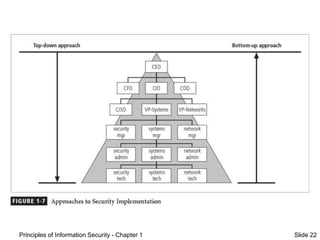
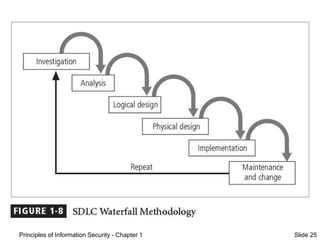
This document provides an introduction to information security. It discusses the history of computer security and how it evolved into information security. Key topics covered include the definition of information security, the systems development life cycle for security, and security professionals' roles in an organization. The document presents information security as both an art and a science due to its complex interactions between users, policies, and technology controls.