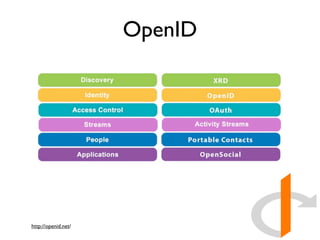
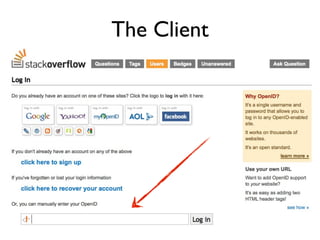
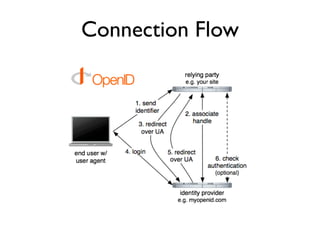
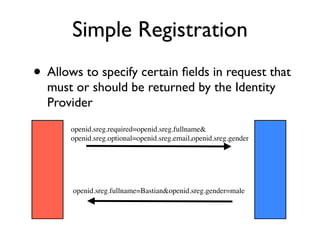
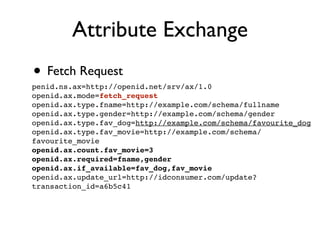
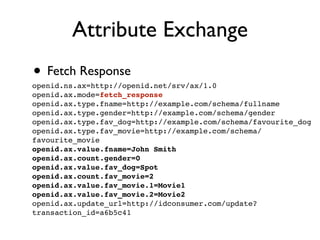
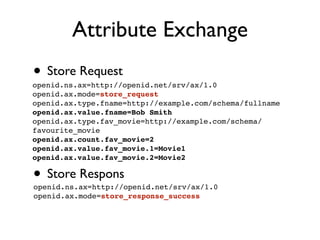
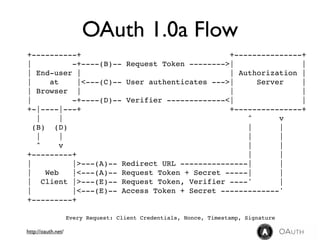
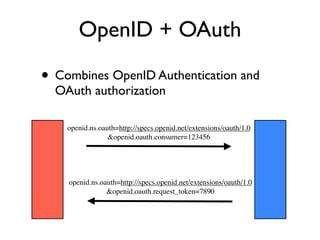
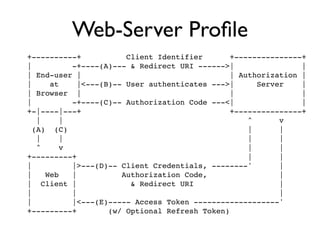
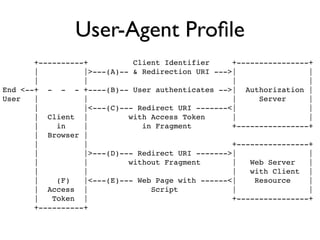
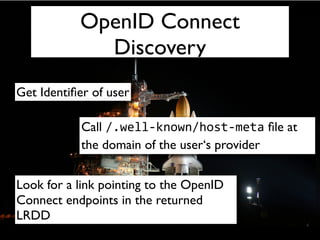
The document discusses identity management solutions like OpenID and introduces OpenID Connect as an evolution of OpenID that aims to be easier to implement with a better user experience by building on OAuth 2.0. It outlines some of the failures of OpenID 2.0 like being complex to implement and having a URL-based identifier that provides a bad user experience. It then explains some of the improvements in OAuth 2.0 and OpenID Connect like removing signatures, introducing bearer tokens, and adding scopes to provide more flexibility and control over access.