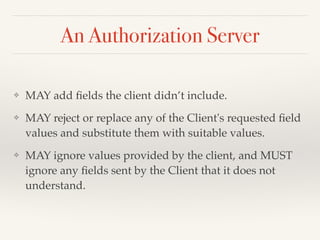
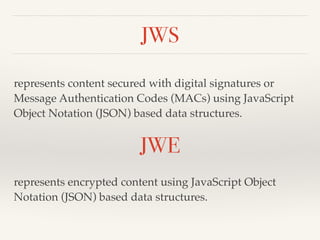
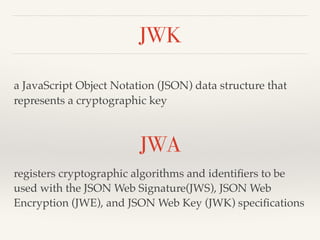
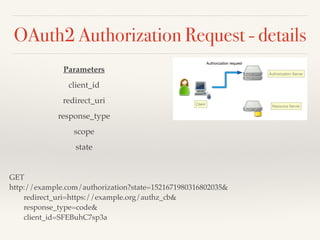
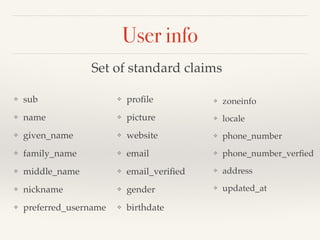
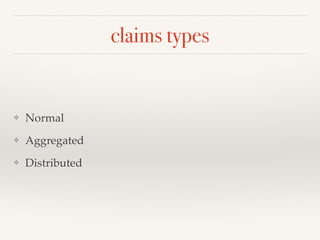
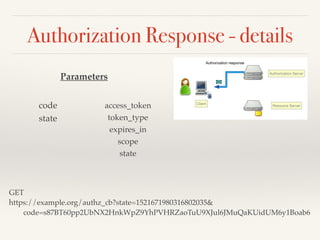
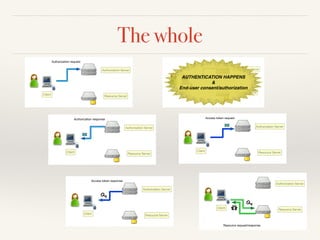
The document provides an overview of OAuth 2.0 and OpenID Connect, detailing how OAuth 2.0 enables limited access to HTTP services through various authorization flows. It describes the differences between OAuth and OpenID Connect, highlighting the additional identity layer and the processes for provider discovery and client registration. Key components such as authorization requests, access tokens, and ID tokens are also elaborated, emphasizing the importance of authentication and information claims.























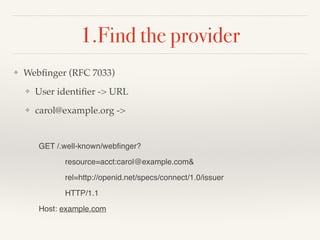
![Webfinger response
HTTP/1.1 200 OK!
Access-Control-Allow-Origin: *!
Content-Type: application/jrd+json!
!
{!
"subject" : "acct:carol@example.com",!
"links" :!
[ {!
"rel" : "http://openid.net/specs/connect/1.0/issuer",!
"href" : "https://openid.example.com"!
} ]!
}](https://image.slidesharecdn.com/cisopenidconnectintro-140811131050-phpapp02/85/CIS14-Working-with-OAuth-and-OpenID-Connect-27-320.jpg)