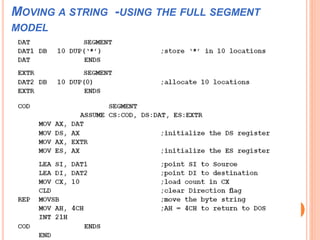
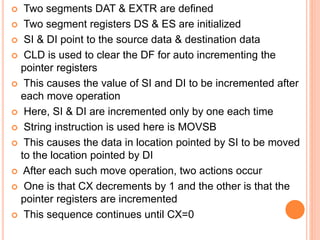
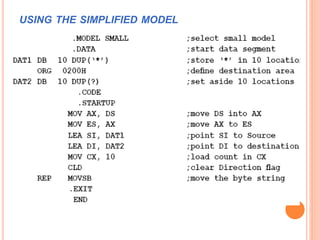
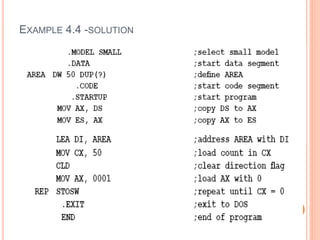
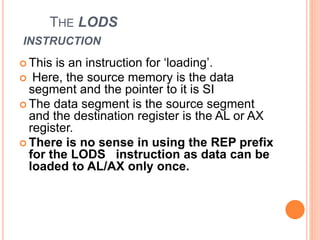
Chapter 4 discusses string instructions in the 8086, explaining their purpose and usage in handling blocks of data, such as moving, comparing, and scanning strings. It outlines prerequisites for utilizing these instructions, including setting up segment registers and pointers, as well as controlling the direction of operation with the direction flag. Additionally, the chapter covers procedures, calling and returning from procedures, the use of the stack, passing parameters, and the macro functionality for code efficiency.





















![II) INDIRECT CALL
Usage: CALL reg16, CALL [reg16]
In this case, the destination is specified in a 16-bit
register or in a memory location pointed by a
register.
This is not a ‘relative’ call. The content of the
referred register or memory location is loaded into
IP for using the procedure.
Examples
CALL BX ;the procedure’s address is in BX
CALL WORD PTR[BX] ;the address of the
procedure is in memory and is pointed by BX](https://image.slidesharecdn.com/chapter4-programmingconceptsiii-170612061533/85/Chapter-4-programming-concepts-III-32-320.jpg)


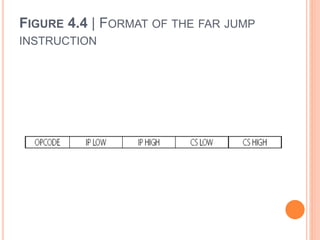

![ Example of an indirect far call
CALL DWORD PTR [SI] can be a far call instruction.
[SI] and [SI + 1] gives the new value of IP and [SI + 2]
and [SI + 3] gives the new value of CS.
Far calls and procedures are specified using the ‘far’
directive when defining the procedure.
In Chapter 5, we will see how the EXTRN directive is
used in this context.](https://image.slidesharecdn.com/chapter4-programmingconceptsiii-170612061533/85/Chapter-4-programming-concepts-III-37-320.jpg)











![WRITING A MACRO –THE FORMAT
MACRO-NAME MACRO [parameter list]
Instructions (body of the macro)
ENDM](https://image.slidesharecdn.com/chapter4-programmingconceptsiii-170612061533/85/Chapter-4-programming-concepts-III-54-320.jpg)