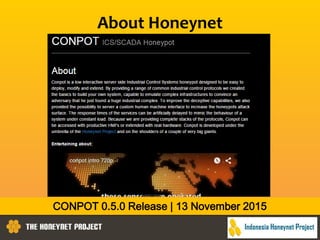
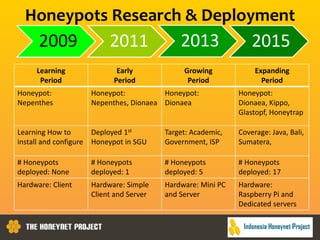
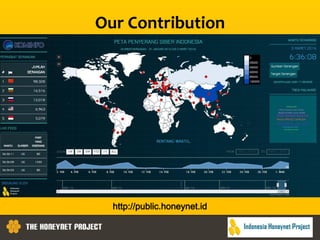
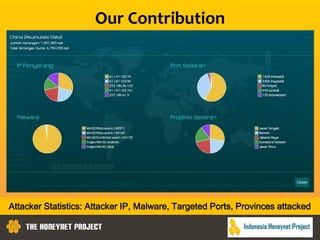
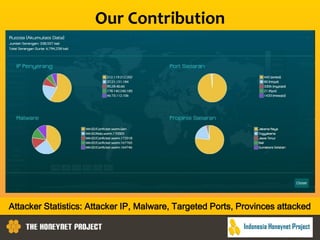
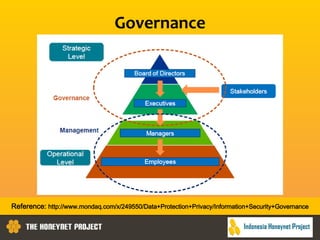
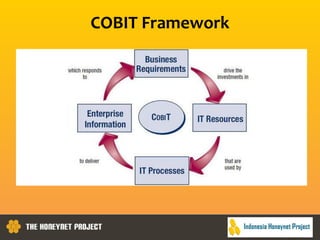
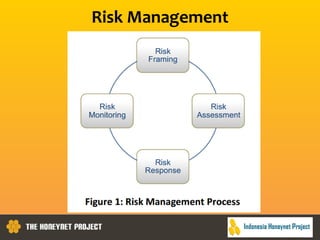
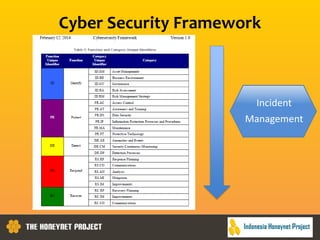
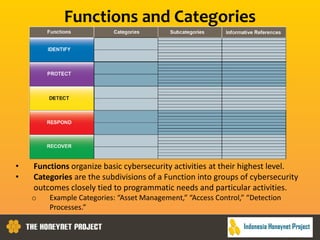
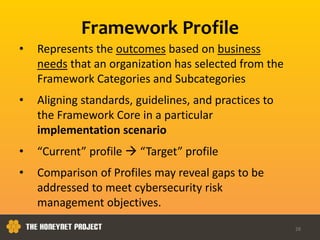
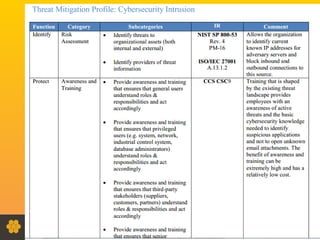
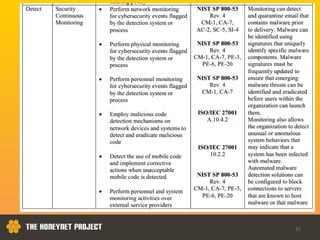
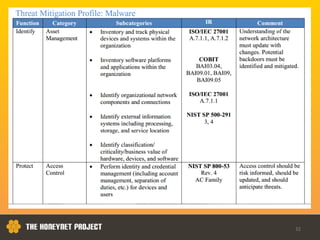
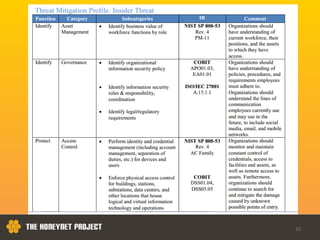
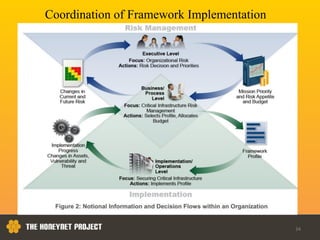
This document discusses the Honeynet Project and cyber security governance frameworks. It provides an overview of Honeynet, a non-profit focused on computer security research. It then discusses the importance of cyber security governance and introduces the NIST Cybersecurity Framework. The framework consists of five functions (Identify, Protect, Detect, Respond, Recover), categories within each function, and implementation tiers that describe an organization's cybersecurity risk management practices. The document emphasizes that effective cyber security requires leadership and continuous risk management to address evolving threats.