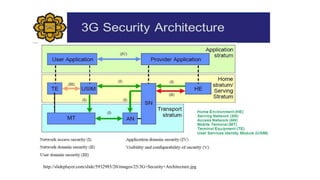
This document discusses security issues and mechanisms in cellular wireless networks. It begins by explaining how cellular communication has become important for daily tasks like accessing the internet, banking, messaging, etc. It then outlines several key security issues for cellular networks including authentication, integrity, confidentiality, access control, location detection, viruses/malware, downloaded content security, device security, and operating system vulnerabilities. Next, it describes various types of attacks such as denial of service, distributed denial of service, channel jamming, and man-in-the-middle attacks. The document concludes by explaining 3G and 4G security architectures and features like network access security, challenge response authentication, and encryption between devices and base stations.












![References
[1]”Security in Wireless Cellular Networks” IJAIEM, Volume 4,Issue 4,April 2015
http://www.ijaiem.org/Volume4Issue4/IJAIEM-2015-04-29-72.pdf
[2]”Wireless Cellular Security Mechanism” IJESI, Volume 3,Issue 5,May 2015
http://www.ijesi.org/papers/Vol(3)5/Version-1/A035101011.pdf
[3]”A Survey of Wireless Network Security” IJCSMC, Vol. 3, Issue. 1, January 2014
http://d.researchbib.com/f/7nnJcwp21wYzAioF9xo2AmY3OupTIlpl9XLJ51LKW5ZwNkAP9JZ0xkZwNkAQR
jYaOxMt.pdf
[4]”Wireless Networking and Communication” International Journal of Advanced Research in Computer and
Communication Engineering Vol. 2, Issue 8, August 2013](https://image.slidesharecdn.com/cellularwirelessnetworksecurity-171018175507/85/Cellular-wireless-network-security-14-320.jpg)