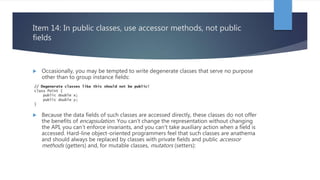
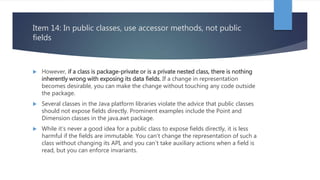
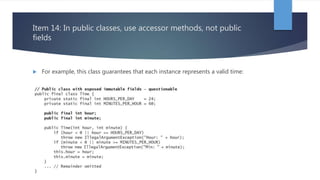
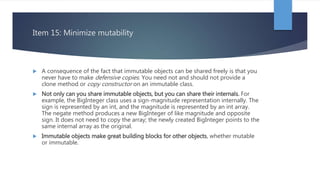
Chapter 4 of 'Effective Java' discusses the importance of classes and interfaces in Java, emphasizing encapsulation and information hiding as key principles for module design. It advises minimizing accessibility of classes and members to enhance reusability and reduce risks in software development, as well as recommending immutable classes for safety and simplicity. The chapter also cautions against improper use of inheritance, advocating for composition and thoughtful design to facilitate future changes.




![Item 13: Minimize the accessibility of classes and members
For top-level (non-nested) classes and interfaces, there are only two possible access levels:
package-private and public. If you make it public, you are obligated to support it forever to
maintain compatibility.
For members (fields, methods, nested classes, and nested interfaces), there are four possible
access levels,
private—The member is accessible only from the top-level class where it is declared.
package-private(default)—The member is accessible from any class in the package where it is
declared. Technically known as default access, this is the access level you get if no access modifier
is specified.
protected—The member is accessible from subclasses of the class where it is declared (subject to a
few restrictions [JLS, 6.6.2]) and from any class in the package where it is declared.
public—The member is accessible from anywhere.](https://image.slidesharecdn.com/effectivejava-2ndedition-chapter4-151203200429-lva1-app6891/85/Effective-Java-Chapter-4-Classes-and-Interfaces-5-320.jpg)