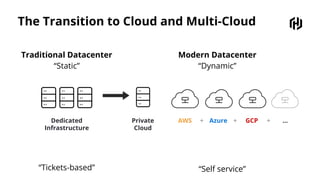
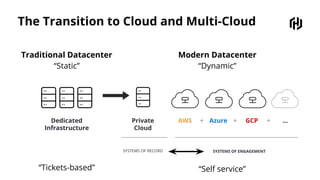
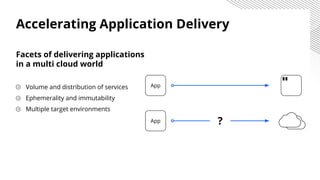
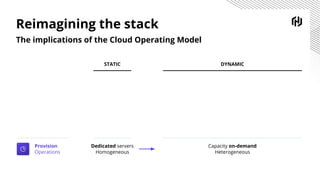
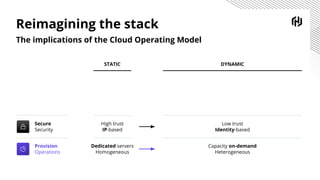
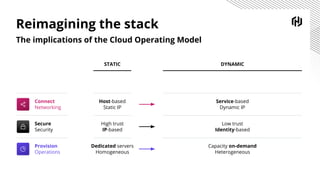
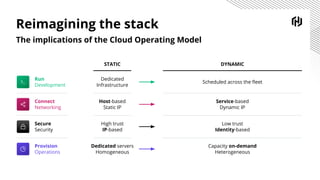
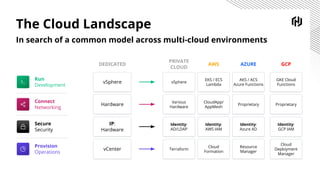
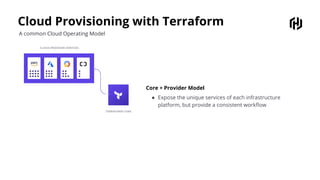
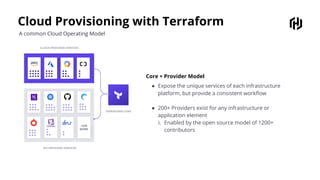
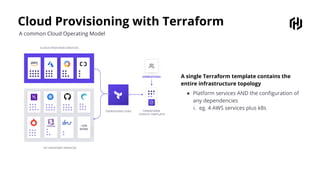
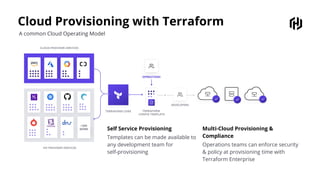
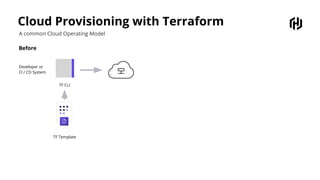
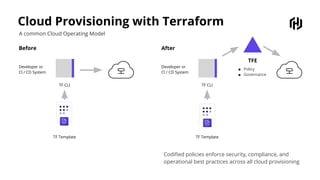
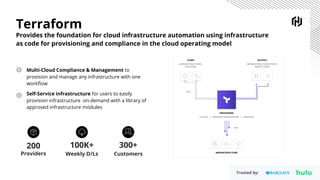
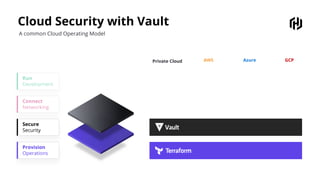
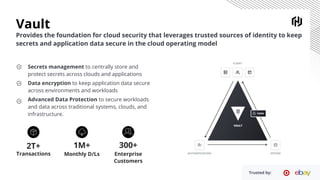
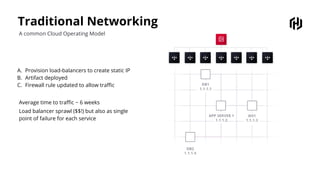
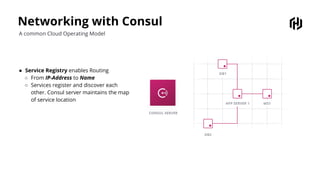
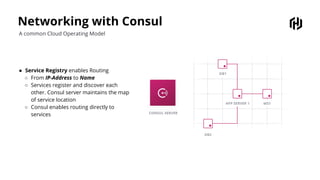
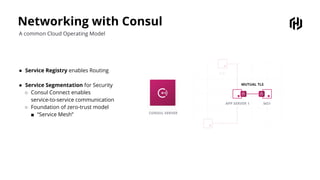
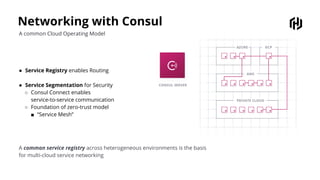
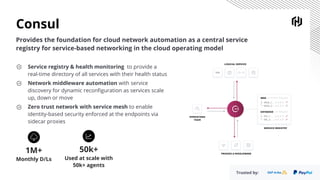
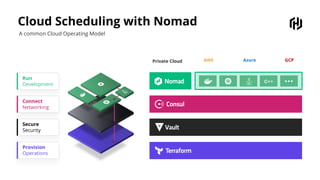
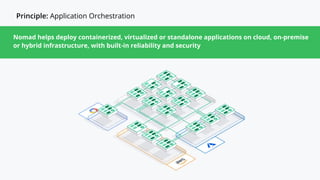
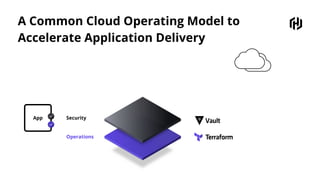
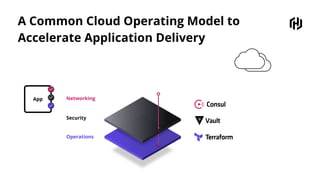
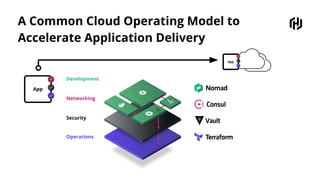
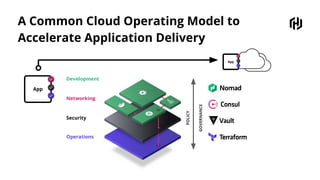
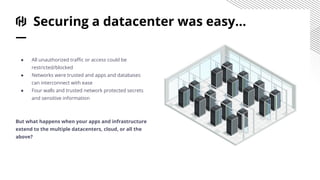
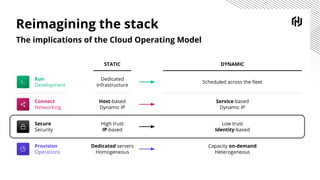
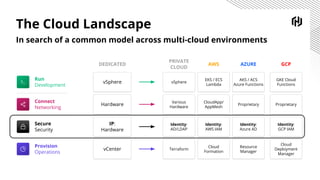
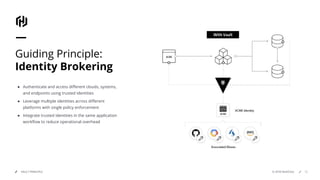
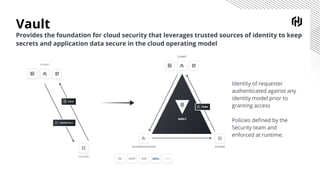
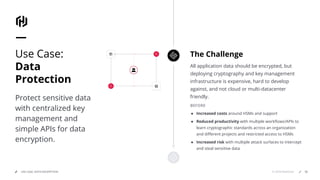
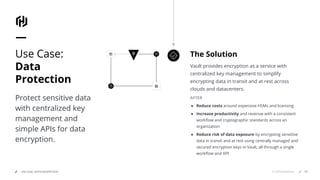
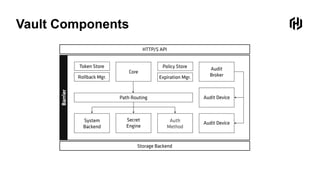
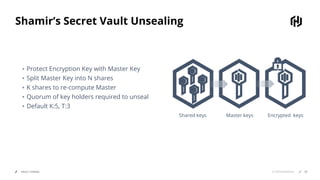
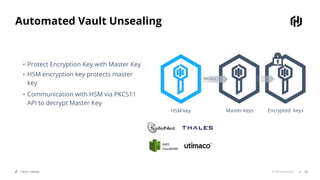
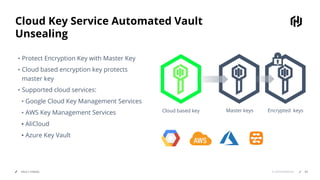
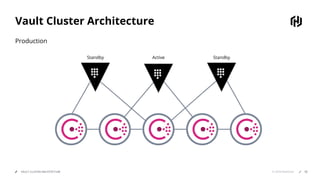
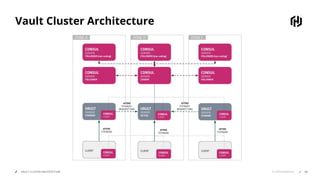
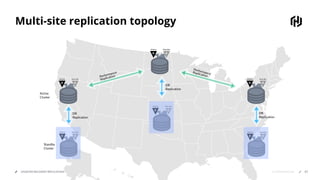
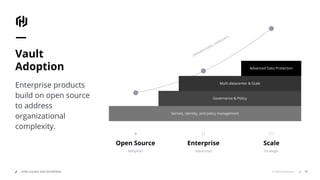
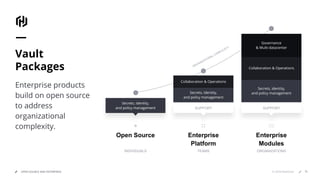
HashiCorp provides cloud infrastructure automation that supports digital transformation strategies and facilitates multi-cloud transitions. Their stack includes tools for provisioning, security, networking, and application orchestration across various cloud platforms. Key offerings include Terraform for infrastructure management, Vault for secrets and data security, and Consul for service networking, aiming to streamline application delivery and enhance security in dynamic environments.