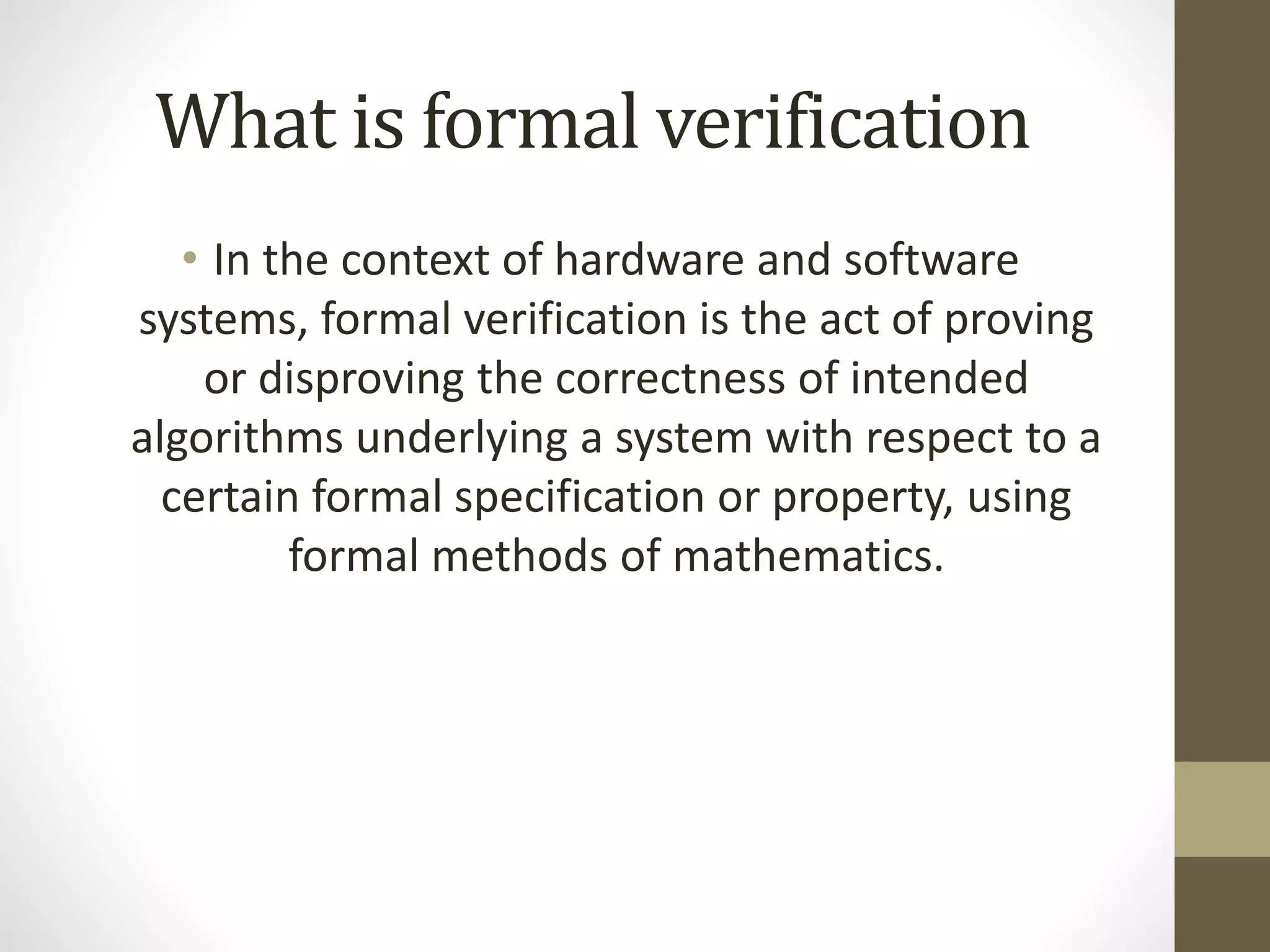
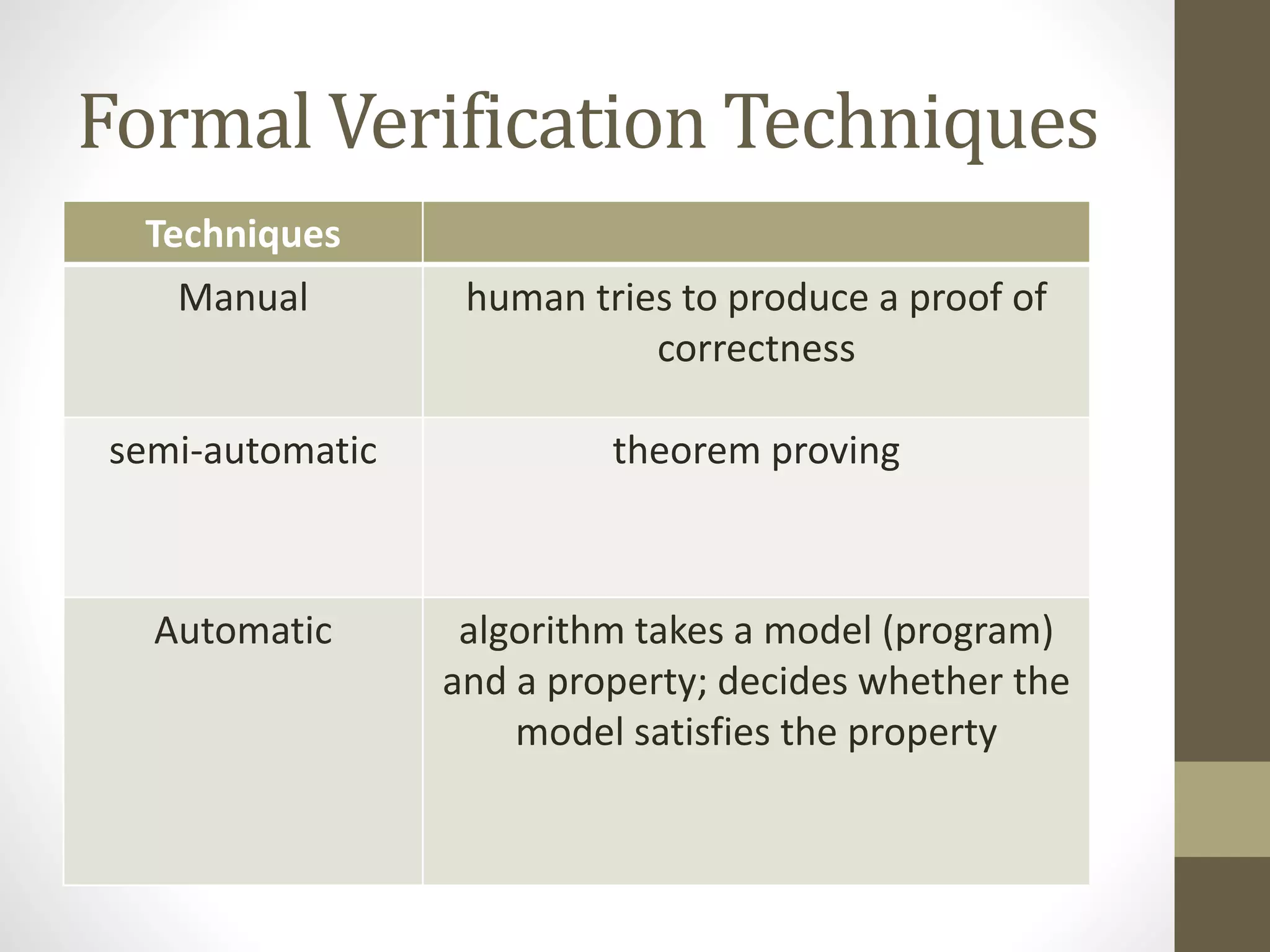
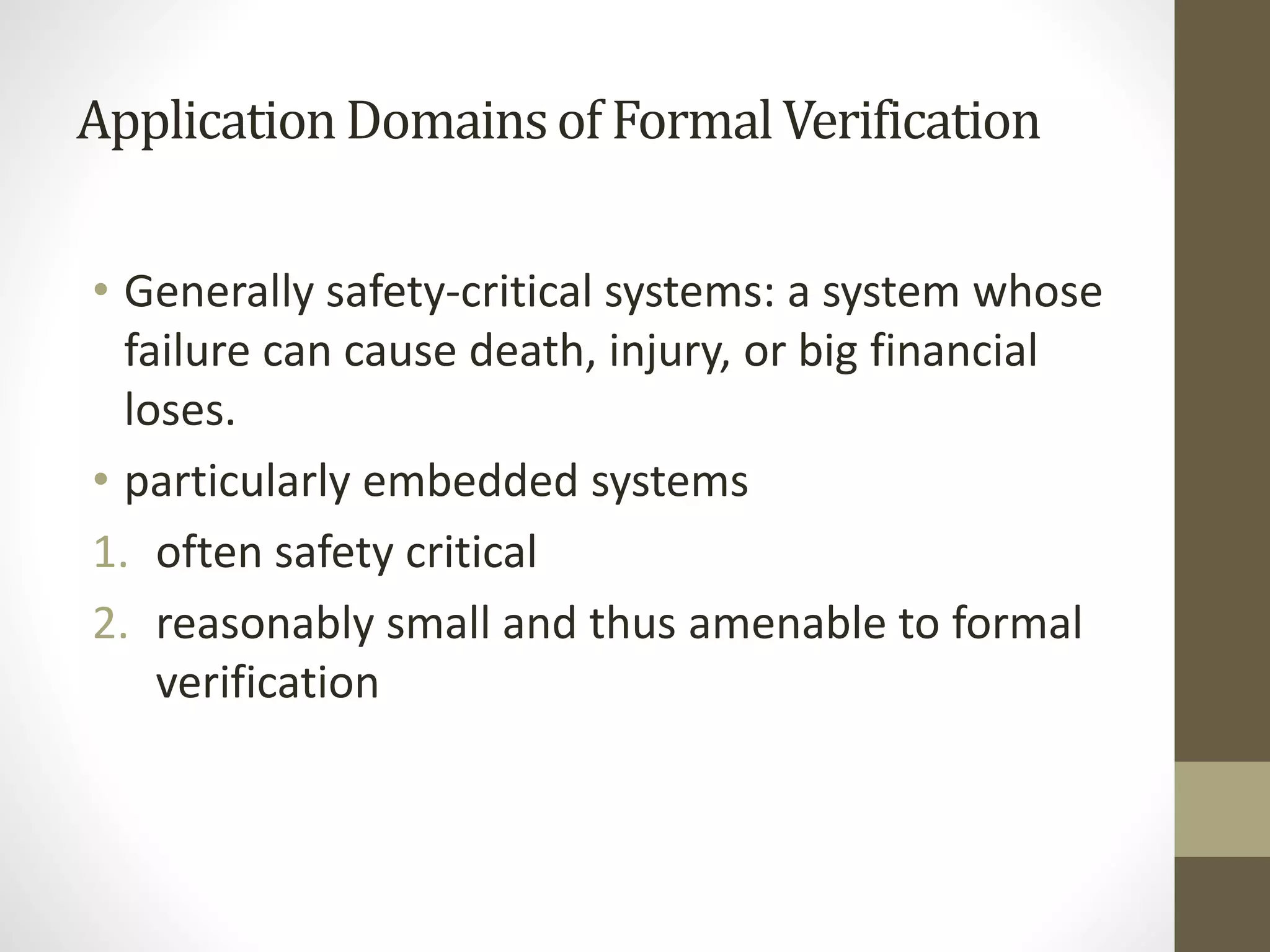
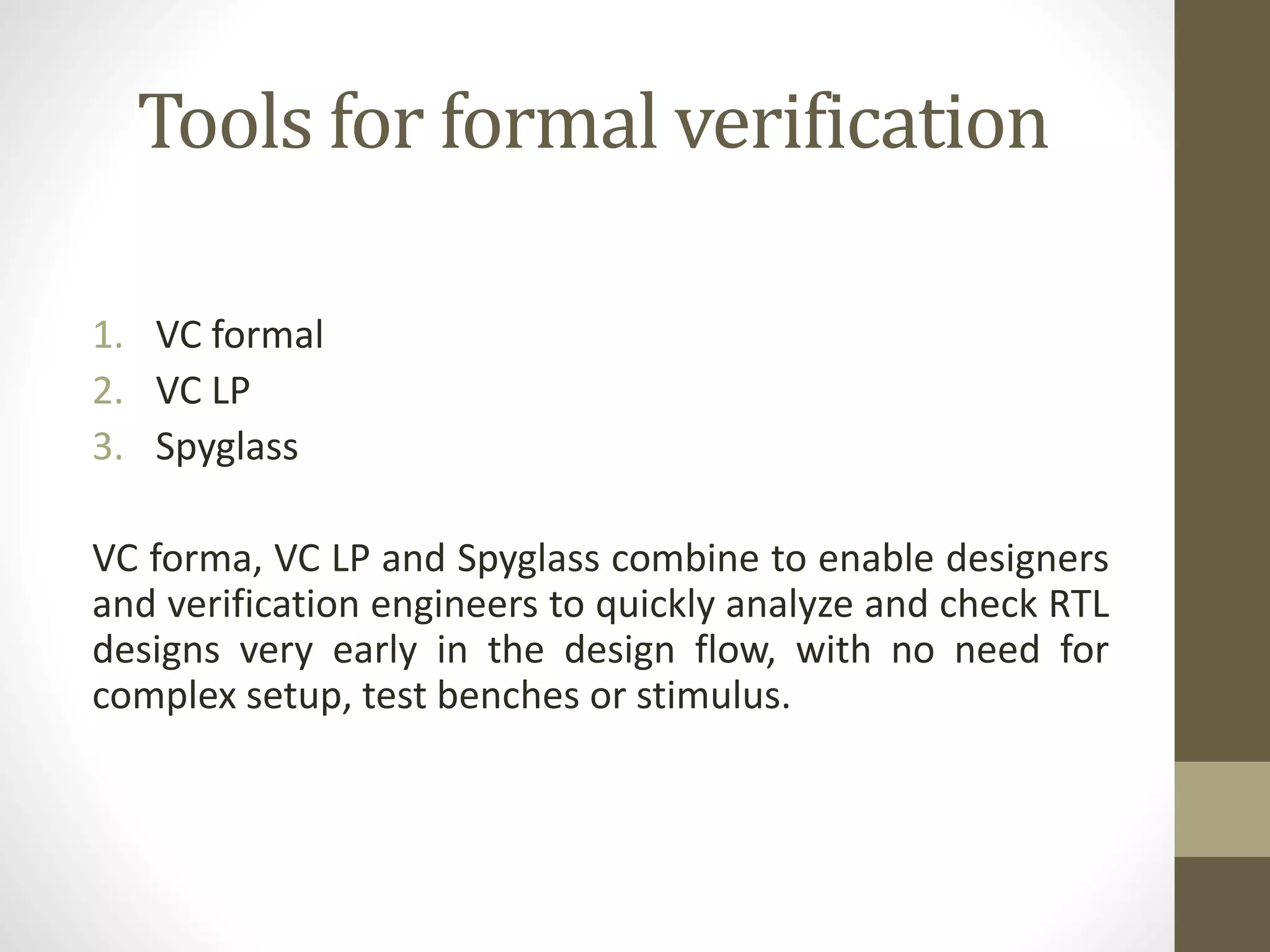
Formal verification refers to mathematical techniques for specifying, designing, and verifying software and hardware systems. It involves proving or disproving the correctness of algorithms in a system with respect to a formal specification or property using formal methods of mathematics. Formal verification techniques include manual proofs, semi-automatic theorem proving, and automatic algorithms that take a model and property to determine if the model satisfies the property. Formal verification is commonly used for safety-critical systems like embedded systems to help ensure correctness. Tools like VC formal, VC LP, and Spyglass can be used to formally verify designs early in development without complex test benches or stimulus.