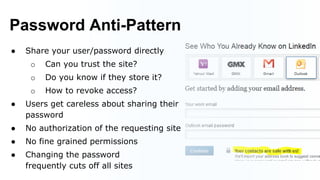
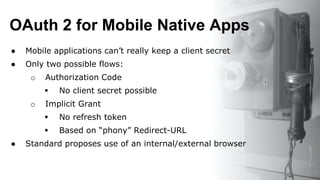
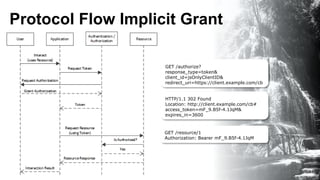
The document discusses building an ecosystem of applications using OAuth 2.0, Jersey, and Guice. It describes how to implement OAuth 2.0 authentication and authorization in a REST API built with JAX-RS and Jersey. Specifically, it shows how to enable the Implicit Grant flow to allow access from JavaScript clients, and integrates an external identity provider. The presentation includes a demonstration of these techniques using a coffee price service.














![Image Credits
Slide 2: By McKay Savage from London, UK [CC-BY-2.0], via Wikimedia Commons
Slide 4: By Hubert DENIES (Own work) [CC-BY-SA-3.0], via Wikimedia Commons
Slide 5: By Kweniston (Own work) [CC-BY-3.0], via Wikimedia Commons
Slide 6: By Ibonzer (Own work) [CC-BY-SA-3.0], via Wikimedia Commons
Slide 7: 2004 by Tomasz Sienicki [CC BY 2.5]
Slide 8: by Joe Shlabotnik [CC-BY 2.0] via Flickr
Slide 9: By Demilune [CC-BY-SA-2.5], via Wikimedia Commons
Slide 10: By David Bacon (Flickr: IMG_5126) [CC-BY-2.0], via Wikimedia
Commons
Slide 11: By Andrés Nieto Porras from Palma de Mallorca, España ([C] Café
Uploaded by russavia) [CC-BY-SA-2.0], via Wikimedia Commons
Slide 15: By Scott Schiller (Flickr: Master lock, "r00t" password) [CC-BY-2.0], via
Wikimedia Commons
Slide 16:
https://s3.amazonaws.com/github/ribbons/forkme_right_red_aa0000.png](https://image.slidesharecdn.com/j1-2013-bof3861-130926130527-phpapp02/85/Mixing-OAuth-2-0-Jersey-and-Guice-to-Build-an-Ecosystem-of-Apps-JavaOne-2013-18-320.jpg)